Generating sequence of network data while preventing acquisition or manipulation of temporal data
A technology of time data and data, applied in the direction of digital data protection, electronic digital data processing, homomorphic encryption communication, etc., to achieve the effect of preventing fraud, protecting user privacy, and preventing fraudulent manipulation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
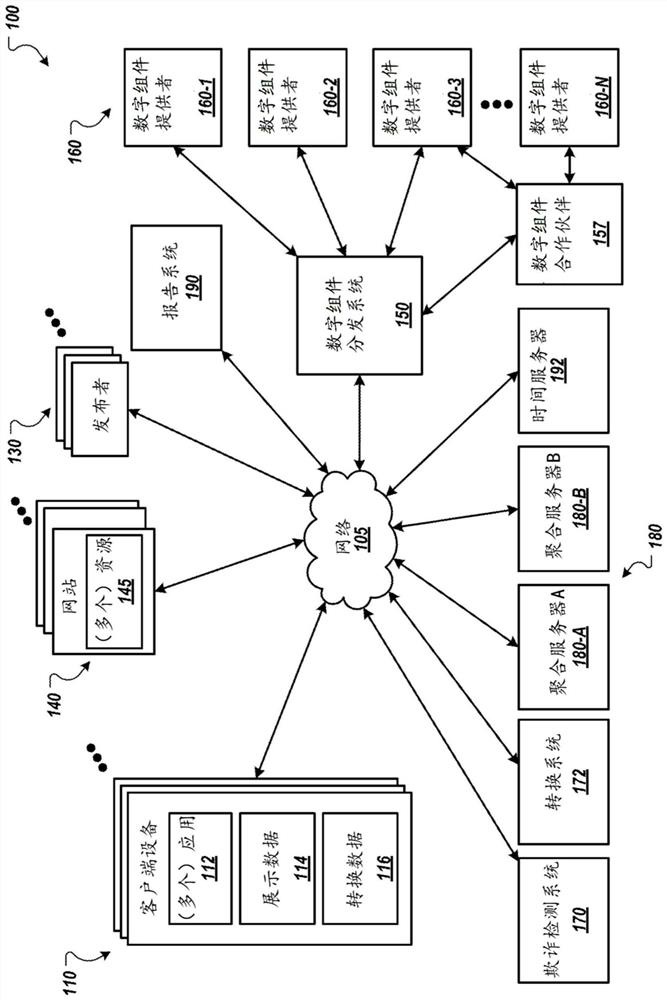
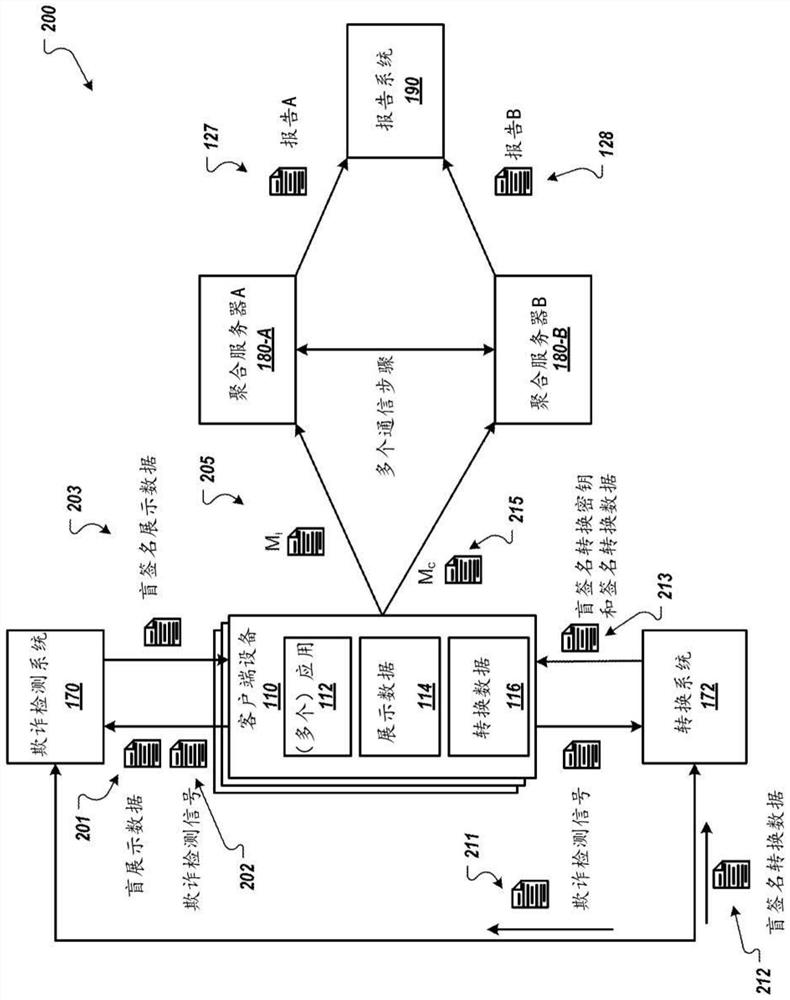
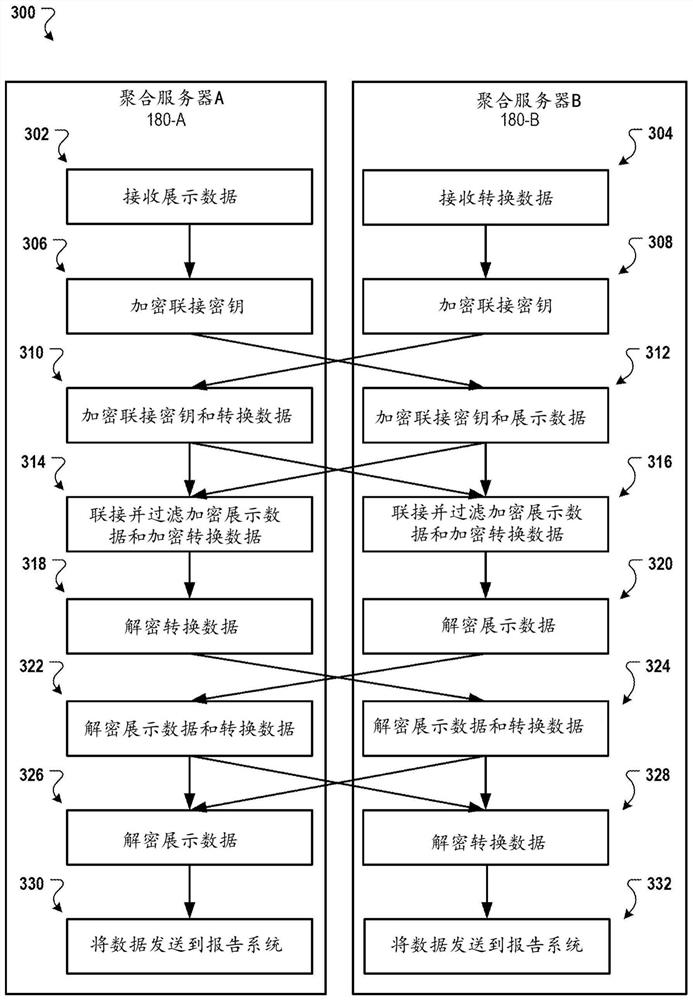
[0027] In general, this document describes cryptographic techniques used to prevent fraud when determining event levels and aggregating network measurements. For example, the technology described in this document prevents fraud when determining event levels and aggregate impressions and conversion measurements across digital components used for various types of conversions. The cryptography techniques described in this document may also protect user privacy, for example, by preventing all entities from being able to track or aggregate user data received from a user's client device.
[0028] System Overview
[0029] figure 1 is a block diagram of an example environment 100 in which an aggregation server 180 determines aggregated network measurements. The example environment 100 includes a data communications network 105, such as a local area network (LAN), a wide area network (WAN), the Internet, a mobile network, or combinations thereof. Network 105 connects client device...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com