Side channel attack preventing algorithm applicable to full life cycle of system data
A full life cycle, channel attack technology, applied in the field of anti-side channel attack algorithm, can solve security threats, no common algorithm model for anti-side channel and other problems, and achieve the effect of easy implementation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0050] The specific embodiments provided by the present invention will be described in detail below in conjunction with the accompanying drawings.
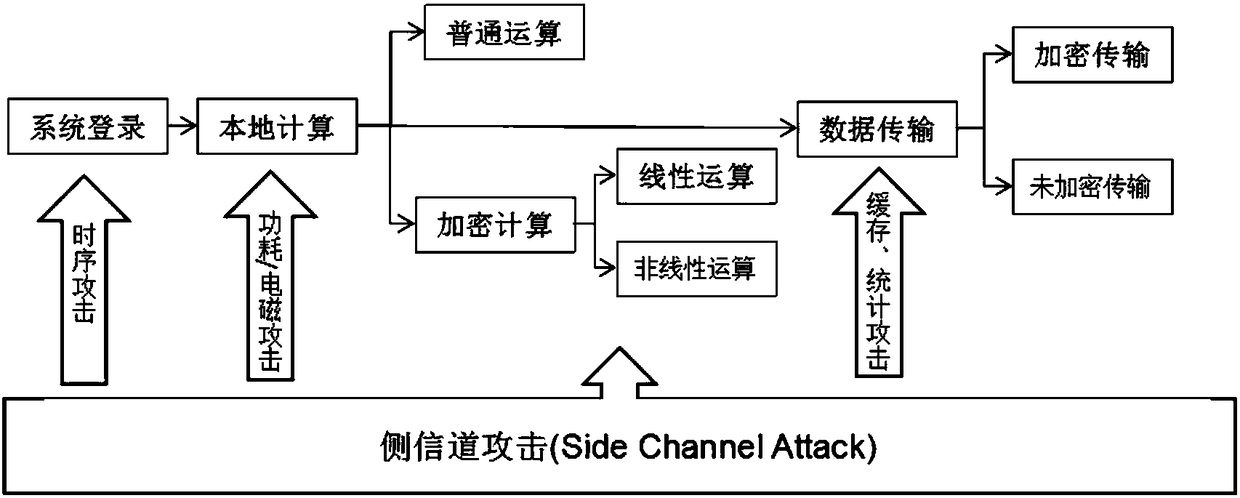
[0051] Please refer to figure 1 , figure 1 It is a schematic diagram of the SCA attack process framework. It is aimed at all links in any system that may encounter side-channel attacks during the entire life cycle of operation and the corresponding three main side-channel attack methods. This scheme is designed to defend against the currently known mainstream and highly harmful side-channel attack methods, but not to defend against all side-channel attack methods.
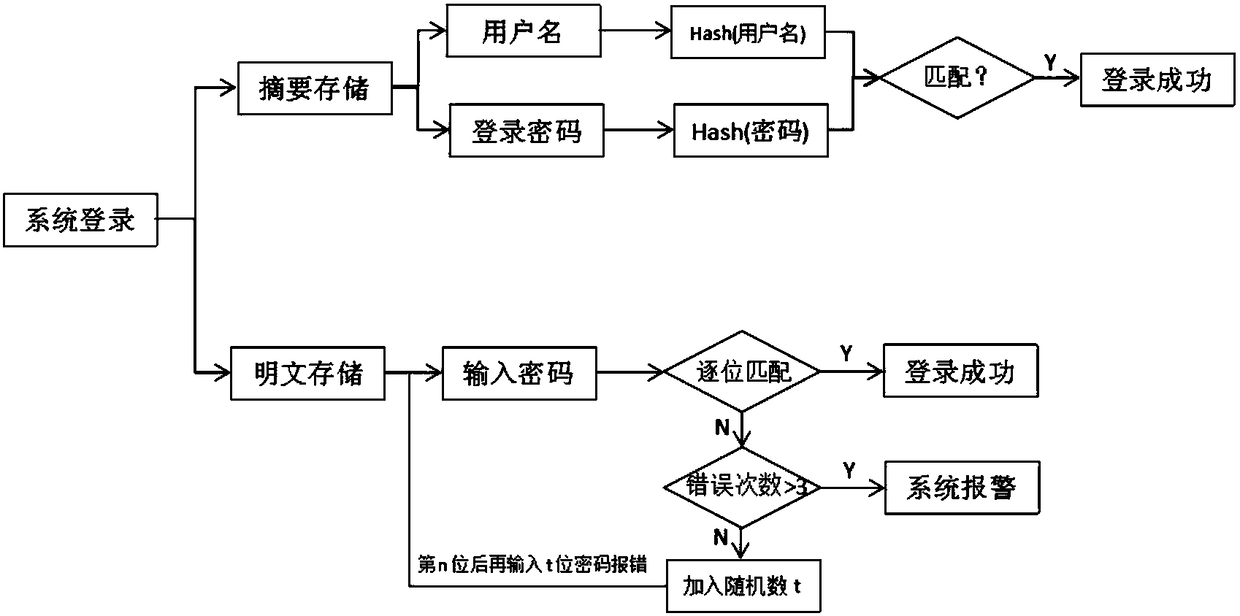
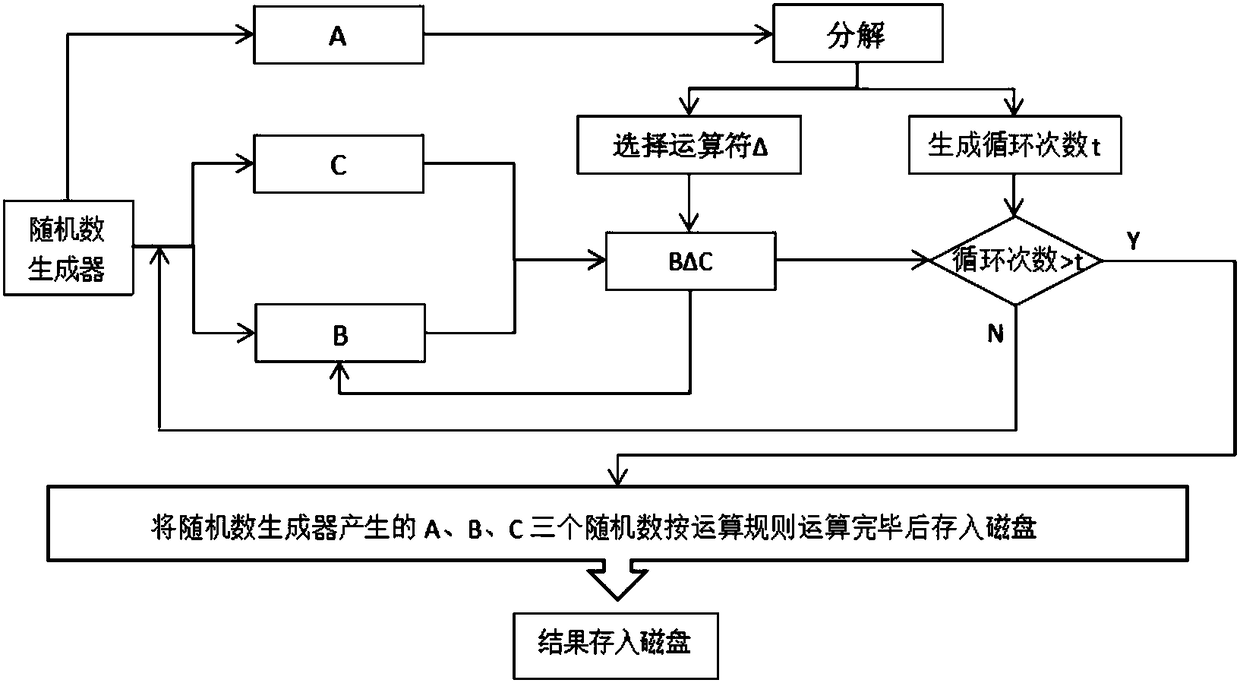
[0052] Therefore, through the defense framework of this solution, the whole life cycle of the system can be defended and protected, and the more harmful part and the key operation data part can be effectively protected, so that the data can be accessed from system login, data operation, and data transmission. It has security guarantees in the field of side channel a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com