Network security assessment method and device, network security equipment and storage medium
A network security assessment and network security technology, which is applied in the field of network security equipment and storage media, and network security assessment, can solve the problems of consuming manpower and material resources, being unable to accurately determine the source and type of external threats, and deviations in security event analysis results.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0026] In order to make the purpose, technical solutions and advantages of the embodiments of the present application clearer, the technical solutions in the embodiments of the present application will be clearly and completely described below in conjunction with the drawings in the embodiments of the present application.
[0027] Any number of elements in the drawings is for illustration rather than limitation, and any designation is for distinction only and has no limiting meaning.
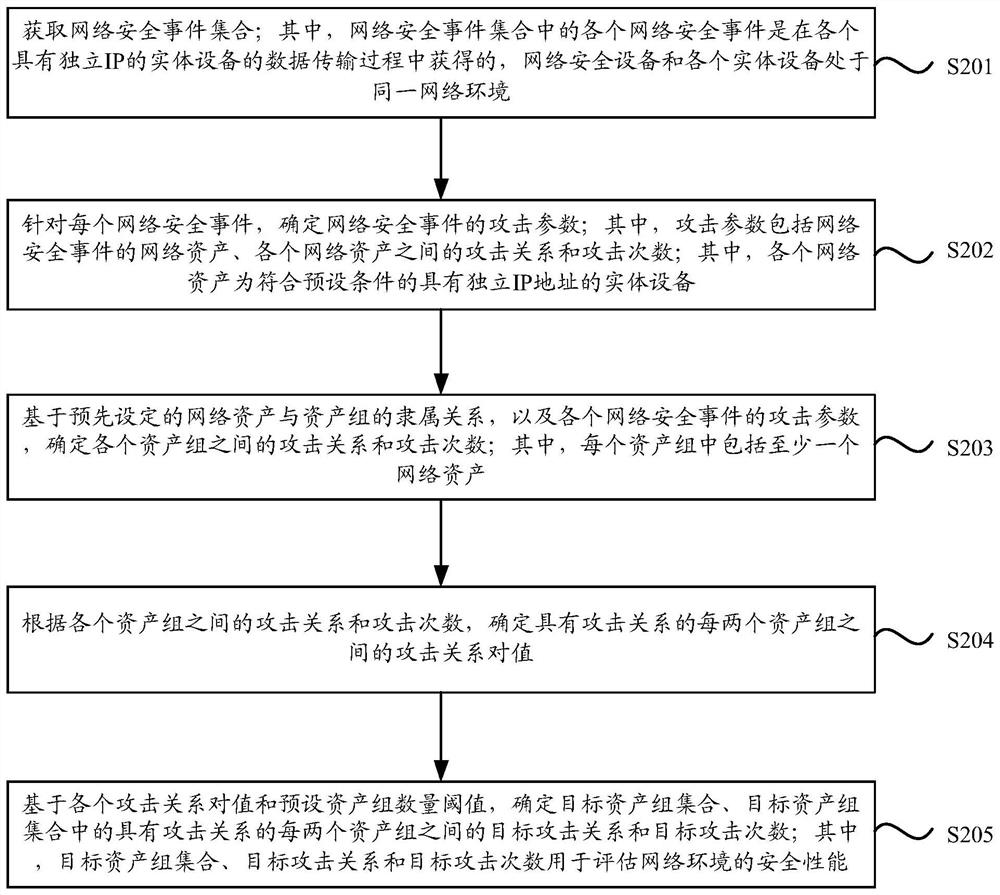
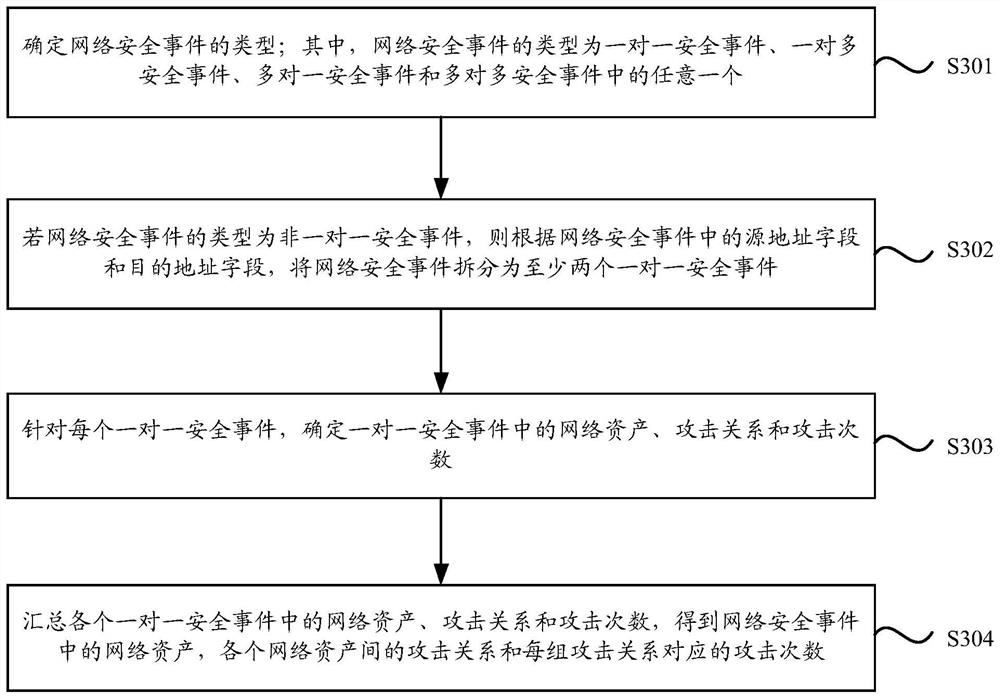
[0028] In practice, the threats inside the network where each network asset is located mainly include bots, worms, scanning and detection, and login with weak passwords. In related technologies, when faced with security events caused by the above-mentioned threats, operation and maintenance personnel usually respond and handle them according to their own understanding, such as analyzing log events. However, on the one hand, it consumes manpower and material resources. On the other hand, due to t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com