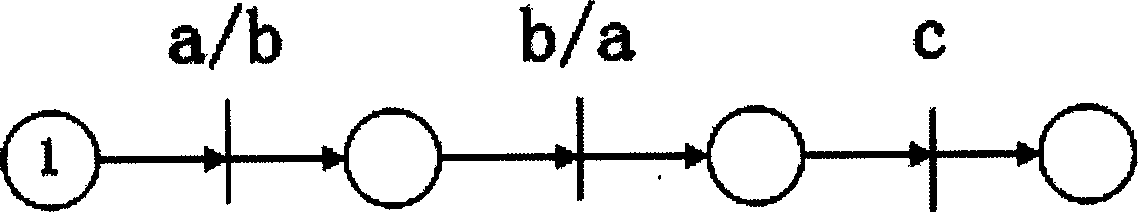Formalized description method of network infection behaviour and normal behaviour
A formalized description and network intrusion technology, applied in user identity/authority verification, timely exchange of telegram messages, digital transmission systems, etc., can solve complex intrusion behaviors, inability to effectively detect intrusion behaviors, information system collapse and denial of service, etc. question
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0036] In the intrusion petri net, the action feature (Action) and the state (State) in the quadruple are respectively represented by T and P sets, which have a good correspondence. The quantitative relationship (Quantity) in the quadruple is well expressed by the identification number in P.
[0037] For the sequence (Sequence) relationship in the quadruple, there is also a good corresponding description with the intrusion petri net, a, b, c∈A (A is the set of intrusion actions), there are the following sequence relationships:
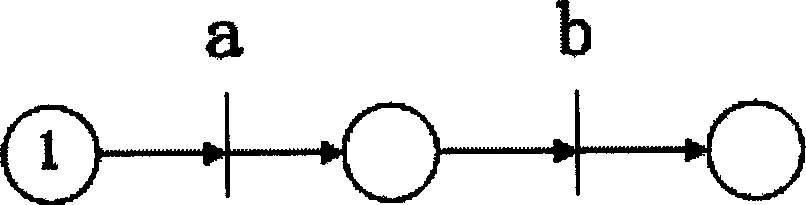
[0038] Sequential relationship such as figure 2
[0039] Partial order relation such as image 3
[0040] Choose a relationship such as Figure 4
[0041] concurrent relations such as Figure 5
[0042] status label
remember
status description
action mark
remember
Action description
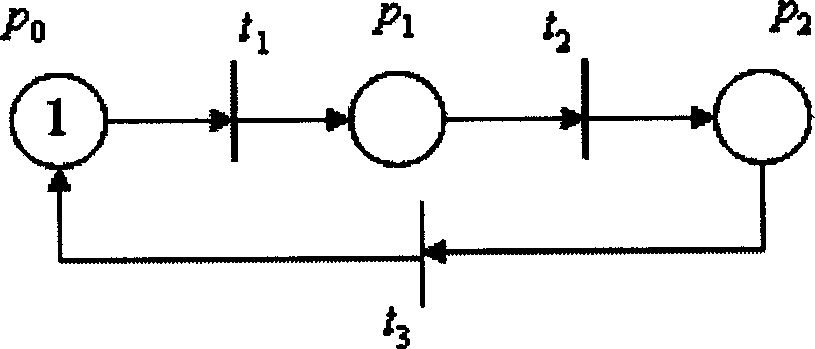
p 0
initial listening status
t 1
The server receives the syn request
p 1
recei...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com