Digital fingerprint processing and signature processing method and device, and storage medium
A technology of digital fingerprint and processing method, which is applied in the direction of electrical digital data processing, digital data protection, instruments, etc., and can solve problems such as insufficient security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example ;
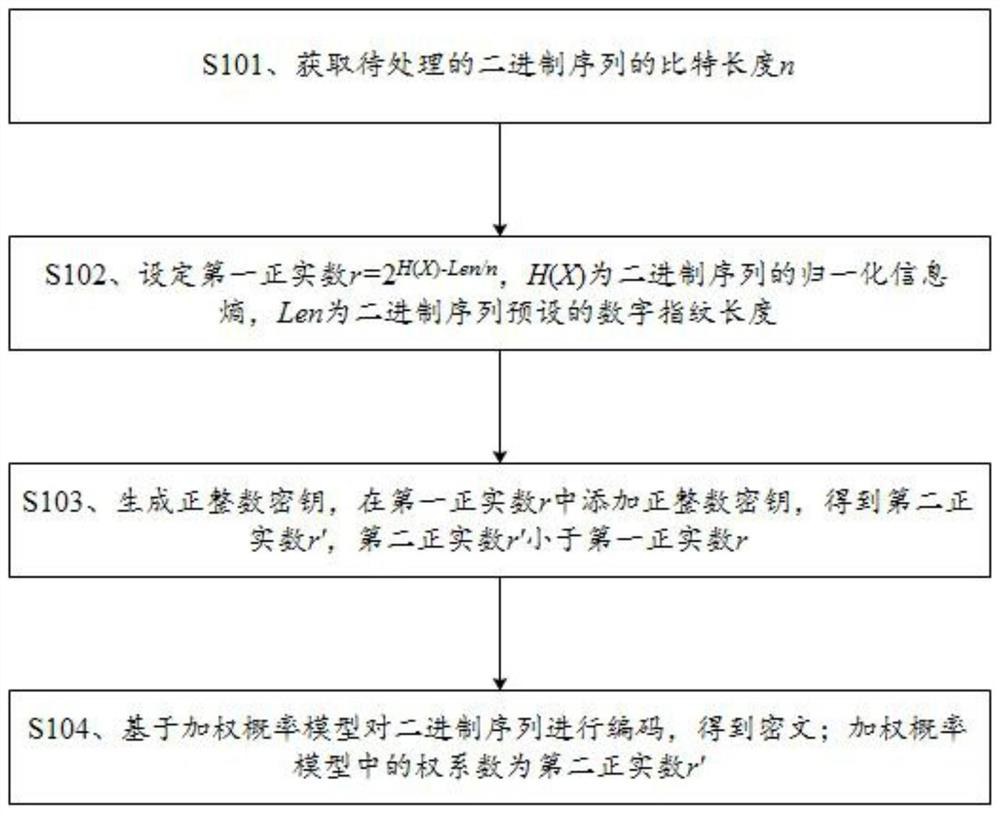
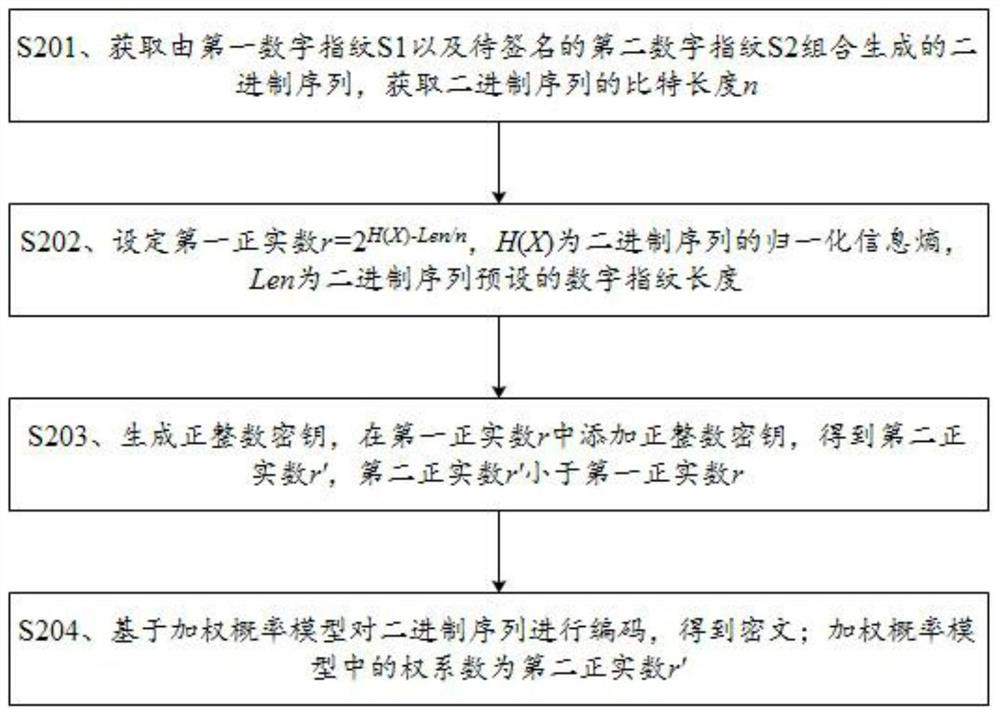
[0062] refer to figure 1 , one embodiment of the present invention provides a kind of digital fingerprint processing method, comprises the following steps:
[0063] S101. Obtain the bit length n of the binary sequence to be processed;
[0064] S102, setting the first positive real number r=2 H(X)-Len / n , H(X) is the normalized information entropy of the binary sequence, and Len is the preset digital fingerprint length of the binary sequence;
[0065] S103. Generate a positive integer key, and add a positive integer key to the first positive real number r to obtain a second positive real number r', where the second positive real number r' is smaller than the first positive real number r;
[0066] S104. Encode the binary sequence based on the weighted probability model to obtain the ciphertext; the weight coefficient in the weighted probability model is the second positive real number r′.
[0067] The coding process based on the weighted probability model in step S104 is as f...
no. 2 example ;
[0085] In order to make it easier for those skilled in the art to understand this solution, based on the first embodiment, an example of an actual application scenario is provided:
[0086] If the method of the first embodiment is applied to the smart door lock, the diversity of the lock cylinder can reach 480 million times, that is, there are 480 million different lock cylinders.
[0087] Assume that a company has purchased multiple smart door locks of the same brand and installed them in various places in the company. If the same password is set for the convenience of remembering the password, if someone cracks it, it will be found that the hash value stored inside is all In the same way, it can be deduced that multiple combination locks use the same password, and it is easy to break the whole ending. Its solution can only be that the user sets different passwords for each door lock, which is inconvenient for the user to manage passwords and also easily forgets the passwords...
no. 3 example ;
[0090] The solution of the first embodiment can be applied in multiple scenarios such as security encryption, unique identification, data verification, hash function, load balancing, and distributed caching. People's daily user password encryption usually uses hash functions such as MD5 and SHA. Because it is irreversible, using the method of the first embodiment can make small differences in dynamic encryption and the result after encryption is very different, so the security is better. it is good.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com