Anti-printing and scanning watermark algorithm for two-value text image based on row space and word space
An anti-print scanning, text image technology, applied in image data processing, image data processing, computing and other directions, can solve the problems of complex watermark embedding and extraction systems, high visibility, low embedding capacity, etc., to avoid quality degradation, widely used. Scope of application, effect of increasing embedded capacity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
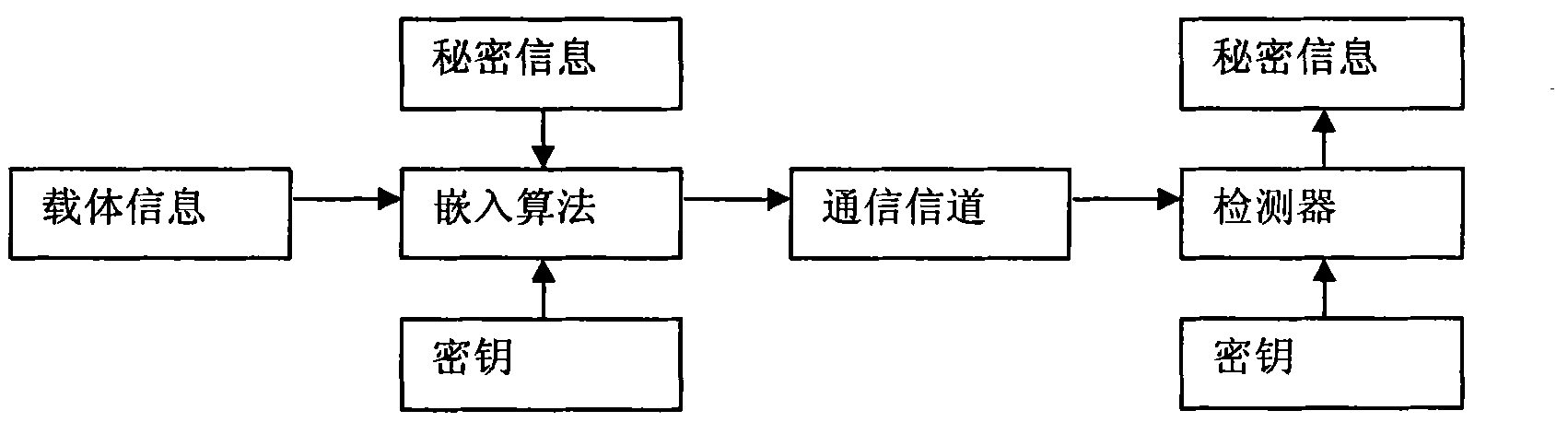
[0043] The specific implementation steps of watermark embedding of binary text image refer to Figure 5 ,Described as follows:
[0044] Step 1, extract all line spaces and word spaces in the binary text image.
[0045] According to the binary text image to embed the watermark, obtain all its row space and word space, and form a one-dimensional vector respectively in row-major order, which are respectively recorded as the row space vector Row and the word space vector Word.
[0046] Step 2, scrambling operation.
[0047] In order to improve the invisibility and security of the watermark embedded in the binary text image, a custom scrambling operation is performed on Row and Word. Scrambling rules can be defined by the executor himself. For example, the line / word space vector of the binary text image is scrambled first, then the watermark 01 sequence to be embedded is modulated to the line / word space vector, and finally the scrambled line / word space vector is reversed, so as ...
Embodiment 2
[0064] The specific implementation steps of watermark extraction of binary text images refer to Image 6 ,Described as follows:
[0065] Step 1, extract all line spaces and word spaces in the binary text image.
[0066] Same as step 1 for watermark embedding of binary text images.
[0067] Step 2, scrambling operation.
[0068] Same as step 2 for watermark embedding of binary text images.
[0069] Step 3, block operation.
[0070] Same as step 3 for watermark embedding of binary text images.
[0071] Step 4, demodulate all blocks.
[0072] The demodulation operation is to judge the pulse waveform characteristics of the elements in the block from the divided line / word space vector according to the pulse waveform distribution defined during modulation, so as to extract the embedded watermark information; for example, according to each obtained in step 3 Divide into blocks, and analyze the pulse waveform represented by each block in turn. If the values of the three eleme...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com