Method, device and equipment for monitoring weak password vulnerabilities of network equipment
A network device and weak password technology, applied in the field of network security, can solve the problem of finding weak password devices without effective measures, and achieve the effect of relieving work pressure
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
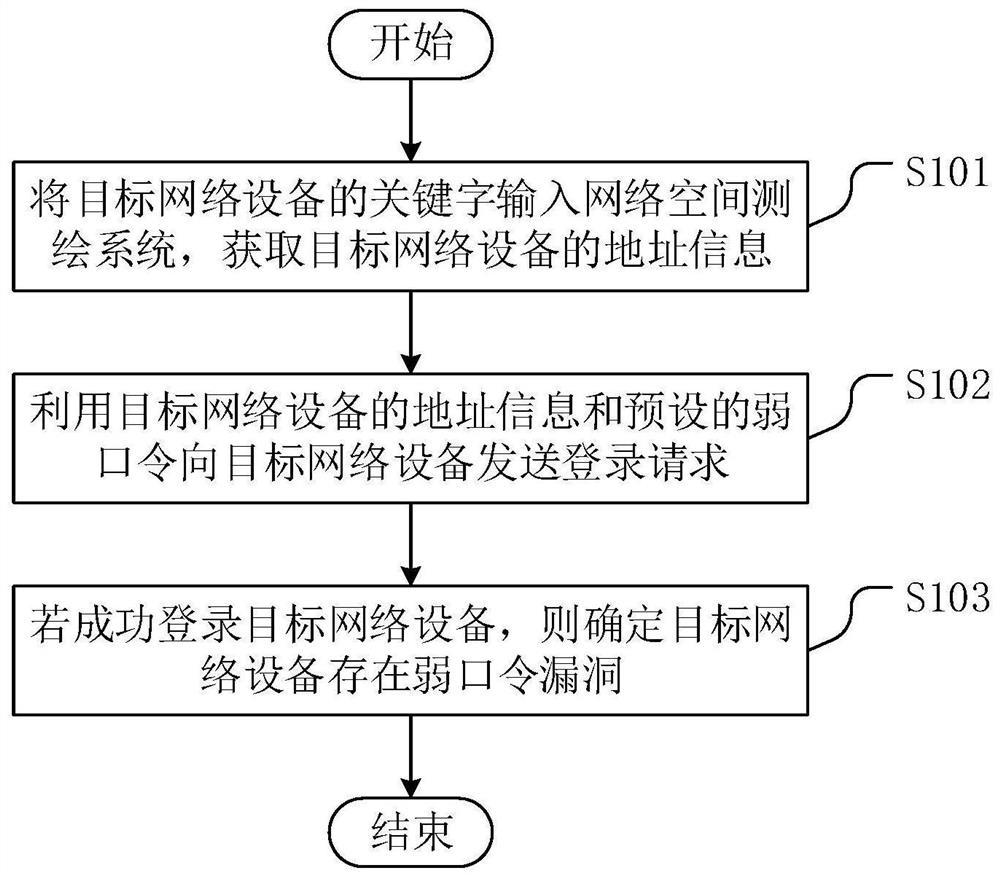
[0041] figure 1 It is a flow chart of a method for monitoring weak password vulnerabilities of network devices provided by the embodiment of the present application.
[0042] Such as figure 1 As shown, the method for monitoring weak password vulnerabilities of network equipment provided by the embodiment of the present application includes:
[0043] S101: Input a keyword of a target network device into a cyberspace surveying and mapping system to obtain address information of the target network device.
[0044] S102: Send a login request to the target network device by using the address information of the target network device and a preset weak password.
[0045] S103: If the target network device is successfully logged in, it is determined that the target network device has a weak password vulnerability.
[0046] To realize the monitoring of weak password vulnerabilities of network devices in the Internet, it is first necessary to obtain the address of the target network d...
Embodiment 2
[0062] In the foregoing embodiments, the address information of the target network device is obtained through the network space surveying and mapping system. Existing cyberspace surveying and mapping systems include sumap, fofa, zoomeye, etc. These cyberspace surveying and mapping systems all have their own search syntax, and they are pre-designed according to the type of cyberspace surveying and mapping system to call the cyberspace surveying and mapping system and input the keyword of the target network device script.
[0063] Therefore, in the embodiment of this application, figure 1 Step S101 in: Input the preset keyword of the target network device into the cyberspace surveying and mapping system to obtain the address information of the target network device, specifically including:
[0064] Input the preset keyword of the target network device into the built-in grammar corresponding to the cyberspace surveying and mapping system, and obtain the constructed query stateme...
Embodiment 3
[0098] Target network devices may include routers, firewalls, load balancers, etc. Different network devices have different access methods. On the basis of the above embodiments, in the method for monitoring weak password vulnerabilities of network devices provided in the embodiments of the present application, step S102: send a login request to the target network device using the address information of the target network device and the preset weak password, specifically Can include:
[0099] According to the JS object numbered notation (json) of the address information of the target network device output by the cyberspace surveying and mapping system, generate a uniform resource location system (URL) for logging in to the firewall of the target network device;
[0100] Utilize Uniform Resource Locator and weak passwords to send login requests to target network devices.
[0101] The various embodiments corresponding to the monitoring method for weak password vulnerabilities of ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com