Safe access method for borad band network
A technology for secure access and broadband network, applied in the access field of network systems, can solve the problems of poor security, endanger network security, hidden dangers of DHCP server security, etc., and achieve the effects of isolation protection, improved security, and good security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0012] The present invention will be described in further detail below in conjunction with the accompanying drawings.
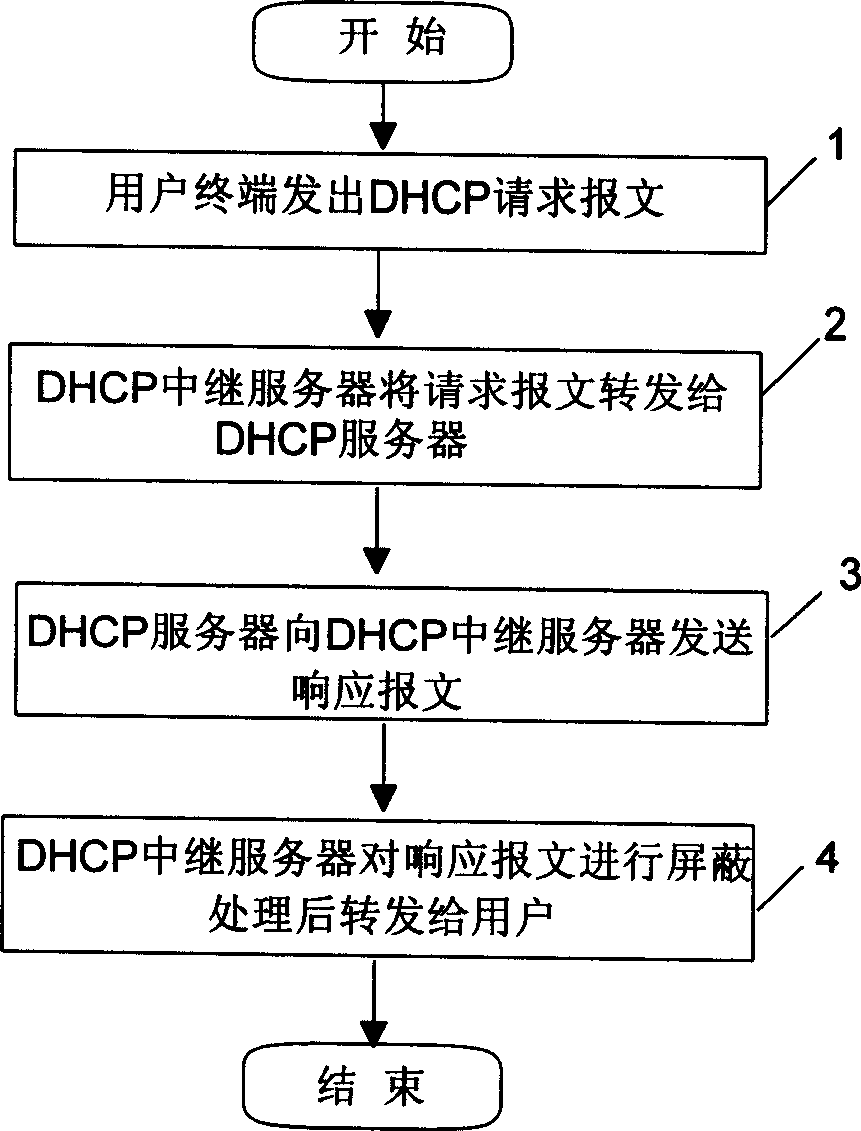
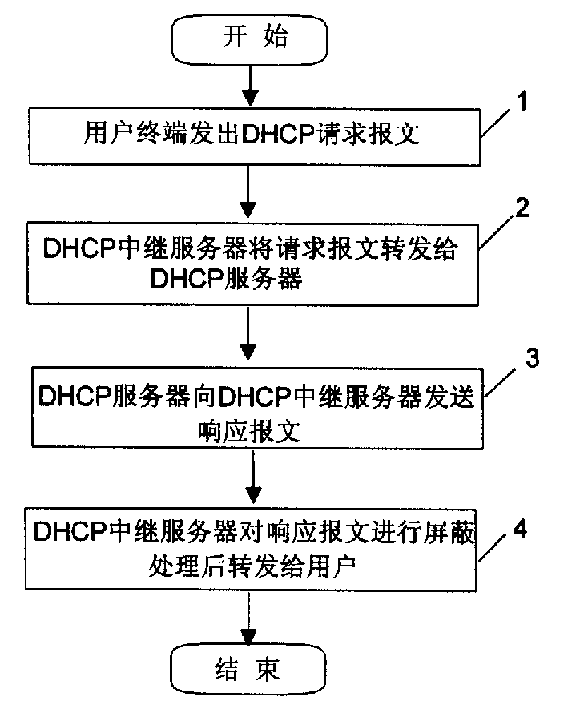
[0013] Since during the user network access process, the DHCP request message sent by the user terminal needs to be forwarded to the DHCP server through the DHCP relay server in the network, so the response message fed back to the user terminal by the DHCP server at the DHCP relay server can be The text is processed to realize the isolation between the DHCP server and the user.
[0014] figure 1 It is a flow chart of the method embodiment of the present invention. according to figure 1 First, the user terminal sends a DHCP request message for network access to the DHCP relay server in step 1; the DHCP relay server receives the DHCP request message of the user terminal in step 2, and then relays the DHCP request message of the user terminal To the DHCP server; After the DHCP request message of the user terminal is received by the step 3DHCP server, the IP a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com