A decentralized encryption system for the Internet of Things
An encryption system and decentralized technology, applied in the field of Internet of Things, can solve the problem of insufficient security, and achieve the effect of increasing difficulty and improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
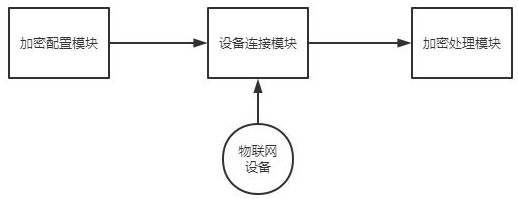
[0036] This embodiment provides a decentralized encryption system for the Internet of Things, combined with figure 1 , including an encryption configuration module, a device connection module and an encryption processing module, the device connection module is used to form a pair with the IoT device and enable communication between each device and the encryption configuration module, and the encryption configuration module is used to manage encrypted data information, the encryption processing module is used to calculate and process the encrypted data information;
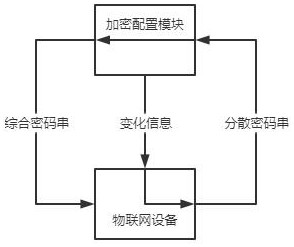
[0037] The encryption configuration module generates a comprehensive password string, and splits the comprehensive password string into several dispersed password strings and sends them to the IoT device respectively. The position in the string gets its device serial number;
[0038] The encryption processing module includes several encryption processing units, each encryption processing unit is set on the IoT dev...
Embodiment 2
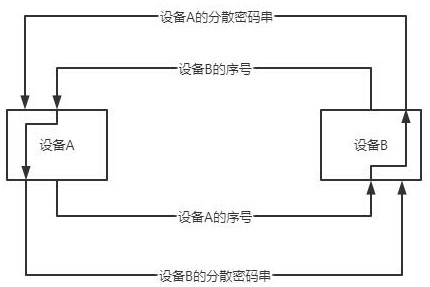
[0057] This embodiment includes all the content of Embodiment 1, and provides a decentralized encryption system for the Internet of Things, including an encryption configuration module, a device connection module, and an encryption processing module, and the device connection module is used to communicate with Internet of Things devices forming a pair, and saving encryption-related data information, the encryption configuration module is used to manage the encrypted data information, and the encryption processing module is used to calculate and process the encrypted data information;
[0058] The encryption configuration module generates a string of character strings according to the number n of connected IoT devices, which is called a comprehensive password string, and then sends part of the character strings in the comprehensive password string to the IoT devices, each IoT The length of the character string obtained by the device is s, and the character string is called a dis...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com