Network attack tracing method, device and equipment
A network attack and attack source technology, applied in the computer field, can solve problems such as poor reliability and low efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
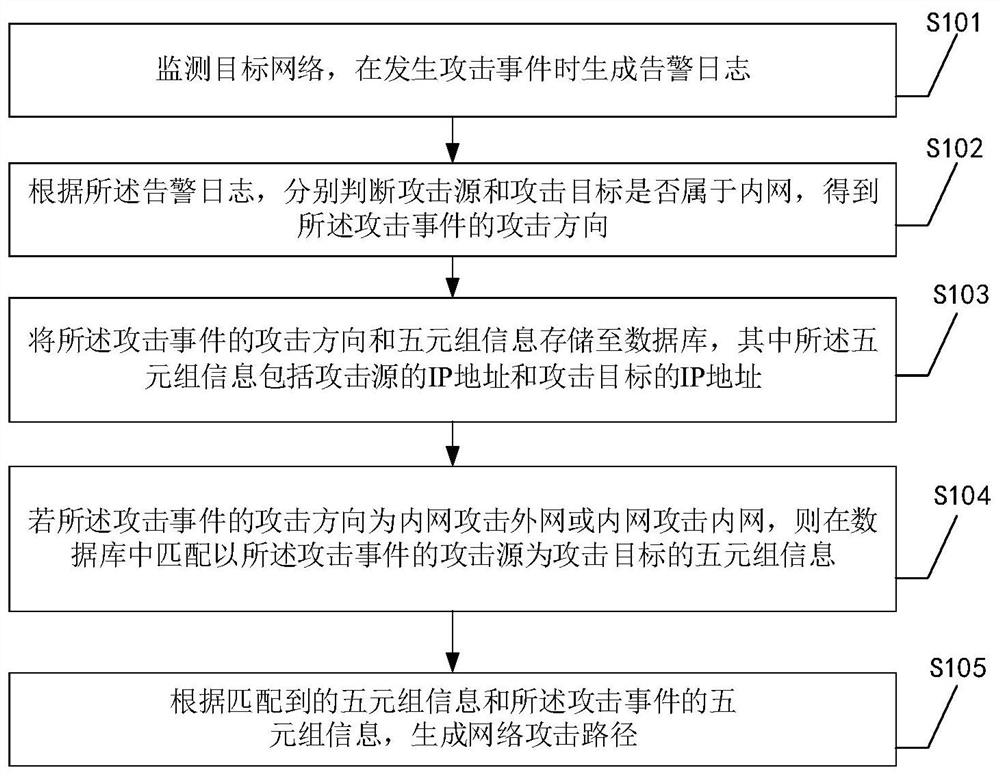
[0053] The following is an introduction to Embodiment 1 of a network attack source tracing method provided by this application, see figure 1 , embodiment one includes:
[0054] S101, monitor the target network, and generate an alarm log when an attack event occurs;
[0055] S102. According to the alarm log, respectively judge whether the attack source and the attack target belong to the intranet, and obtain the attack direction of the attack event;
[0056] S103. Store the attack direction and quintuple information of the attack event in a database, wherein the quintuple information includes the IP address of the attack source and the IP address of the attack target;
[0057] S104. If the attack direction of the attack event is that the internal network attacks the external network or the internal network attacks the internal network, match the quintuple information in the database with the attack source of the attack event as the attack target;
[0058] S105. Generate a net...
Embodiment 2
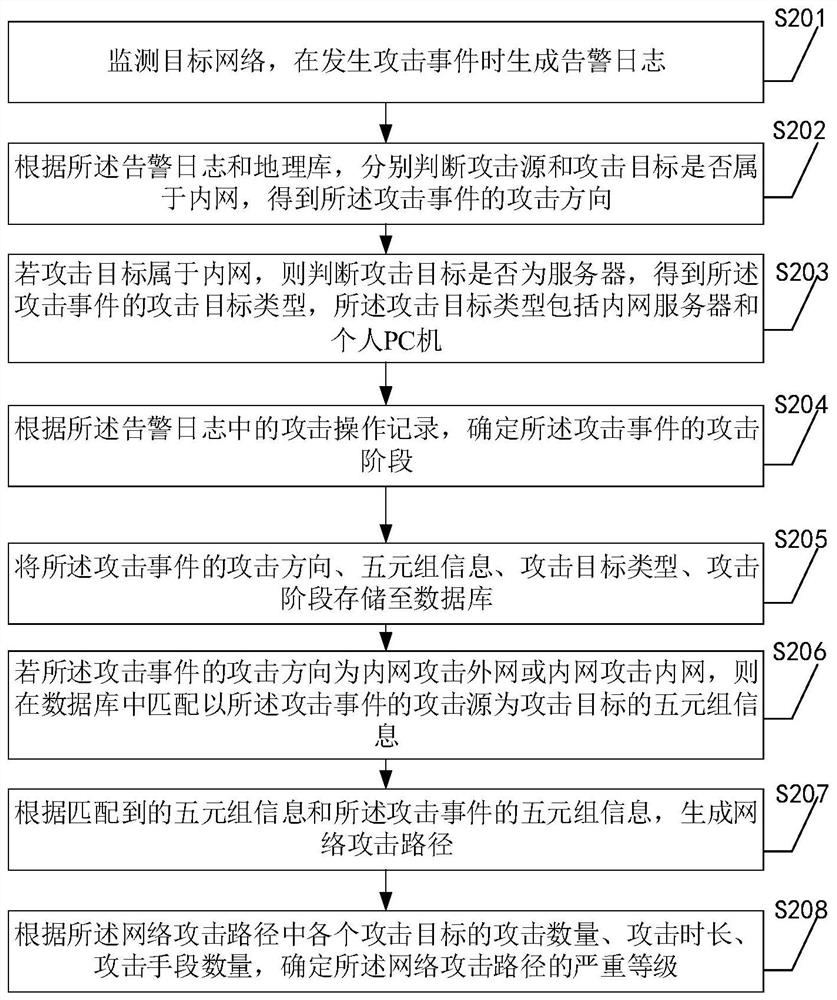
[0071] see figure 2 , embodiment two specifically includes:
[0072] S201. Monitor the target network, and generate an alarm log when an attack event occurs;
[0073] S202. According to the alarm log and the geographic database, respectively determine whether the attack source and the attack target belong to the intranet, and obtain the attack direction of the attack event;
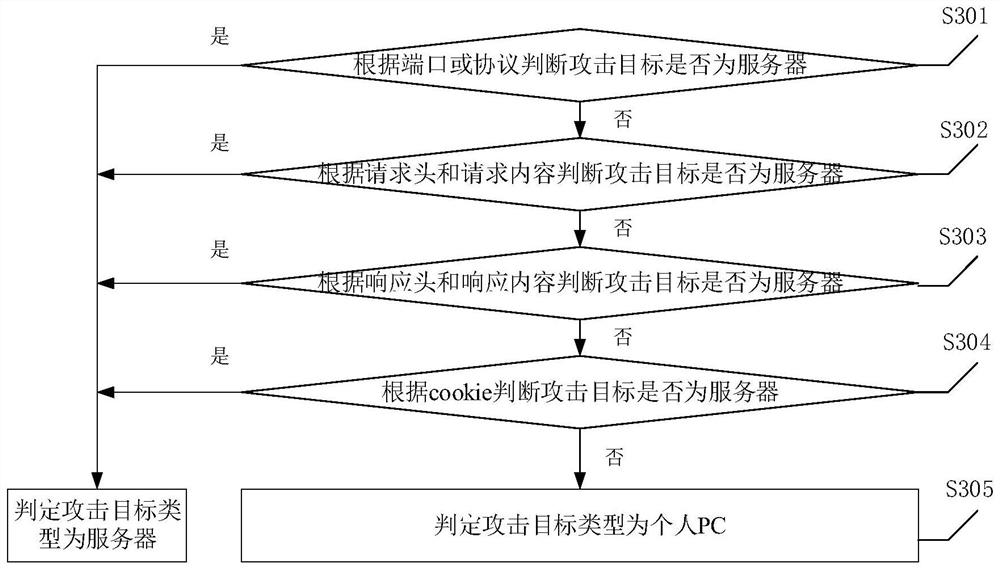
[0074] S203. If the attack target belongs to the intranet, judge whether the attack target is a server, and obtain the attack target type of the attack event, and the attack target type includes an intranet server and a personal PC;
[0075] S204. Determine the attack phase of the attack event according to the attack operation records in the alarm log, where the attack phase includes vulnerability detection, penetration intrusion, authority acquisition, command control, and data theft;
[0076] This embodiment traces the attack process, and divides the threat activities of the attack process into five ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com