Reversible database watermark embedding and extracting method based on integral wavelet transformation
A technology of wavelet transform and extraction method, applied in the direction of digital data protection, program/content distribution protection, etc., can solve the problems of poor watermark invisibility and weak robustness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
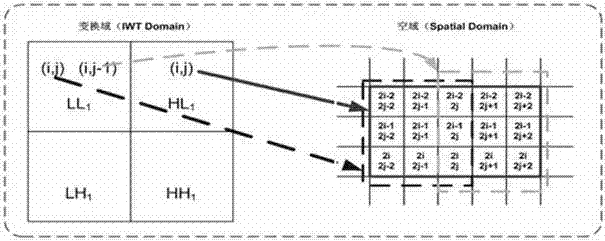
[0019] In this embodiment, the Le Gall5 / 3 filter is used to realize the first-level integer wavelet transform, the watermark adopts a pseudo-random binary sequence, the size of the data group is 8×8, and the coefficient vector parameter coefficient k i Take 2 or 4, embedding strength β j Take 2 or 4.
[0020] The specific steps are:
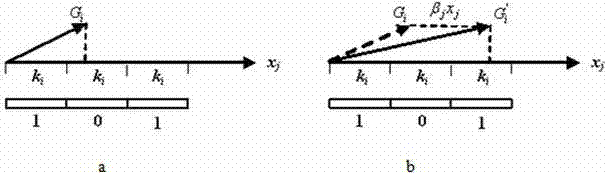
[0021] Step 1 watermark generation: generate a binary watermark sequence W1 from the owner and user information, use the key k1 to generate a binary chaotic sequence L, their length is nw, perform chaotic modulation on W1 by L, and get the watermark signal W to be embedded, Then by the watermark W i Generate a sub-watermark sequence {w i0 ,w i1 ,L,w i(t-1)}, whose length is t. where 0≤i≤nw-1, here Indicates XOR, and the sub-watermark generation rules are as follows:
[0022] w ij = 0 W ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com