Application container monitoring method and device, equipment and storage medium
A technology for applying containers and containers, applied in the computer field, can solve problems such as difficulty in discovering business application anomalies, inability to monitor business applications, etc., and achieve the effect of being easy to deal with
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
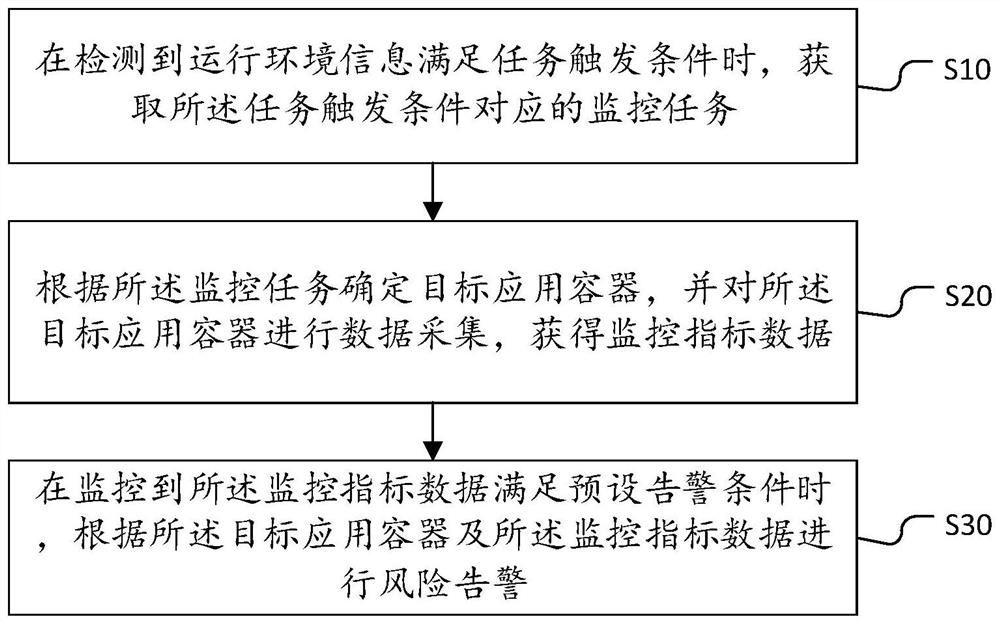
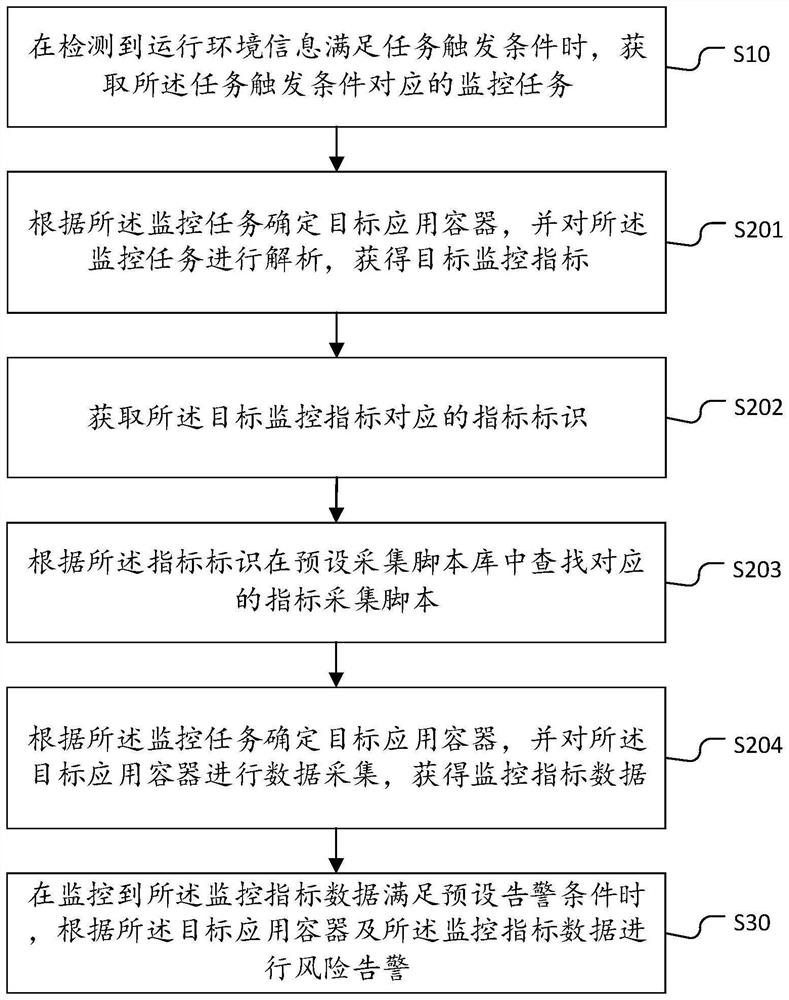
[0089] Based on the first embodiment above, this embodiment applies the step S20 of the container monitoring method, including:
[0090] Step S201: Determine a target application container according to the monitoring task, and analyze the monitoring task to obtain a target monitoring index.
[0091] It should be noted that the target monitoring indicators can be the monitoring indicators that need to be collected when monitoring the target application container, and the monitoring indicators can include: memory, read and write (I / O), processor (CPU), network traffic and other indicators at least one of . Analyzing the monitoring task to obtain the target monitoring index may be analyzing the monitoring task, extracting task information in the monitoring task, and determining the target monitoring index according to the task information.
[0092] Step S202: Obtain an indicator identifier corresponding to the target monitoring indicator.
[0093] It should be noted that the in...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com