Address encryption method for flash memories
An address, electronic storage technology, applied in the direction of preventing unauthorized use of memory, memory systems, instruments, etc., can solve problems such as inappropriate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
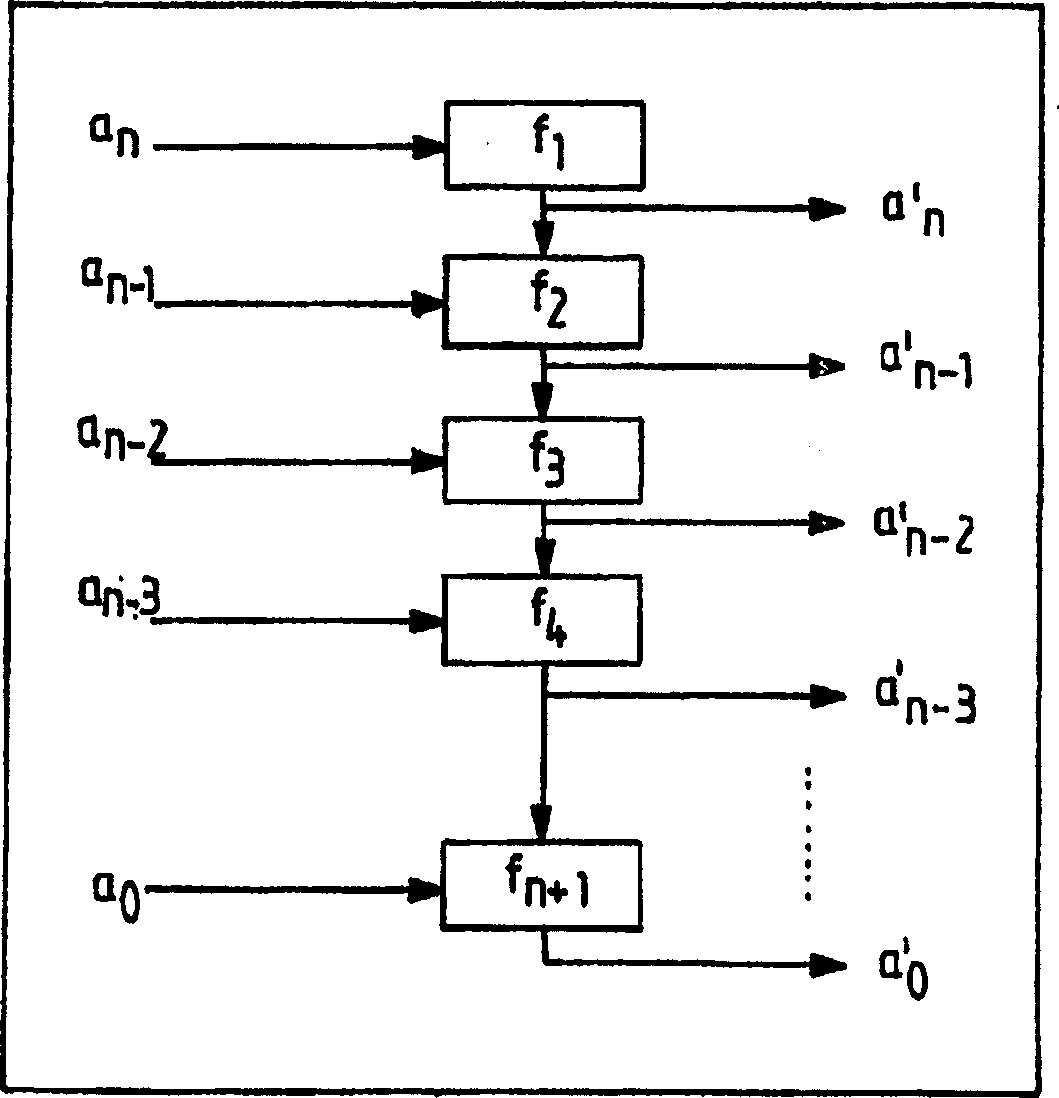
[0025] The encryption method applied in an electronic storage unit according to the invention is based on the idea that the unencrypted addresses a of the access-protected storage areas are encrypted only in certain areas, i.e. by means of one or more further storage areas n , a n-1 ,...,a 1 , a 0 , making the encrypted address a’ n , a' n-1 ,...,a' 1 , a' 0 be formed.
[0026] To do this, provide i=n+1 one-to-one (-->2 i = 2 n+1 no format / cipher pair) scrambling function f 1 , f 2 ,...,f n , f n+1 , such that when passed through the function f 1 (see figure 1 ) encryption, the form a n , a n-1 ,...,a 1 , a 0 The unencrypted address of has the following form:
[0027] f 1 (a n ), f 2 (f 1 (a n )+a n-1 ), f 3 (f 2 (f 1 (a n )+a n-1 )+a n-2 ),...,f n+1 (f n (f n-1 (…)))
[0028]This enables each subregion to be encrypted with different parameters in each case.
[0029] In this paper, it is clear that although address a n , a n-1 ,...,a 1 , a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com