Method and system for re-authentication in IP multimedia core network system (IMS)
A multimedia and authentication technology, applied in the field of communication systems, can solve problems such as loss of user trust
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
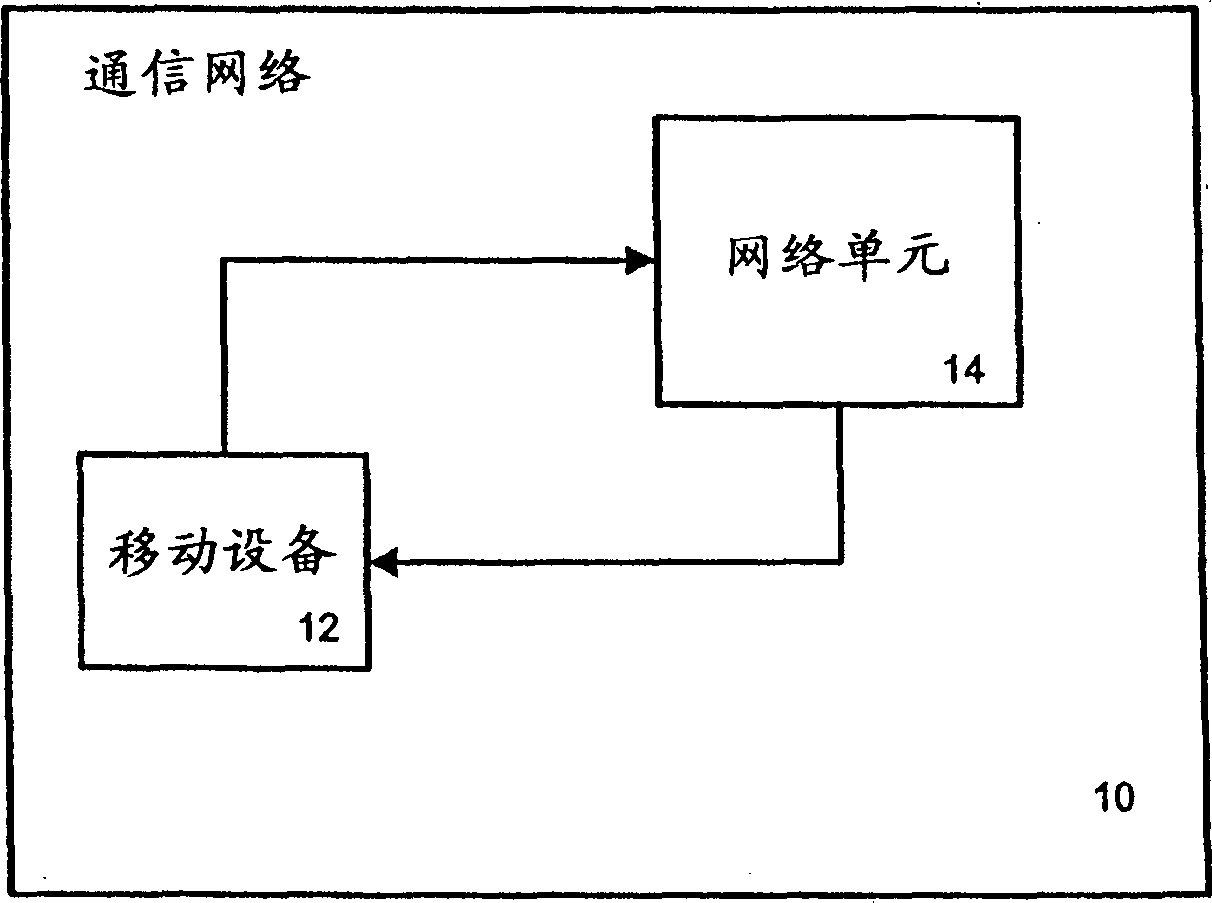
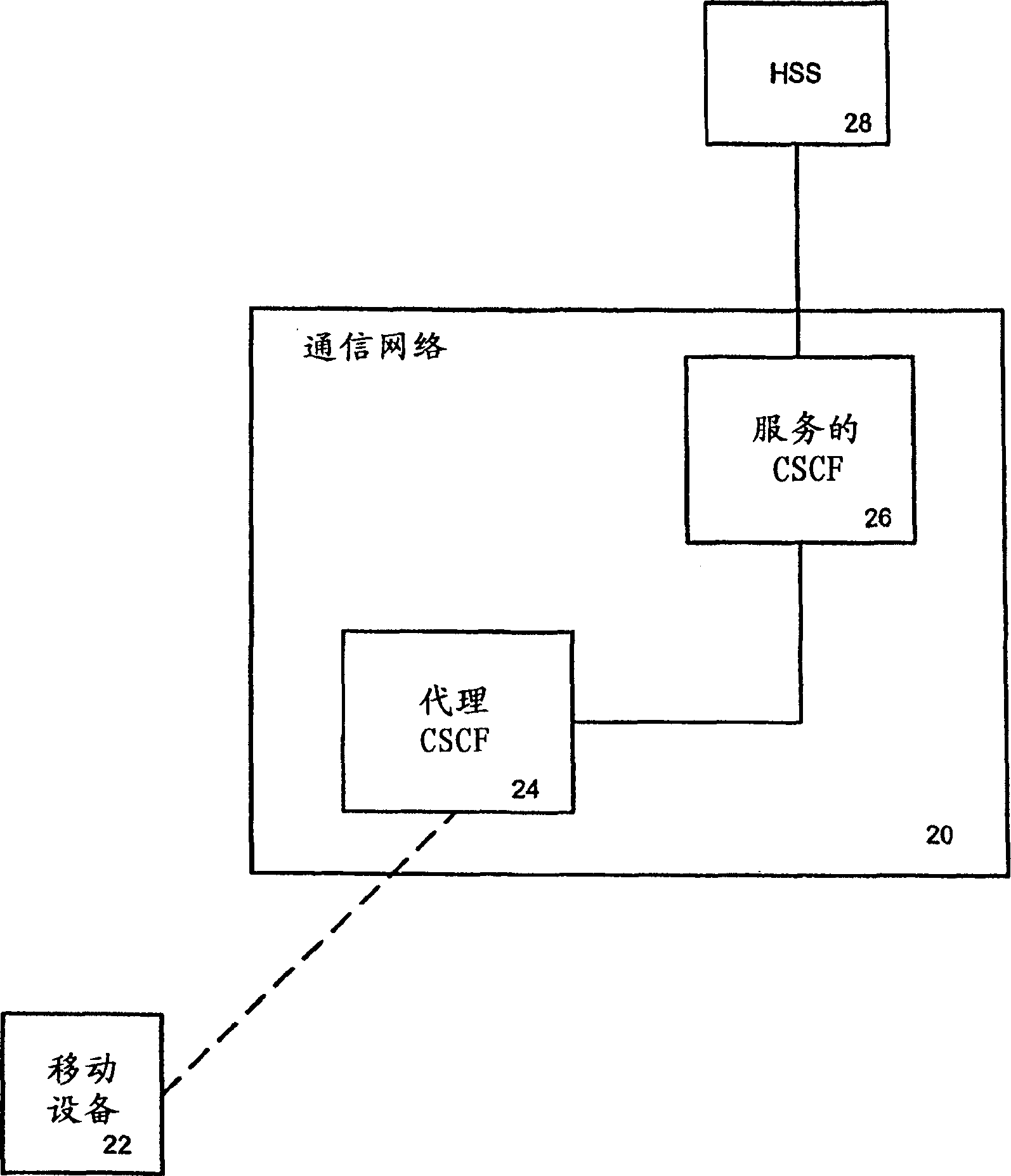
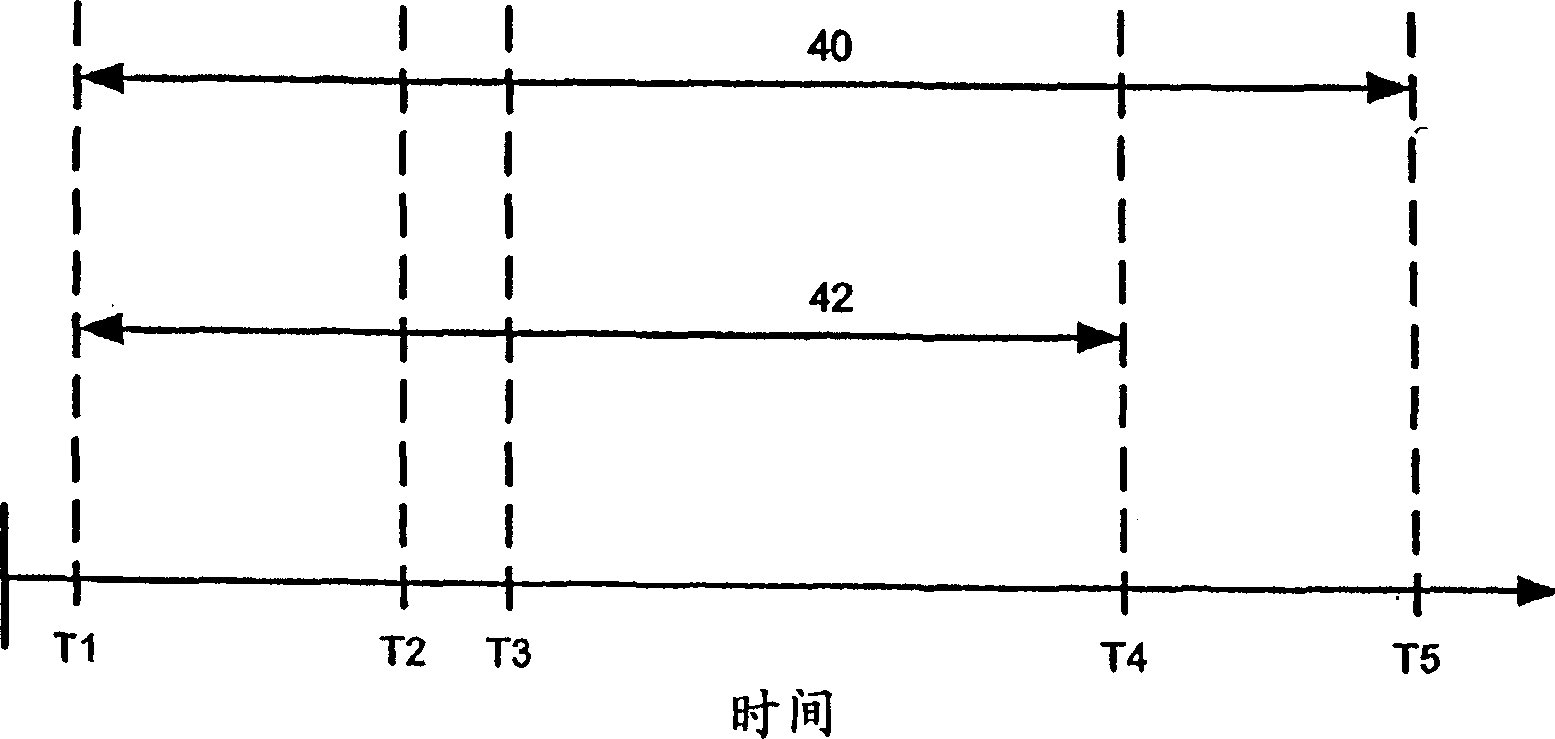
[0013] Details are presented here for purposes of illustrative discussion of embodiments of the invention, by way of example. Instructions and attached Figure 1 It is intended to acquaint those skilled in the art how the present invention may actually be practiced.
[0014] In addition, in order to avoid obscuring the present invention, the fact that details about implementing such a block diagram largely depend on the platform on which the present invention is implemented is also taken into account, that is, the details should be within the ability of those skilled in the art, and can be described as a block diagram Form expresses arrangement. While specific details (eg, circuits, flowcharts) are set forth to describe example embodiments of the invention, it will be apparent to those skilled in the art that the invention can be practiced without these specific details. Finally, it is apparent that any combination of hardwired circuitry and software instructions can be used...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com