Realizing method for strengthening meeting telephone service
A technology of a conference call and an implementation method, applied in the field of communications, can solve the problems that the communication security of the conference call cannot be well guaranteed, the conference call service cannot flexibly adjust the conference members, and the legitimacy of the conference members is not considered. Market potential, improved commercial value, and improved practicability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
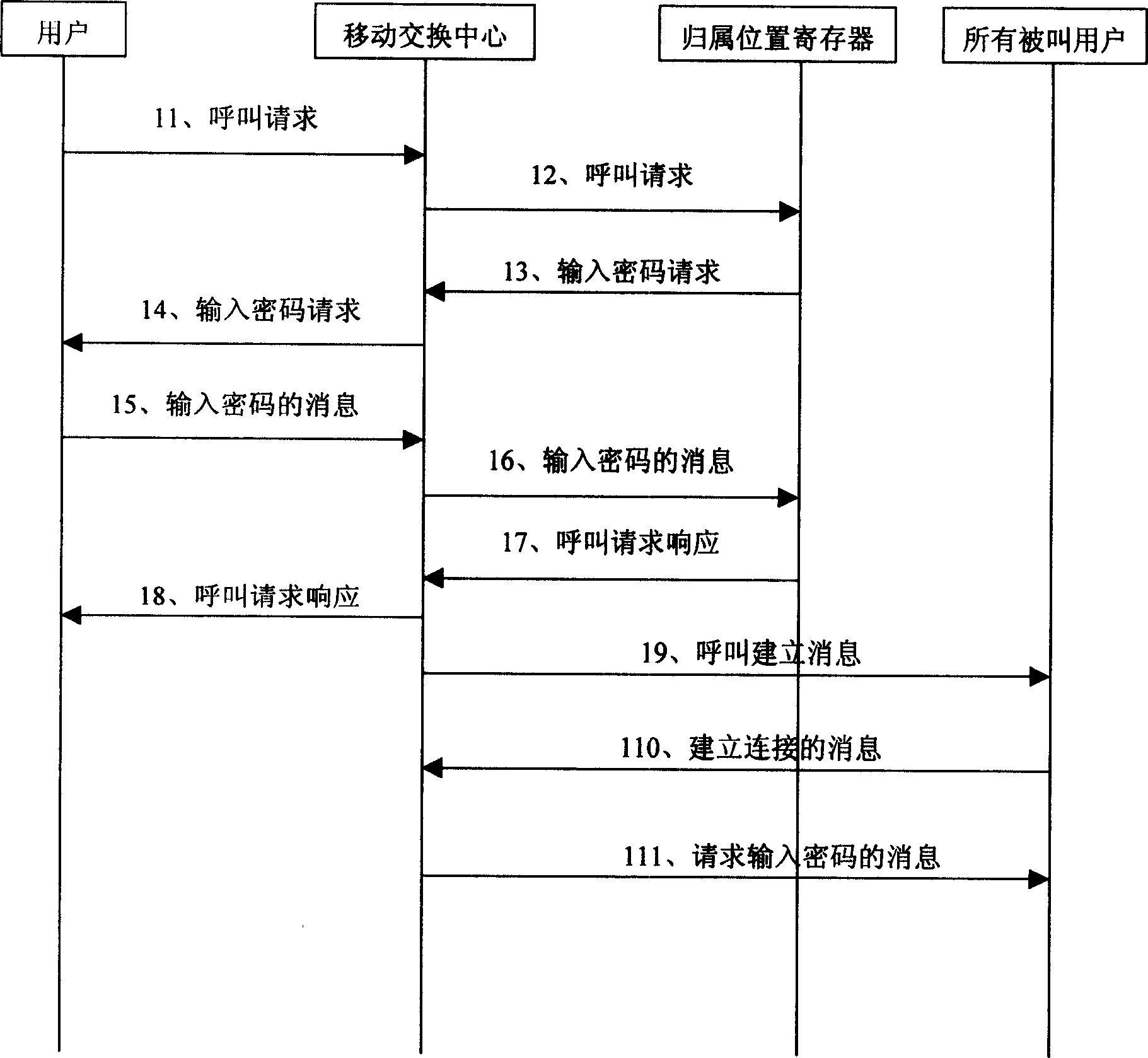
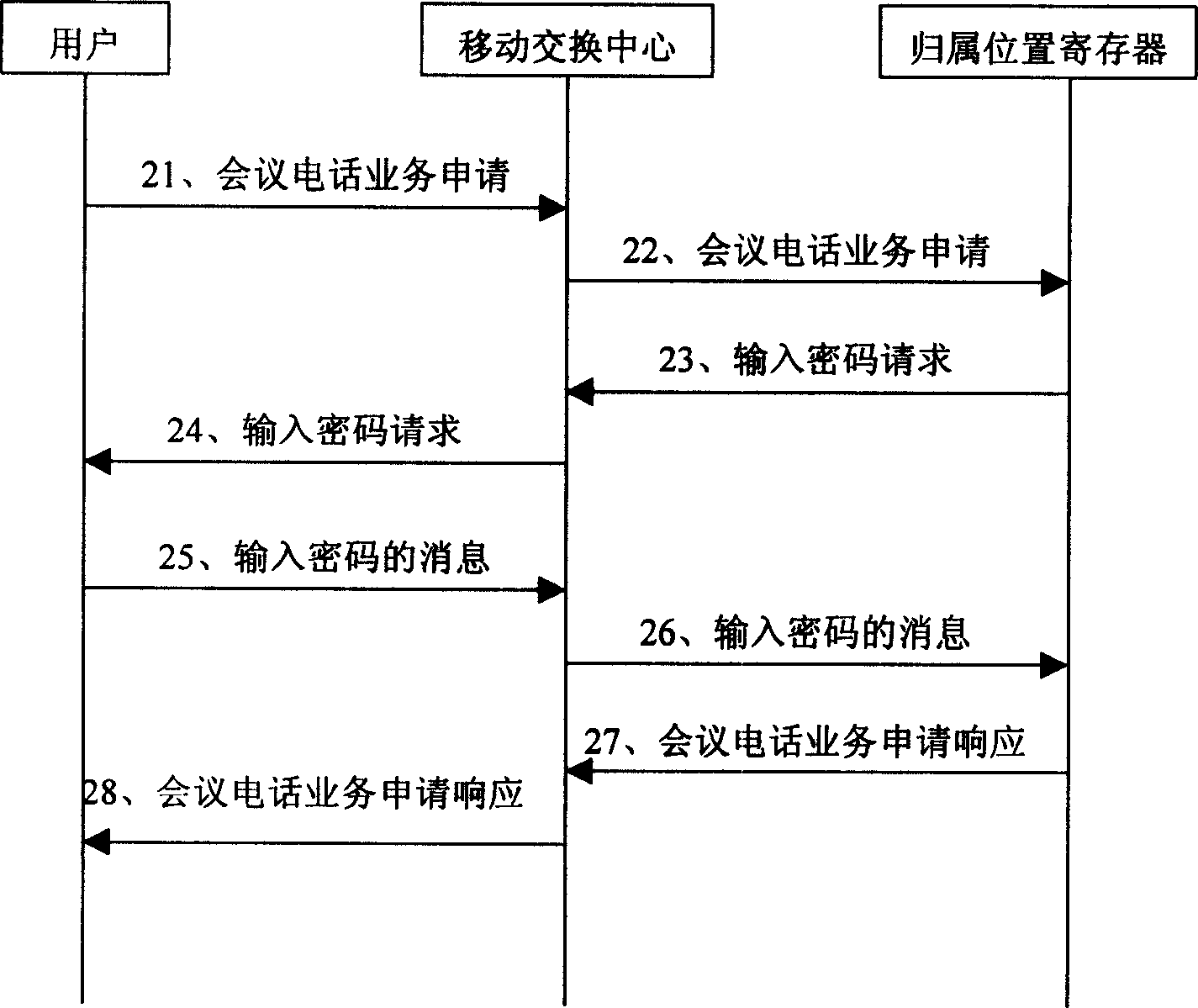
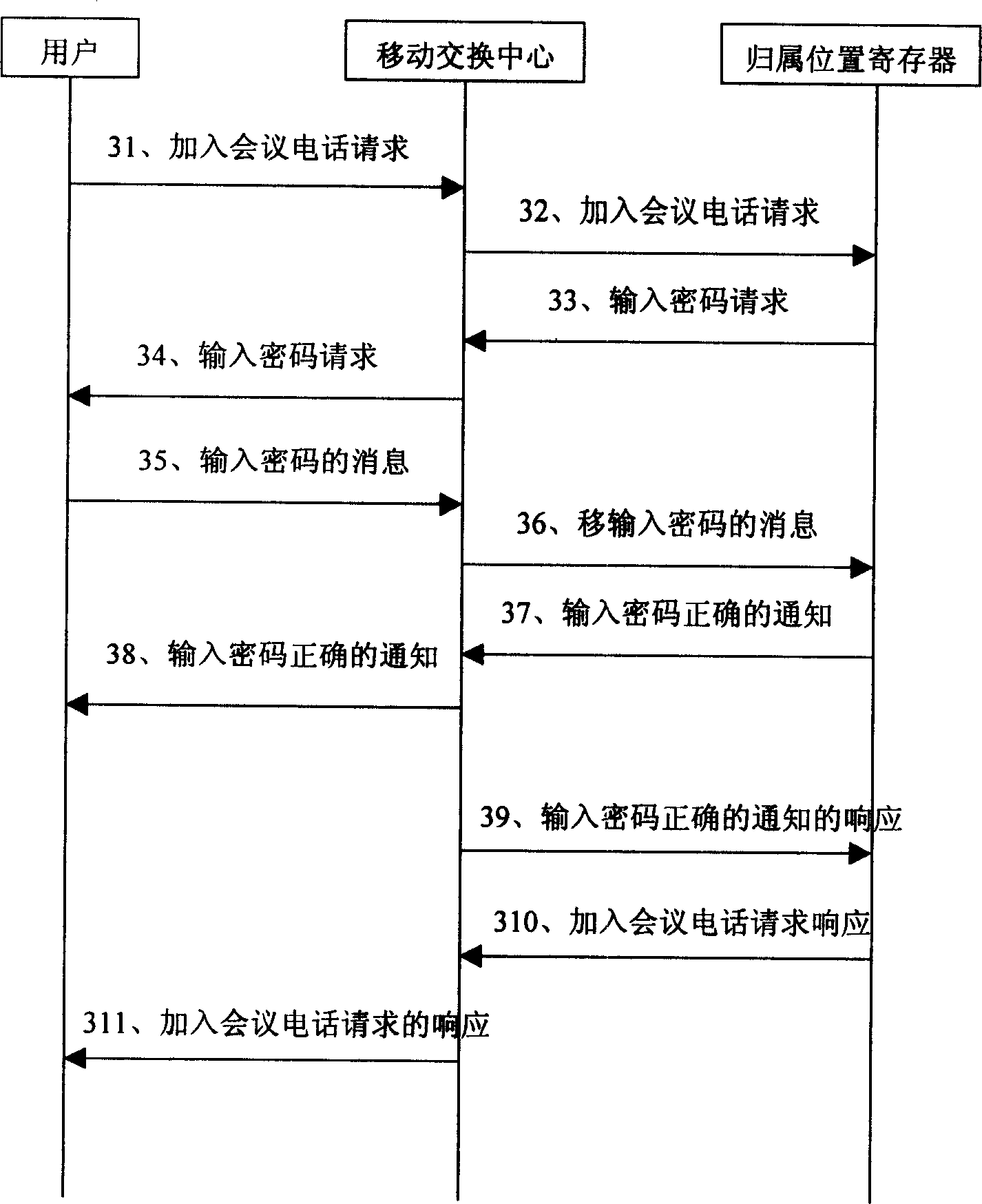
[0045] The core idea of the present invention is by signing eCC (Enhanced Conference Call) service, group, group master user password, controlled user password and conference member number at HLR (Home Location Register), thereby can realize in the communication network The conference call service can be developed flexibly. For example, the master control user can delete any controlled user, and the controlled user can actively apply to join the established conference call. At the same time, the present invention can also ensure the security of the conference call service.
[0046] The present invention mainly comprises to the improvement of existing conference phone:
[0047] 1. The process of initiating and establishing a conference call. In this process, the main control user of the present invention can initiate a call to each conference member in a group mode and request to establish a conference call service; All members included in the group, and at this time, the mas...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com