Trusted archive system based on block chain
A file system and blockchain technology, applied in the field of trusted file systems, can solve the problems of people's livelihood file management and trusted sharing, and achieve the effect of reducing storage costs, taking into account privacy management and control, and reducing storage space.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
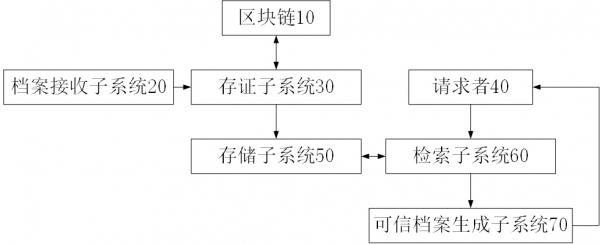
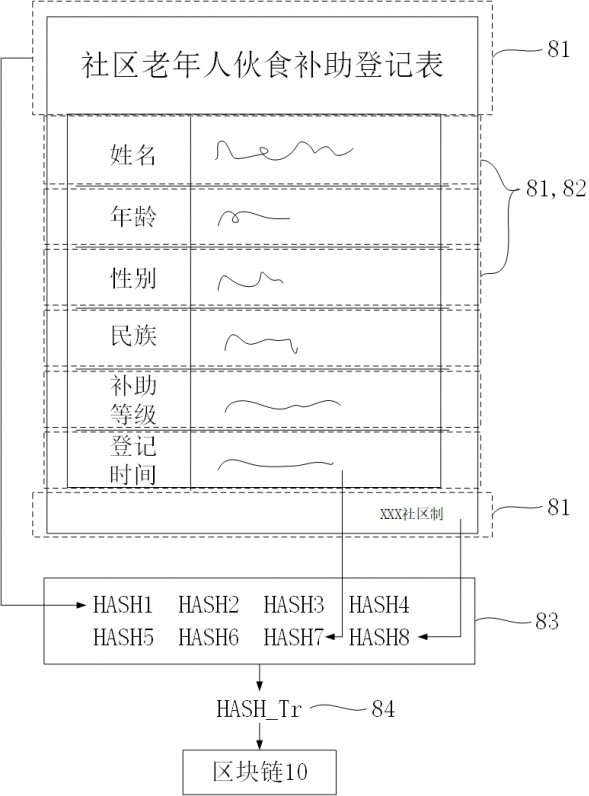
[0027] A blockchain-based trusted archive system, see appendix figure 1 , including a file receiving subsystem 20, a deposit subsystem 30, a storage subsystem 50, a retrieval subsystem 60 and a credible file generating subsystem 70, the file receiving subsystem 20 receives file scans and file description information, and the file description information includes File source department, file type and generation time, copy the scanned copy of the file as a copy, add a preset watermark on the copy, the storage subsystem 30 extracts the hash value of the scanned file as the file hash value, and extracts the hash of the copy The value is recorded as the copy hash value 84, and the file hash value and the copy hash value 84 are uploaded to the block chain 10 for storage, and the corresponding block height is obtained. The storage subsystem 50 assigns and stores the file name for the scanned copy of the file and the copy, The retrieval subsystem 60 establishes a file directory, and t...
Embodiment 2
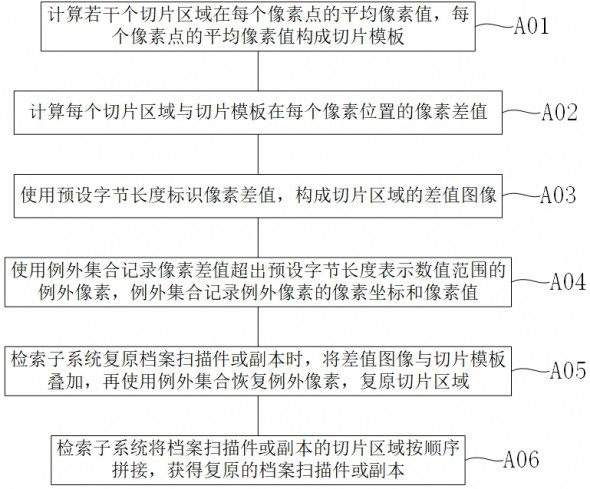
[0052] A trusted file system based on blockchain. This embodiment proposes a further solution for file sharing on the basis of Embodiment 1. Please refer to the attached Figure 5 , the method for sharing files in this embodiment includes: step B01) the retrieval subsystem 60 stores a list of items, and the list of items records the set of field names required for handling each item; step B02) the file access request includes multiple required file types , after the retrieval subsystem 60 finds a plurality of matched file scans, it lists all the fields that need to be provided according to the item list, and obtains the slice area 81 corresponding to the field; step B03) according to the file scans to which the slice area 81 belongs, from the storage sub-system The system 50 reads multiple slice areas 81; step B04) the retrieval subsystem 60 sends the read multiple slice areas 81 and slice hash value sets 83 to the trusted file generation subsystem 70; step B05) trusted file T...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com