Method and device for defending against network hostile attack
A malicious attack and malicious technology, applied in the field of network security, can solve the problem of port malicious attack, lack of effective defense, etc., to achieve the effect of protecting access, enhancing security, and securing network services
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
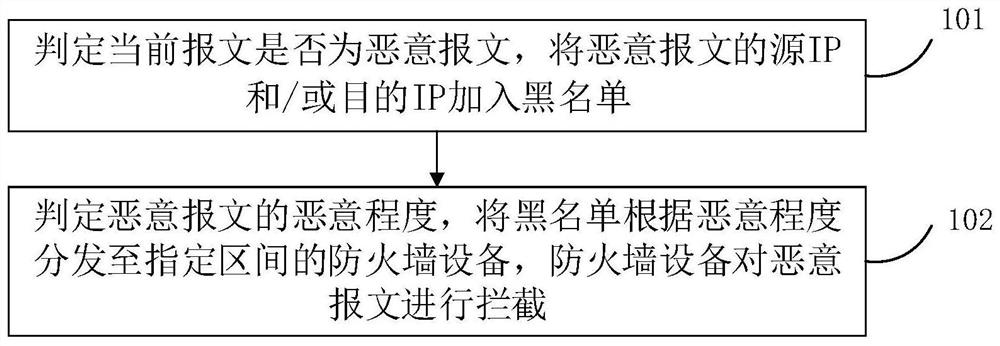
[0030] In the current firewall devices, the general protection measure is to block access according to the blacklist. This protection method can only be blocked according to the known blacklist, and must rely on the update of the blacklist, and the blacklist is usually only after being attacked. Updates are made and defenses are delayed. For high-performance firewall devices, the packet can also be parsed to determine whether it contains malicious feature fields. This method can identify and intercept attack behaviors in a timely manner, but requires the device to have better performance to parse packets and feature fields. In contrast, since the packet parsing and identification takes time, the packet forwarding time will be increased, and this method can only be defended after receiving malicious packets, that is, after actually being attacked. In an actual network environment, only a network node device with a firewall set up has the function of packet identification and in...
Embodiment 2
[0077] On the basis of the method for defending against malicious network attacks provided in the above-mentioned Embodiment 1, the present invention also provides a system for defending against malicious network attacks that can be used to implement the above method, such as Figure 4 As shown, it is a schematic diagram of an apparatus architecture according to an embodiment of the present invention.
[0078] It includes a management and control platform 1, a trap system device 2 and at least one firewall device 3, and the management and control platform 1, the trap system 2 and each firewall 3 device are interconnected through a network.
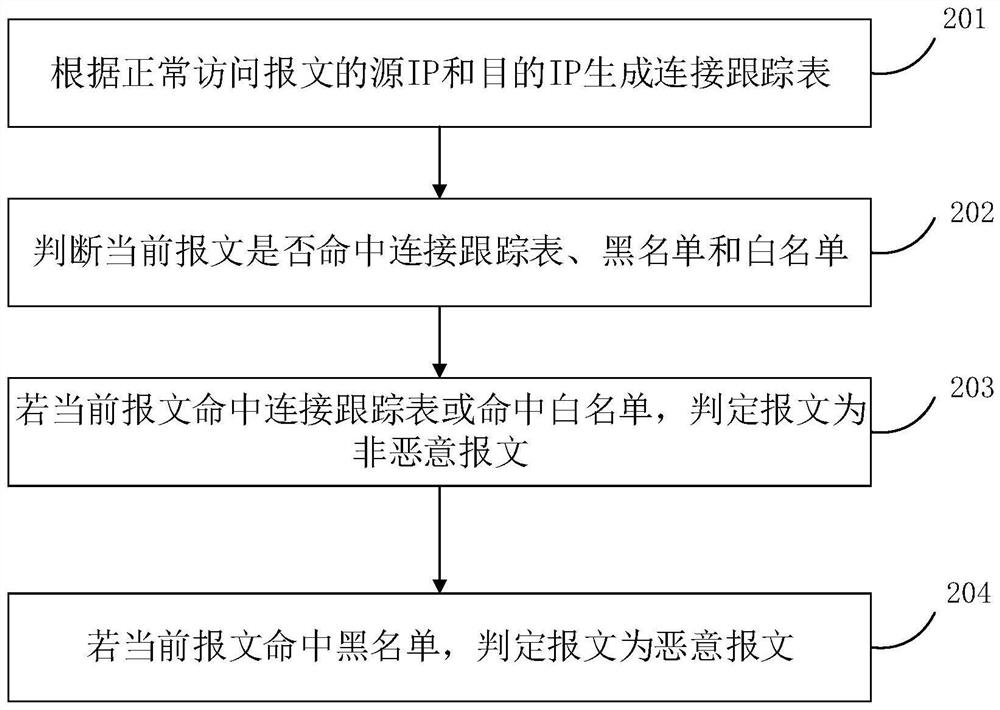
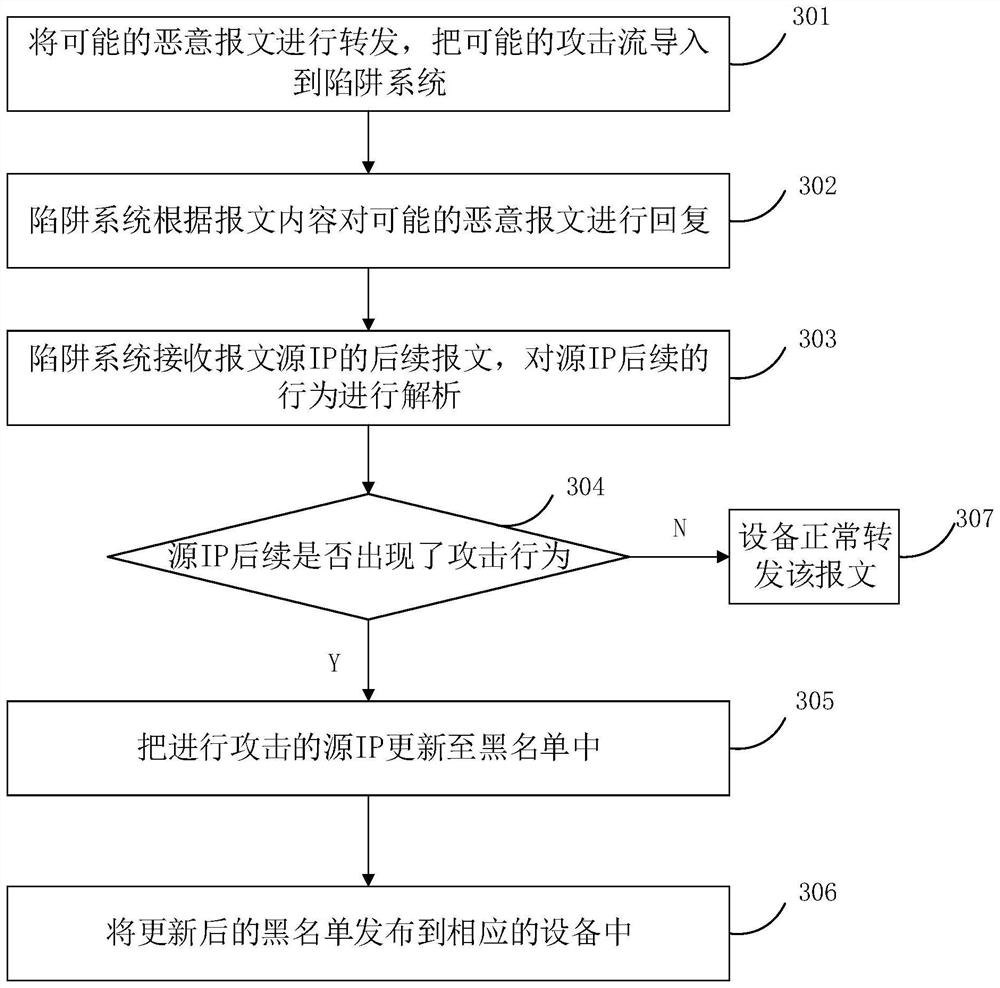
[0079] The management and control platform 1 analyzes the packet according to the method of step 101, determines whether there is a malicious attack according to the blacklist, connection tracking table and whitelist, adds the malicious attack information to the blacklist, and analyzes the possible malicious attack according to the method o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com