Image steganography method based on SE-ResNet
An image and secret image technology, applied in the field of image processing, can solve the problems of complex embedding and extraction process, and achieve the effects of enhanced invisibility, increased steganographic capacity, and optimized weights
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0040] The present invention will be described in detail below in conjunction with the accompanying drawings and specific embodiments.
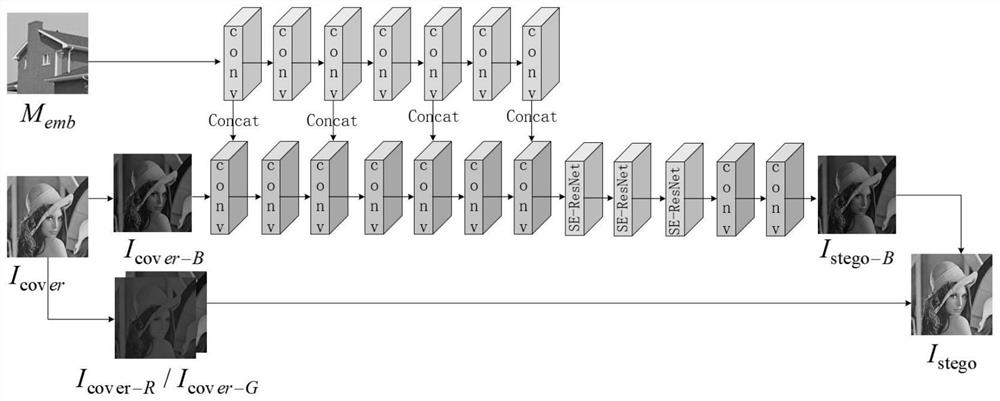
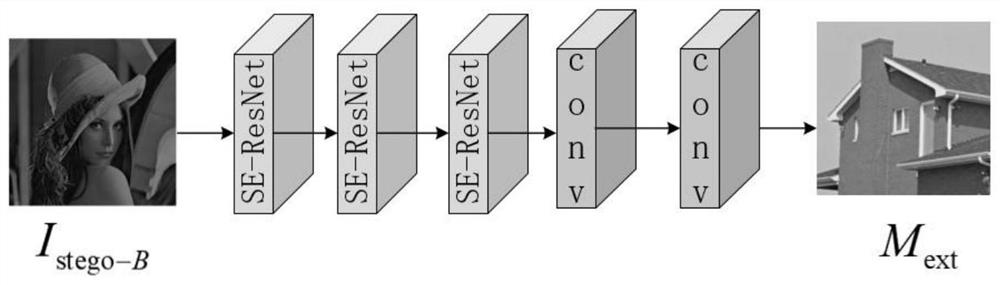
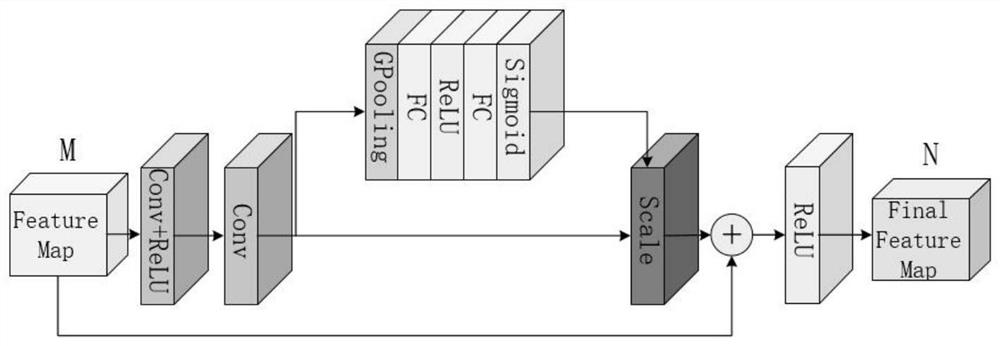
[0041] The present invention is based on the SE-ResNet steganography method, such as figure 1 As shown, I cover Indicates the color carrier image, Icover-B Represents the B channel of the color carrier image, I cover-R and I cover-G Represent the R channel and G channel of the carrier image, I stego-B represents the B channel of the steganographic image, I stego Represents a steganographic image. The specific process is: the secret image M emb Input the Guest network branch of the encoding network. The Guest network branch is composed of 7 convolutional layers, each of which is composed of a conv convolution operation and a ReLU activation function. Conv convolution operation feature extraction, ReLu activation operation for nonlinear mapping. At the same time, the B channel I of the carrier image cover-B Input the Host network branch...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap