Telecommunication network fraud identification method and device, equipment and storage medium
A telecommunication network and identification model technology, applied in the field of network communication, can solve problems affecting work and life, economic loss of users, troubles in normal life, etc., and achieve the effect of avoiding losses and solving identification problems
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
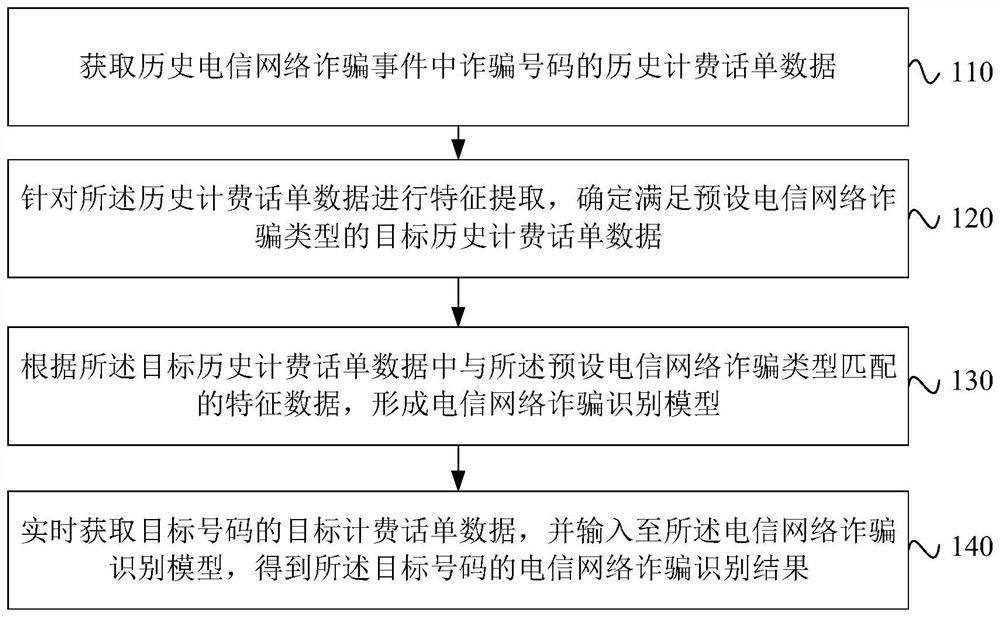
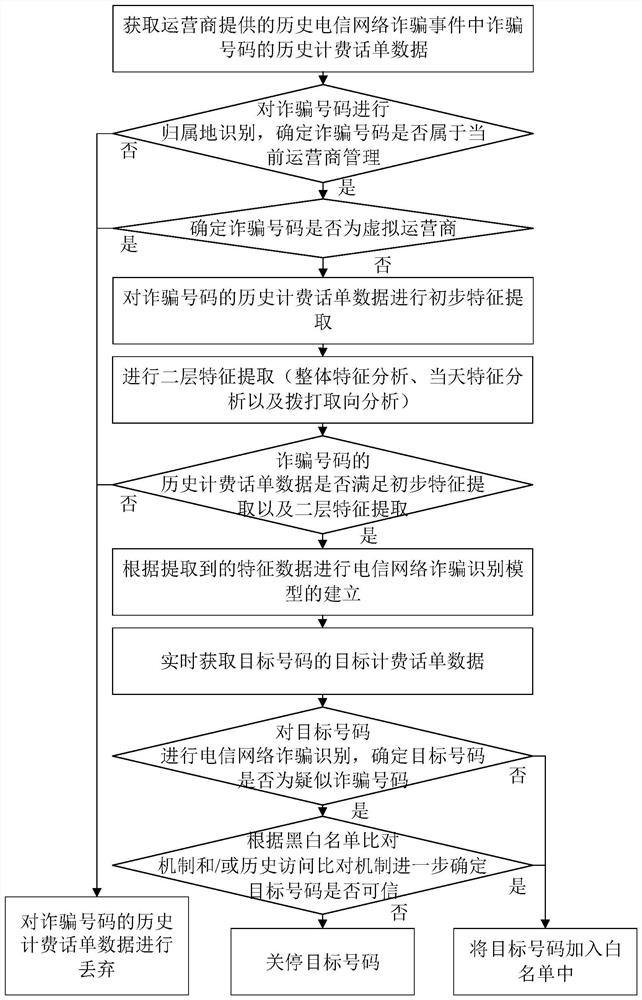
[0027] Figure 1a It is a flow chart of a telecommunications network fraud identification method provided by Embodiment 1 of the present invention. This embodiment is applicable to the situation of identifying fraudulent mobile phone numbers in a telecommunications network for fraud early warning, especially applicable to fraudulent mobile phone numbers for online shopping identification, the method can be performed by a telecommunications network fraud identification device, the device can be implemented by software and / or hardware, and the device can be integrated in electronic equipment such as mobile phones, servers or computers, such as Figure 1a As shown, the method specifically includes:
[0028] Step 110, acquiring historical billing data of fraudulent numbers in historical telecommunication network fraud events.
[0029] Wherein, the historical telecommunication network fraud event may be an event composed of recorded historical fraud information reported by the defra...
Embodiment 2
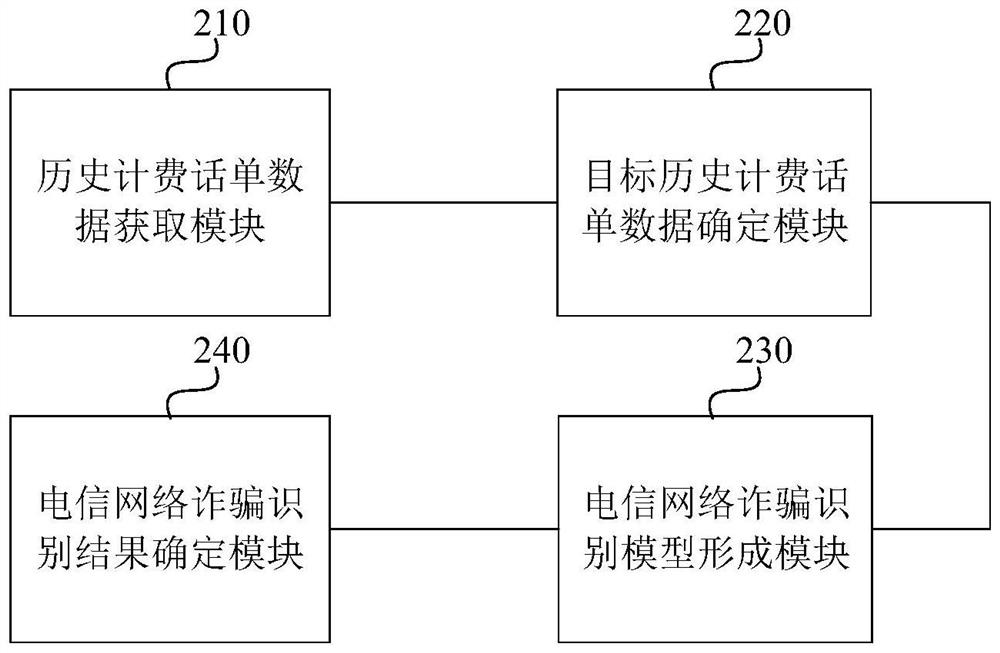
[0071] figure 2 It is a schematic structural diagram of a telecommunications network fraud identification device provided in Embodiment 2 of the present invention. to combine figure 2 , the device includes: historical billing bill data acquisition module 210, target historical billing bill data determination module 220, telecommunications network fraud identification model forming module 230 and telecommunications network fraud identification result determination module 240. in:
[0072] The historical billing bill data acquisition module 210 is used to obtain the historical billing bill data of the fraudulent number in the historical telecom network fraud event;
[0073] The target historical billing bill data determination module 220 is used to perform feature extraction for the historical billing bill data, and determine the target historical billing bill data that meets the preset telecommunications network fraud type;
[0074] A telecommunications network fraud ident...
Embodiment 3
[0096] image 3 It is a schematic structural diagram of an electronic device provided in Embodiment 3 of the present invention, such as image 3 As shown, the equipment includes:
[0097] one or more processors 310, image 3 Take a processor 310 as an example;
[0098] memory 320;
[0099] The device may also include: an input device 330 and an output device 340 .
[0100] The processor 310, the memory 320, the input device 330 and the output device 340 in the device can be connected by a bus or in other ways, image 3 Take connection via bus as an example.
[0101] The memory 320, as a non-transitory computer-readable storage medium, can be used to store software programs, computer-executable programs and modules, such as program instructions / modules corresponding to a telecommunications network fraud identification method in an embodiment of the present invention (for example, attached figure 2 The historical charging bill data acquisition module 210 shown, the targe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com