Security enhancement processing method for embedded security module
A security module and processing method technology, applied in the direction of electrical digital data processing, computer security devices, instruments, etc., can solve problems affecting the security of transmitted data, user experience, data leakage, etc., to reduce the probability and traceability of abnormal situations strong effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
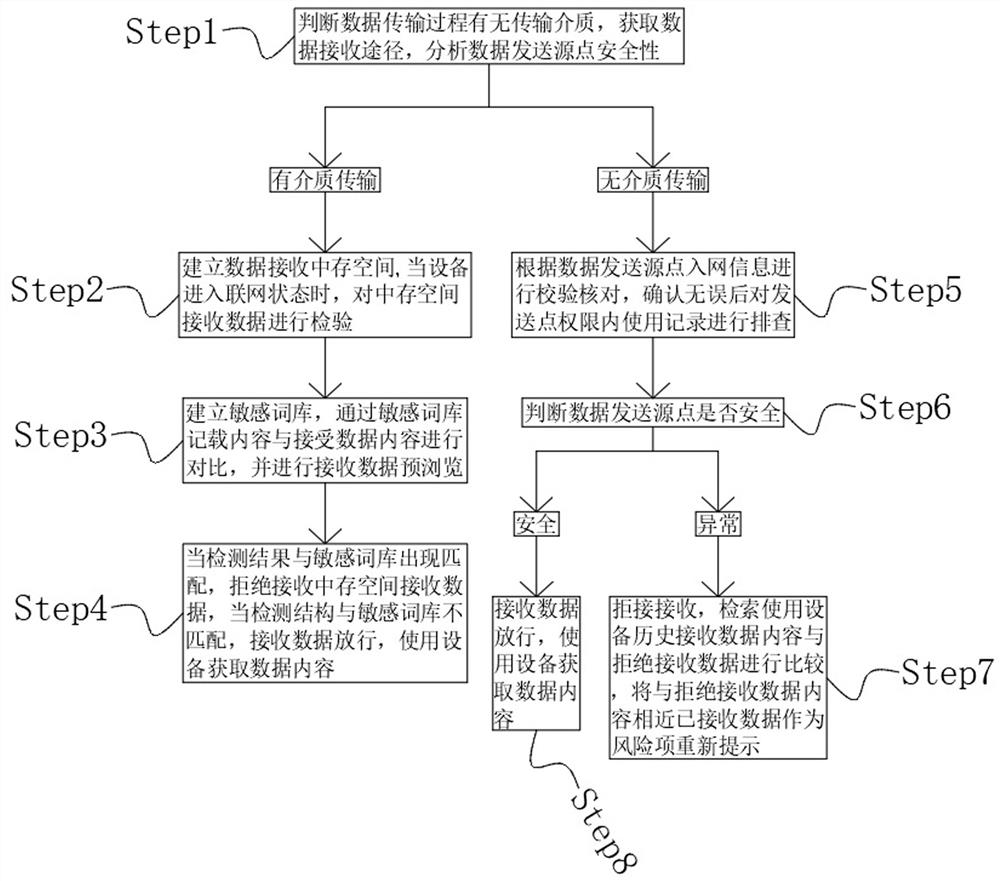
[0046] A security enhancement processing method of an embedded security module in this embodiment, such as figure 1 shown, including the following steps:
[0047] Step1: Determine whether there is a transmission medium in the data transmission process, obtain the data receiving path, and analyze the security of the data sending source;
[0048] Step2: When the data transmission adopts the medium transmission method, establish the data receiving storage space, and when the device enters the network state, check the data received in the storage space;
[0049] Step3: Establish a sensitive thesaurus, compare the content recorded in the sensitive thesaurus with the content of the received data, and perform a pre-browsing of the received data;
[0050] Step4: When the detection result matches the sensitive lexicon, refuse to receive the data received in the storage space; when the detection structure does not match the sensitive lexicon, the received data is released, and the devi...
Embodiment 2
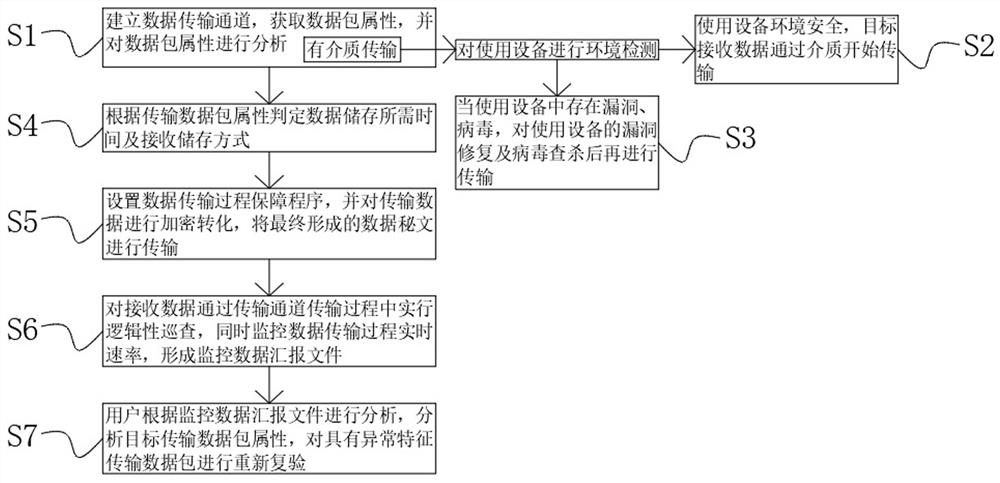
[0064] At the level of specific implementation, the present invention provides a security enhancement processing method for the use state of an embedded security module, comprising the following steps:
[0065] S1: Establish a data transmission channel, obtain data packet attributes, and analyze the data packet attributes;
[0066] S2: When the data transmission channel is transmitted by a medium, the transmission environment of the equipment is safe, and the data received by the target starts to transmit through the medium;
[0067] S3: When the data transmission channel is transmitted by a medium, and there are loopholes or viruses in the transmission environment of the equipment used, the loopholes of the equipment used are repaired and the virus is checked and killed before transmission;
[0068] S4: Determine the time required for data storage and the receiving and storing method according to the attributes of the transmitted data package;
[0069] S5: Set up the data tr...
Embodiment 3
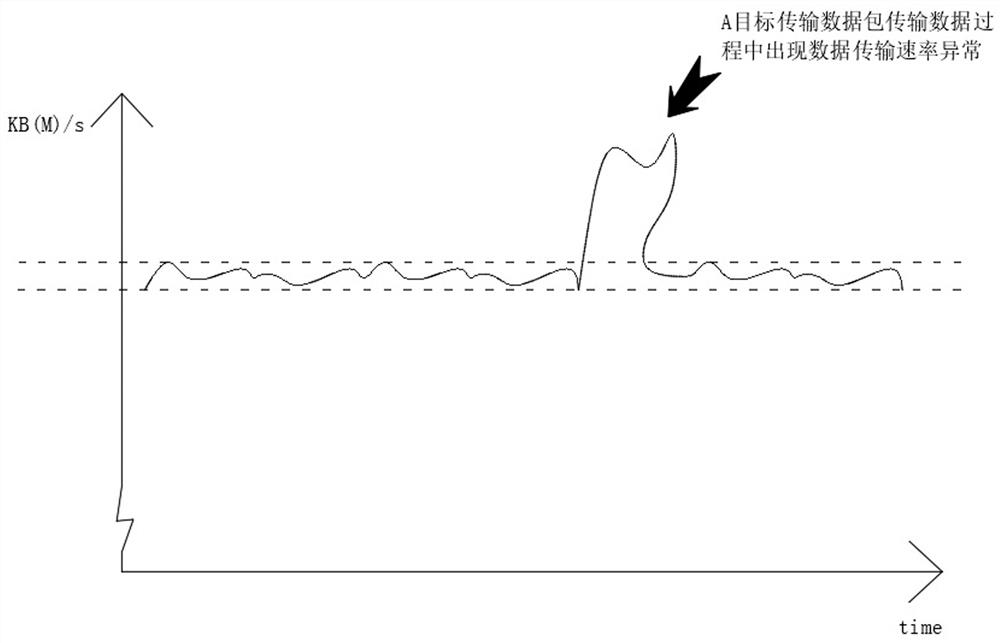
[0080] Such as image 3 , 4 and 5, with Figure 5 It can be obtained that there is no Zip format file in the transfer target A, and the transfer target B contains the Zip format file. During the transfer process of both, the transfer rate is abnormal, because there is no Zip format file in A, and the file in B contains For files in Zip format, it can be preliminarily determined that the abnormal rate in B may be caused by the impact of the Zip file, so the abnormal rate in A can be confirmed as abnormal.
[0081] To sum up, the present invention provides a more targeted security enhancement processing method for the use of embedded security modules. This method can distinguish the methods used in the data storage process, and the transmission with medium transmission and without medium transmission is highly secure. It has strong traceability for abnormal situations in transmission without medium, and compared with the transmission with medium, it has enhanced security prote...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com