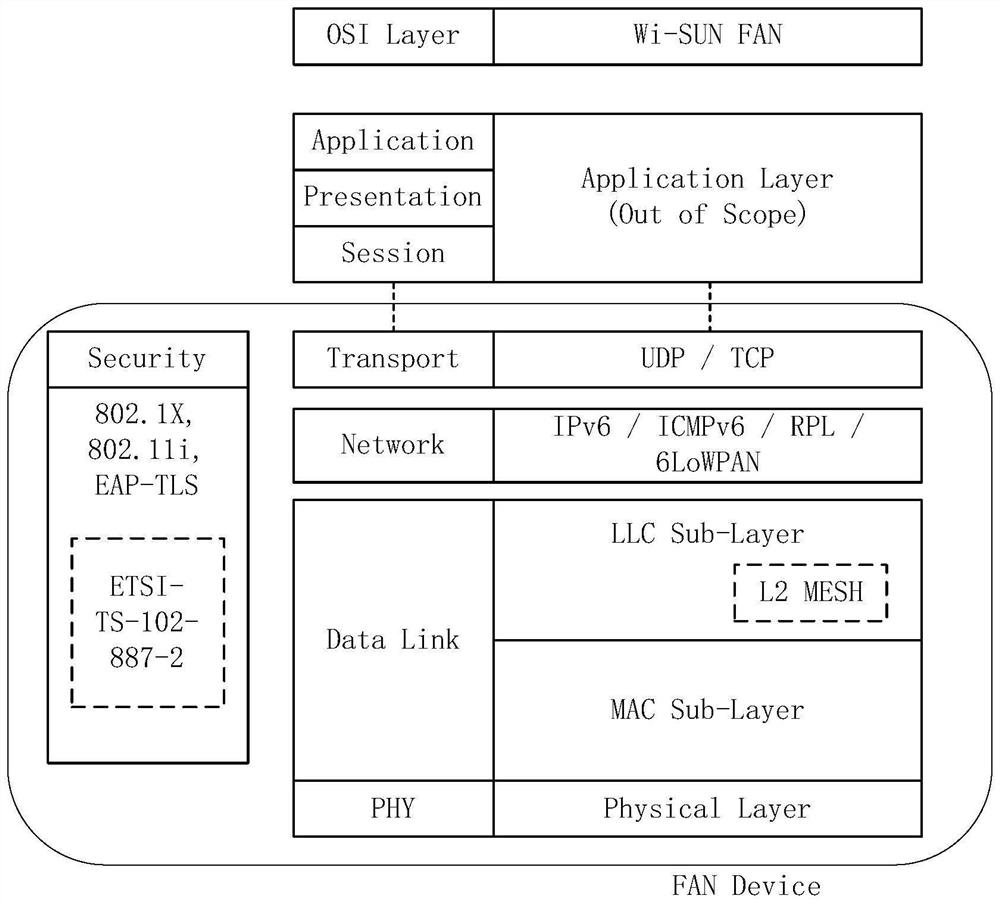
Access encryption verification method and device based on wi-sun network and electronic equipment
A wi-sun and verification method technology, applied in safety devices, electrical components, wireless communication, etc., can solve problems such as insufficient safety, and achieve the effect of improving safety and reducing safety risks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
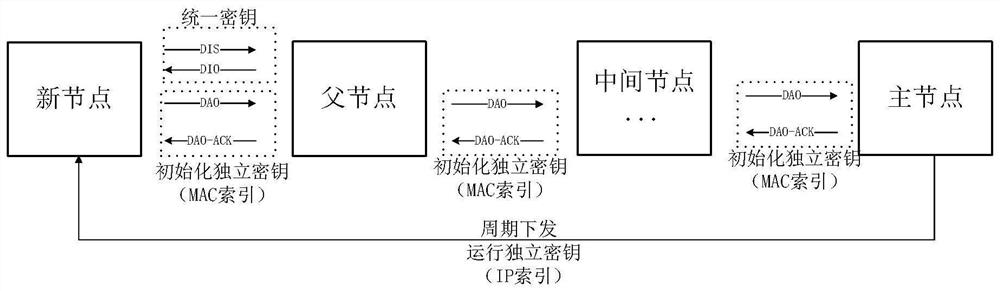
[0042] In order to solve the problems existing in the existing technology, such as image 3 As shown, the present invention provides a kind of access encryption verification method based on wi-sun network, comprising:
[0043] Nodes in the entire edge network store a unified common key, which does not change.
[0044] The newly joined node and the root node of the edge network store an initialization independent key indexed by the MAC of the newly joined node, which is generated by the installer and injected into the newly joined node and the root node.
[0045] When a newly joined node joins the edge network, it uses a unified common key to encrypt the DIS message and decrypt the DIO message to determine the parent node of the newly joined node;
[0046] The root node sends the pre-stored initialization independent key with the MAC index of the newly added node to each node on the downlink path, including the parent node of the newly added node and the nodes on the uplink pa...
Embodiment 2
[0051] In the embodiment of the present invention, the new node access process is described in detail, including:
[0052] (1) It is necessary to store a unified general key and a special initialization independent key in the newly added node, and at the same time, enter the initialization independent key into the root node of the edge network, with the MAC value as the index.
[0053] Specifically, the nodes in the entire edge network store a unified common key, which does not change; the newly joined node and the root node of the edge network store an initial independent key indexed by the MAC of the newly joined node, and this key The key is generated by the installer and injected into the newly added node and the root node;
[0054] (2) When a newly joined node joins the edge network, it first encrypts the DIS message with the unified common key and sends it to its adjacent neighbor nodes; after the neighbor nodes receive the message, they use the same common key of the ed...
Embodiment 3
[0062] In the embodiment of the present invention, the process of node sending and receiving data is described in detail:
[0063] (1) When a node sends a message, it encrypts the application layer of the message with its own running independent key, and forwards it to the root node by the uplink route.
[0064] (2) After receiving the message, the root node finds the stored running independent key of the sender node according to the source IP of the message, and decrypts the application layer of the message.
[0065] (3) The root node analyzes the destination IP of the message. If it is in the edge network, it uses the corresponding destination IP as an index to find the running independent key of the receiving node, encrypts the application layer of the message, and then according to the downlink route It is sent to the destination node. After the destination node receives it, it finds that the destination IP is itself, and then uses the running independent key stored by its...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com