XACML-based access control policy conflict detection method
An access control strategy and conflict detection technology, applied in other database retrieval, special data processing applications, creation/generation of source code, etc., can solve the problems of difficult and flexible modification, opacity of policy designers, etc., to achieve efficient and accurate policy control, implementation The effect of conflict detection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0039] The present invention will be further described below in conjunction with the accompanying drawings.
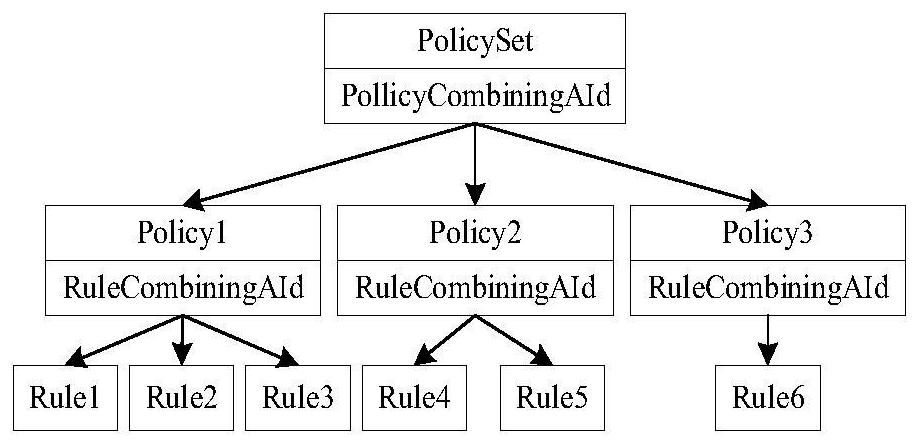
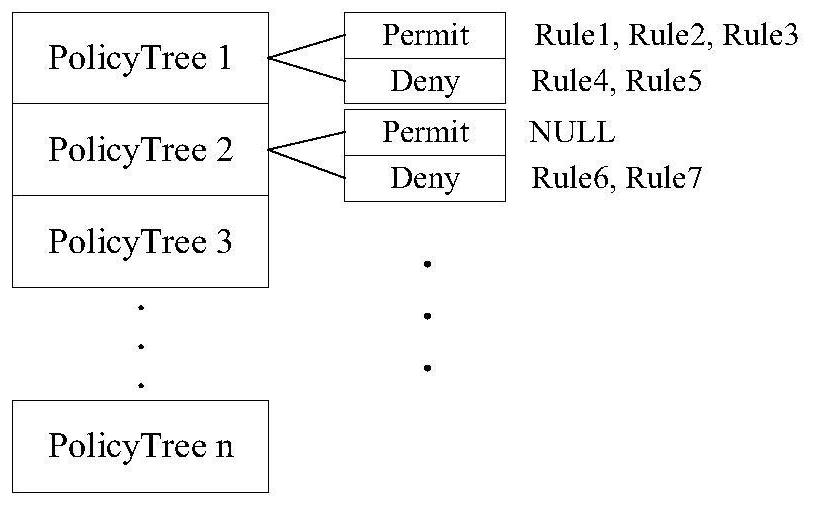
[0040] In order to solve the problems in the prior art, the present invention provides a method for detecting XACML policy rules. This method has a brand-new policy index structure, based on expression tree comparison, which can realize the conflict detection of complex policies and mark the cause of the conflict. Users can flexibly configure and resolve policy conflicts based on conflict marks to achieve efficient and accurate policy control.
[0041] The technical problems to be solved in the present invention are as follows:
[0042] (1) Establishment of expression trees and formal analysis of comparison rules;
[0043] (2) Conflict detection algorithm design.
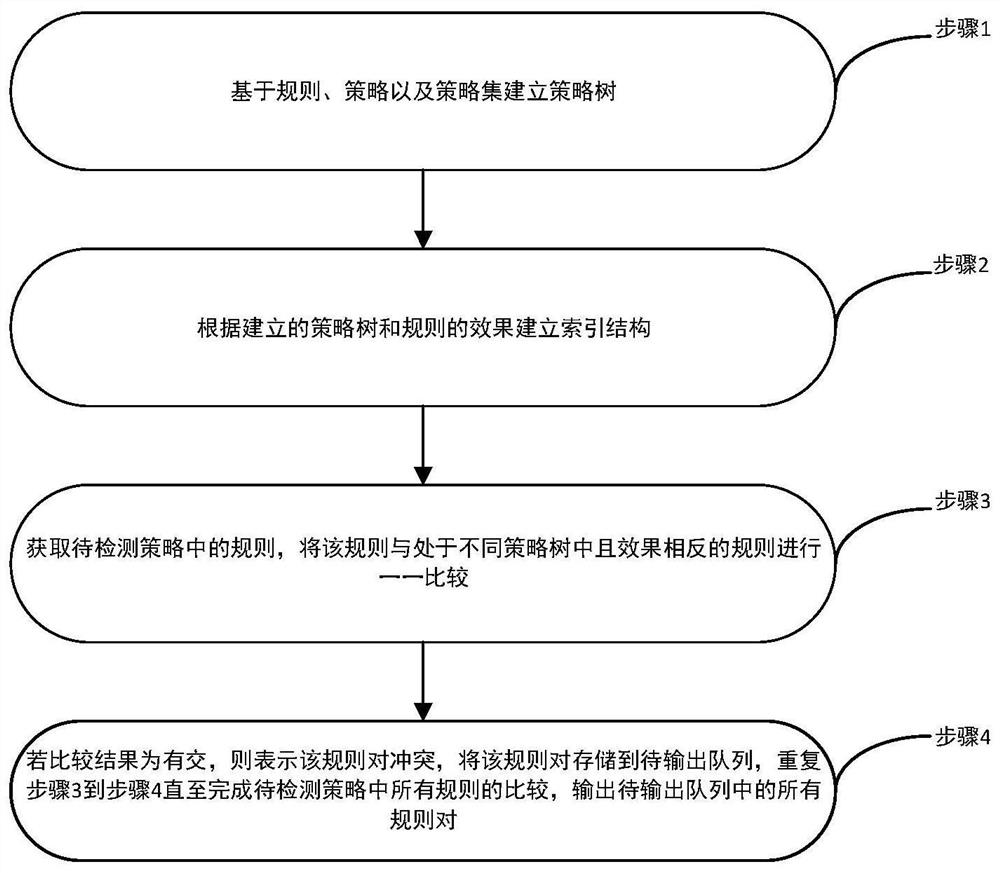
[0044] Such as figure 1 As shown, the present invention proposes a method for detecting conflicts of access control policies based on XACML, including the following processes:
[0045] Step 1. Build a p...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com