Network security emergency isolation anti-theft device
A network security and emergency technology, applied in the field of network security, can solve the problems of unfavorable network security protection work convenience and stability, affecting the query of malicious attack sources on the external network, etc., to ensure convenience and stability, strengthen security protection, The effect of protecting data security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
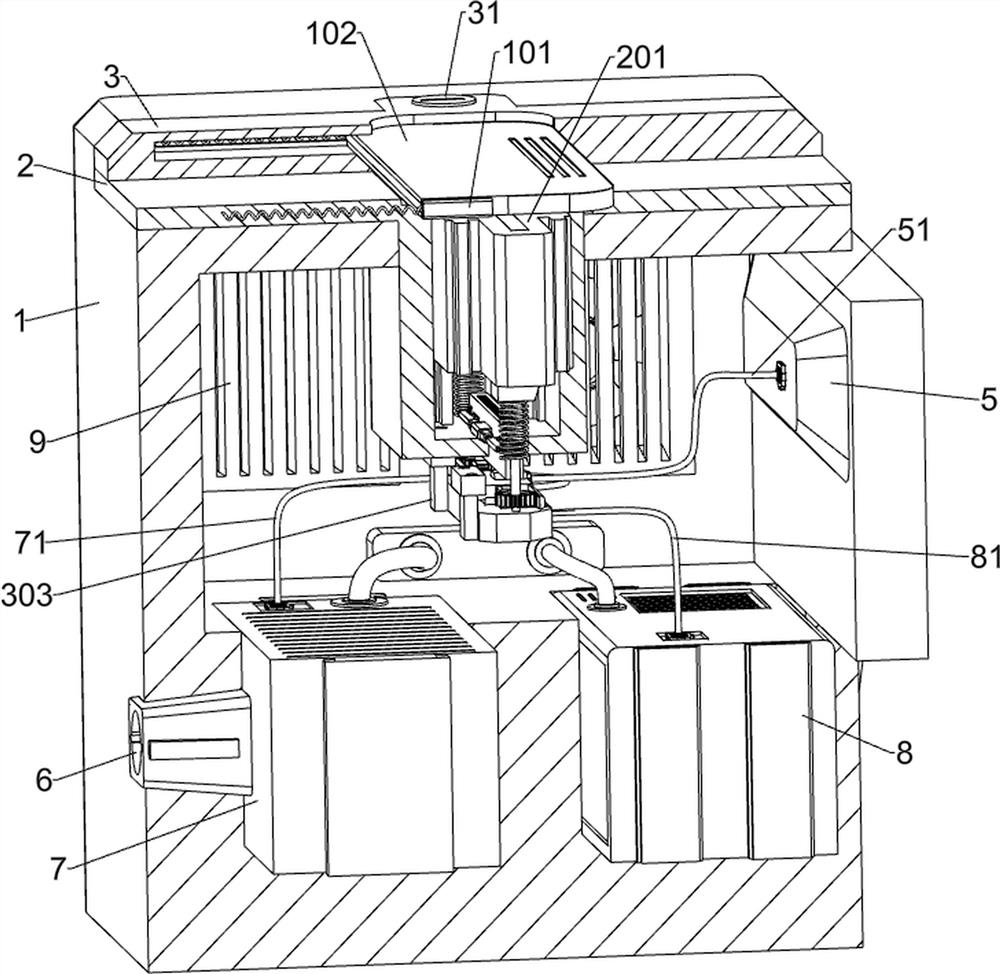
[0028] In the embodiment of the present invention, both the first elastic member 203 and the second elastic member 403 use a spring member, and the telescopic member 309 uses a miniature electric push rod.
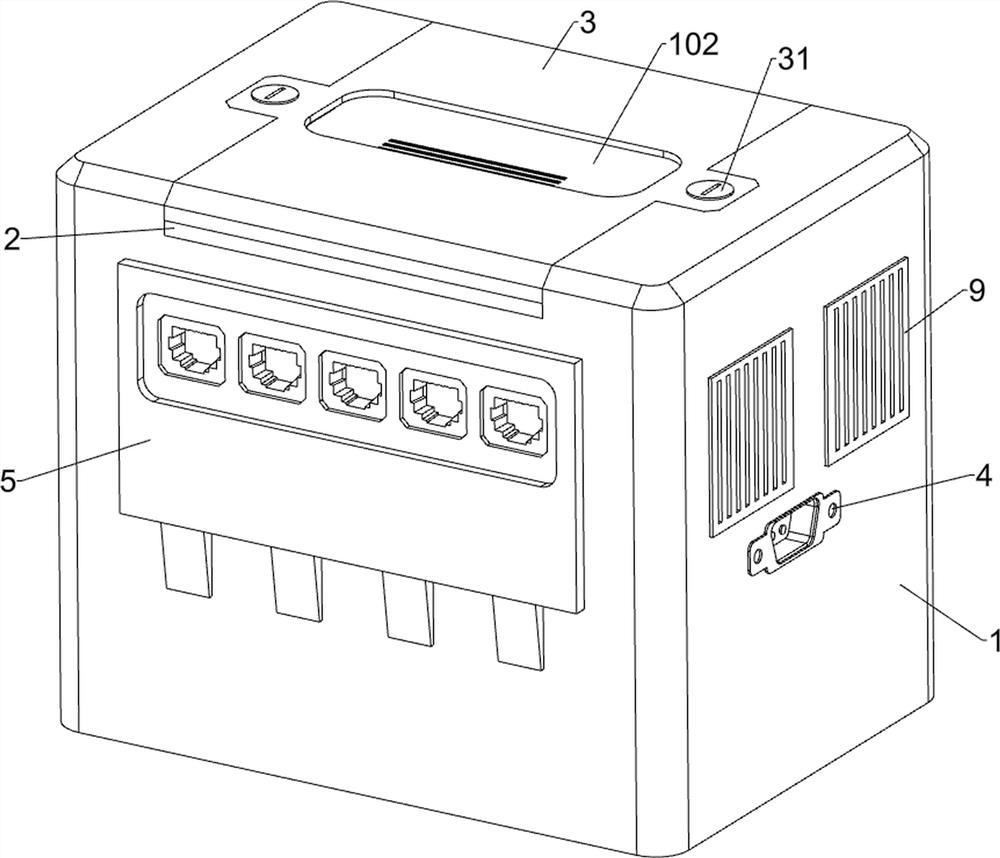
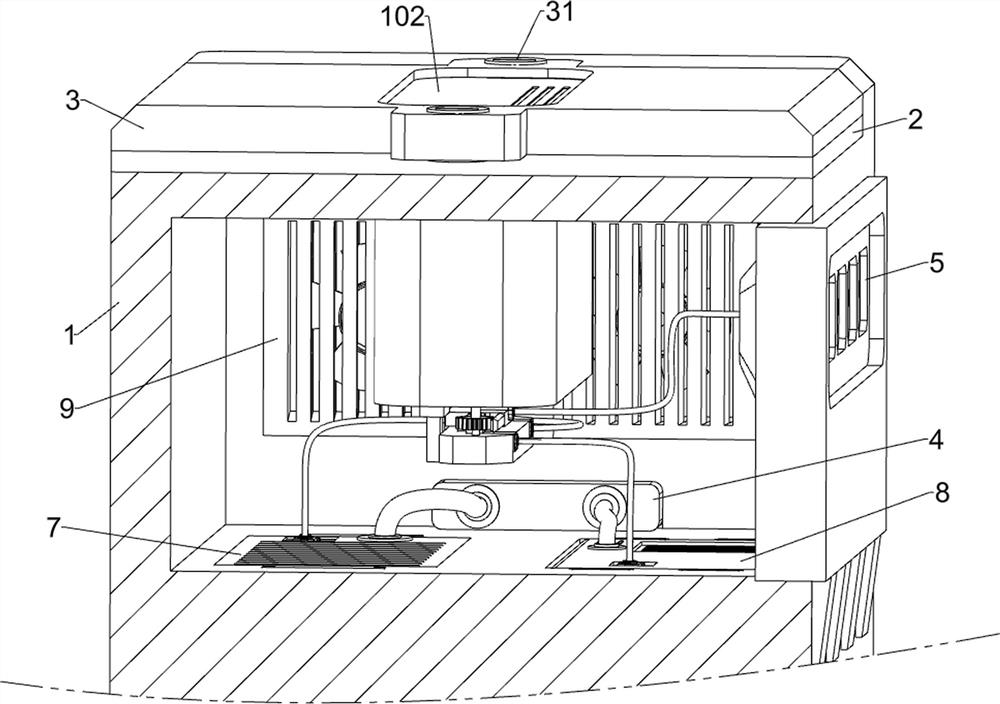
[0029] A network security emergency isolation anti-theft device, such as Figure 1-Figure 9 As shown, it includes a sliding cover unit, a card insertion unit, an isolation and anti-theft unit, a main casing 1, an inner casing 2, a cover plate 3, a safety lock 31, a power supply module 4, an external interface 5, a security interface 6, and an encryption module 7. , the storage module 8, the first cable 51, the second cable 71, the third cable 81 and the heat dissipation module 9; the inner casing 2 is fixed in the middle of the upper side of the main casing 1; the upper side of the main casing 1 passes through two Each safety lock 31 is plugged with a cover plate 3; the right side of the main casing 1 is fixedly connected with a power supply module 4; the front side of the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com