Longitudinal federated learning backdoor defense method based on neuron activation value clustering
A neuron and activation value technology, applied in the privacy and security field of product recommendation, can solve the problems of decreased accuracy of product recommendation tasks, inability to defend against backdoor attacks, inability to balance backdoor defense performance and recommended task performance, etc. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0044] In order to make the objects, technical solutions and advantages of the present invention, the present invention will be further described below with reference to the accompanying drawings and examples. It will be appreciated that the specific embodiments described herein are intended to explain the present invention and does not limit the scope of the invention.
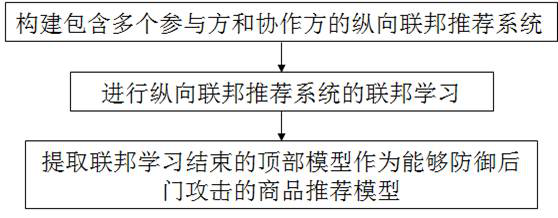
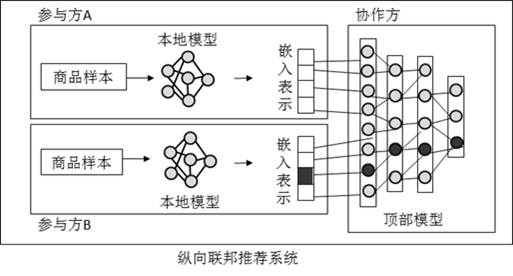
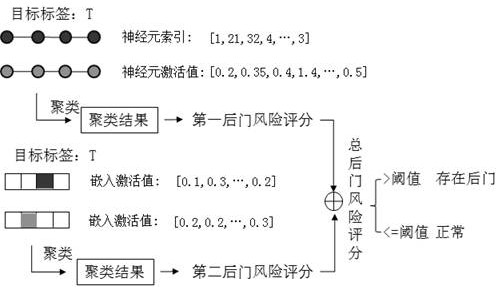
[0045] In view of how to protect the model security issues in longitudinal federal learning, given a valid defensive method in view of the risks of the longitudinal federal recommendation system in business scenes. The present invention aims to propose longitudinal federal learning latte defense based on neuronal activation value clustering from the perspective of the longitudinal federated recommendation system, specific technical concept is: lattime attacks initiated by the initiative and passive in portrait federal recommendation system In the end, it will show the effect of injection of the back door, in part...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com