Computer encryption unit and encryption method
An encryption method and encryption device technology, applied in the field of computer and data communication, can solve problems such as hidden dangers
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
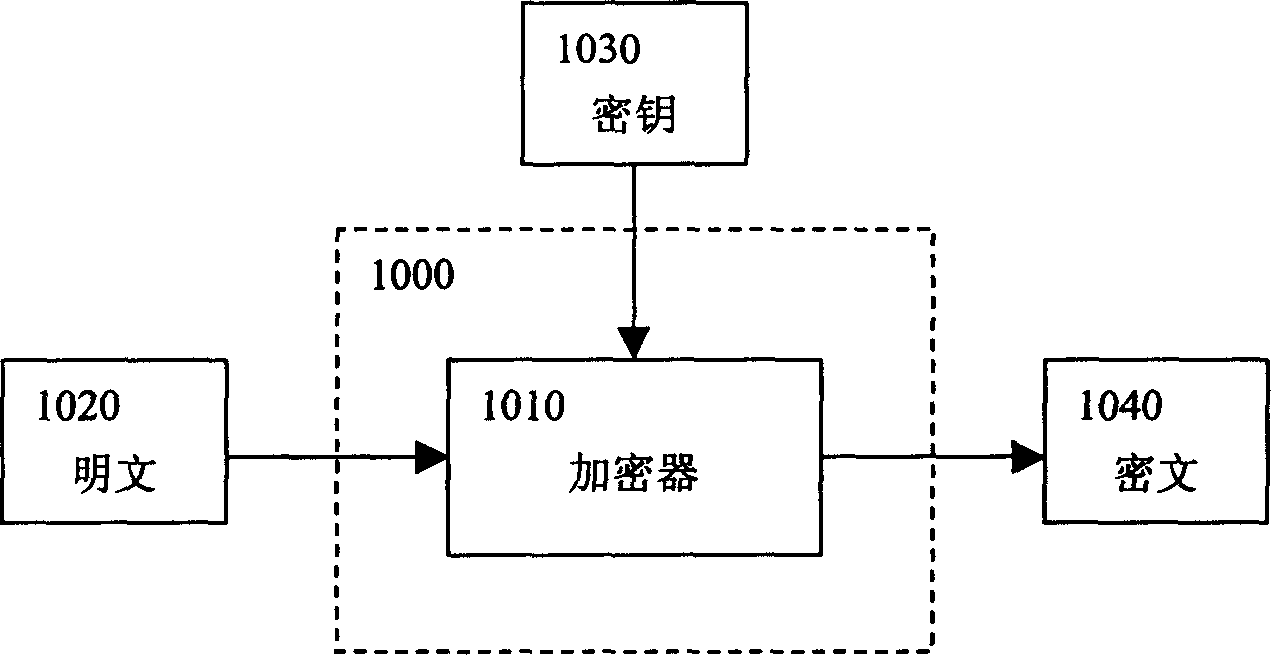
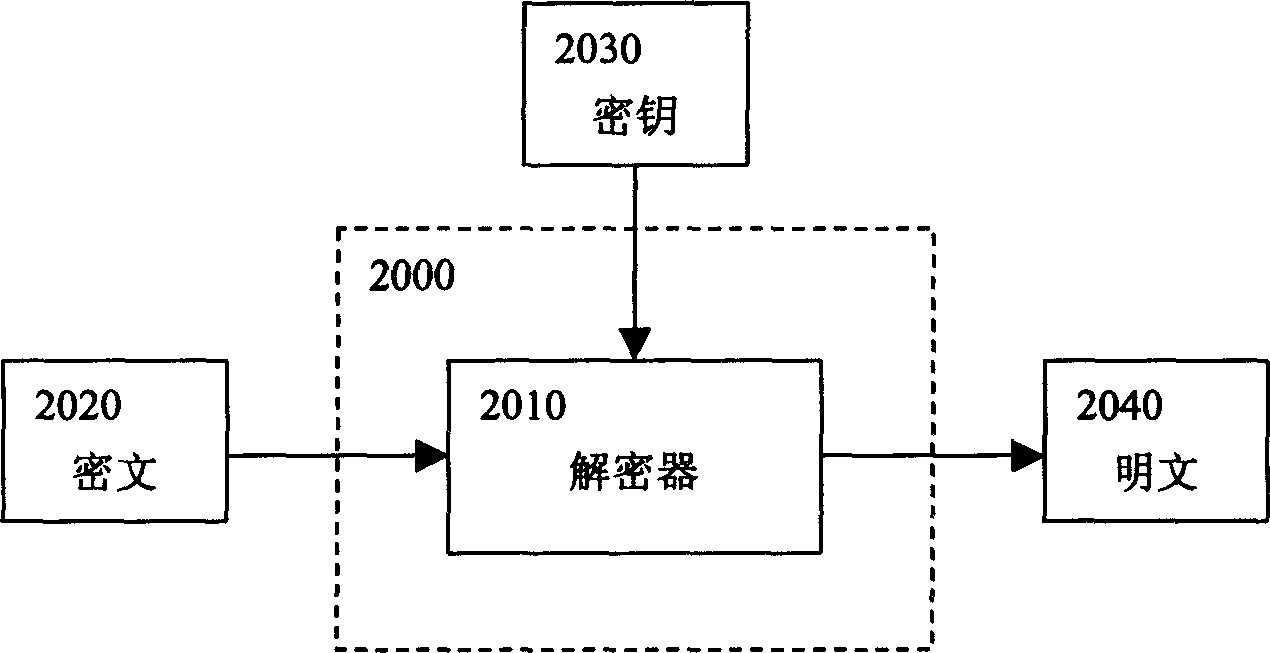
[0065] The computer data encryption system and method thereof of the present invention will be described in detail below in conjunction with the accompanying drawings. For the convenience of description, the symbols and positions involved in this manual are stipulated as follows:
[0066] The plaintext is M={M 1 ,M 2 ,...,M 1m}, 0≤M i 1 , C 2 ,...,C 1c}, 0≤C i <256, its length is lc;
[0067] The user-defined key text is Key={Key1 ,Key 2 ,...,Key 1k}, 0≤Key i 1 , k 2 ,...,k 1k}, 0≤k i 4 , namely k i It is a 4-byte integer, and its length is also lk;
[0068] If f() is a chaotic function, then f n+1 (x)=f(f n (x))(n>0), f 1 (x)=f(x). where 0≤x4 , 0≤f(x)4 .
[0069] In order to achieve the chaotic effect, the initial value needs to be iterated several times (that is, N) times before encryption, and usually N=50 can satisfy the condition.
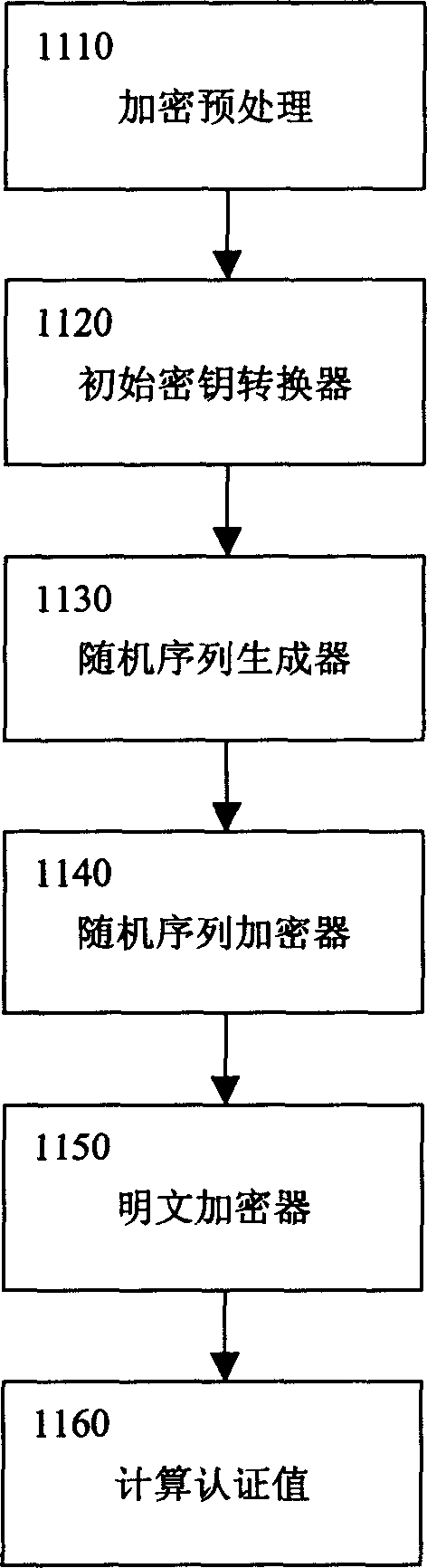
[0070] In addition, in this encryption / decryption method, a total of 5 steps use the chaotic function: encrypted header (...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com