Method of establishing the trustworthiness level of participant in communication connection
A technology of trust level and communication connection, applied in key distribution, can solve the problem of high expected cost and achieve the effect of saving time
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0038] Next, typical embodiments of the present invention will be described.
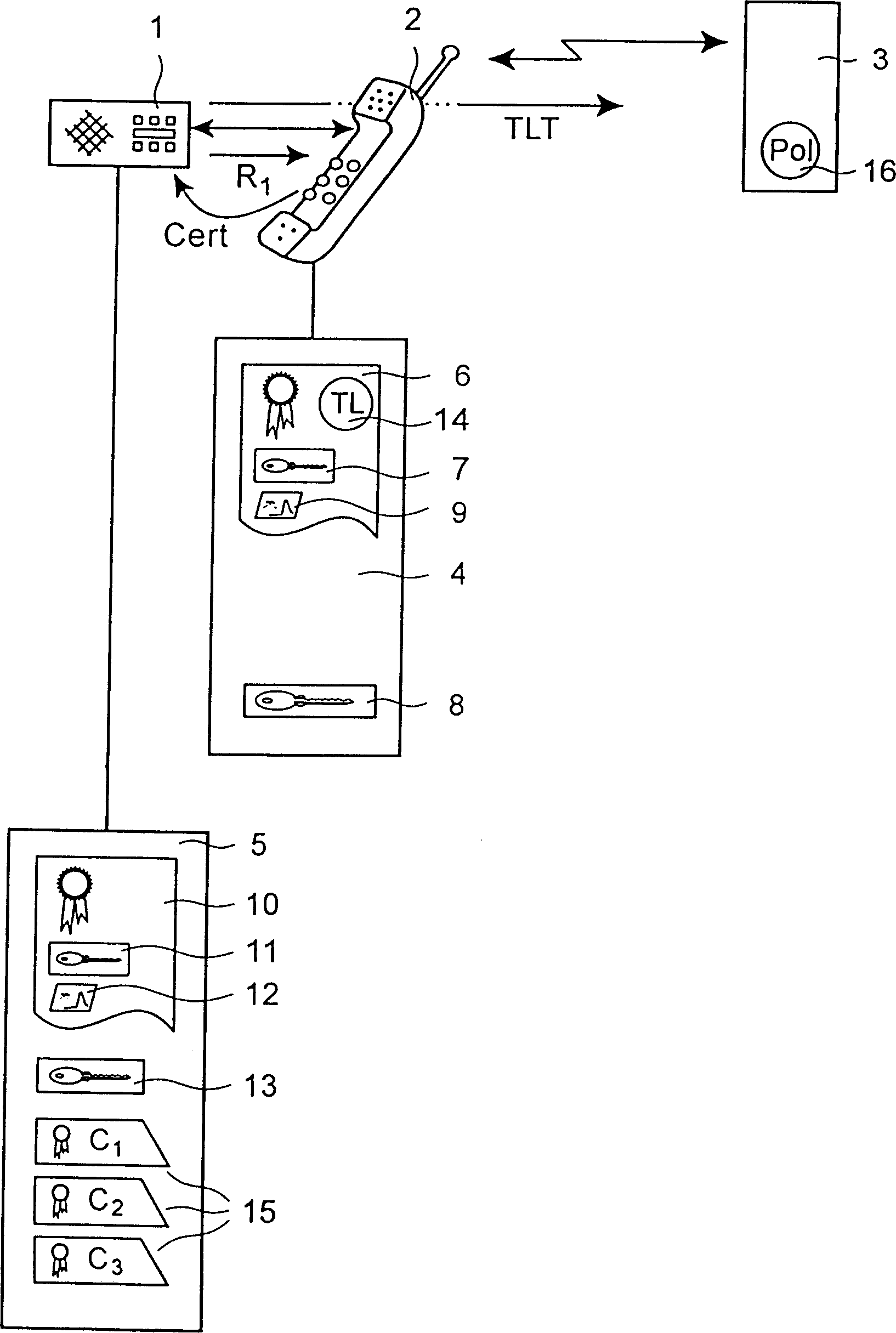
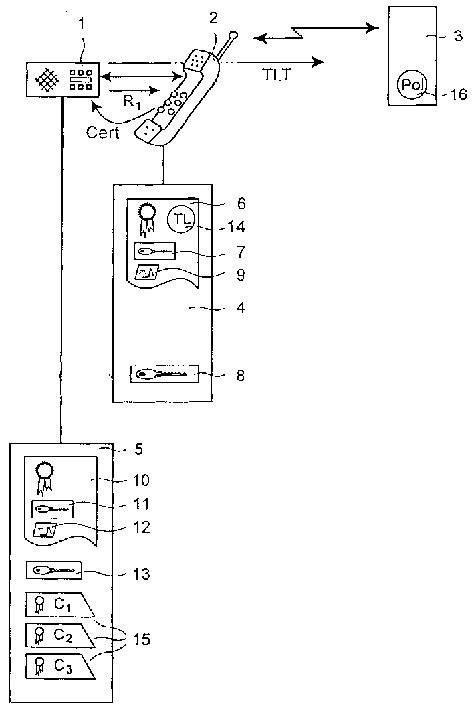
[0039] In Fig. 1, a system is shown, comprising a first communication party in the form of a smart card, a second communication party in the form of a back-end server 3 and a handset connected between the communication parties 1, 3 Form parties 2. The handset 2 includes a memory unit 4, also called a phone trust module, in which a trust certificate 6 is stored.
[0040] When the Smartcard 1 is inserted into the handset 2 to initiate a session via the communication link, the Smartcard 1 requests the transfer of the trust certificate 6 from the handset 2 .
[0041] The latter implementation is based on the principle of using public key cryptography, enabling one entity to generate a digital signature and another entity to verify the signature. However, other authentication methods may also be used.
[0042] Assume that the effective set of trust levels TL is represented by a list of L+1 integers 0,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com