Patents
Literature
863 results about "Outernet" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Outernet is a wireless community network based in Poland, in which everyone owns their own node's hardware configured in a mesh network managed by OLSR. Participants must permit routing of other node's data through their routers, which allows building a large maintenance-free and low-cost network infrastructure which is a personal property of its users.
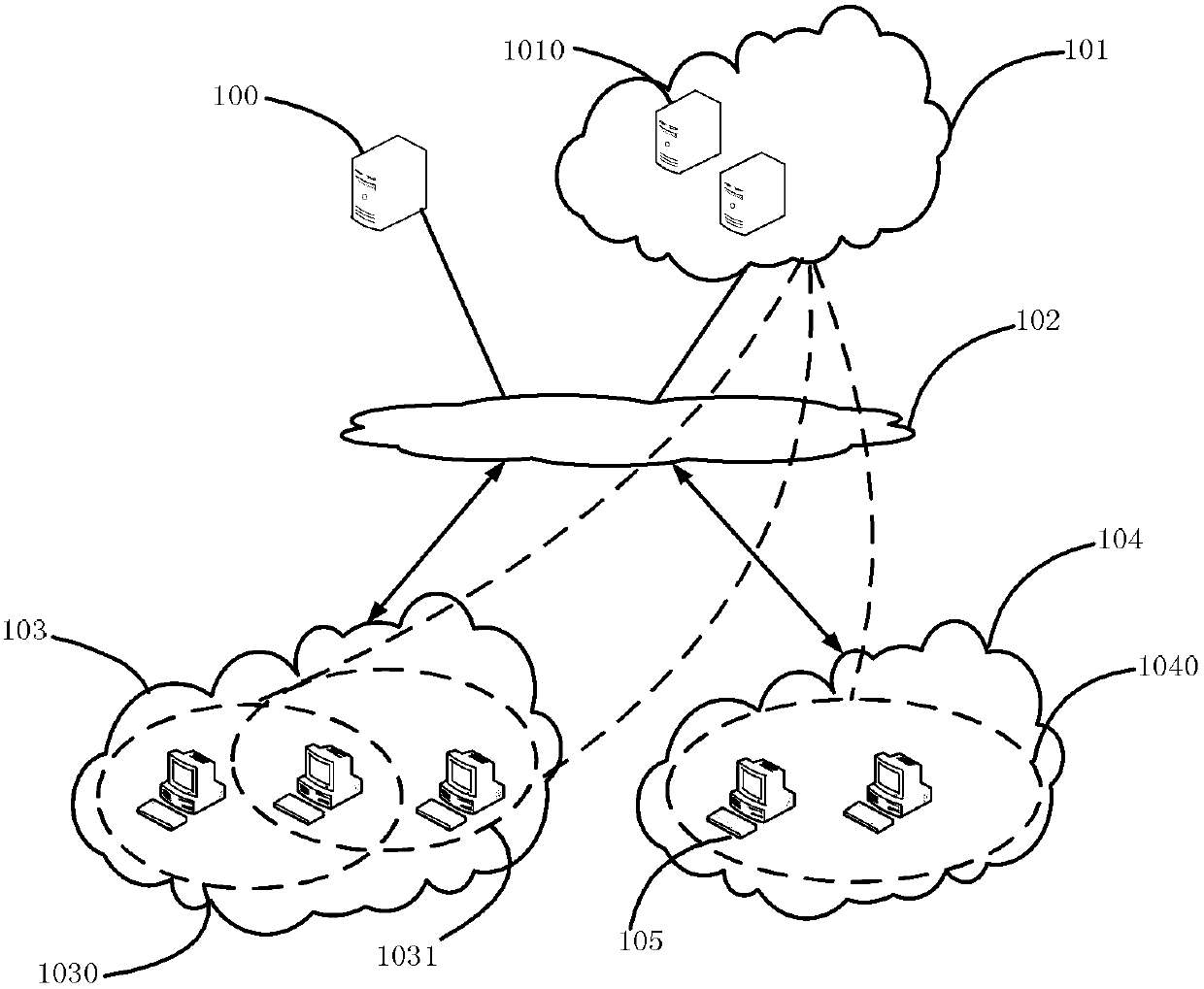
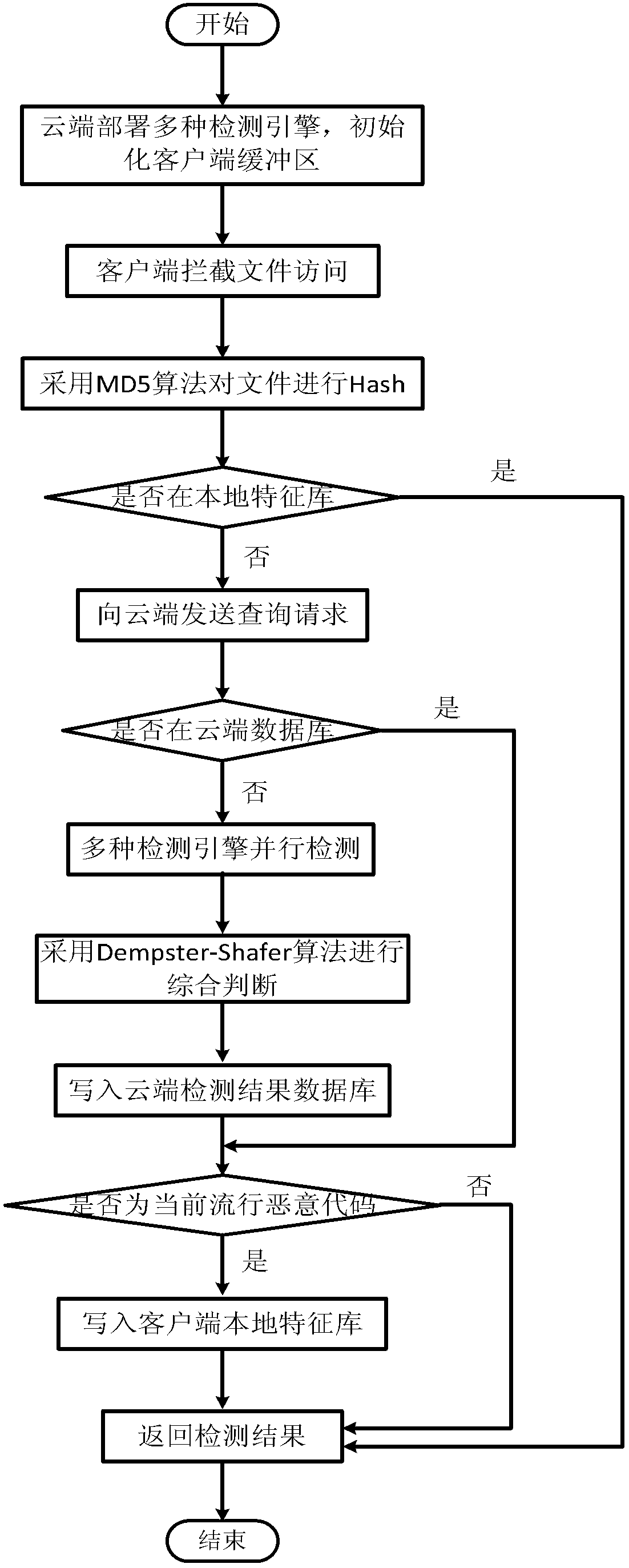
System and method for judging cloud safety malicious program
The invention discloses a system for judging a cloud safety malicious program. The system comprises a cloud terminal, a client, a virtual defending group and a station, wherein light malicious code defending software is installed on the client. A local characteristic base maintains the current prevalent malicious code information and keeps relatively stable scale, so that the performance of the client is improved. The client organizes in the form of a virtual defending group, the cloud terminal distributes malicious risk solving schemes with the virtual defending group as a unit, and group members belonging to the same virtual defending group can interact malicious code information, so that the spending of the client terminal is reduced. According to a cloud safety malicious program judging method based on the system, the working mode thereof includes an online mode and an offline mode. The online mode comprises a series of sub steps, and the client updates the local characteristic base through an extranet or an intranet. In the offline mode, the client synchronizes the local characteristic base through the intranet, and the offline safety of the client is guaranteed.
Owner:SHANGHAI MARITIME UNIVERSITY
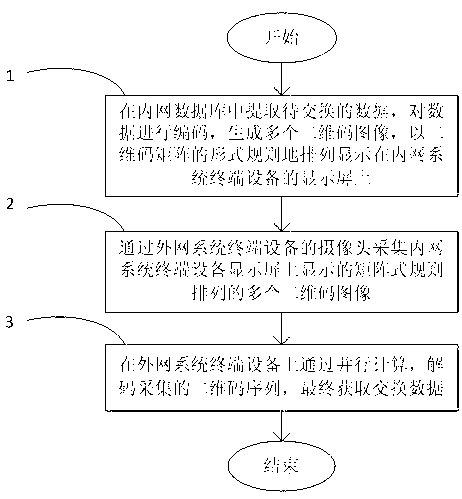
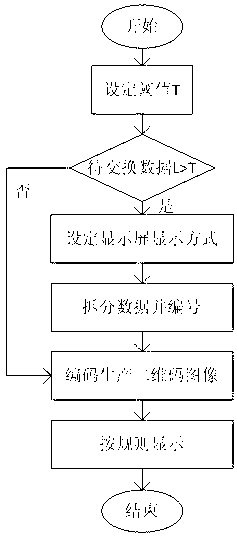
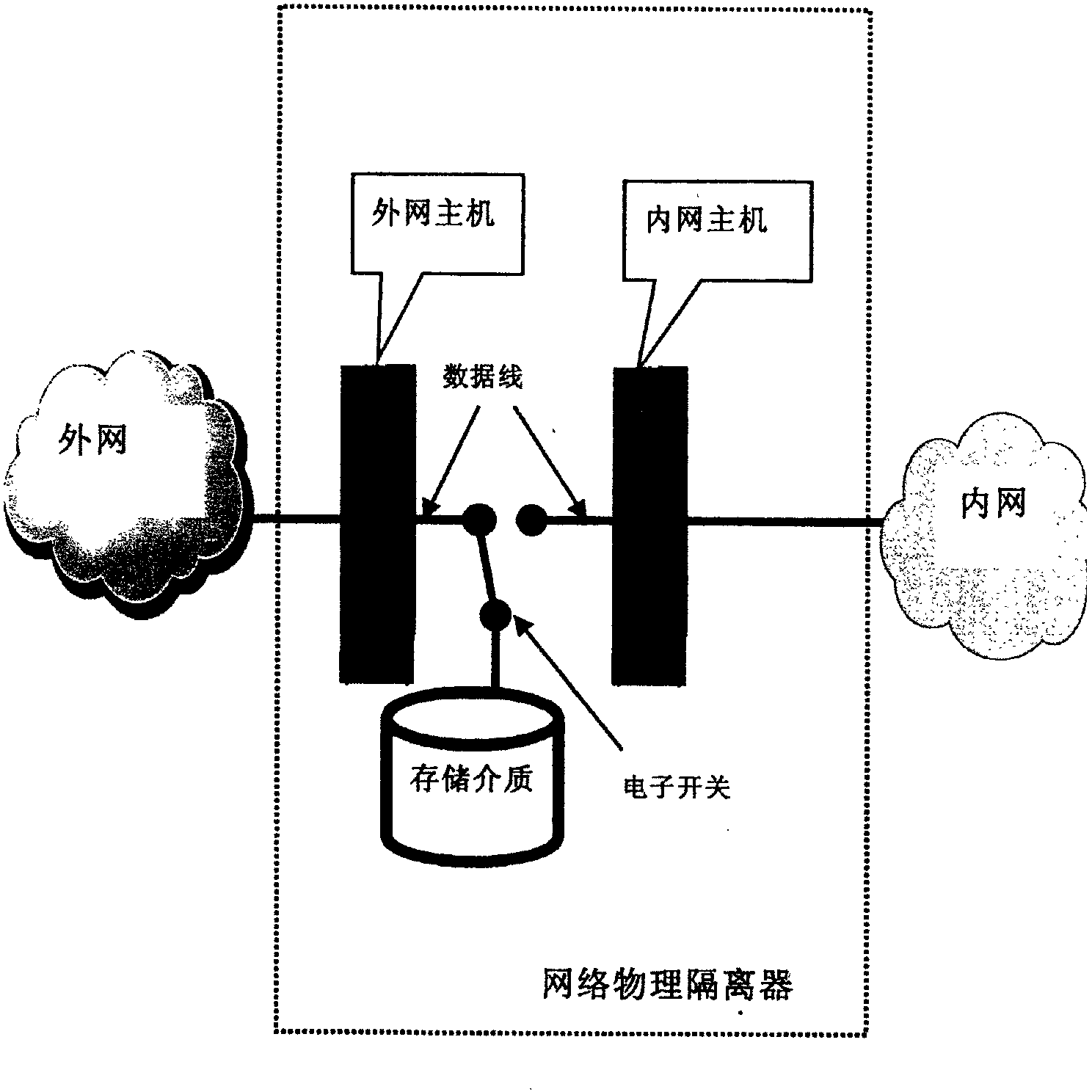
Intranet-extranet physical isolation data exchange method based on QR (quick response) code
InactiveCN103268461AMake up for the high priceMake up for defects such as labor requiredCo-operative working arrangementsInternal/peripheral component protectionParallel algorithmData exchange
The invention discloses an intranet-extranet physical isolation data exchange method based on QR (quick response) code. The method of exchanging data from an intranet to an extranet includes: firstly, extracting data to be exchanged in an intranet database, encoding the data to generate a plurality of QR code images, and regularly arranging and displaying the images on a display screen of intranet system terminal equipment in a form of QR code matrix; secondly, using a camera of extranet system terminal equipment to acquire the matrix-type irregularly arranged QR code images displayed on the display screen of the intranet system terminal equipment; and thirdly decoding acquired QR code sequences by parallel algorithm on the extranet system terminal equipment so as to obtain exchanged data. The method has the advantages that such defects as high precise and need for labor in existing traditional exchange methods of gateway copying or USB (universal serial bus) flash drive copying, the method is high in reliability, high in safety and low in operation and maintenance cost, exchange time is shortened, and efficiency in intranet-extranet data exchange is improved.
Owner:浙江成功软件开发有限公司
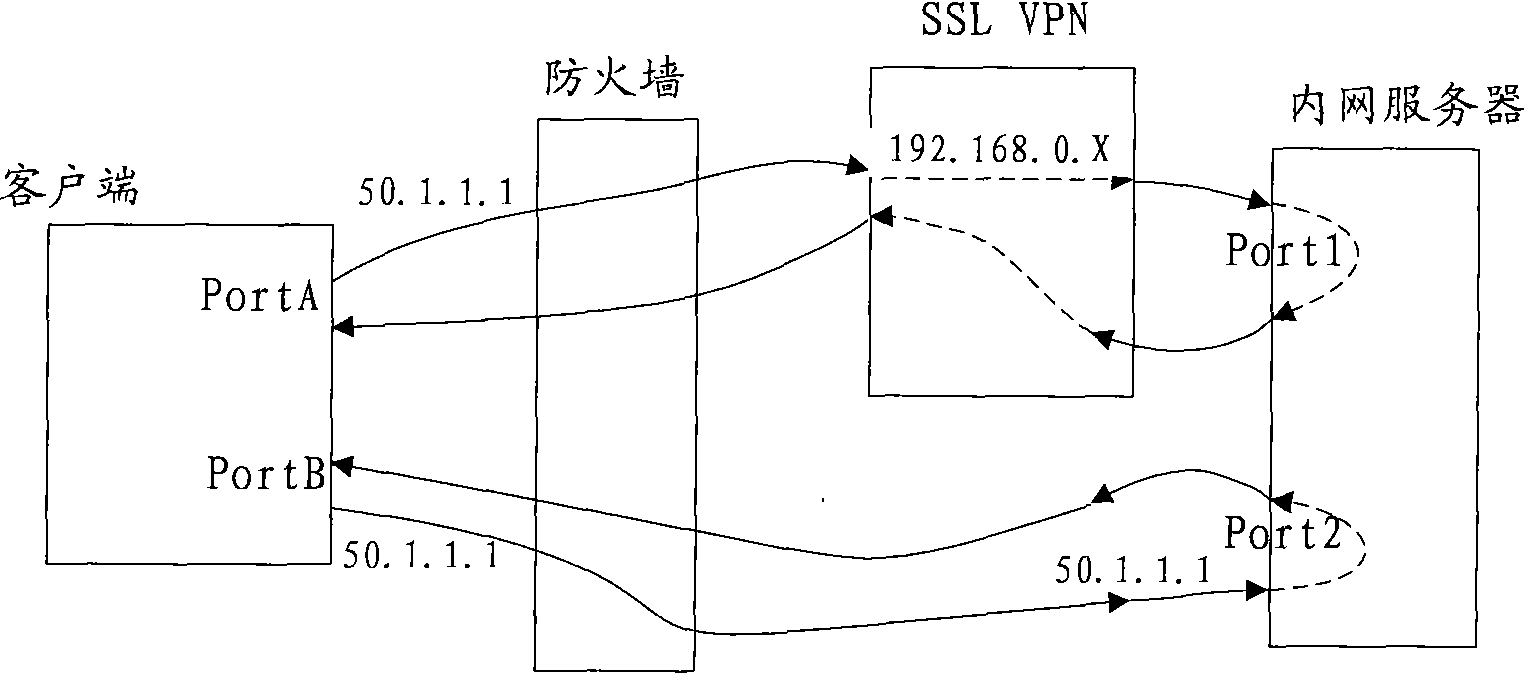
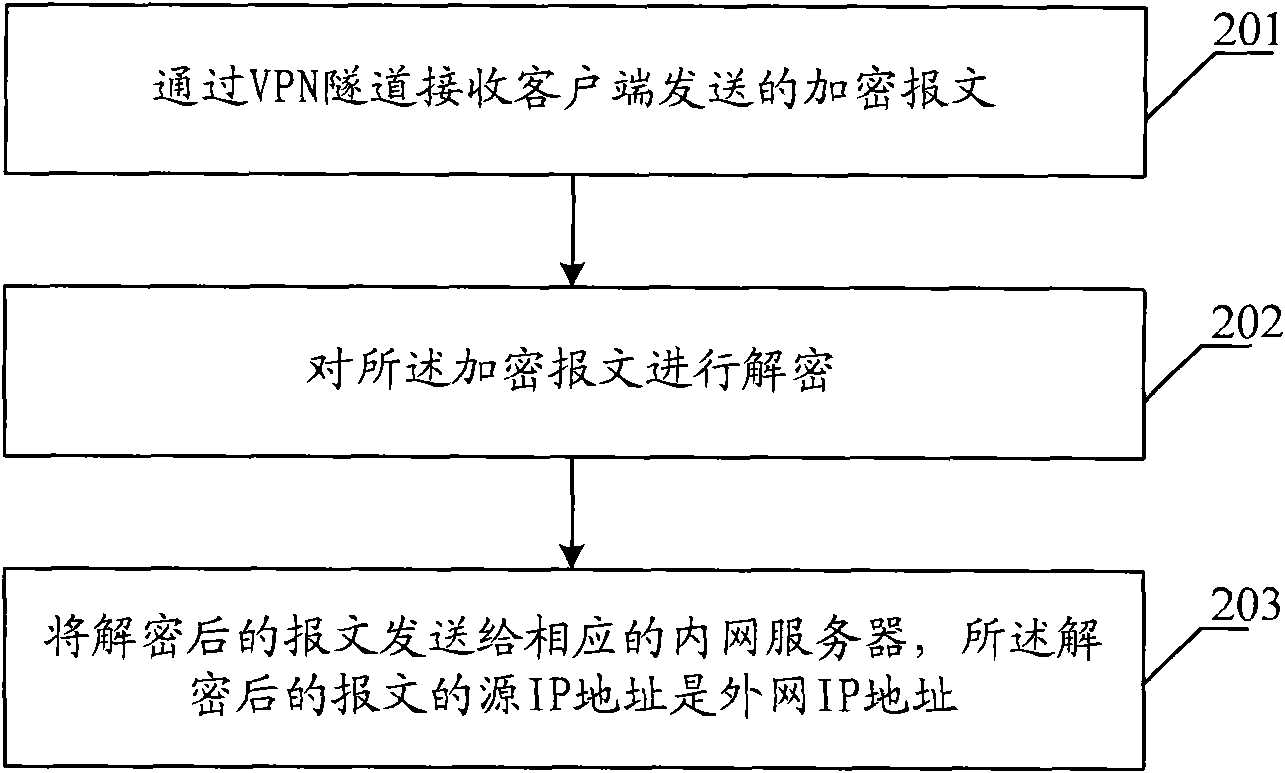
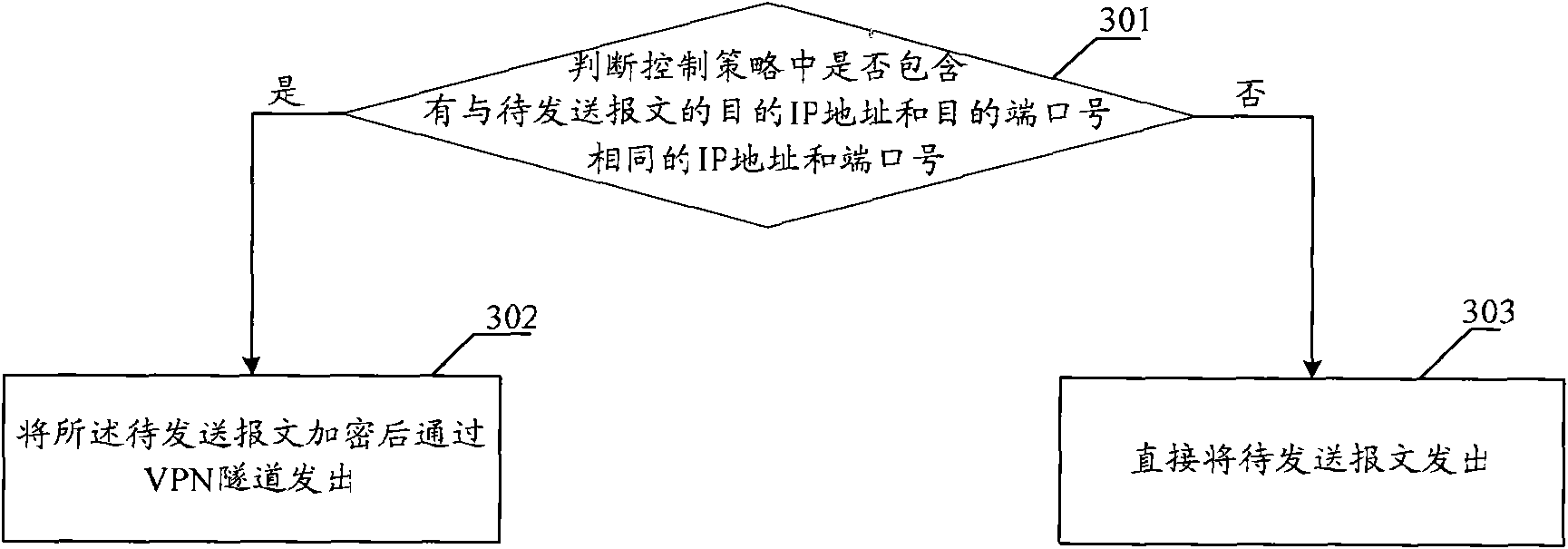
Message transmission method, device and network system
The embodiment of the invention provides a message transmission method, a device and a network system, wherein the message transmission method comprises the following steps of: receiving an encrypted message transmitted by a client through a VPN (Virtual Private Network) tunnel, decrypting the encrypted message and transmitting the decrypted message to a corresponding intranet server, wherein the encrypted message is transmitted by encrypting the message to be transmitted when the client determines that a control strategy comprises an IP address and a port number which are the same with the IP address and the port number of a destination of the message to be transmitted according to the pre-set control strategy; the control strategy comprises the information of the IP address and the port number of the intranet server which can carry out message interaction with a secure socket layer virtual private network (SSLVPN) server; and the source IP address of the decrypted message is an extranet IP address. The message between an intranet and an extranet can be transferred through a secure socket layer virtual private network (SSLVPN) under the condition of unchanging the topology structure of the intranet by utilizing the technical scheme provided by the embodiment of the invention.
Owner:CHENGDU HUAWEI TECH
One-way data exchange device and method for physical isolation among networks at different security levels
InactiveCN102938761ASafe and reliable data exchangeConfidential Data SecurityRecord information storageTransmissionControl systemEngineering
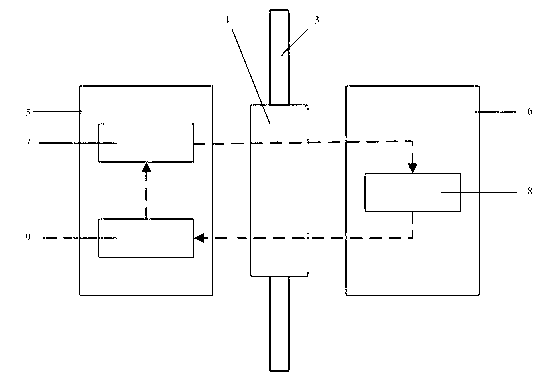
The invention discloses a one-way data exchange device and method for physical isolation among networks at different security levels. The device comprises an intranet processing unit and an extranet processing unit, wherein a transition unit for data exchange is arranged between the intranet processing unit and the extranet processing unit and comprises an intranet optical drive group (namely a burn drive), an extranet optical drive group (namely a read-only drive) and a manipulator assembly. The one-way data exchange device does not need manual intervention and can implement data transfer by virtue of non-direct connection of the manipulator assembly, the specific drive, a control system and a disc shredder (according to selection) so as to achieve the true physical isolation. The one-way data exchange device and method adopt a simple principle, are safe and reliable, prevent various invasive bugs from hiding fundamentally, save time for manual data exchange by disc burning, conveniently implement the safe data exchange, and bring convenience for safe data storage and exchange among secret departments of the Chinese People's Liberation Army and China.
Owner:SUZHOU NETZON INFORMATION STORAGE TECH
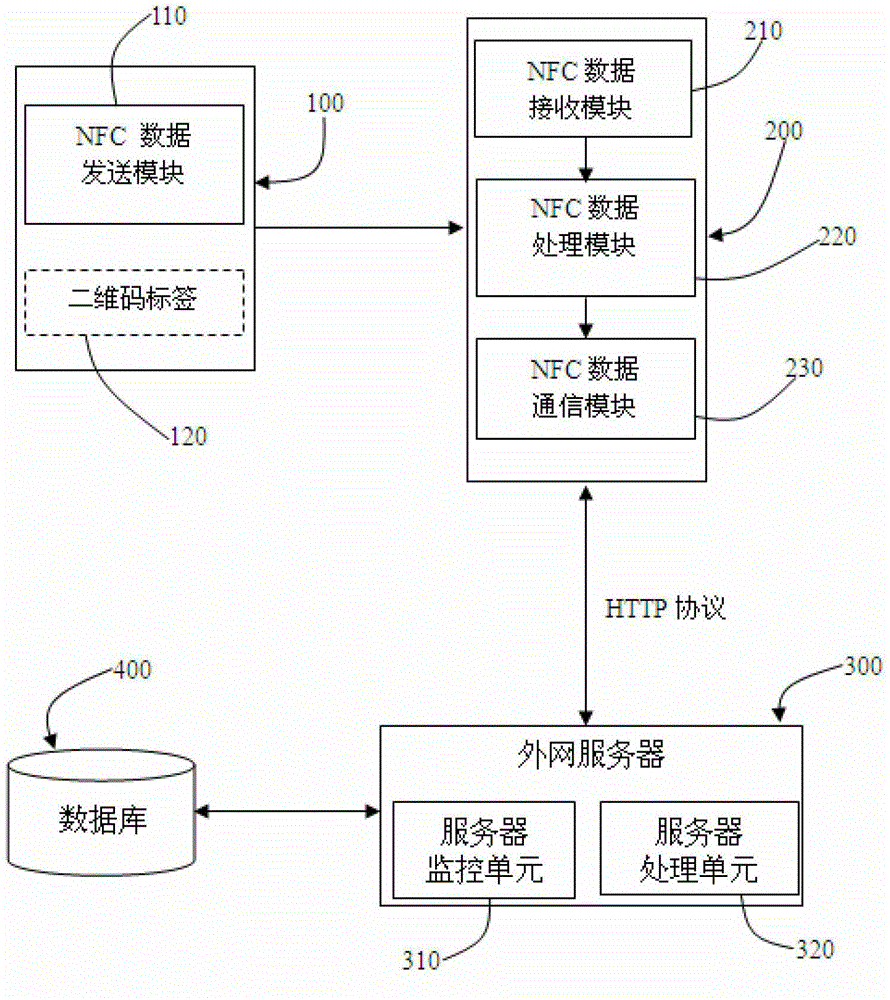
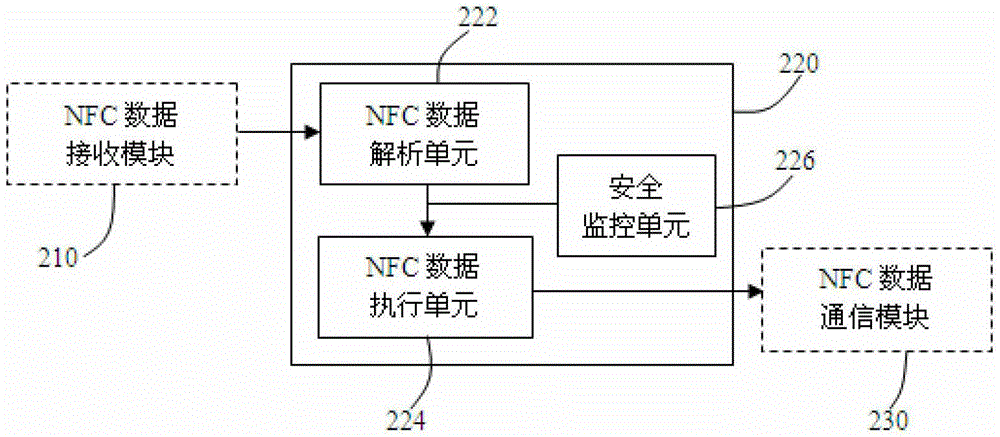
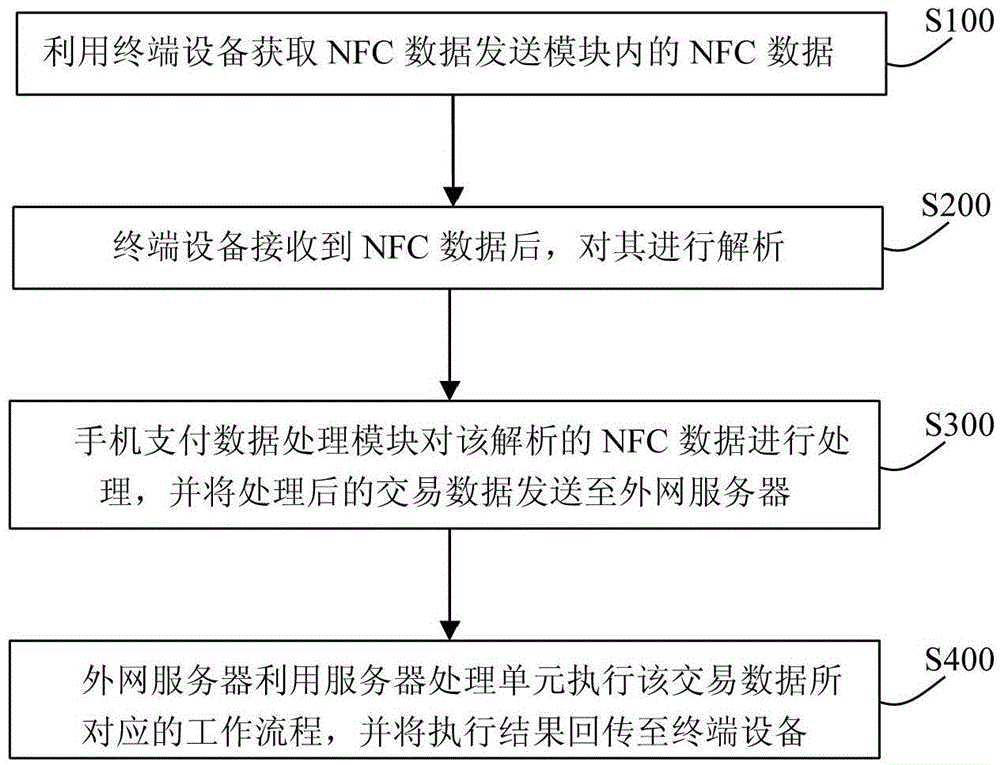
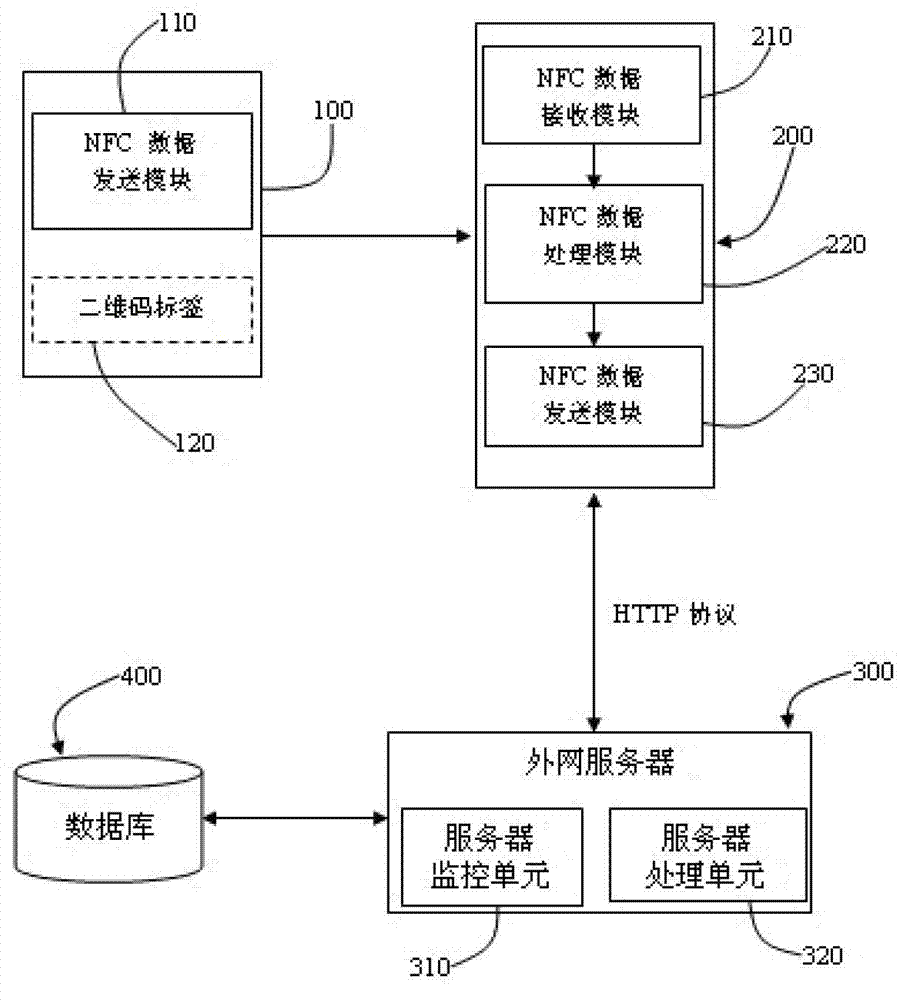
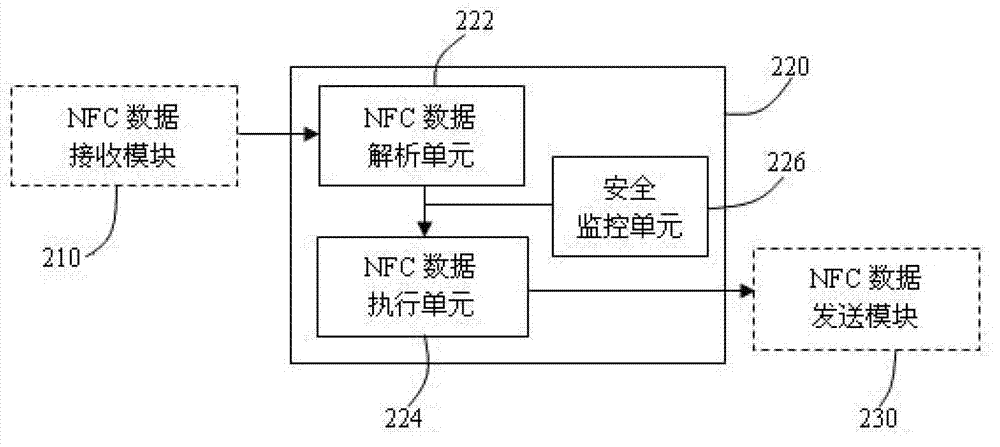
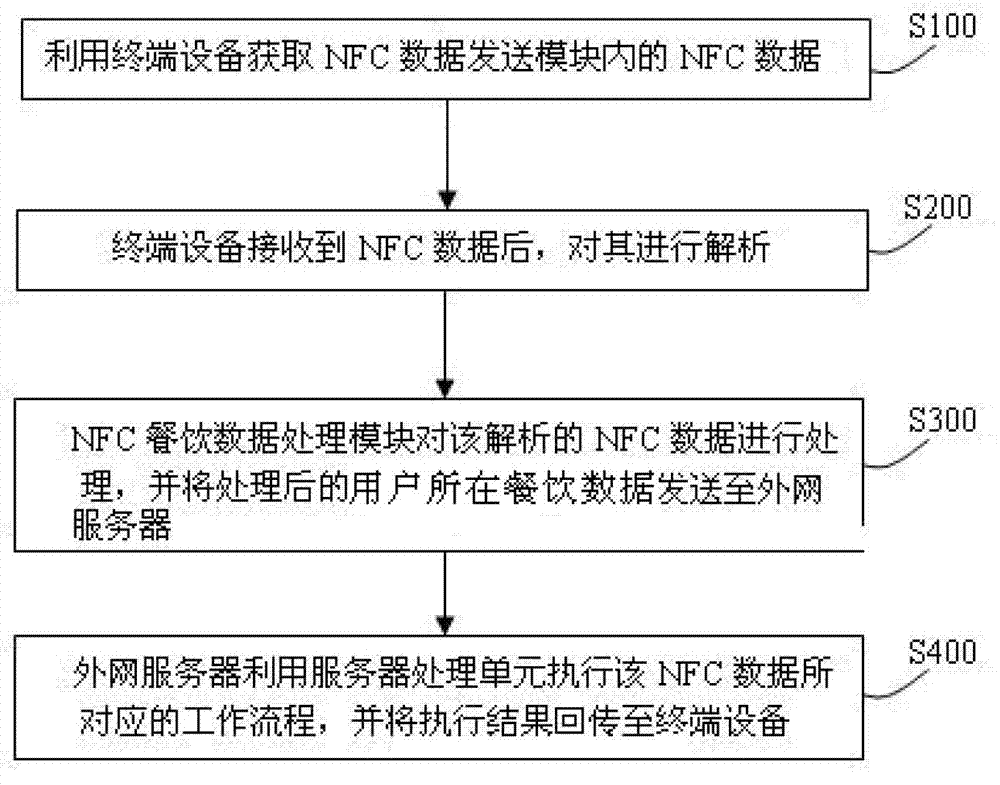
Mobile payment system and method
The invention provides a mobile payment system which comprises an NFC (Near Field Communication) electronic tag and terminal equipment, wherein the NFC electronic tag comprises an NFC data sending module and a two-dimension code tag. The NFC data sending module is used for sending commodity information to the terminal equipment, the commodity information includes company identification information and commodity identification information; the two-dimension code tag is used for recording the commodity information; and the terminal equipment is used for obtaining the commodity information from the NFC electronic tag and then generating payment command information according to the commodity information and sending the payment command information to an outside server. The mobile payment system has the advantages of simplicity, activeness, timeliness and high accuracy in the mobile payment process; and moreover, the mobile payment system provides information security compared to Bluetooth communication and can therefore be widely used for various e-commerce fields.
Owner:上海照恒科技有限公司
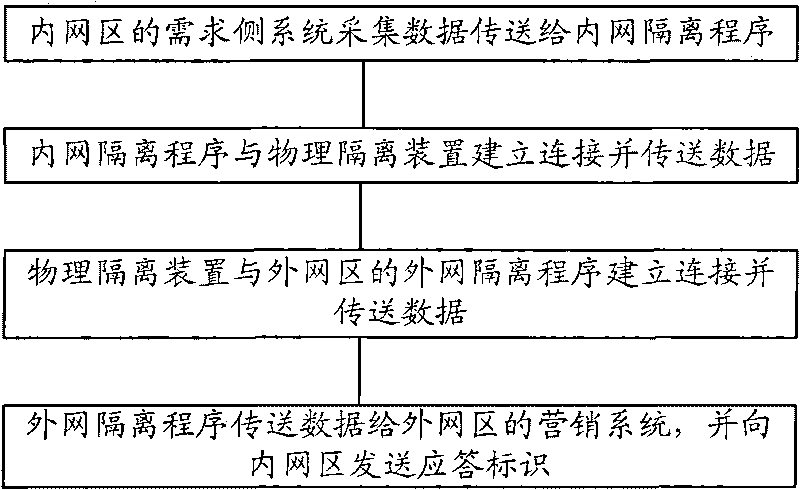
Method for transmitting mass data in real time by penetrating positive physical isolation device
InactiveCN101697536ASolve the blockageComplete in real timeSecuring communicationService flowElectricity
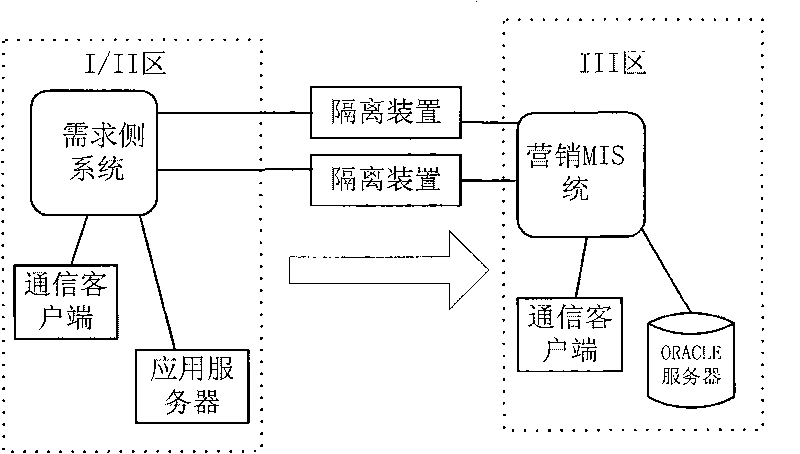
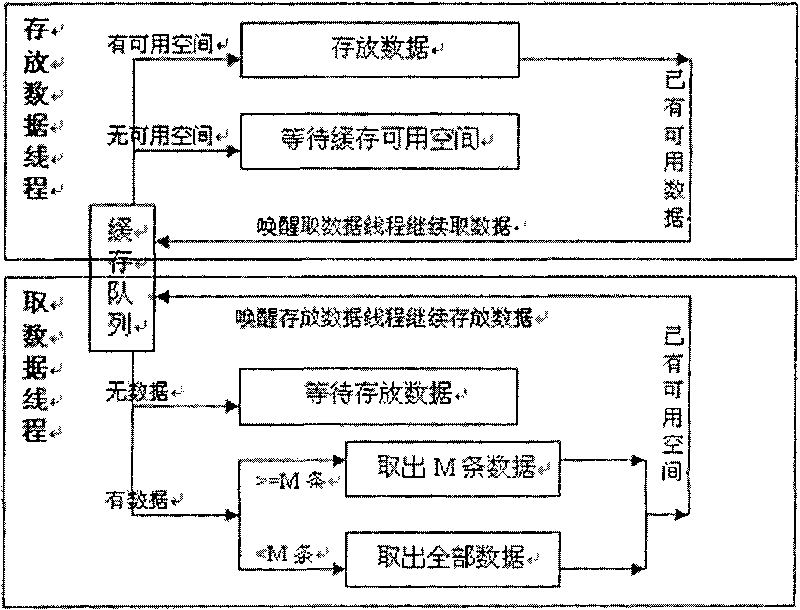
The invention relates to the technical field of electricity and communication, and discloses a method for transmitting mass data in real time by penetrating a positive physical isolation device, which comprises the following steps of S1, acquiring data by a requirement side system of an internal network zone and transmitting the data to an internal network isolation program; S2, establishing a connection between the internal network isolation program and the physical isolation device and transmitting the data; S3, establishing a connection between the physical isolation device and an external network isolation program of an external network zone and transmitting the data; and S4, transmitting the data to a marketing system of the external network zone by the external network isolation program and transmitting a response identification to the internal network zone. The invention ensures that the requirement side system acquires the mass data and effectively transmits the data to the marketing system in real time through the positive physical isolation device, solves the problem of block of the mass data transmitted through the positive physical isolation device among the traditional systems, and enables the marketing system to immediately and completely acquire the data of charge and the like so as to accurately complete the service flow in real time.
Owner:深圳市联创知识产权服务中心
Electric marketing mobile application safe protection system
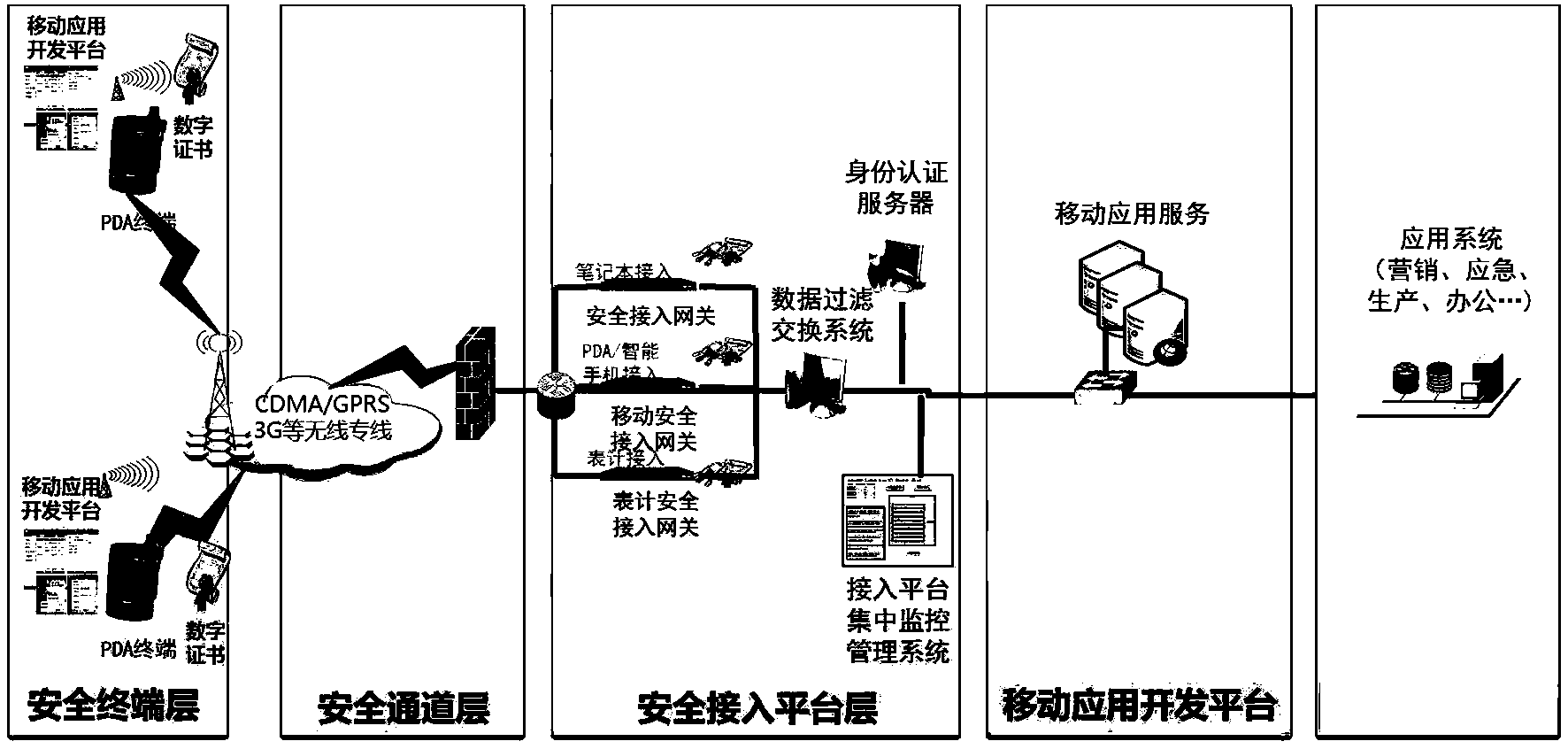
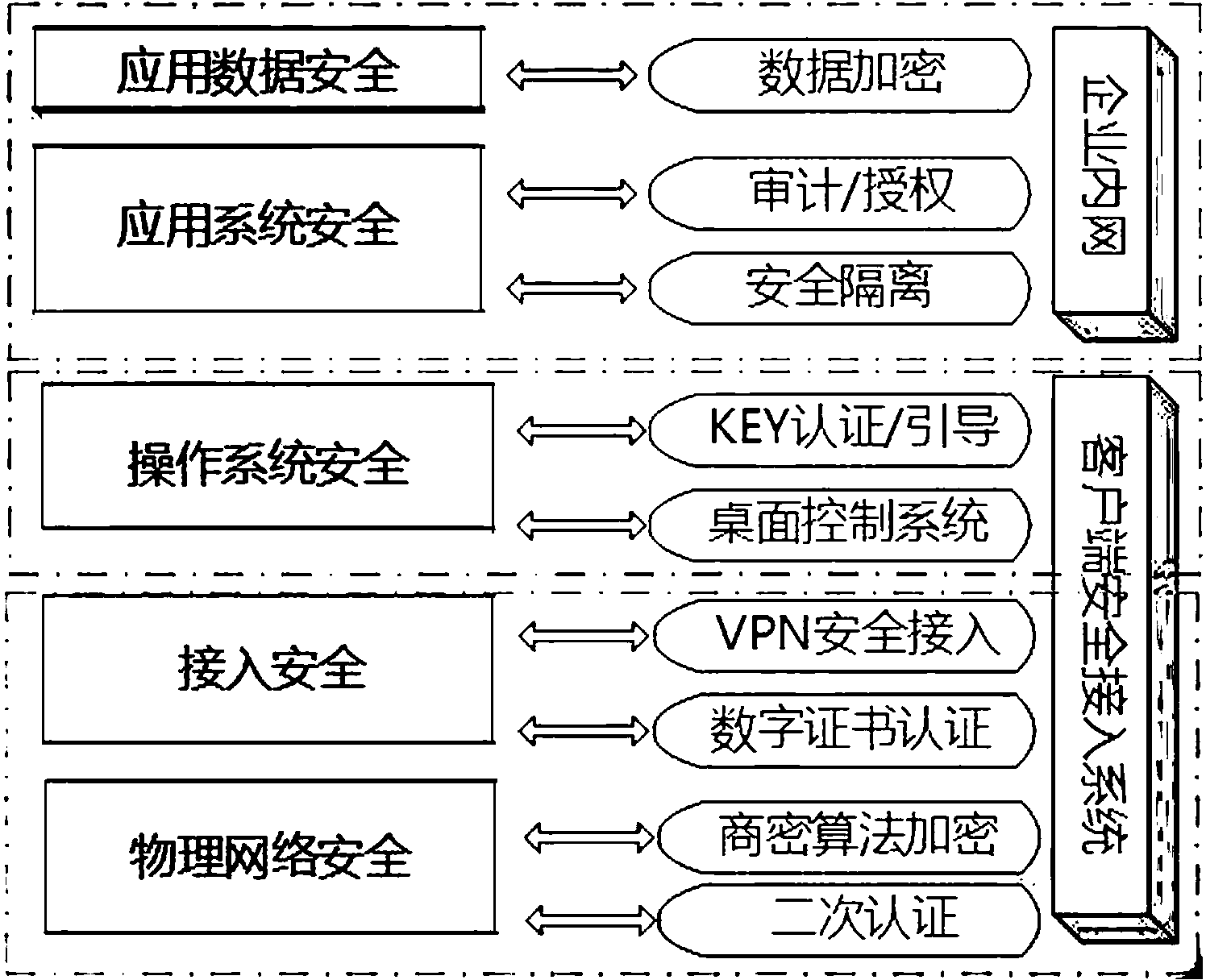
ActiveCN104184735AEnable secure accessImprove securityMarketingSecuring communicationInformation networksEngineering
Provided is an electric marketing mobile application safe protection system. In the present, the safety problem is caused after a mobile terminal is used, and third-party secondary encryption is easy to crack to generate information leakage. The electric marketing mobile application safe protection system comprises a safe terminal layer, a safe channel layer, a safe access platform layer and a mobile application layer. The mobile application layer is used for supporting service application of the mobile terminal and achieving system application safety. The technical scheme of the electric marketing mobile application safe protection system achieves safe access to the mobile terminal, achieves strong insulation between an outer information network and an inner information network through an insulation method, cuts down attack of outer networks and effectively improves information safety.
Owner:STATE GRID ZHEJIANG ELECTRIC POWER +2
Method, device and system for processing source downloading
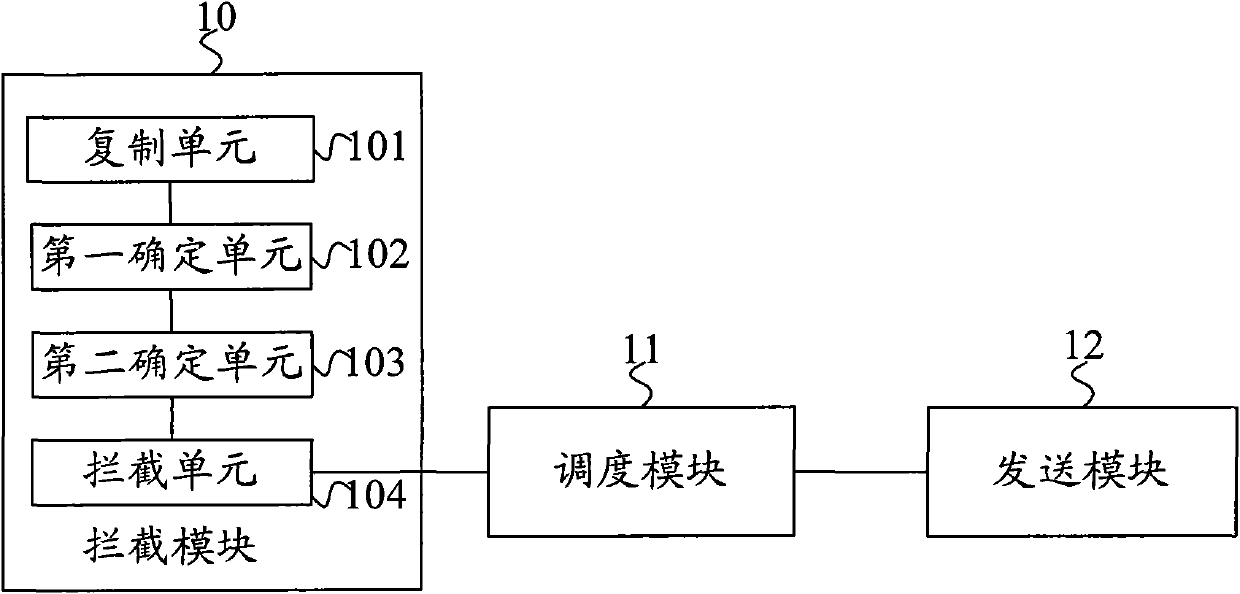
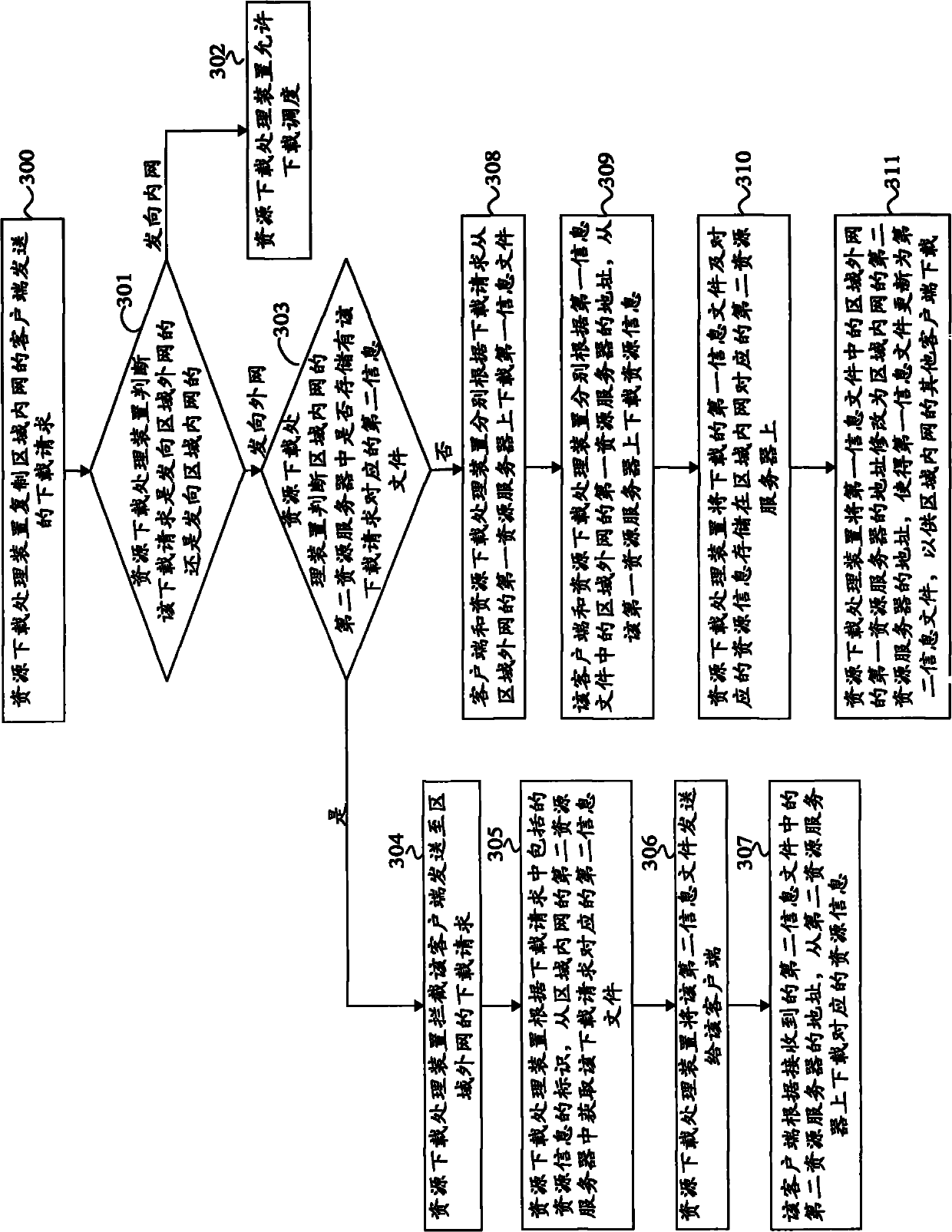
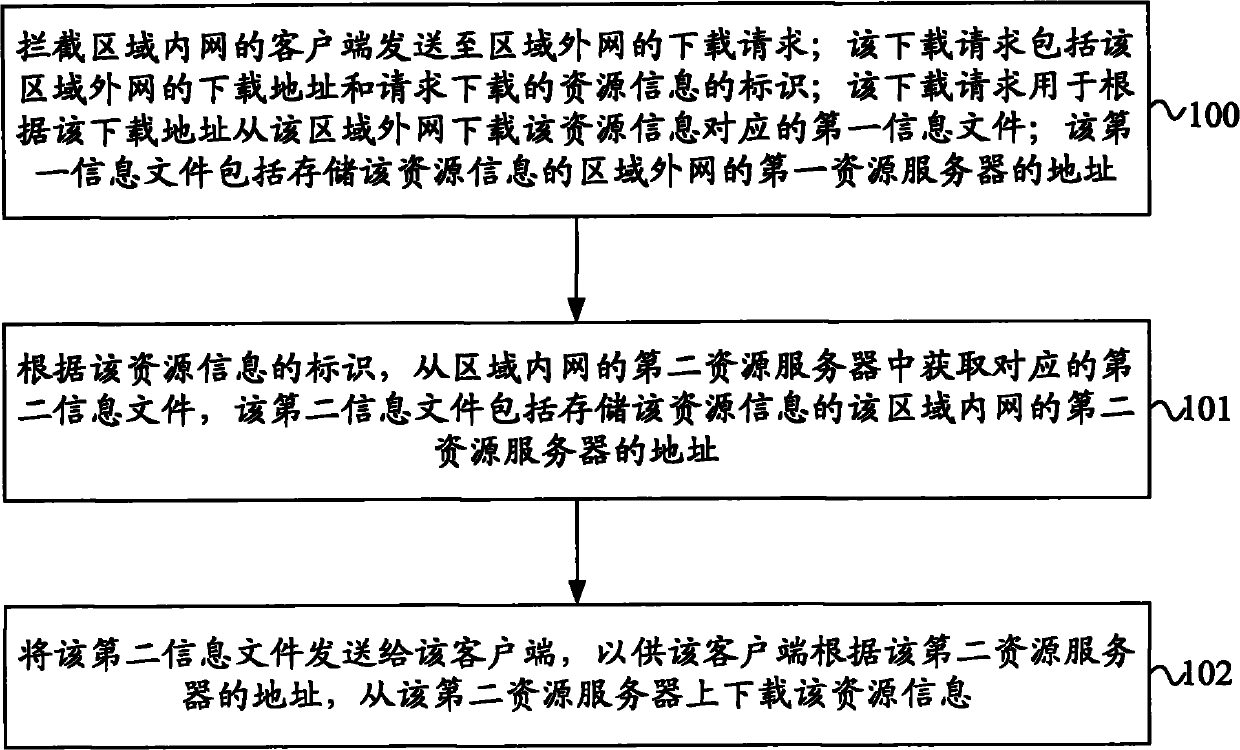
The embodiment of the invention provides a method, a device and a system for processing the source downloading. The method comprises a step of: intercepting a downloading request in an area interior net sent to an area exterior net by a client, wherein the downloading request contains a downloading address of the area exterior net and source information identification requested to download, and the downloading request is for requesting a first information file corresponding to the downloading source information of the area exterior net. The method also comprises the steps of: obtaining a corresponding second information file from a second source server in the area interior net according to the source information identification, and sending the second information file to the client for the client to upload and download the source information from the second source server according to the address of the second source server, wherein the second information file contains the address of the second source server of the area interior net for storing the source information. The technical solution of the embodiment of the invention can efficiently reduce the area scheduling flow in a P2P network, promote the scheduling efficiency, reduce the pressure of the P2P network in the scheduling process and ensure the property of the P2P network.
Owner:HUAWEI CLOUD COMPUTING TECH CO LTD
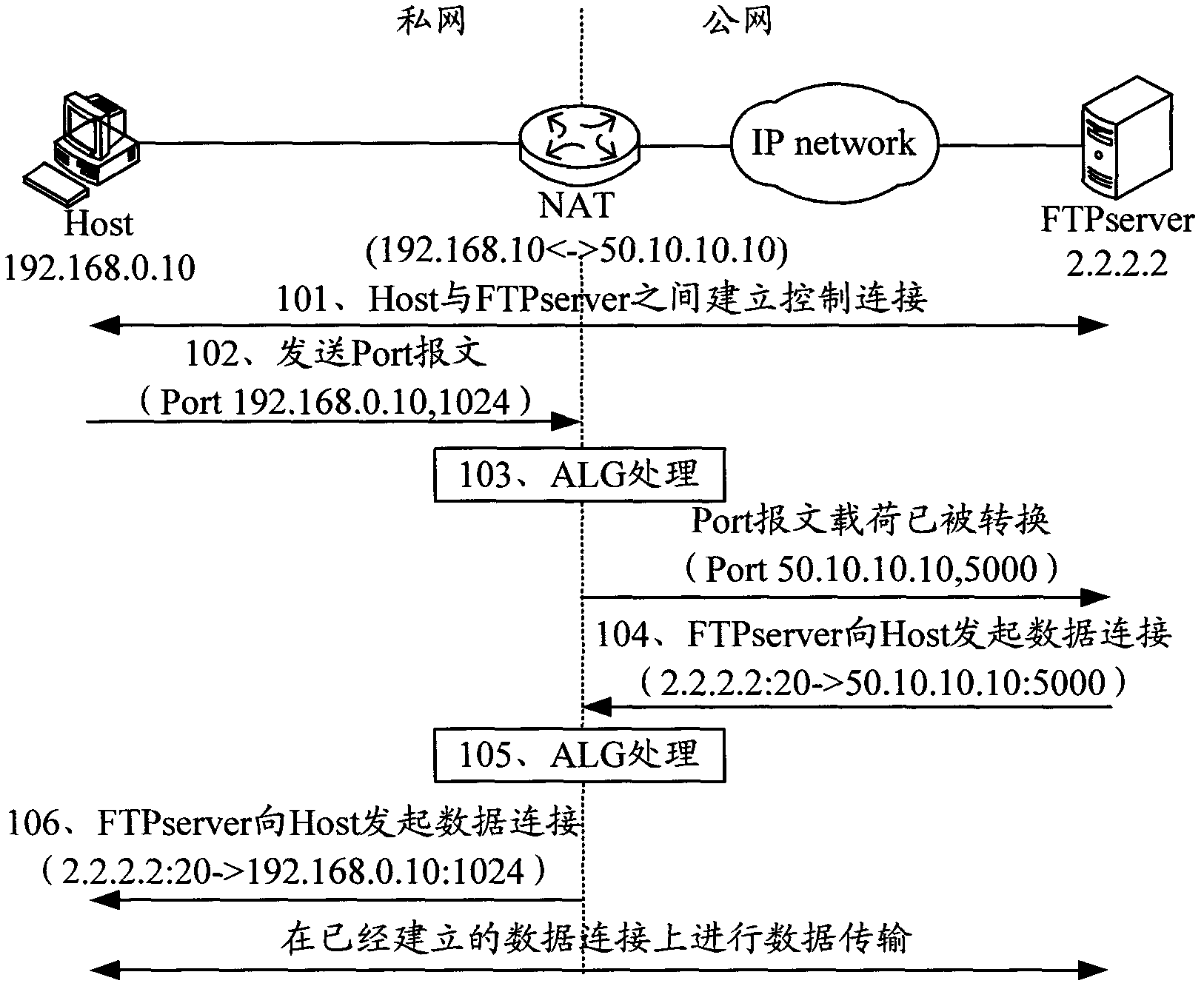
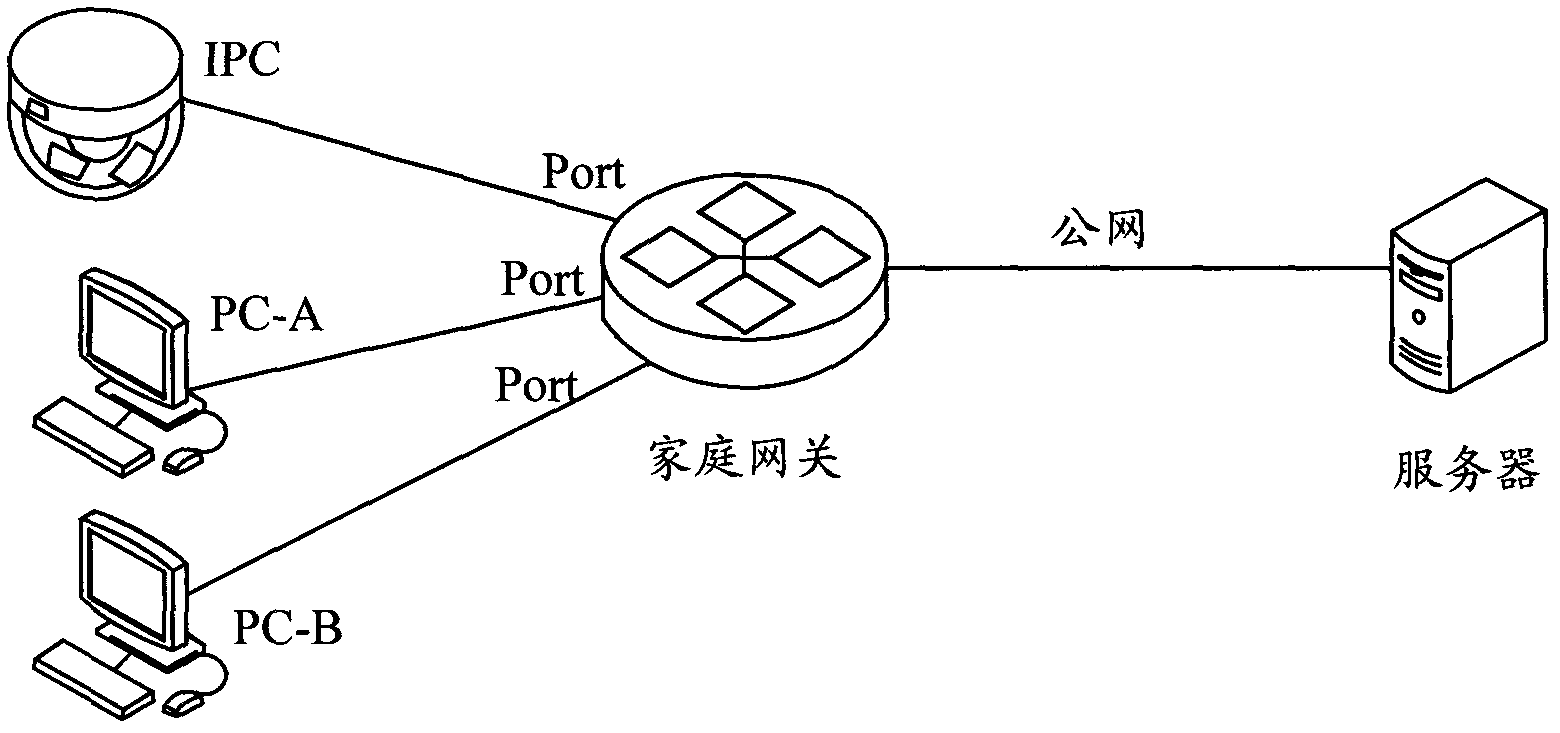
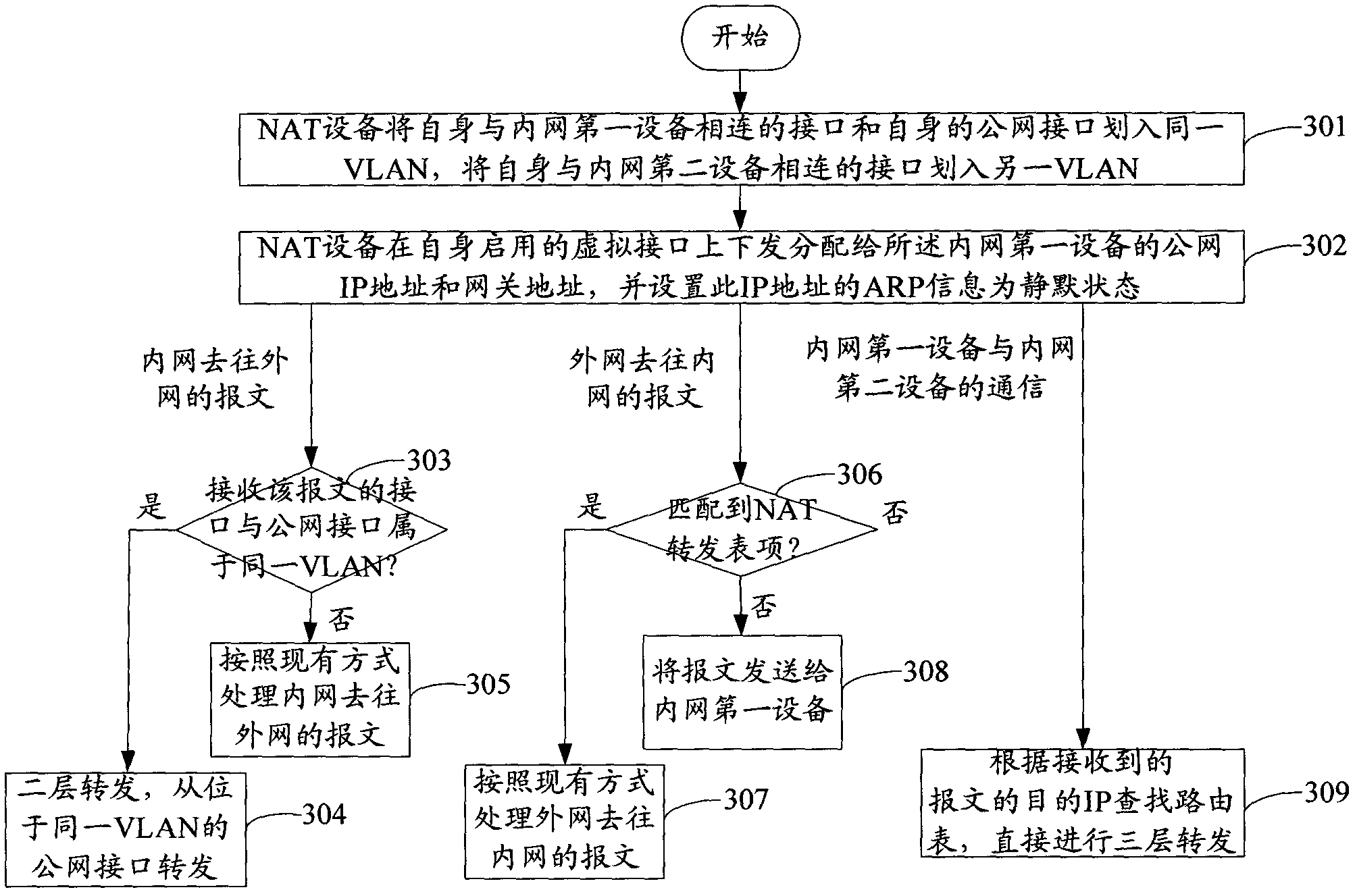
Method for communication between intranet equipment and internet equipment and network address transformation equipment
The invention discloses a method for communication between intranet equipment and internet equipment and NAT (Network Address Transformation) equipment. The method comprises the steps of: classifying an interface connected with first intranet equipment and a public network interface of the NAT equipment per se into a same VLAN (Virtual Local Area Network) by the NAT equipment, classifying an interface connected with second intranet equipment of the NAT equipment per se into the other VLAN by the NAT equipment, issuing a public network IP (Internet Protocol) address and a gateway address, distributed to the first intranet equipment, on a virtual interface enabled by the NAT equipment per se, and setting ARP (Address Resolution Protocol) information of the IP address to be a silent state; forwarding a received message sent by the first intranet equipment to the internet from a public network interface located in the same VLAN with an ingress interface of the message; forwarding a message, which is sent by the second intranet equipment to the internet and transformed by a network address port, from the public network interface; and forwarding a message sent by the internet equipment according to whether the message is matched with a NAT forwarding table. By applying the method and the NAT equipment, provided by the invention, one equipment in a local area network can interact with a public network rapidly by using the public network IP address, and other equipment in the local area network interact with the public network through NAT.
Owner:NEW H3C TECH CO LTD
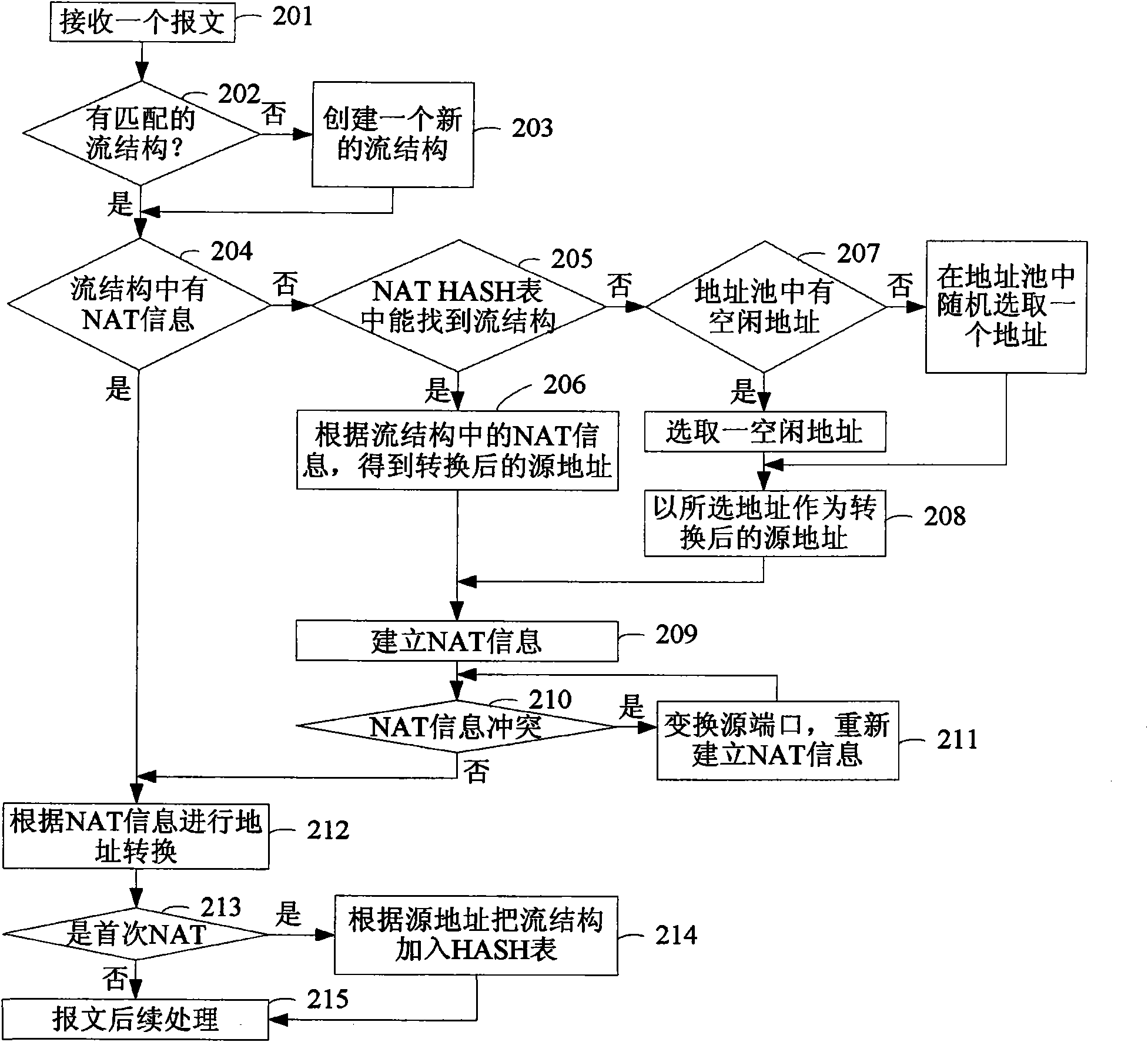
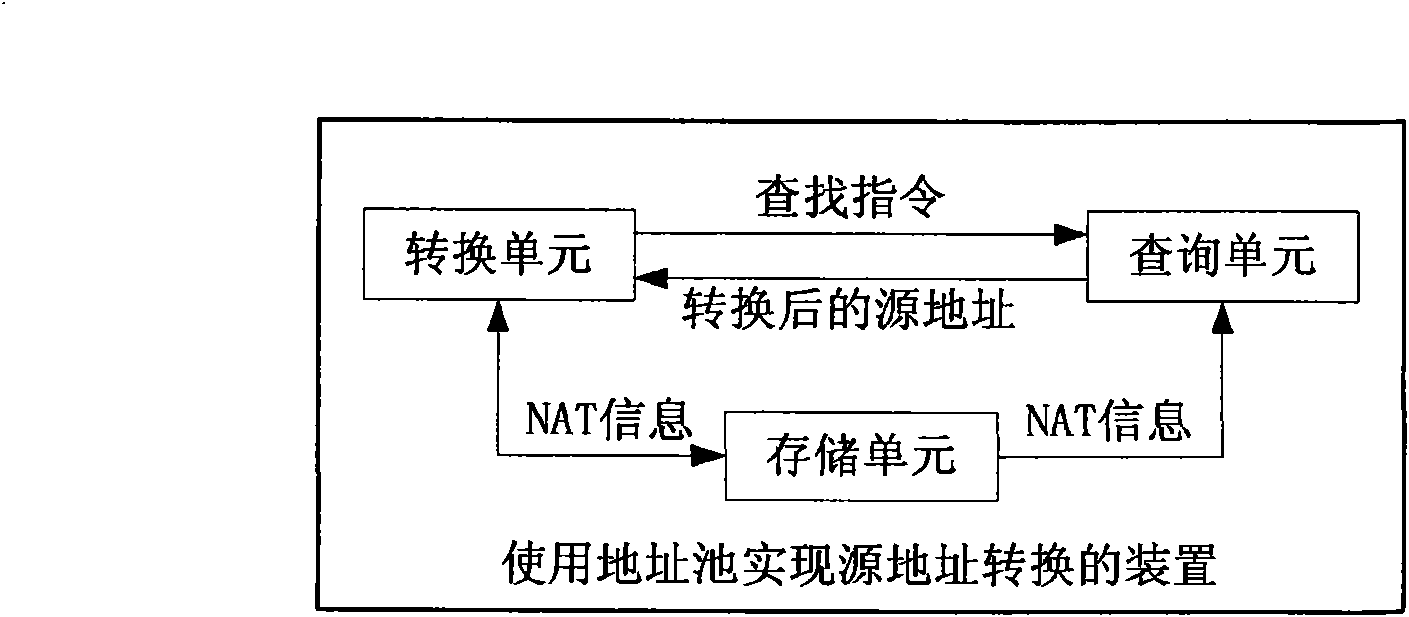
Method and device for realizing source address conversion by using address pool
InactiveCN101800690ABalancedSolve the problem of access failureData switching networksStructure of Management InformationFailure causes
The invention discloses a method and a device for realizing source address conversion by using an address pool. The method comprises the following steps: for a message for an internal network to visit an external network, if the flow structure being matched the message does not contain NAT information, seeking the flow structure of which the internal network source address is the same as that of the message in the flow structure recorded with the NAT information, and converting the source address of the message by using the address of the address pool in the NAT information of the flow structure as the source address after conversion; and for the flow structure carrying out the source address NAT for the first time, recording the conversion relation between the source address of the internal network and the address of the address pool in the flow structure as NAT information. The invention ensures that the same internal network source address can use the same address of the address pool after NAT, thereby avoiding access failure caused by different addresses.
Owner:BEIJING VENUS INFORMATION TECH +1
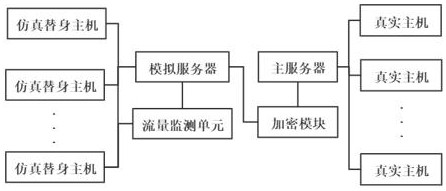
Network security early warning system based on self-adaptive mimicry technology
The invention provides a network security early warning system of a self-adaptive mimicry technology. The system comprises simulation substitute hosts, real hosts, a main server, a simulation server and a flow monitoring unit, a plurality of real hosts are connected with the main server to form an intranet, and the simulation substitute hosts are used for simulating the operation of the real hosts. The simulation server is used for simulating the operation of the main server, the flow monitoring unit and the plurality of simulation substitute hosts are respectively connected with the simulation server so as to form an external network for simulating the operation of an internal network, the external network is accessed to the Internet, and encrypted communication can be carried out betweenthe main server and the simulation server. The flow monitoring unit and the plurality of simulation substitute hosts are respectively connected with the simulation server so as to form an external network for simulating the operation of an intranet, the external network is accessed to the Internet, and attack behaviors are filtered through the external network, so that the security of the intranet can be greatly improved, and the intranet is prevented from being attacked.
Owner:北京智仁智信安全技术有限公司
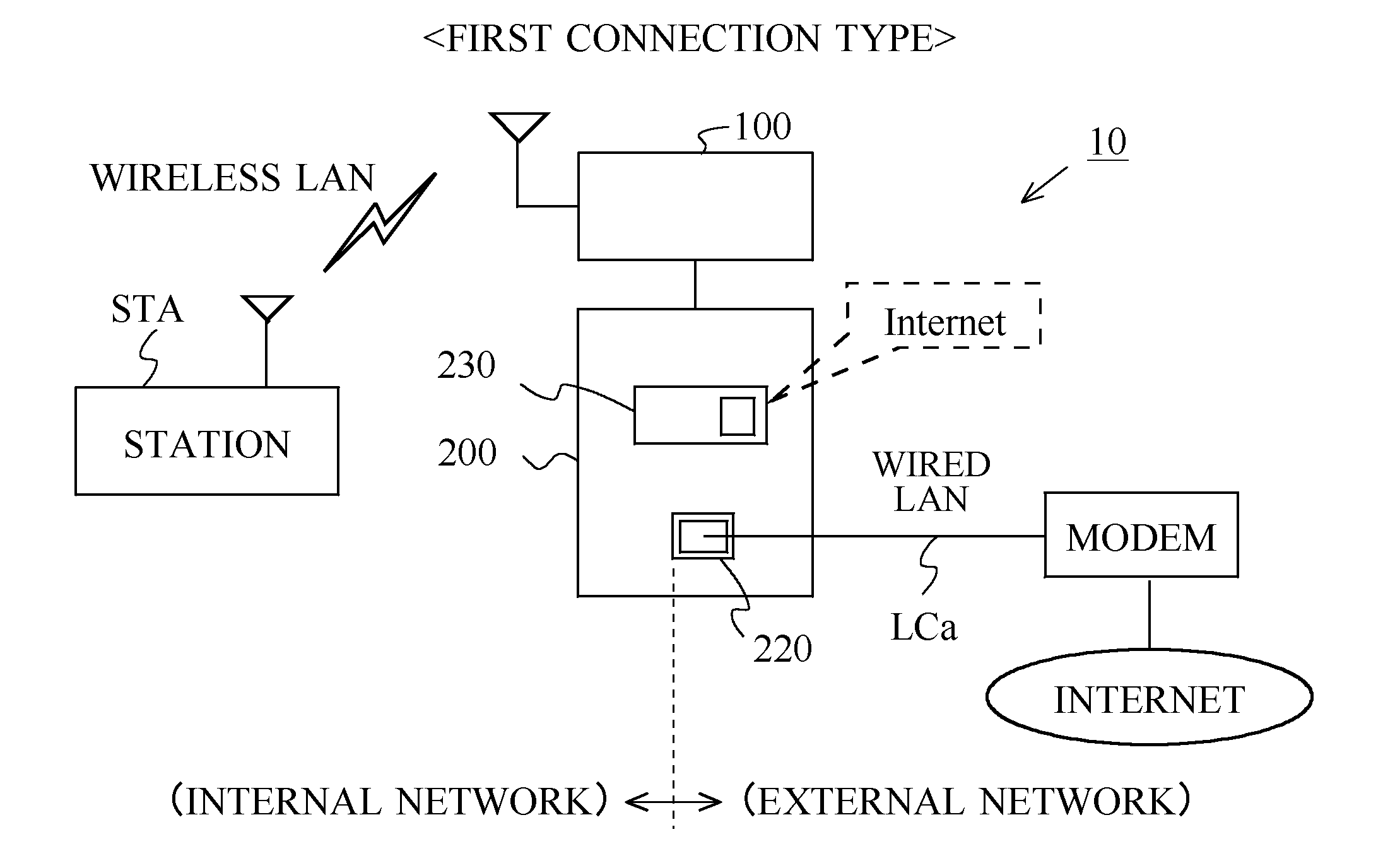
Wireless relay device
InactiveUS20110280175A1Frequency-division multiplex detailsNetwork topologiesExternal connectionInternal connection
A switch switches between an external connection state where a port functions as an external-network-side port, and an internal connection state where the port functions as an internal-network-side port. A transfer process section transfers, when the switch is in the external connection state, a packet between a station belonging to a wirelessly connected internal network and a modem wiredly connected to the port, and otherwise transfers, when the switch is in the internal connection state, a packet between a station wiredly connected to the port and a network device belonging to a wirelessly connected external network.
Owner:BUFFALO CORP LTD
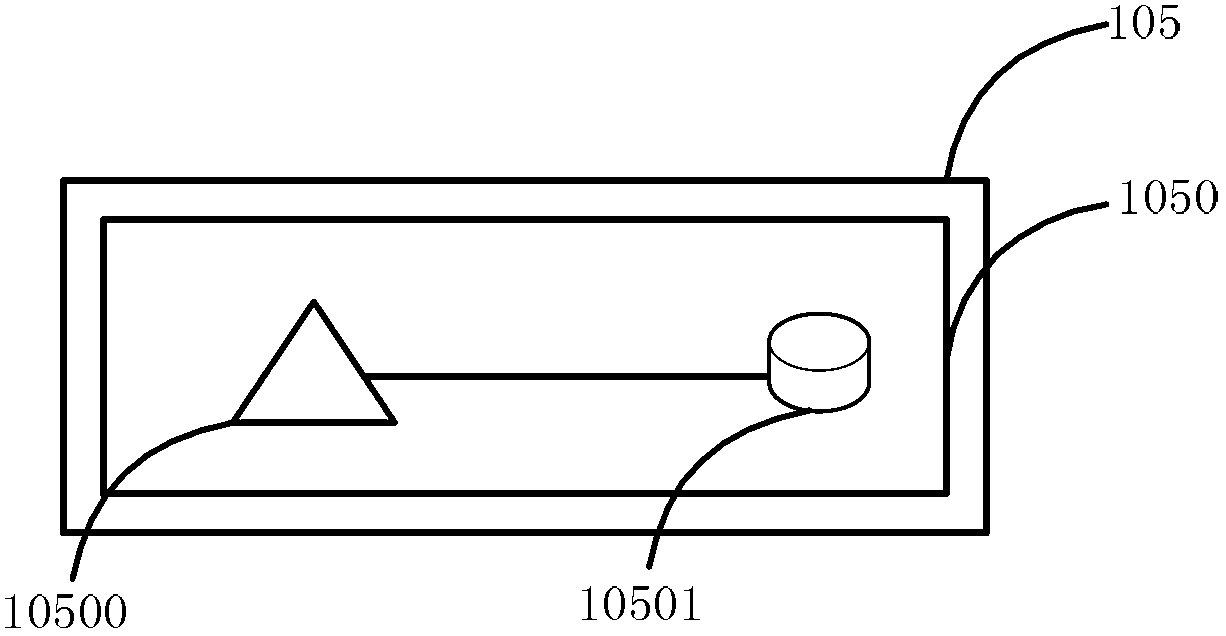
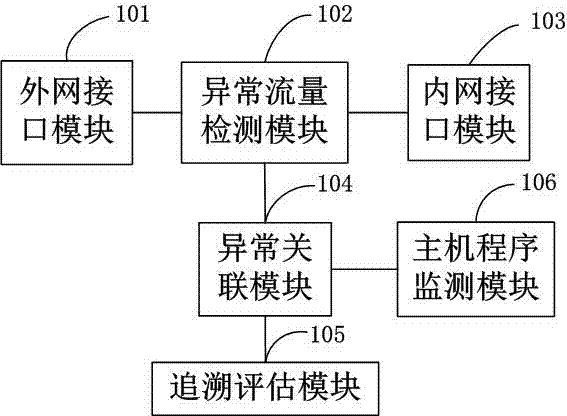
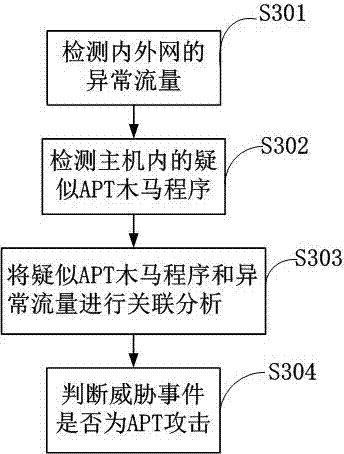
APT firewall
The invention relates to the field of information security, and specifically, the invention relates to an APT firewall system. An extranet interface module 101, an abnormal flow detection module 102, an intranet interface module 103, an abnormal association module 104, a retrospective evaluation module 105 and a host program monitoring module 106 are integrated in the system for detecting the flow of an extranet and an intranet in real time, monitoring the program process in real time and further decomposing and identifying abnormal flow and abnormal behaviors containing APT threats so as to locate the APT threat level, intercept the APT communication, clear the APT Trojan program and eliminate the threat attacks and the potential safety hazards.
Owner:深圳耀东安全科技有限公司
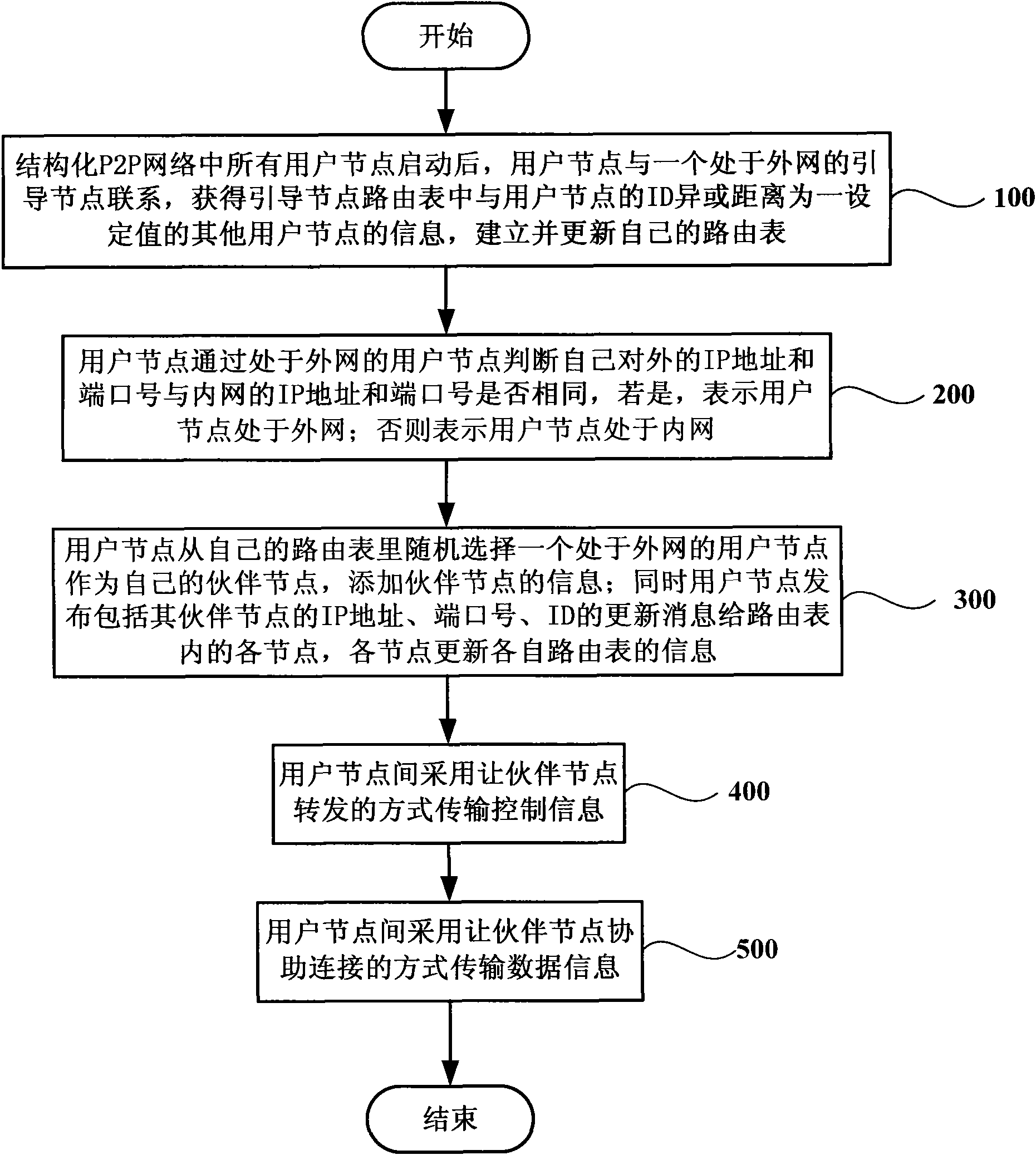
Method and system for realizing NAT traversal in structured P2P network
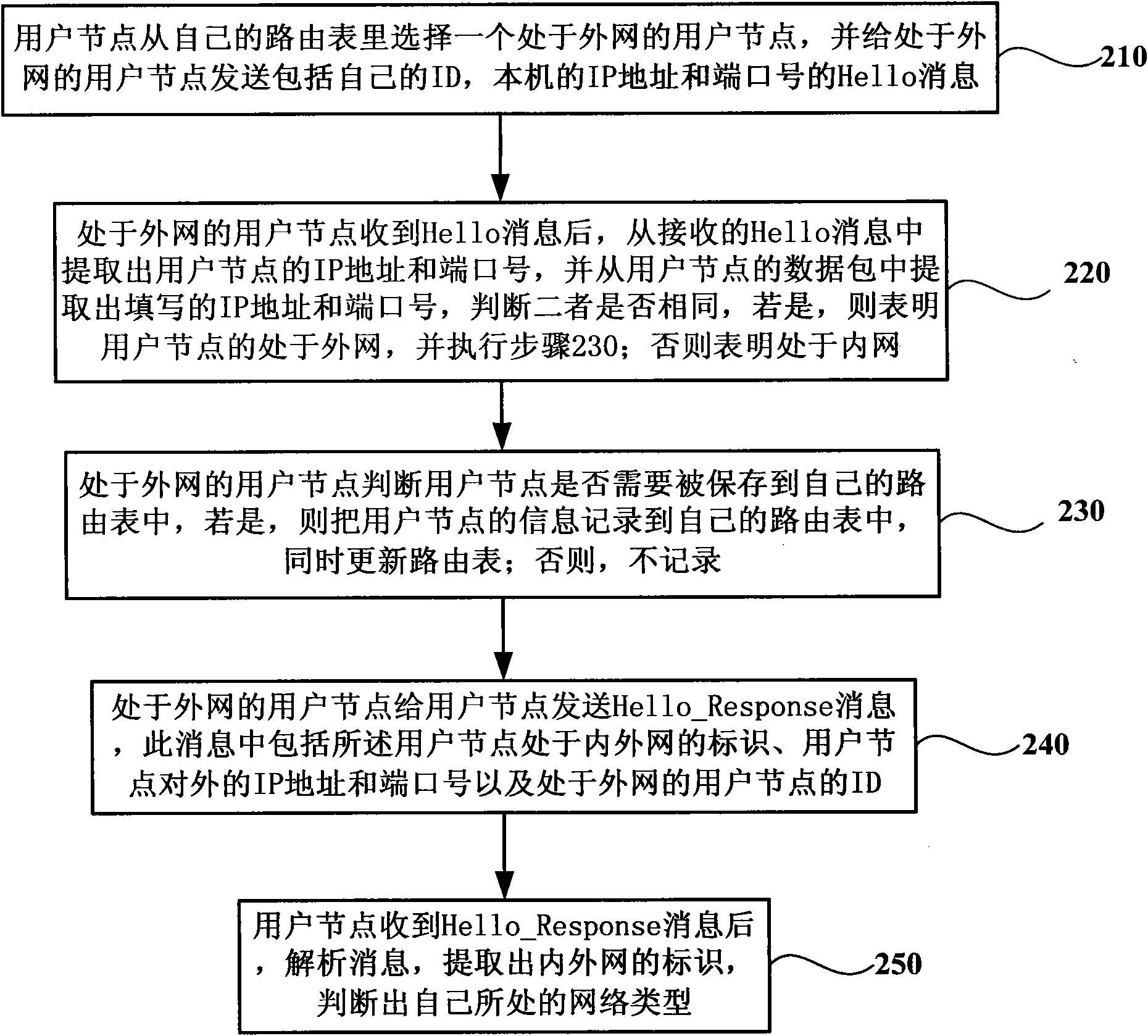
The invention discloses a method and a system for realizing NAT traversal in a structured P2P network. The method comprises that: a user node contacts a guide node positioned in an outer network to acquire the information of other user nodes which are different from the ID of the user node or have a distance in a set value in a guide node route table and establish and update a route table per se;and the user node judges whether the external IP address and port number per se are the same as the IP address and port number of a intranet, if the external IP address and port number are the same as the IP address and port number of the intranet, the user node is positioned in the outer network, and if the external IP address and port number are not the same as the IP address and port number ofthe intranet, the user node is positioned in the intranet; the user node selects a user node positioned in the outer network at random as a partner node per se and adds the information of the partnernode; simultaneously, the user node sends IP address, port number and ID updating messages including the partner node to each node in the route table, and each node updates the information of respective route table; control information is transmitted between user nodes in a mode of forwarding by the partner node; and data information is transmitted between the user nodes in a mode of assisting connection by the partner node.
Owner:SHANGHAI YINGLIAN SOMATOSENSORY INTELLIGENT TECH CO LTD
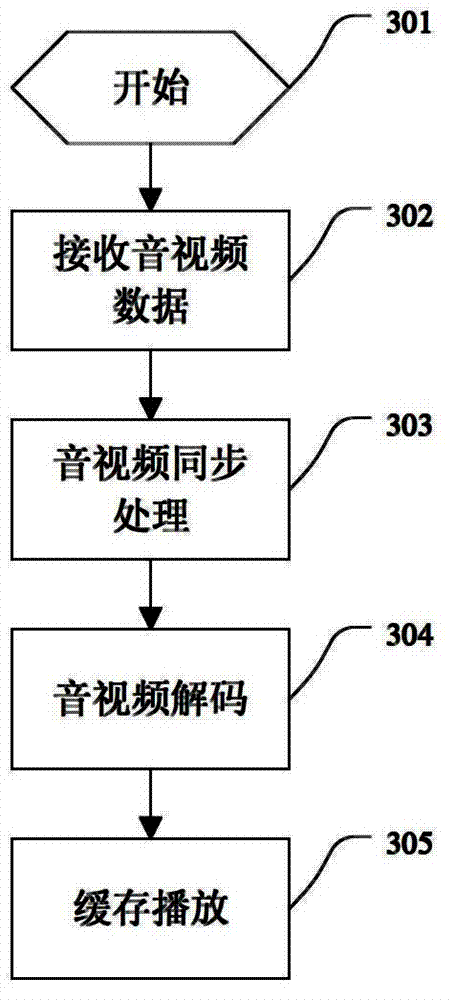
Self-adaptive bandwidth transmitting and playing method based on audio and video frequency synchronization
ActiveCN102932676APlay clearlySmooth playbackSelective content distributionStreaming dataClient-side
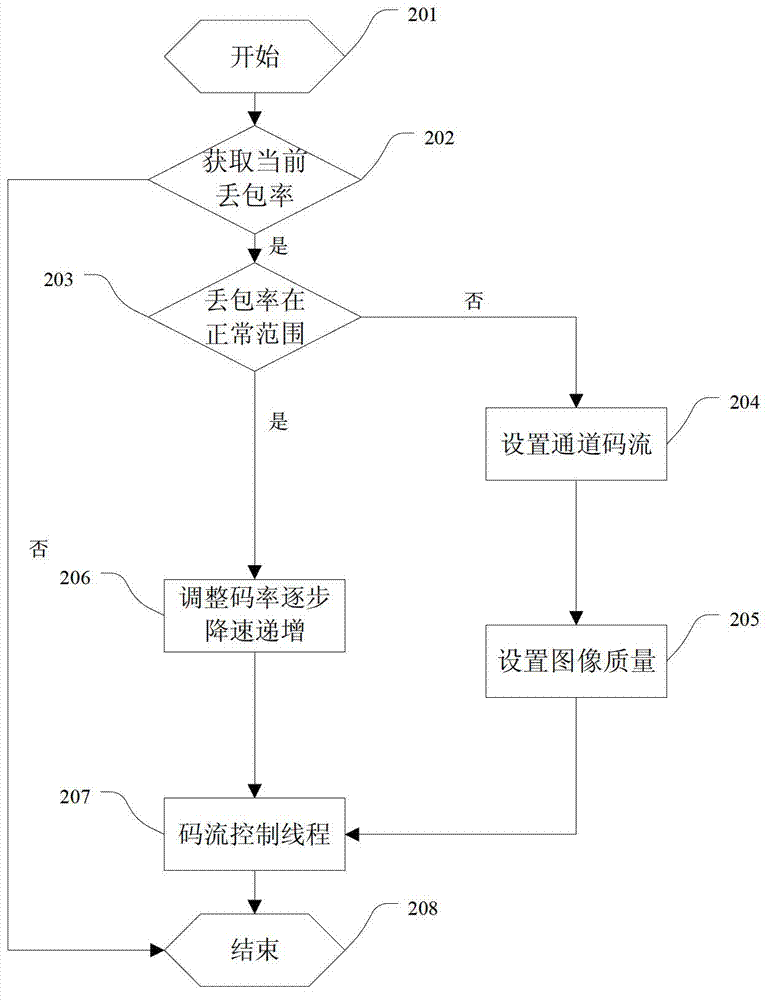
The invention discloses a self-adaptive bandwidth transmitting and playing method based on audio and video frequency synchronization, and relates to a video data transmission processing technology of a public mobile communication device. The method comprises the steps: generating a video stream data according to an H.264 coding; dynamically adjusting size of transmitted data quantity in real time according to the condition of current wireless bandwidth, transmitting the data to an outer network server via a wireless network; receiving and displaying audio and video data received by a client; creating an audio and video data buffer area, displaying and playing the video by a certain playing strategy according to the speed of receiving data quantity, and ensuring synchronization of the real-time video and audio frequency through an audio and video synchronization algorithm in an entire process. According to the method disclosed by the invention, operation and maintenance efficiency is improved; manpower cost is reduced; the video can be detected in real time; the problem of vibration of the wireless bandwidth is solved; the audio and video are synchronous, and the method has the advantages of strong generality, strong transportability and flexible expansibility.
Owner:武汉众智数字技术有限公司
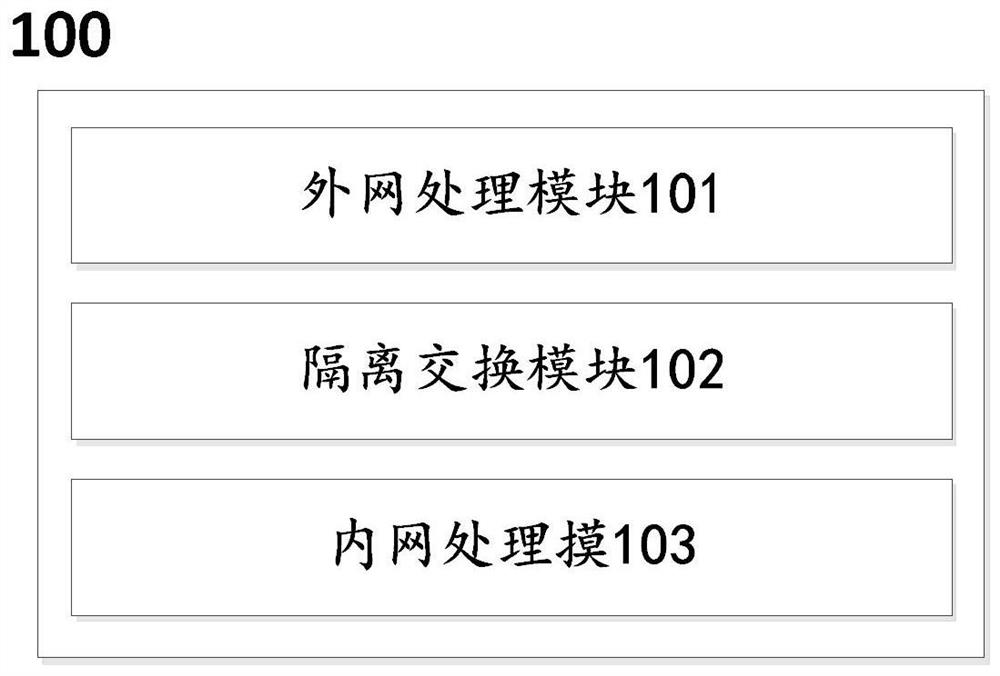
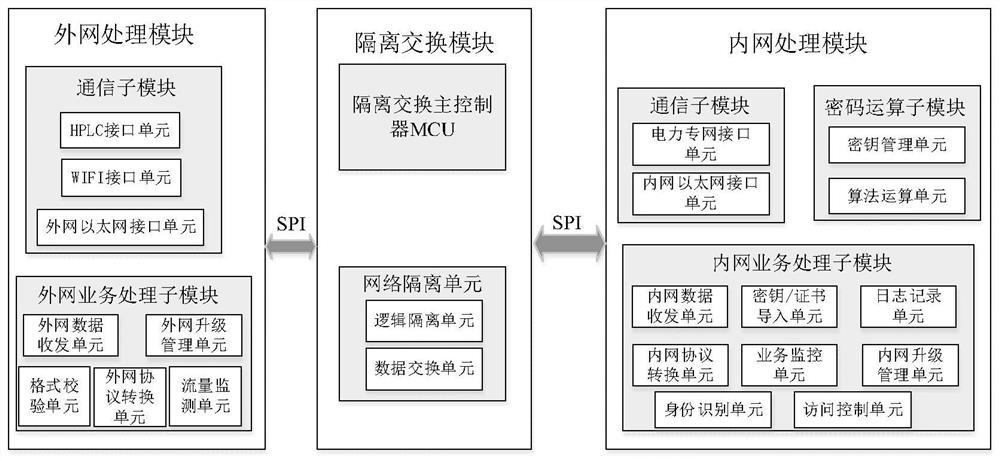
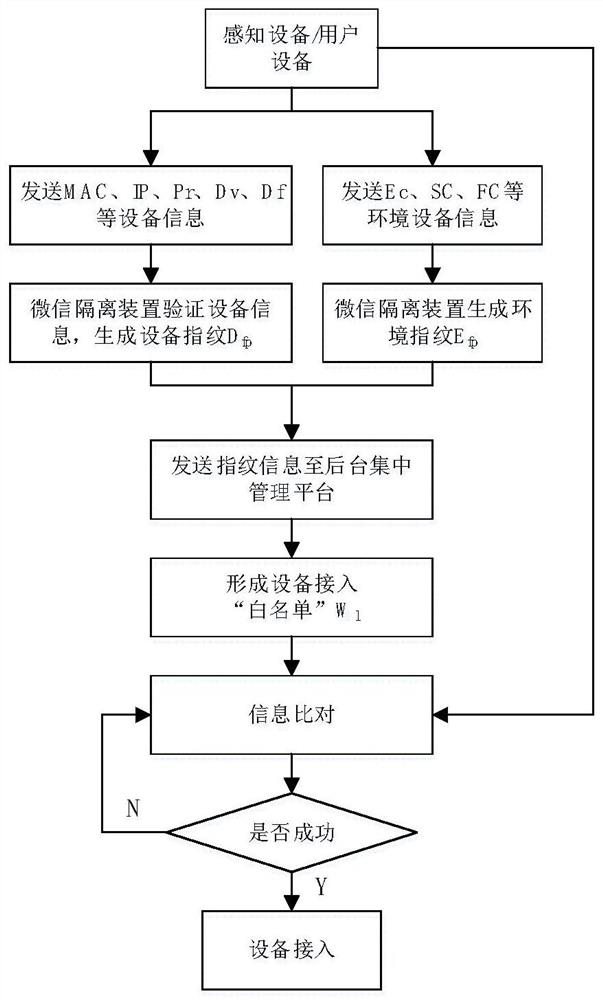
Isolation device and isolation method suitable for power Internet of Things client side
The invention relates to an isolation device and isolation method suitable for a power Internet of Things client side. The method comprises the steps: carrying out analysis of a received first data message transmitted by external network equipment through an external network processing module to obtain key information, and carrying out protocol format conversion of the key information according toa data ferry protocol to obtain a second data message; controlling the external network processing module and an internal network processing module to be in a physical isolation state by utilizing anisolation switching module, and performing format verification on the second data message; after the format of the second data message is verified, decrypting the second data message by using the internal network processing module, and conducting protocol format conversion processing on the decrypted second data message according to a special communication protocol of the power Internet of Things, so that a third data message can be obtained and sent to internal network equipment. Security isolation between an open client side access network and an electric power Internet of Things core network is realized, and a core service system can be effectively prevented from being illegally invaded.
Owner:CHINA ELECTRIC POWER RES INST +2
Video monitoring system based on video resource safety gateway
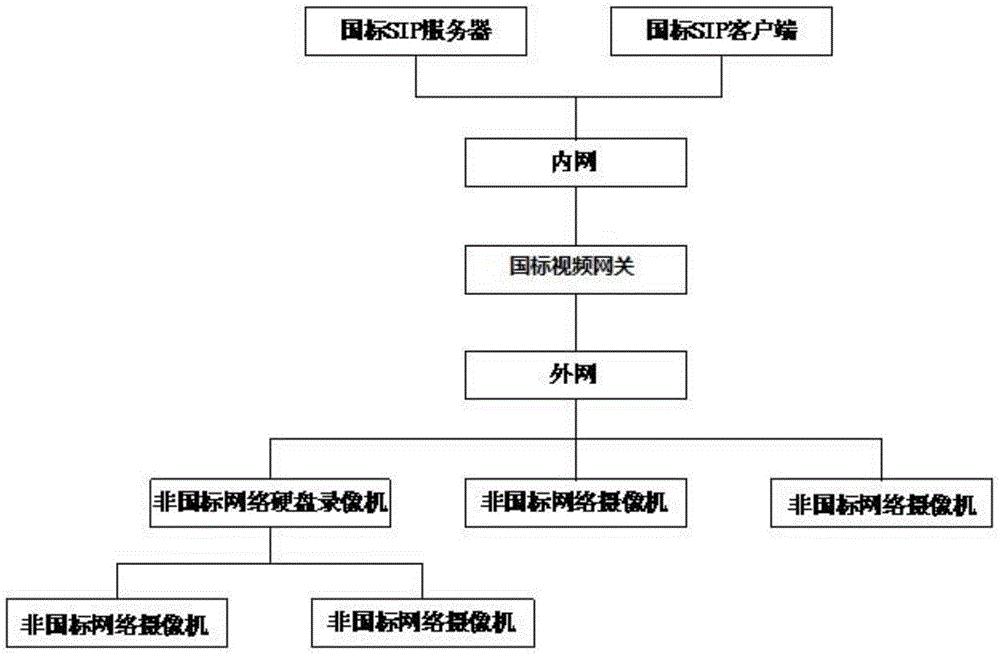
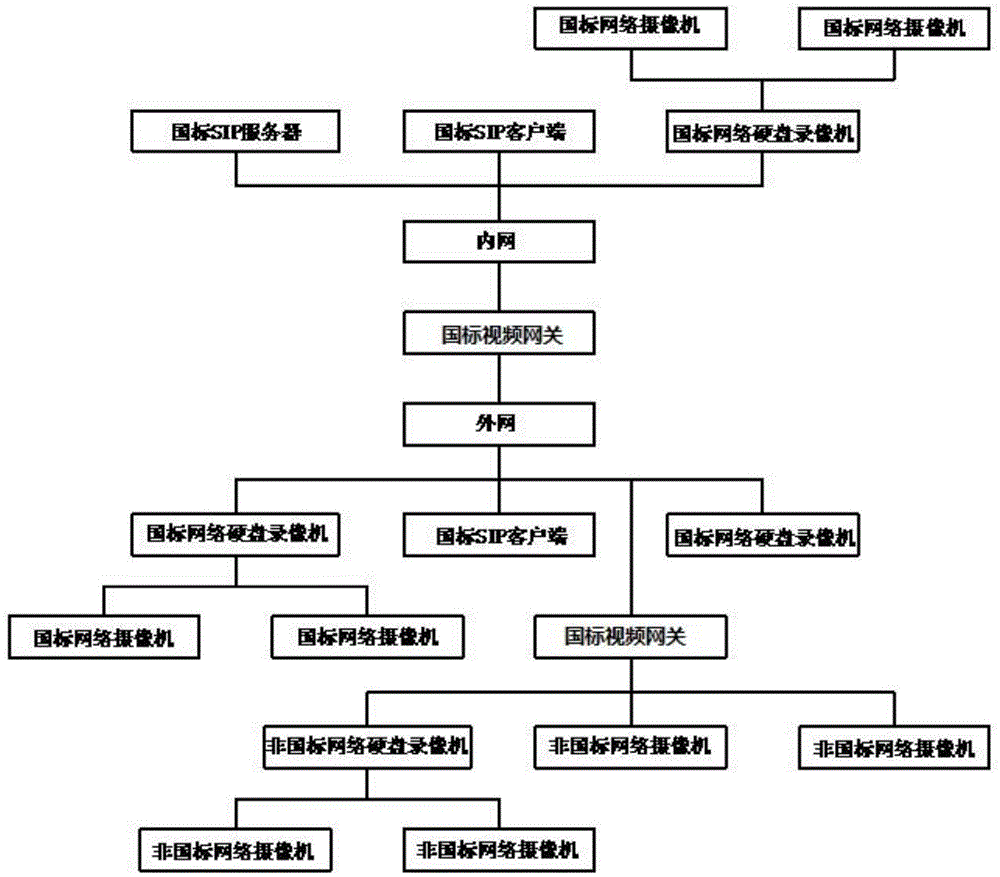
InactiveCN104954764APowerful firewall functionEnsure safetyTelevision system detailsColor television detailsClient-sideNational standard
The invention discloses a video monitoring system based on a video resource safety gateway. The video monitoring system comprises a national standard SIP server on an intranet, a national standard SIP client on the intranet, a national standard video gateway, and non-national standard monitoring equipment on an Extranet, or comprises a national standard SIP server I on the intranet, a national standard SIP client I on the intranet, national standard monitoring equipment I on the intranet, a national standard SIP server II on the extranet, a national standard SIP client II on the extranet and national standard monitoring equipment II on the extranet, wherein a VC-SS3200 GB / T28181 video gateway is adopted as the national standard video gateway. In the video monitoring system, the national standard video gateway supports not only hybrid access of the national standard devices and the non-national standard devices, but also standardization transformation of the non-national standard devices as well as output of standard signaling and standard code streams; various systems can be seamlessly accessed to a national standard video monitoring platform; besides, the national standard video gateway in the video monitoring system has a powerful network firewall function, so that intranet-extranet physical isolation between an accessed system network and a back-end monitoring platform system network is realized, and the safety of network data and information is guaranteed.
Owner:SHANGHAI YUANZHE ELECTRONICS TECH
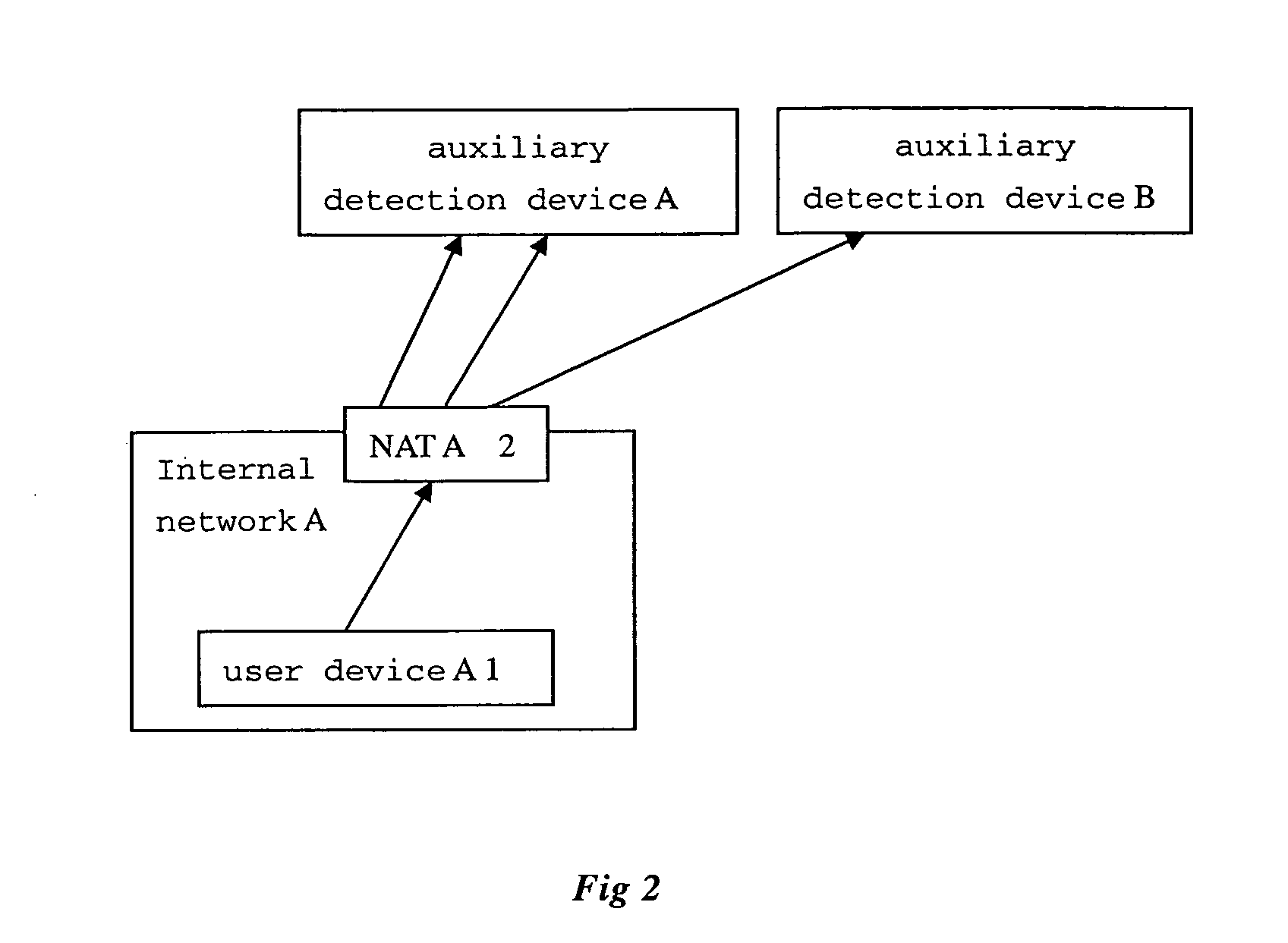
Method for Controlling the Direct Penetrate Communication Two Parts of Which Are Under the Different Nats and the Device Thereof
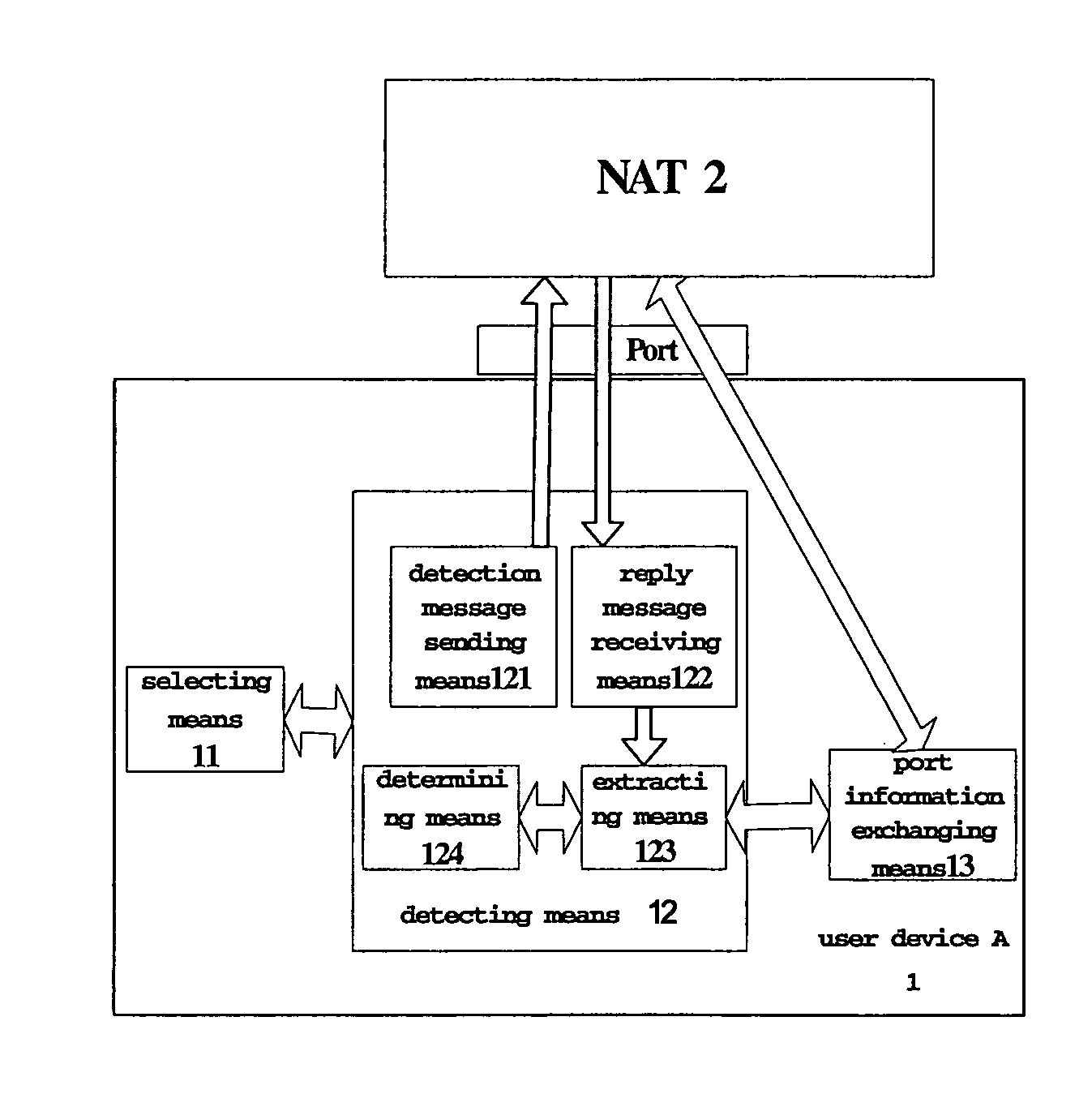
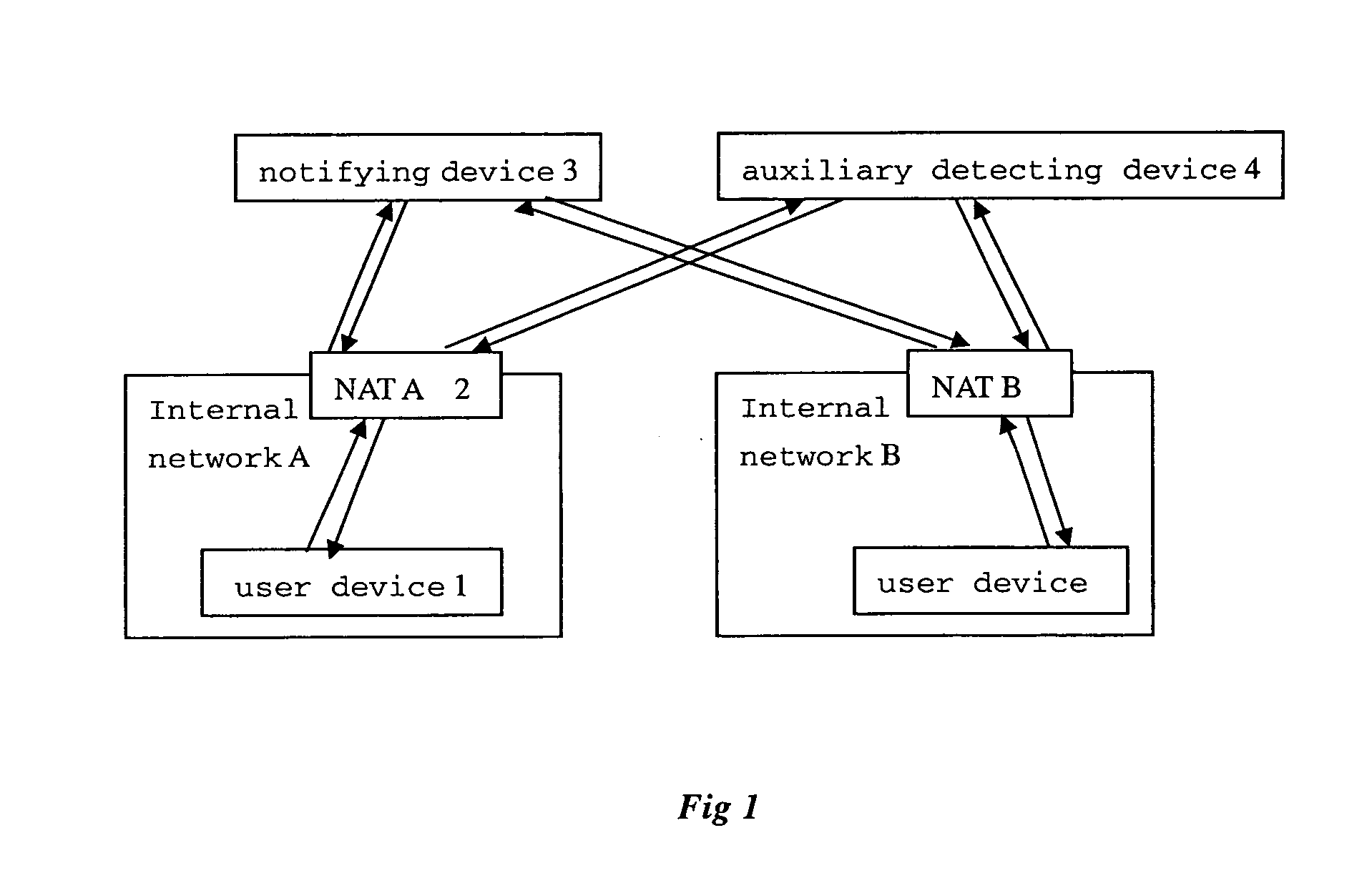
The present invention discloses a user device for implementing direct penetrating communication between a user device under a NAT and another user device under a different NAT and a method for the same. Detection message is sent to an auxiliary detecting device in an external network through a selected local port. Then the reply message from said auxiliary detecting device will be received and the NAT-translated NAT source port of said detection message can be obtained. By comparing the NAT source ports of a plurality of detection messages, it can be determined whether or not the selected port is a penetrated port. After that, the corresponding NAT source address and NAT penetrated port will be informed to another user device under a different NAT (also, the NAT penetrated port and NAT source port determined by said another user device will be received via said external-network device). Therefore, said user device and the opposite-end user device directly communicating with each other through the determined local source port and with the received NAT external-network address and NAT port of the other party as the destination address and destination port.
Owner:BEIJING FUNSHION ONLINE TECH LTD
Network information interaction method and network security system
ActiveCN102447701ARealize the requirements for real-time referencingEasy to identifyCharacter and pattern recognitionPlatform integrity maintainanceData displayData collaboration
The invention relates to the field of computer security protection, in particular to a network information interaction method and a network security system. The network information interaction method comprises the following steps: firstly constructing a heterogeneous data collaboration server for an external network, restoring external network data displayed in different forms into information in an XML (Extensible Markup Language) format, screening and uniformizing, and translating the information in the XML format into Unicode; constructing a recognition and control system for an internal network, displaying the Unicode and control identification with variable color on a display, starting a photographing program and intercepting an image on the screen of the current display by a photography or videography device when the control identification is changed into specific color; and restoring an image file into XML information in a data recognition and control server by adopting an OCR (Optical Character Recognition) technology, and leading the XML information into a corresponding internal network database through a data interface. The network security system takes an image recognition technology as a core, internal and external network equipment is not physically connected, and the data is screened before leading and connection so as to realize real-time data leading and connection on the basis of true physical isolation.
Owner:HEFEI HUARUAN TECH
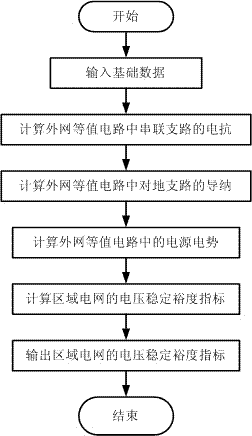
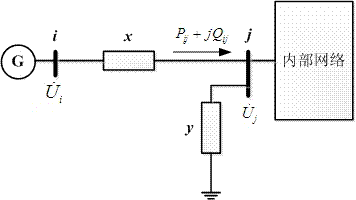
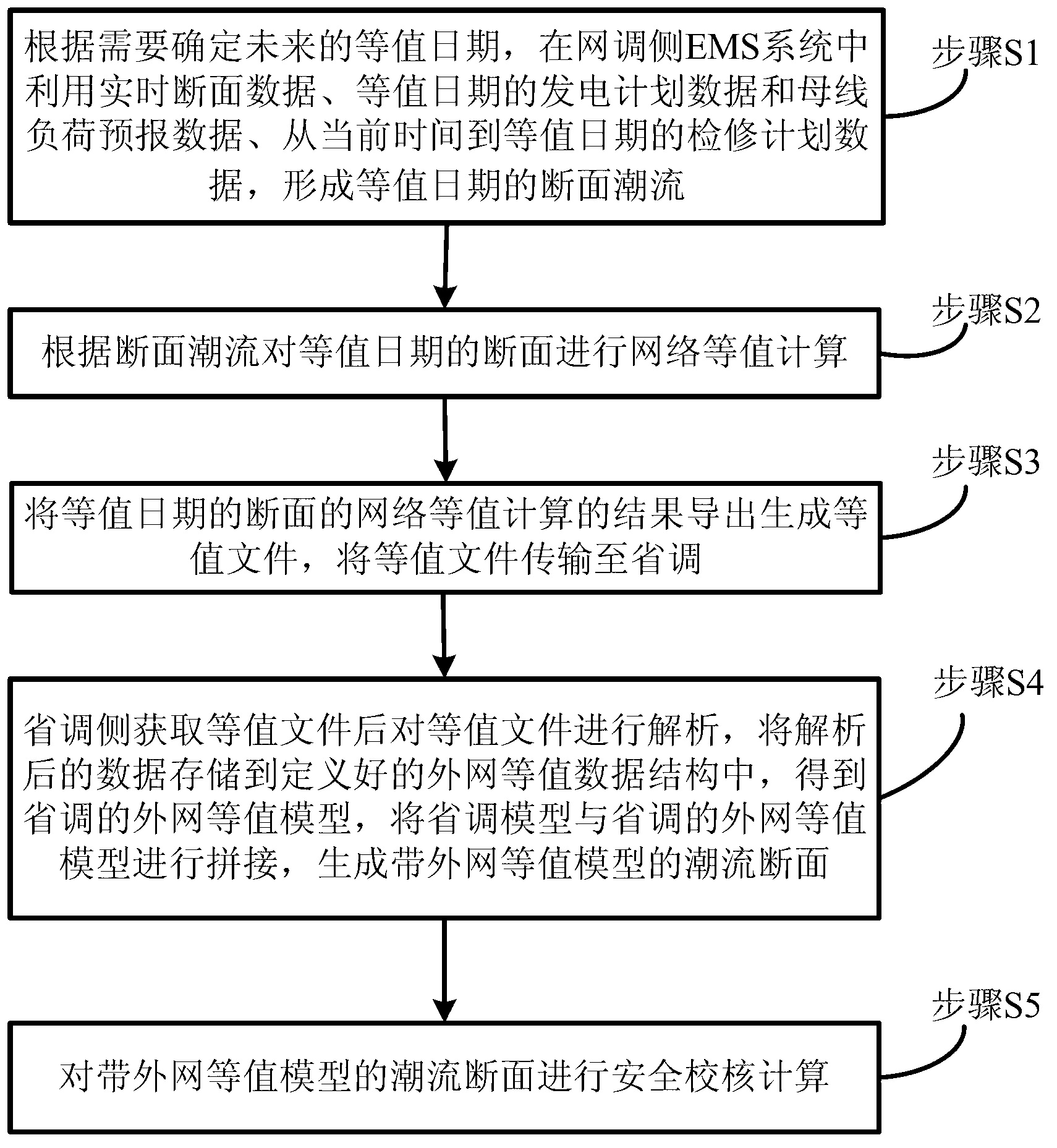
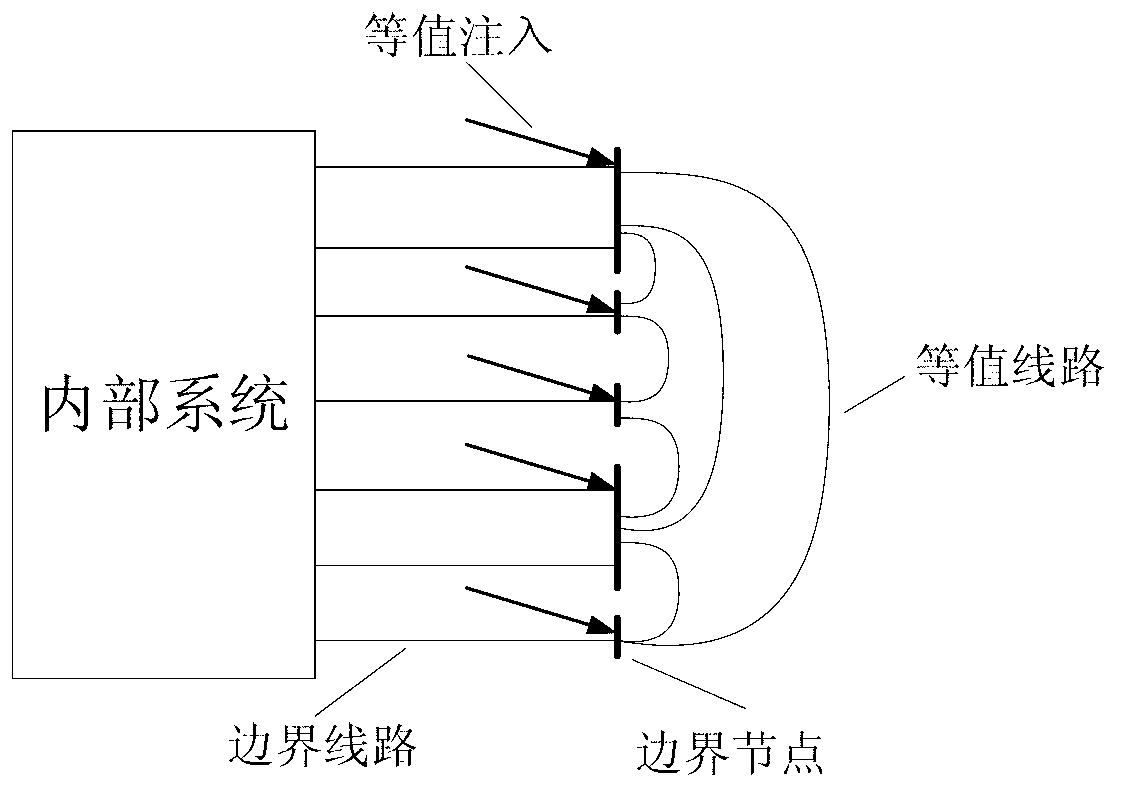
Method for calculating voltage stability margin of regional power grid by considering outer network equivalence
ActiveCN102420427ACorrect reflectionCorrectly reflect the impactComplex mathematical operationsAc network circuit arrangementsElectric power systemControl engineering
The invention discloses a method for calculating a voltage stability margin of a regional power grid by considering outer network equivalence and belongs to the technical field of analysis of static voltage stability of a power system. The method comprises the following steps of: adding a ground branch circuit into a conventional David south model to make an outer network equivalent; calculating outer network equivalence reactance and ground admittance by using a computer through a program according to outer network information under a typical running mode; calculating equivalent power supply electric potential according to inner network measured data and finally calculating an index of the static voltage stability margin of the regional power grid. By the method, the influence of the outer network on the ground branch circuit can be considered effectively and the problem of parameter drift in the conventional David south equivalence method can be solved effectively; therefore, the calculation precision of the stability margin index is high. In the method, only the information under the typical running mode of the outer network is needed and the data under all the running modes of the outer network is not needed, so that the requirement on the data of the outer network is low, the engineering practicability is high and the popularization and application are facilitated. The method can be widely applied to calculation and analysis of the index of the static voltage stability margin of the regional power grid which is connected with the outer network through a single point.
Owner:STATE GRID CORP OF CHINA +4
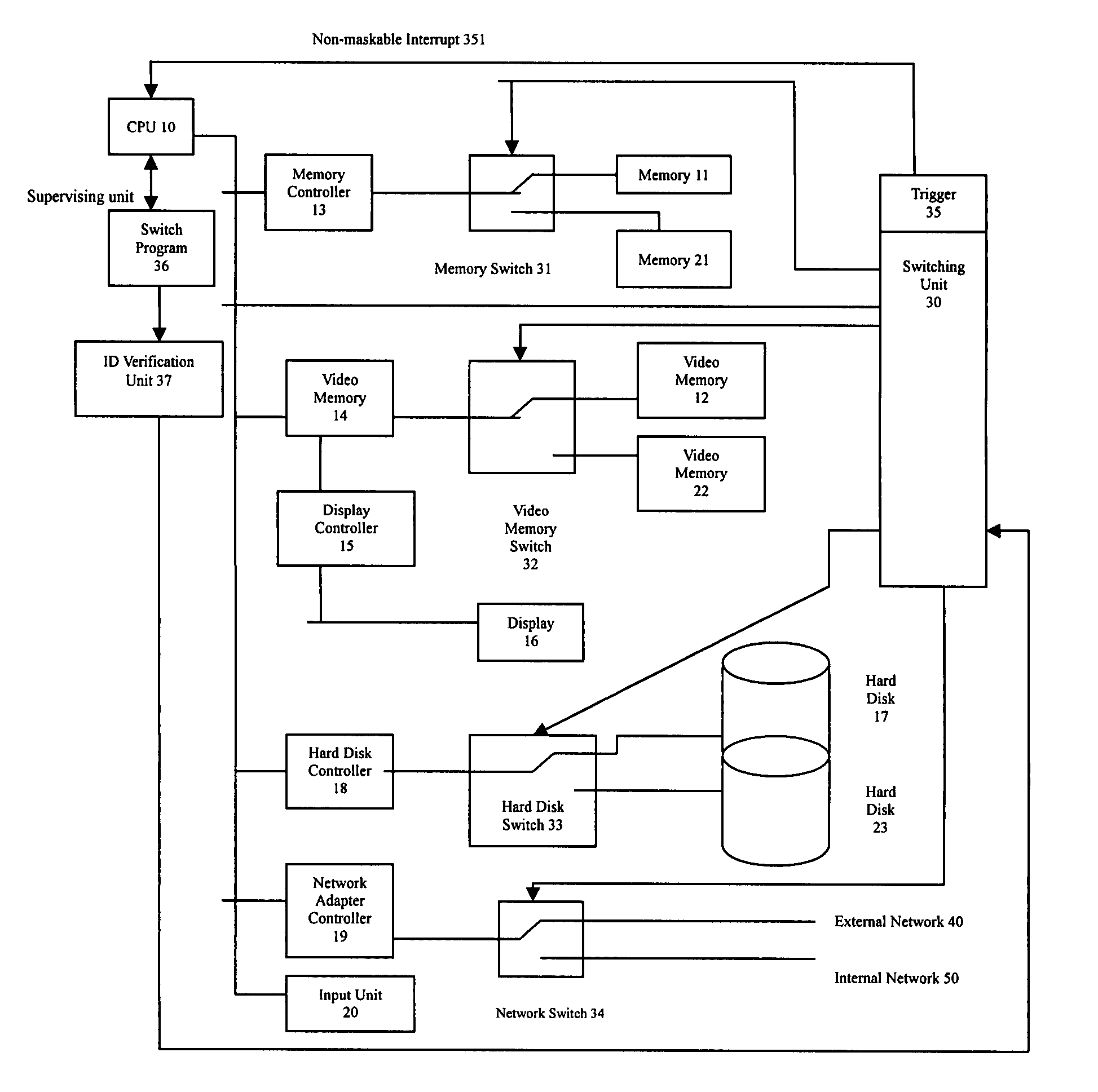
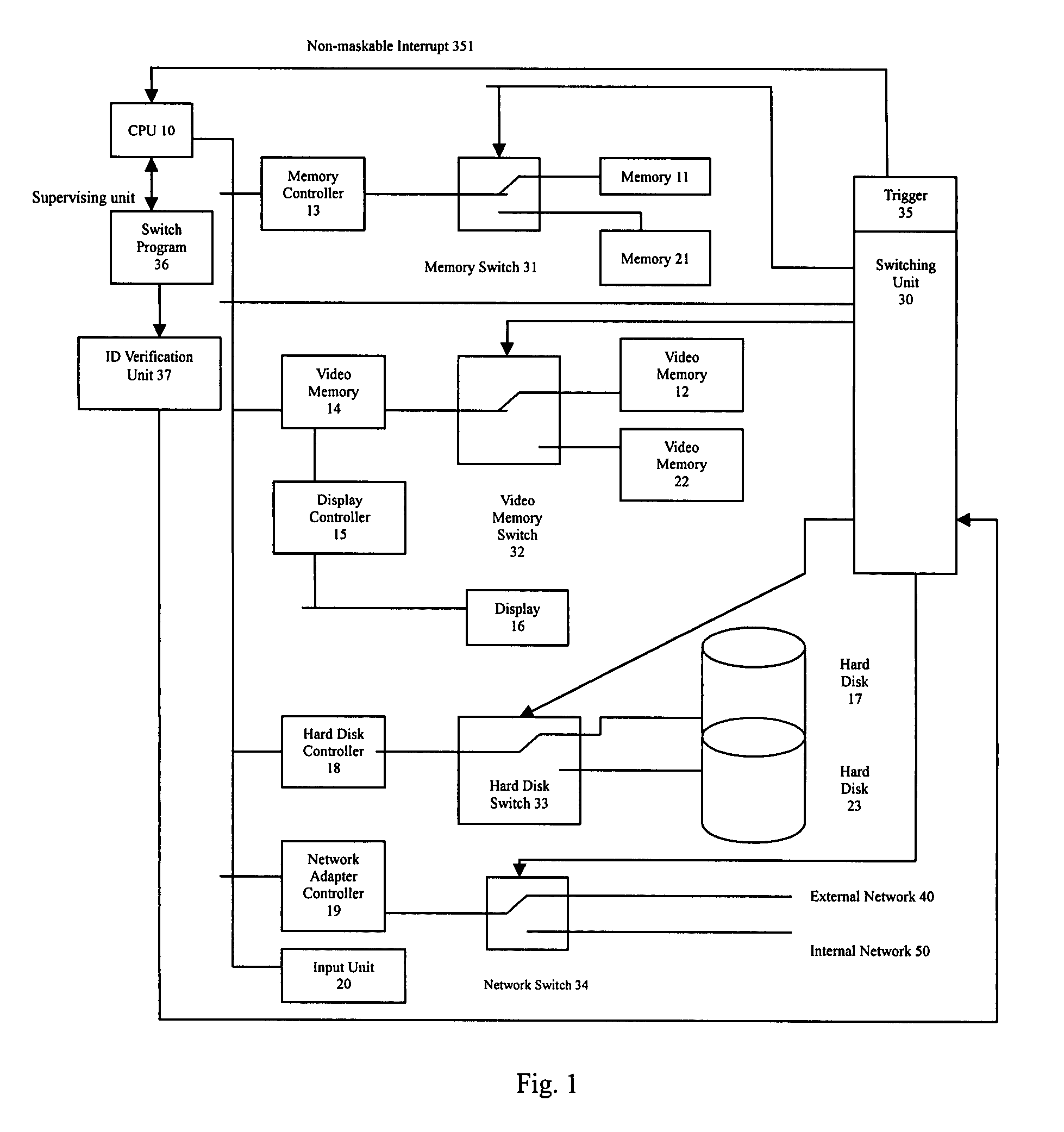
Computing system being able to quickly switch between an internal and an external networks and a method thereof
InactiveUS7370193B2Ensure physical separationQuick switchAnalogue secracy/subscription systemsData resettingNon-maskable interruptUser input
The invention discloses a computing system such as a computer, a Personal Digital Assistant, or a mobile phone, being connected both to an internal network and an external network and being able to quickly and safely switch therebetween without being shut down while ensuring a physical separation between the two networks. When a user inputs a request of switching, a switching unit will set a trigger thereof and generate a consequent non-maskable interrupt to CPU. After receives the NMI, the CPU controls the switching unit to run a switch program kept therein to back up a current status of the system. Then the switch program backs up a current status, controls the switching unit to interrupt all serving programs and loads the other status other than the current status to the computing system, and finally control the switching unit to reset the trigger.
Owner:SHAO TONG
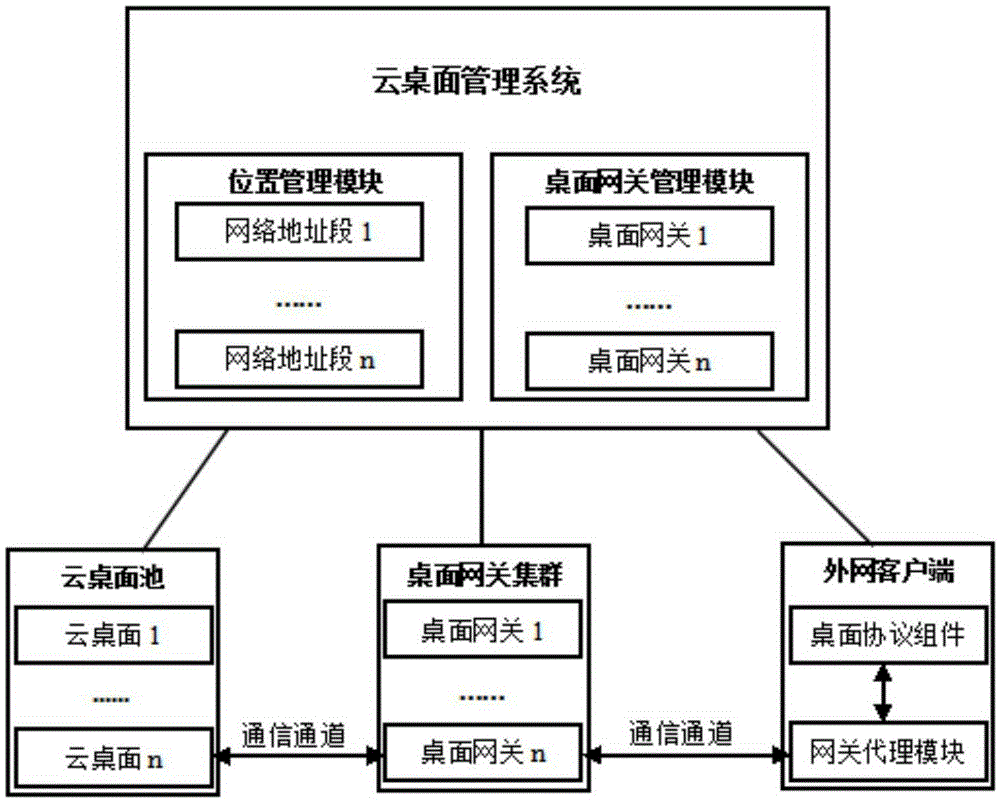
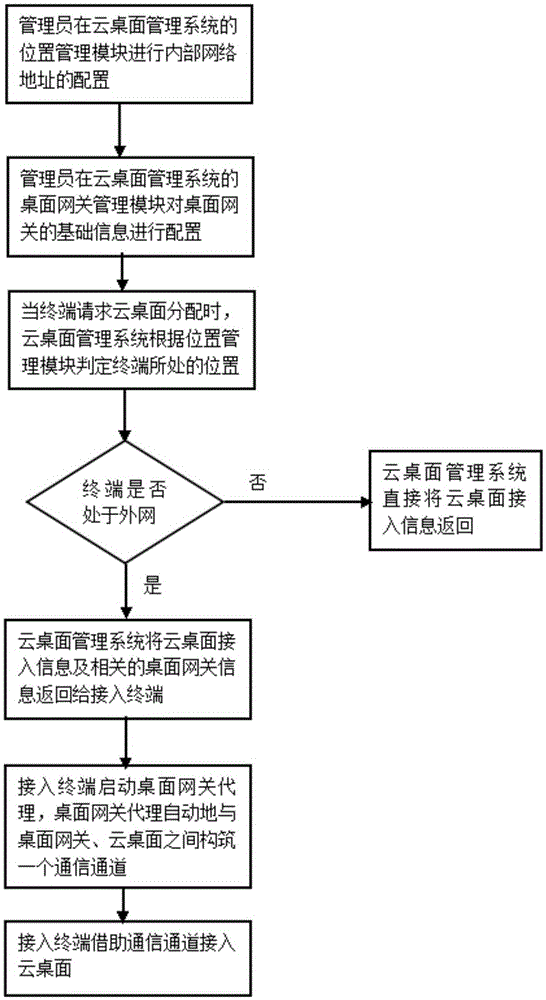
Method for external network client to access private cloud desktop
The invention provides a method for an external network client to access a private cloud desktop. In the method, a position management module in a cloud desktop management system is used to manage an internal network address so that the external network client in an internal network can be directly communicated with the cloud desktop. When being in an external network, the client can be communicated with the cloud desktop through a desktop gateway. An access mode of the internal and external networks is completely transparent and unperceived to a terminal user. The external network client does not need to manually set corresponding desktop gateway information.
Owner:广州云晫信息科技有限公司
Internal and external network parallel running system for database merging and method of database merging
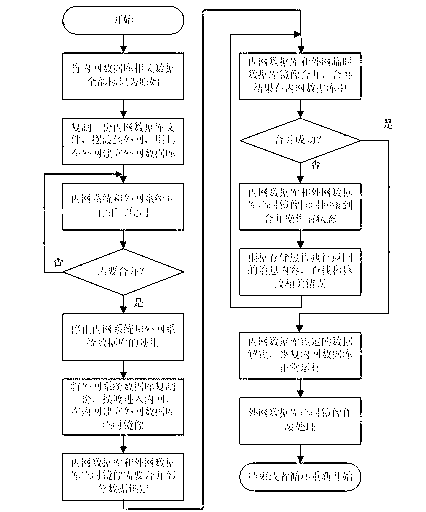
An internal and external network parallel running system for database merging comprises an internal network database management system, an external network database management system, and an all-weather physical isolation system, wherein the internal network database management system and the external network database management system are isolated from each other by the all-weather physical isolation system, and exchange data by ferrying equipment; an external network database temporary mirroring unit imports external network data in an external network data table of the external network database temporary mirroring unit into an intermediate data table; the intermediate data table merges the imported data in an internal network data table; and transaction-based double rollback error treatment is performed on the intermediate data table and the internal network data table after merging. With the adoption of the method, not only can the correct merging of the data in the data tables be realized, but also the out-of-control data during the date merging can be avoided effectively, and the parallel running of an internal network system and an external network system of the all-weather physical isolation system is ensured.
Owner:SHANGHAI SPACEFLIGHT INST OF TT&C & TELECOMM
Generation method of panoramic video code stream based on body area sensing array
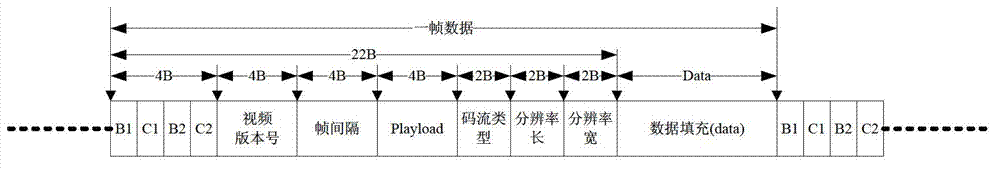
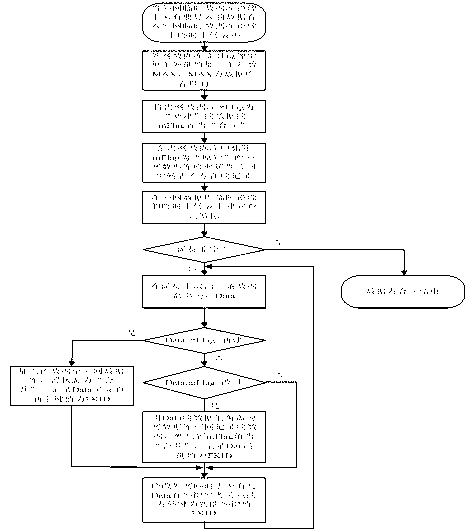
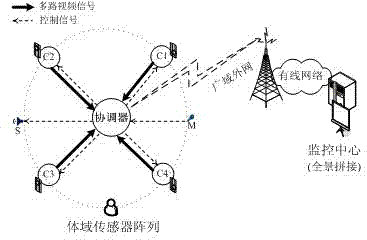
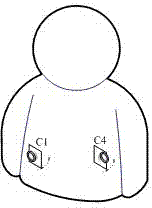
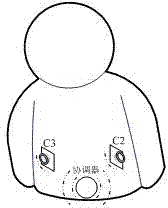
InactiveCN102244680AFlexible layoutRealize synchronous acquisitionClosed circuit television systemsTransmissionUltra-widebandOriginal data
The invention provides a generation method of panoramic video code stream based on a body area sensing array. The generation method is characterized in that the body area sensing array consists of a coordinator and a plurality of sensor nodes which are distributed on a garment of human body, and a star topology ultra wideband body area network is adopted in intercommunication between the coordinator and the sensor nodes; in multi-channel acquisition tasks, the plurality of the sensor nodes are controlled to perform cylindrical projection panoramic imaging within a horizontal visual field at 360 degrees around a wearer, and the acquired multi-channel video images are transmitted into double super-frame buffer areas for synchronous caching and scheduling; in multi-view encoding tasks, multi-channel raw video data is subject to multi-view video encoding according to high-performance sub-frame-level encoding sequence; and in a remote transmission task, compressed code stream of multi-source panoramic video is returned to a monitoring center in real time through an external wide area network. The generation method provided by the invention has the beneficial effects that effective balance between system resource and code stream quality is realized, and overall effectiveness of low power consumption, low latency and high quality is obtained while system concealing property is improved.
Owner:DONGHUA UNIV
Connection transfer method and equipment
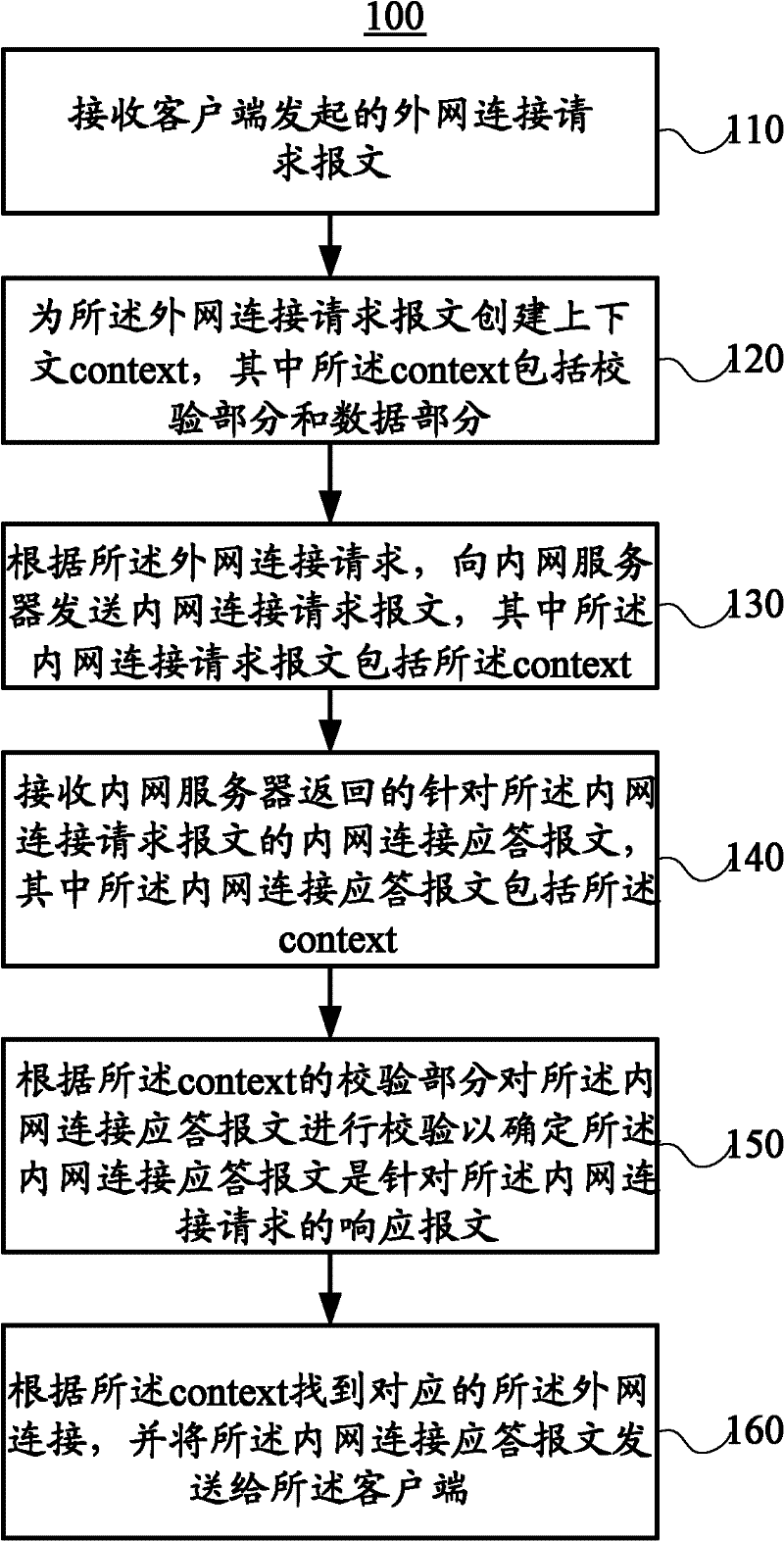
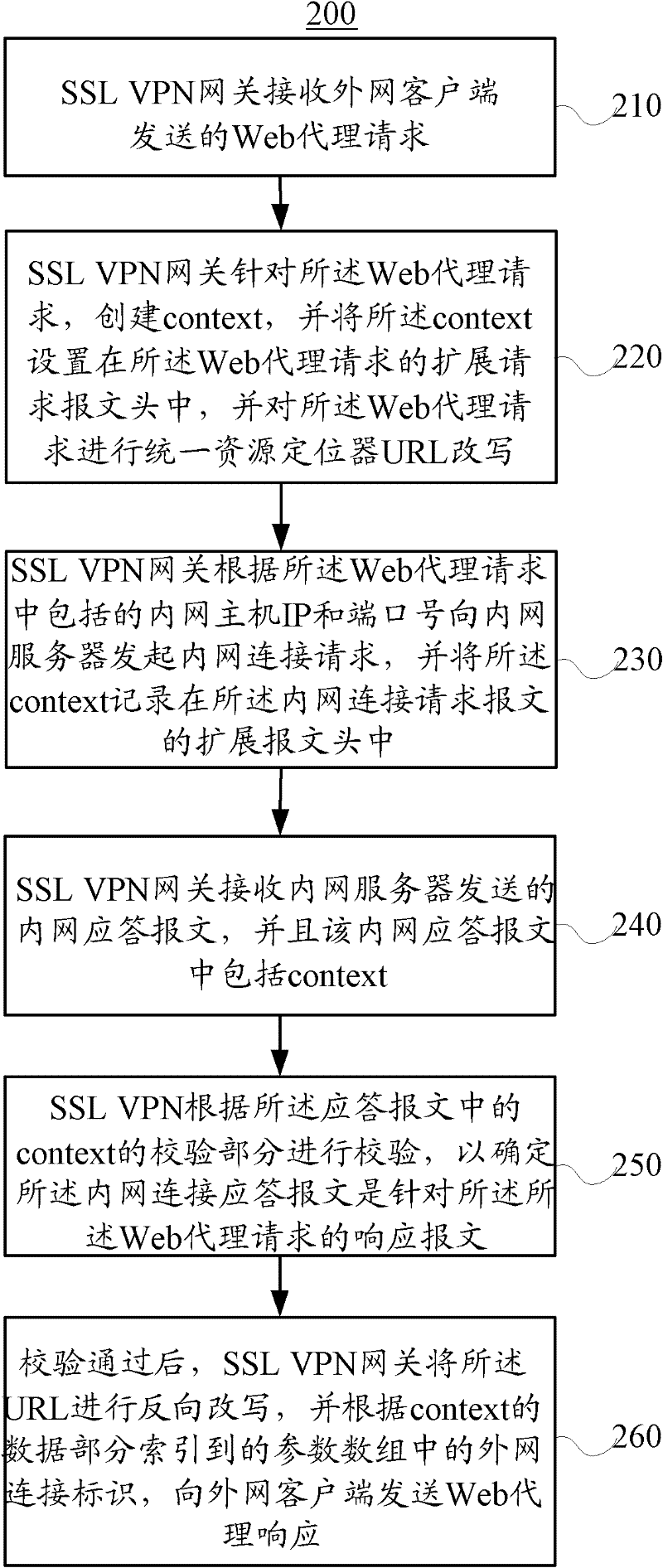
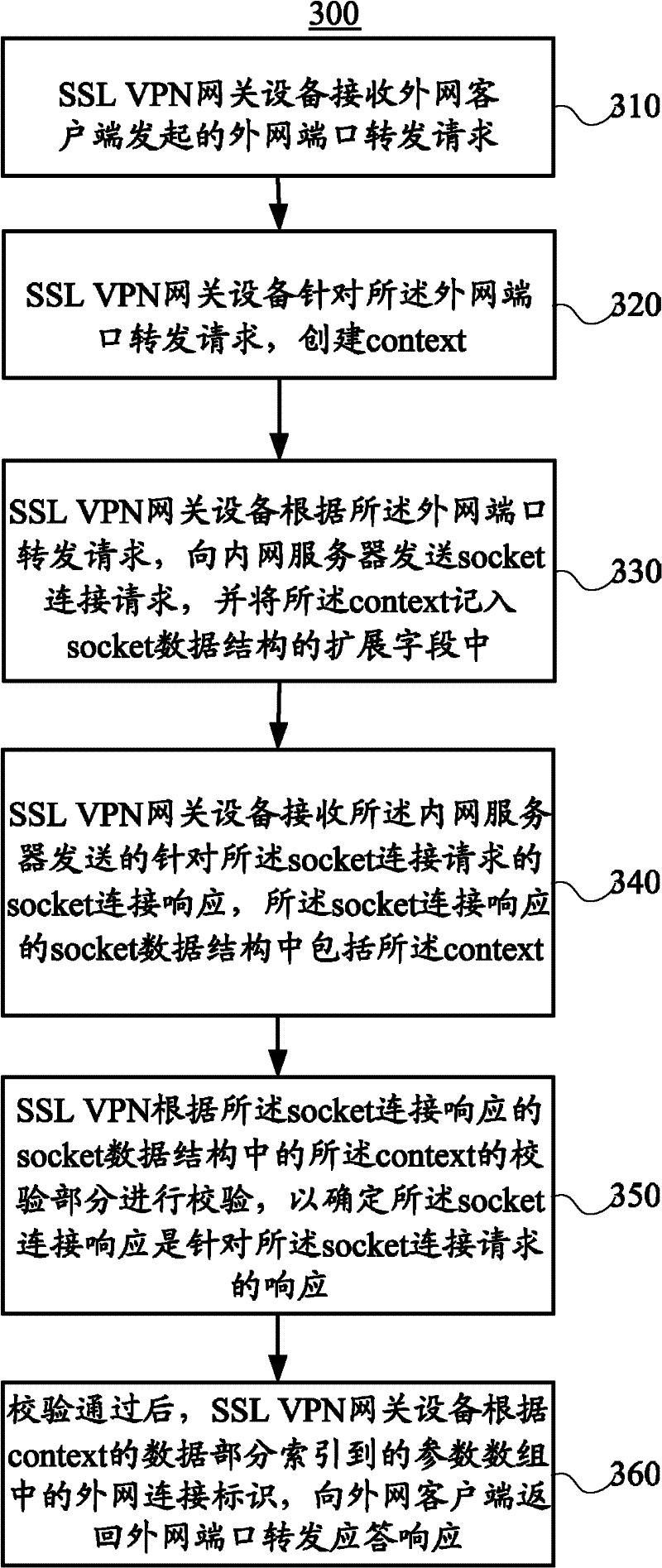
ActiveCN102413176AEnsure safetyGuaranteed normal transmissionNetworks interconnectionRelevant informationClient-side
The invention relates to a connection transfer method and equipment. The method comprises the following steps of: receiving an internet connection request message which is initiated by a client by using gateway equipment; creating a context for the internet connection request message; transmitting an intranet connection request message to an intranet server according to the internet connection request message; receiving an intranet connection response message for the intranet connection request message from the intranet server; checking the intranet connection response message according to the checking part of the context in the intranet connection response message, and after the intranet connection request message passes the checking, finding corresponding internet connection according to the data part of the context; and transmitting an internet connection response message to the client according to the internet connection response message. According to the embodiment of the invention, when connection is established between intranet and internet, the context is set in extended message headers on a wide area network (WAN) side and a local area network (LAN) side, and after the messages are received, related information is directly indexed according to the context for connection checking and message forwarding, so that data is ensured to be transmitted securely and highly efficiently.
Owner:HUAWEI TECH CO LTD
Restaurant management system and method by mobile phone
The invention provides a restaurant management system and method by a mobile phone. The restaurant management system comprises an NFC (Near Field Communication) electronic tag and terminal equipment, wherein the NFC electronic tag comprises an NFC data transmitting module and a two-dimensional code tag; the NFC data transmitting module is used for transmitting restaurant information to the terminal equipment; the two-dimensional code tag is used for recording the restaurant information; the terminal equipment is used for acquiring restaurant information from the NFC electronic tag, then generating restaurant data of a place where a user is positioned according to the restaurant information and transmitting the restaurant data of the place where the user is positioned to an outer network server. The restaurant management system and method provided by the invention have the advantages of simplicity, convenience, activity, accuracy and timely property when being used for managing the catering process of the user and can be widely suitable for the fields of business restaurant.
Owner:上海照恒科技有限公司
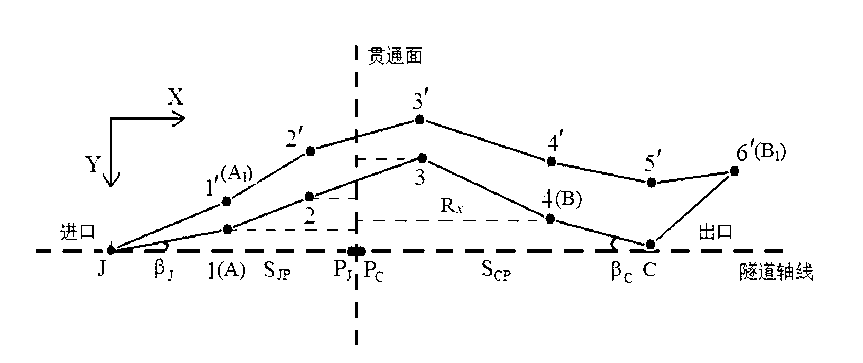
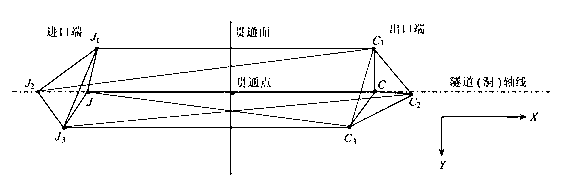
Estimation method of extra-long tunnel horizontal through error
ActiveCN103196425ASimple designSolving Penetration Control Measurement ProblemsHeight/levelling measurementEstimation methodsClassical mechanics
The invention relates to an estimation method of an extra-long tunnel horizontal through error. Hole exterior and hole interior control measuring errors are not inevitable when a tunnel is excavated, and so that the tunnel opposite excavation has the through error. The estimation method provided by the invention comprises the following steps of: establishing a hole exterior horizontal control network, obtaining a breakthrough point coordinate form an inlet point, an outlet point and a directional point, estimating the horizontal through error caused by a hole exterior horizontal control measuring error according to a differential formula method; and then establishing a tunnel hole interior wire network, designing the wire network from the inlet and the outlet and a through surface in a simulating manner according to an equal side, and estimating a tunnel horizontal through error caused by the hole interior wire measuring error. The estimation method provided by the invention can be used for carry outing hole exterior GPS (Global Positioning System) network and hole interior wire net simulation and flat difference without measured data, the horizontal through error caused by the hole exterior GPS network measuring error and the horizontal through error caused by the hole exterior horizontal control measuring error of any length tunnel are estimated, and the problem of extra-long tunnel control measuring horizontal through error and control network optimization design is solved.
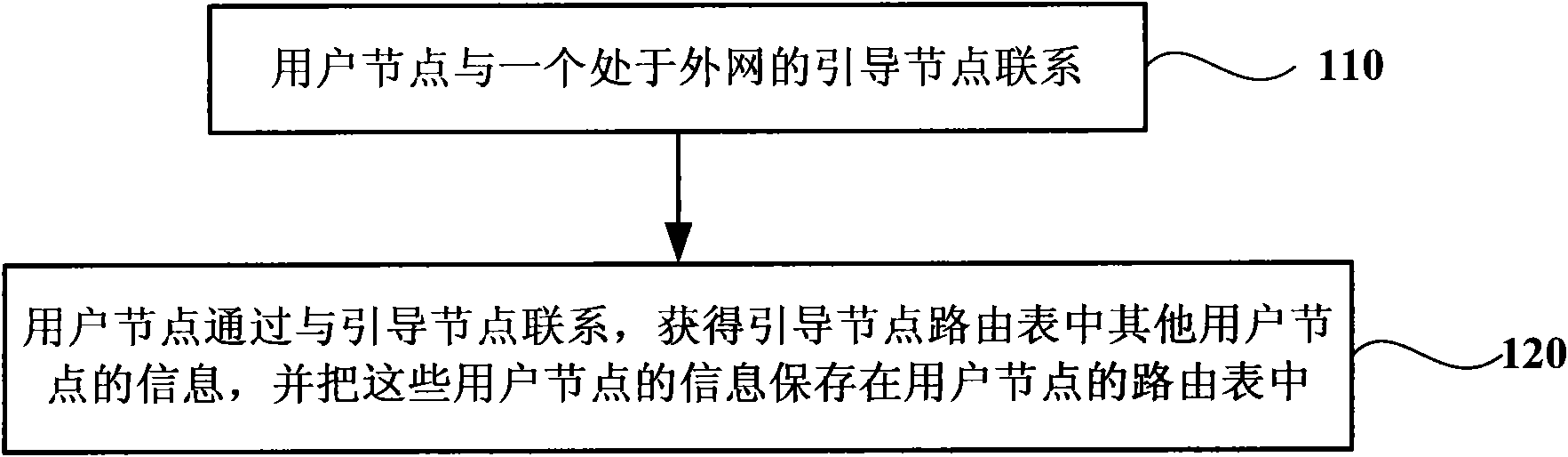
Owner:CHINA RAILWAY FIRST SURVEY & DESIGN INST GRP
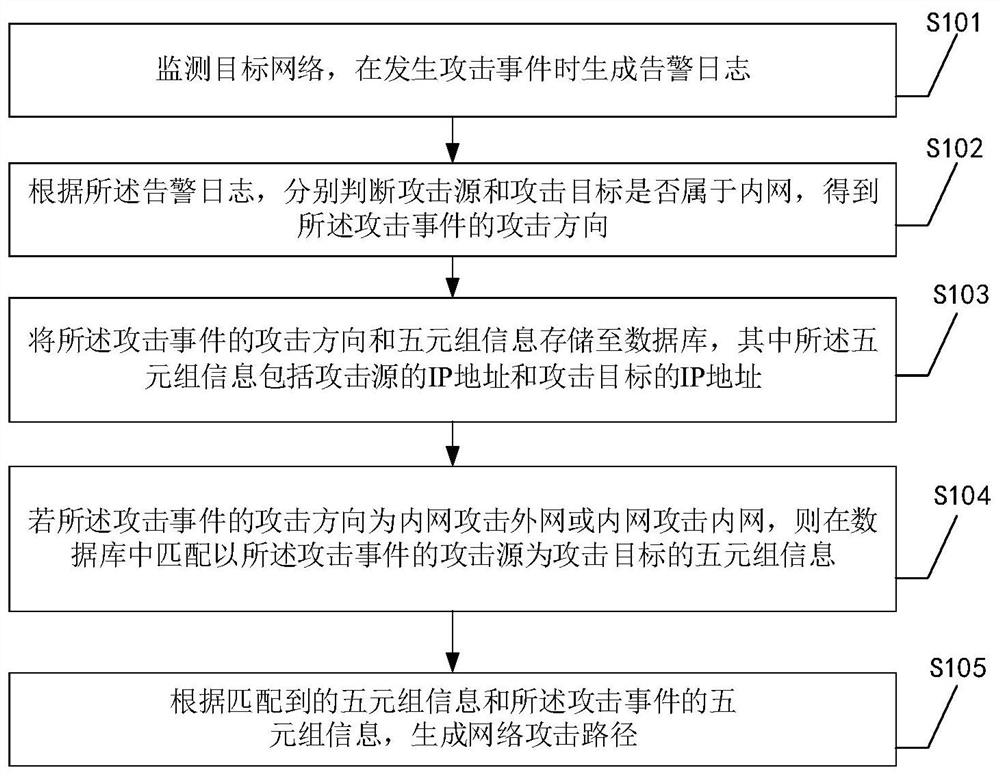
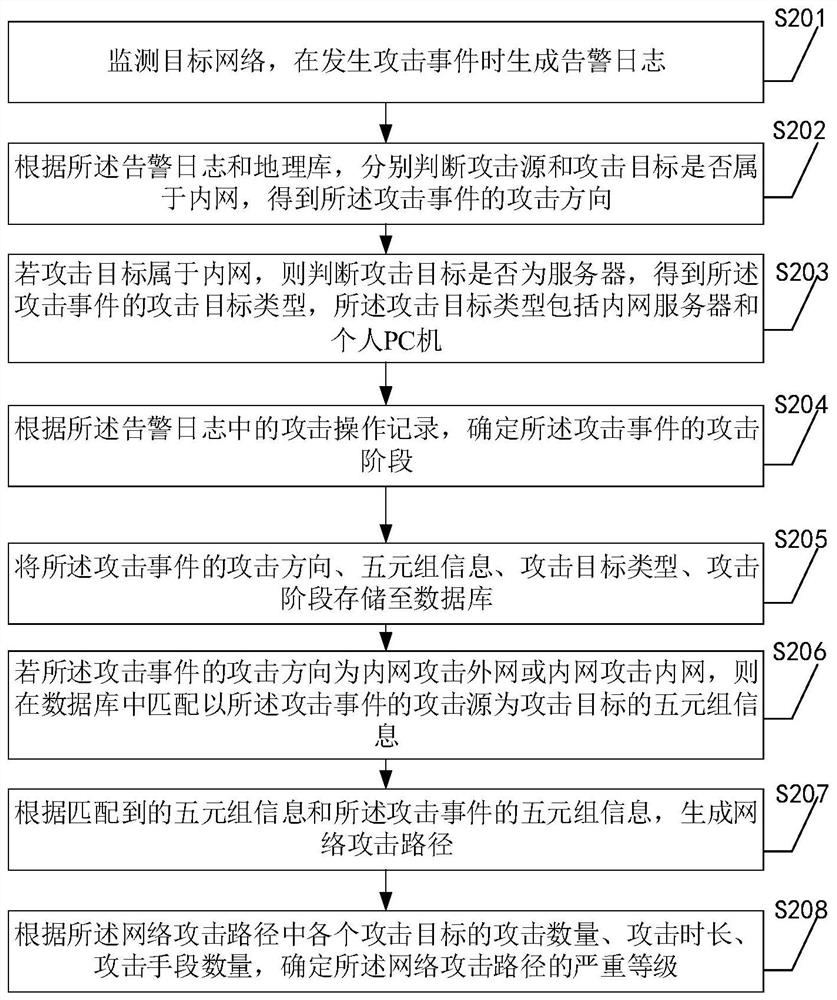
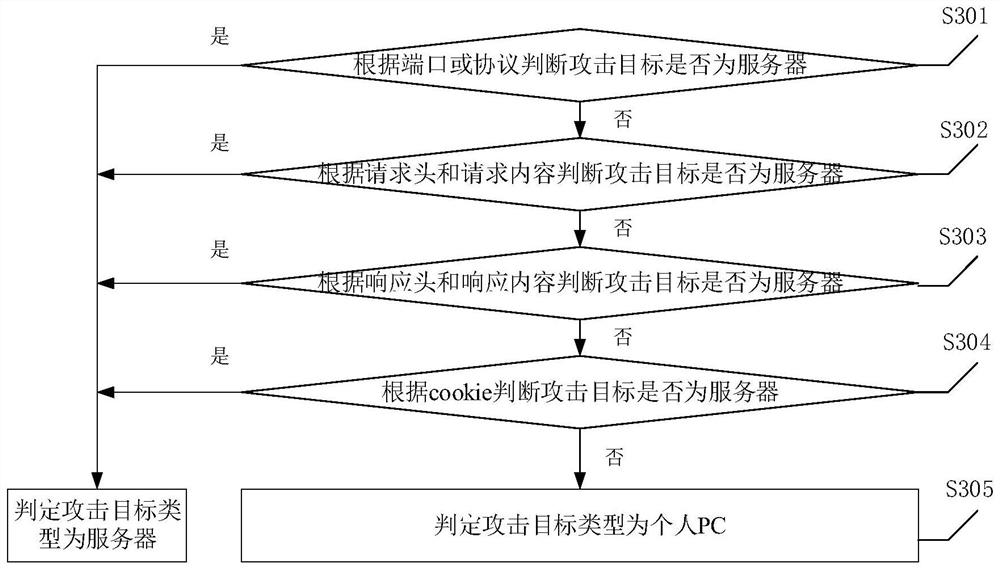
Network attack tracing method, device and equipment
ActiveCN111756759AImprove securityRealize automated monitoringTransmissionHigh level techniquesPathPingIp address
The invention discloses a network attack tracing method. According to the network attack tracing method, attack events in a network can be automatically monitored, an attack source and an attack target are distinguished according to an intranet or an extranet, an attack direction of a security event is determined, then the attack direction, an IP address of the attack source and an IP address of the attack target are stored in a database, finally, information related to the attack event is matched from the database, and a network attack path is generated according to a matching result. The purposes of automatically monitoring the attack event and analyzing the network attack path related to the attack event are achieved, and the network security is remarkably improved. In addition, the invention further provides a network attack tracing device, equipment and a readable storage medium, which have the technical effects corresponds to that of the network attack tracing method.
Owner:HANGZHOU ANHENG INFORMATION TECH CO LTD
Safety checking method for power system
ActiveCN103077480AImprove accuracyImprove rationalityData processing applicationsPower flowParallel computing
The invention provides a safety checking method for a power system. The method comprises the following steps of: S1, determining a further equivalence date as required, and forming interface power flow of the equivalence date on a network scheduling side; S2, performing network equivalence calculation on the section of the equivalence date according to the interface power flow; S3, deriving the result of the network equivalence calculation on the section of the equivalence date to generate an equivalence file, and transmitting the equivalence file to provincial scheduling; S4, obtaining the equivalence file on a provincial scheduling side, resolving the equivalence file, storing resolved data into a defined outer net equivalence data structure to obtain an outer net equivalence model of the provincial scheduling, and splicing a provincial scheduling model with the outer net equivalence model of the provincial scheduling to generate a power flow section provided with the outer net equivalence model; and S5, performing safety checking calculation on the power flow section provided with the outer net equivalence model generated in the S4. Safety checking is performed in comparison to a use history and the current outer net equivalence model, so that the accuracy of an obtained result is increased greatly.
Owner:CHINA ELECTRIC POWER RES INST +1
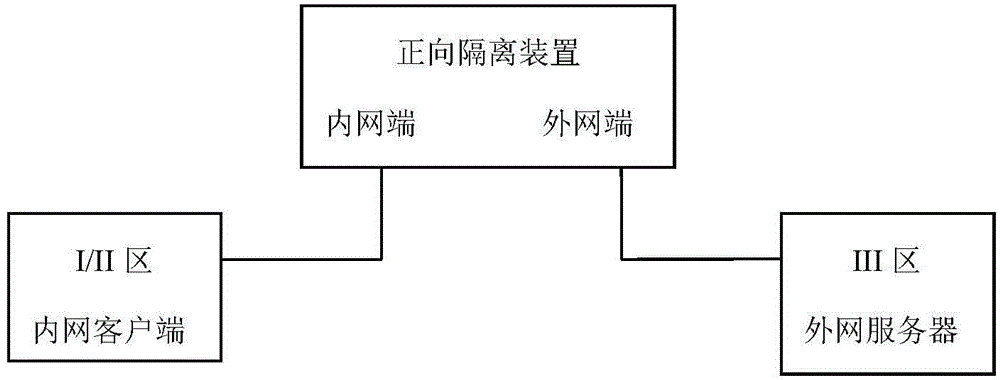
Method for simple data interaction between electric power region I and electric power III by using reserve 1bit data of forward direction isolating device
The invention discloses a method for simple data interaction between an electric power region I and an electric power region III by using reserve 1bit data of a forward direction isolating device, and relates to the technical field of data interaction of electrical power systems. The method is characterized by comprising the following steps: requiring an NAT conversion on IP of an outer net server on which a server-side software is mounted, initializing Socket at an end of the outer net server firstly, then binding with a port, listening into the port, after intranet client software receives a remote control check request, building socket connection with an outer net server-side software, and matching the equipment object unique code in a scheduling command with the equipment object unique code in a remote control constrain analysis request. The method provided by the invention is reasonable, can feedback information in time and is convenient to operate.
Owner:STATE GRID CORP OF CHINA +1
Popular searches
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com