Method of realizing changing open talk to secret talk
A technology of encrypting and transciphering, which is applied in the direction of confidential communication, electrical components, network topology, etc., and can solve problems such as the inability to ensure that the dedicated terminals on both sides enter the encrypted communication process, the terminals cannot communicate normally, and the dedicated terminals cannot control each other.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] In order to make the object, technical solution and advantages of the present invention clearer, the present invention will be further described in detail below in conjunction with the accompanying drawings.
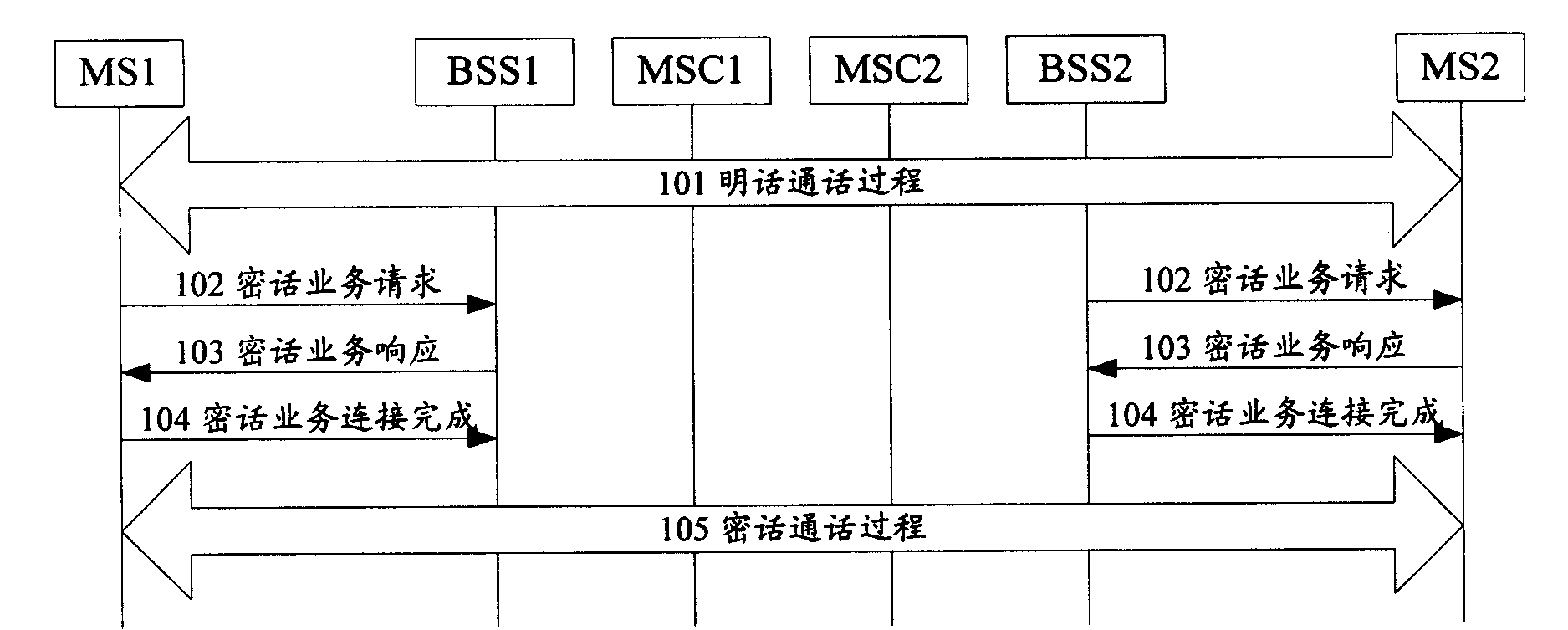
[0029] In the present invention, firstly, the terminals carry out the business negotiation of switching to the encrypted voice, and then establish the transparent transmission channel of the encrypted voice, so as to ensure that the realization process of converting the plain voice to the encrypted voice can be carried out smoothly. The above-mentioned terminal may be a mobile terminal or a fixed terminal. The implementation process of the present invention will be described in detail below by taking the mobile terminal as an example.
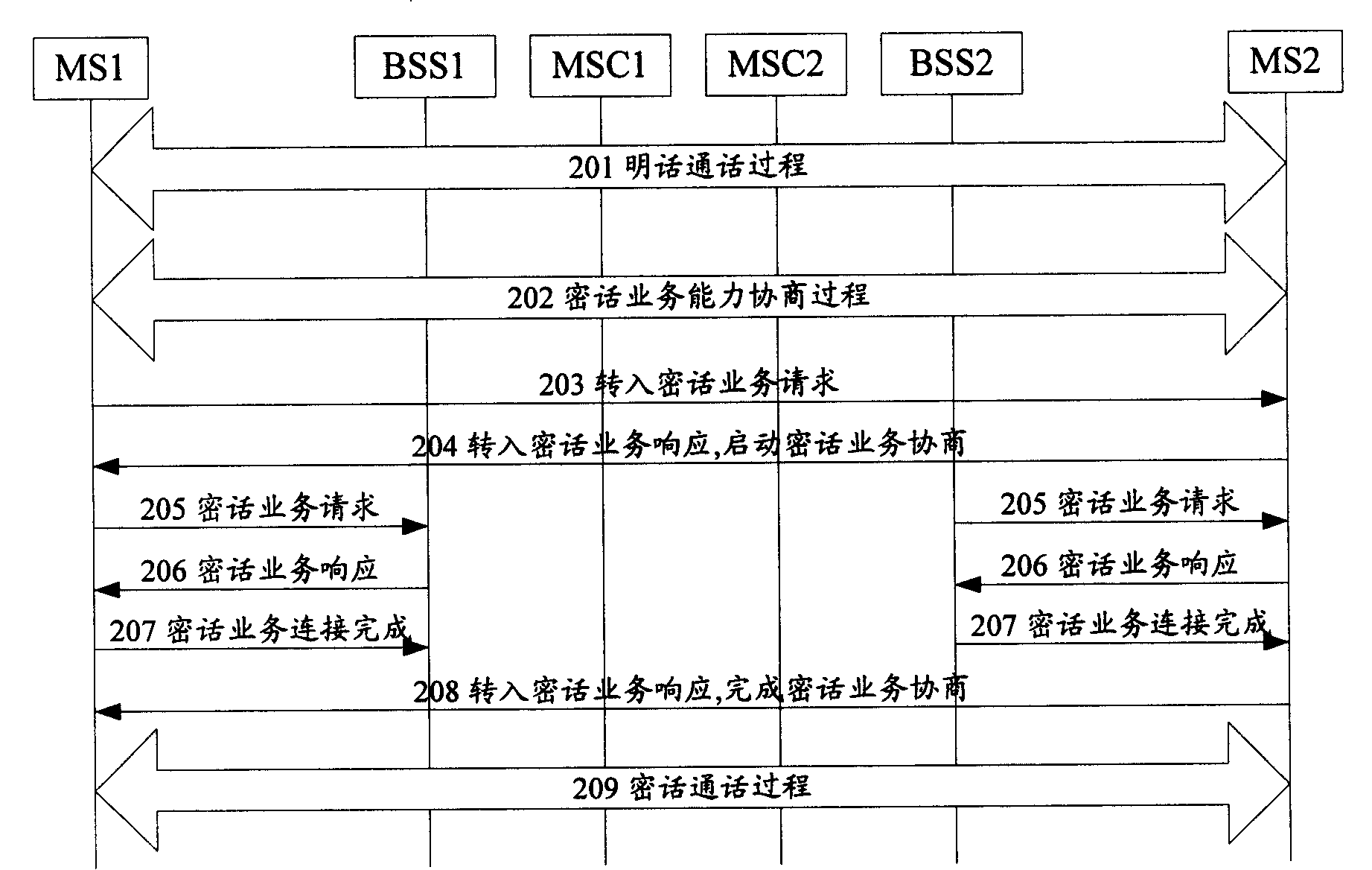
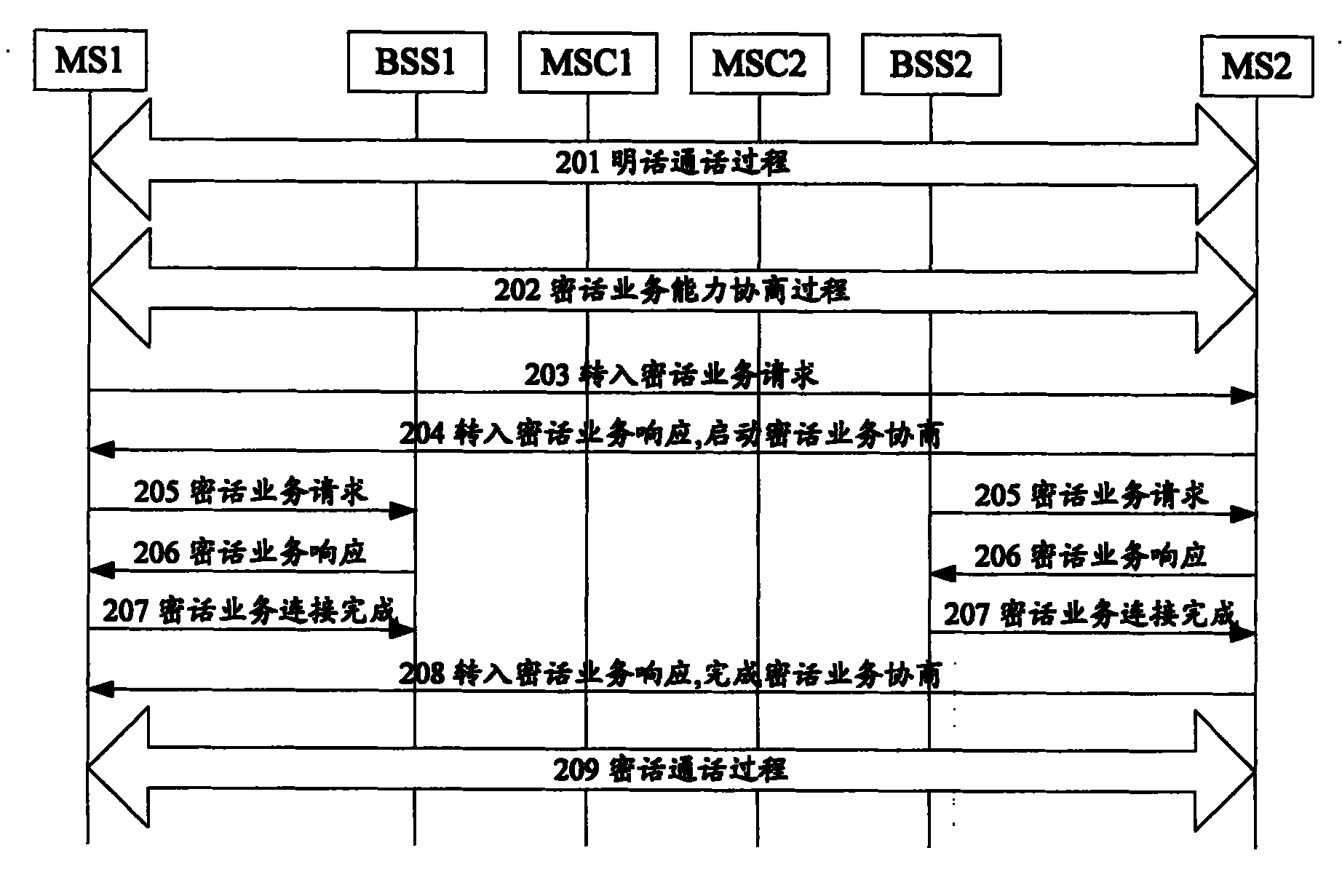
[0030] figure 2 Shows the flow chart of clear speech to encrypted speech in the present invention, such as figure 2 As shown, the implementation process of converting clear speech to encrypted speech includes the following steps...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com