Method for realizing peer-to-peer network system architecture
A peer-to-peer network and architecture technology, applied in the field of network and communication, can solve the problem of inability to penetrate firewalls and NAT routers, and achieve the effect of secure information exchange and resource sharing
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
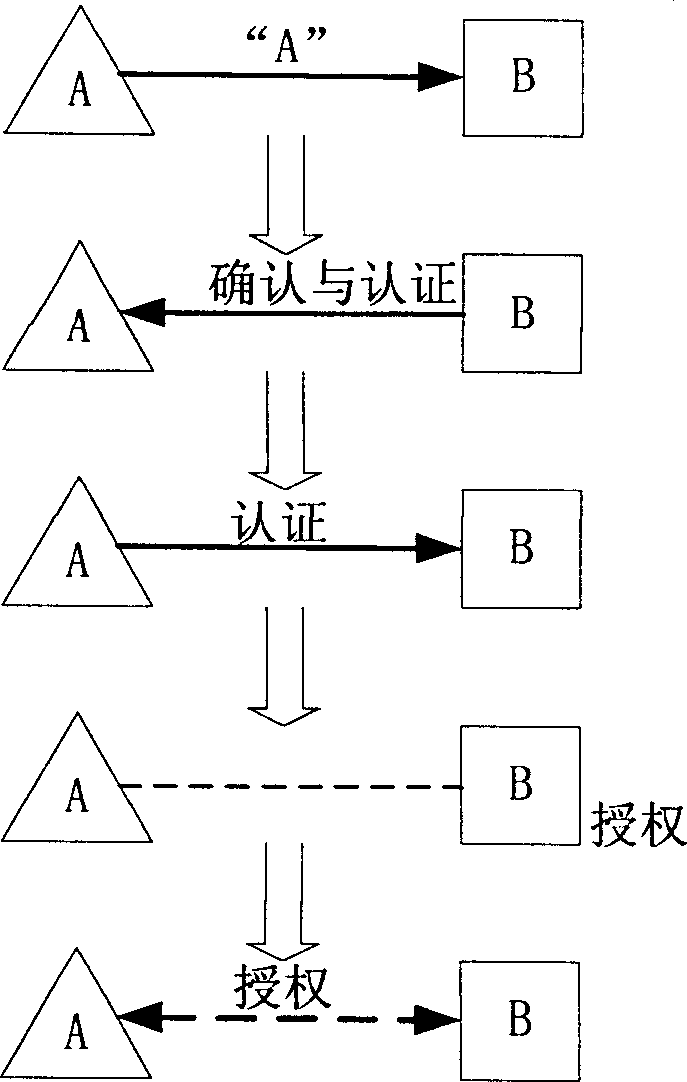
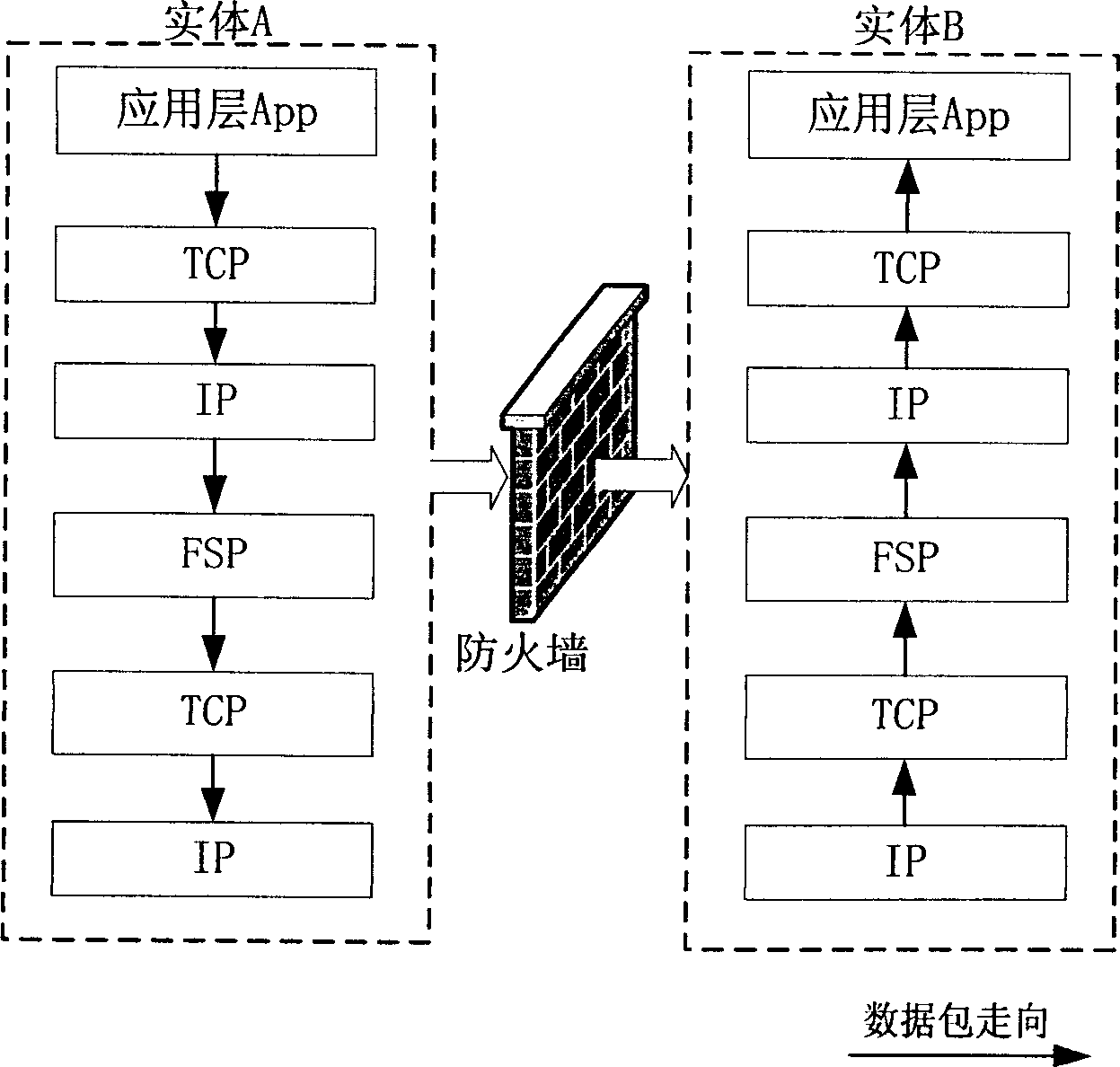
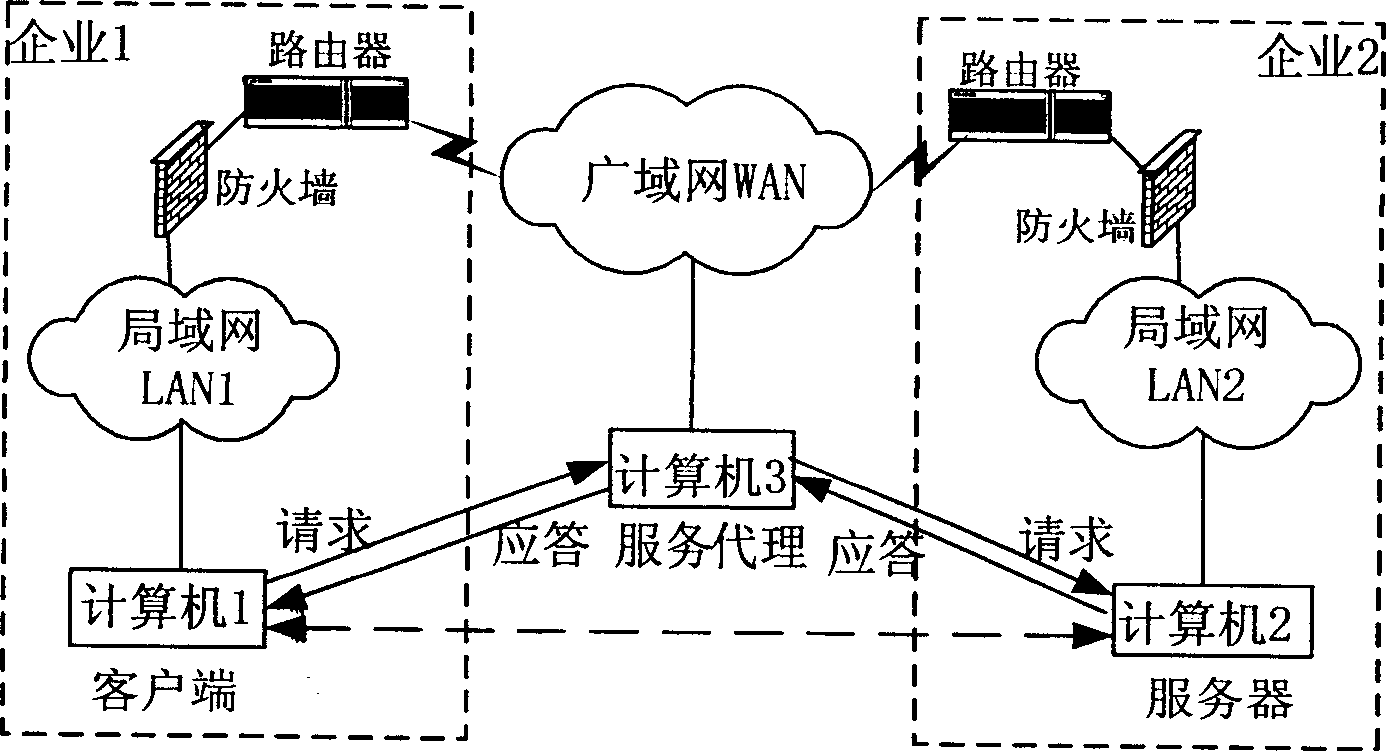
[0015] The steps to establish a peer-to-peer network between entities (peers) are as follows: figure 1 Shown: (1) Entity A newly connected to the network sends a notification message to one of the entity B in the online entity list through the UDP port, indicating that entity A is online; (2) Entity B receiving the information Return a response to the entity A that sent the information, confirming the receipt of the information and asking entity A to authenticate entity B, and at the same time send a data packet to it, the content of which is the name of all online entities that entity B knows. During the authentication process, both entity A and entity B exchange secret information with a shared key; (3) after entity A authenticates entity B, it adds the received list to entity A's online entity list and requires entity B to authenticate Entity A; (4) After Entity B authenticates Entity A, Entity A is added to the entity's online entity list, and Entity A is authorized to acc...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com