Virtual multicast field controlled identification method and router participating method
An authentication method and multicast domain technology, applied in the virtual multicast domain controlled authentication method and router participation field, can solve the problems of uncontrollable multicast data, illegal multicast stream attacks on PIM routers, etc. Facilitate centralized management and maintenance, and control the effect of receiving permissions
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
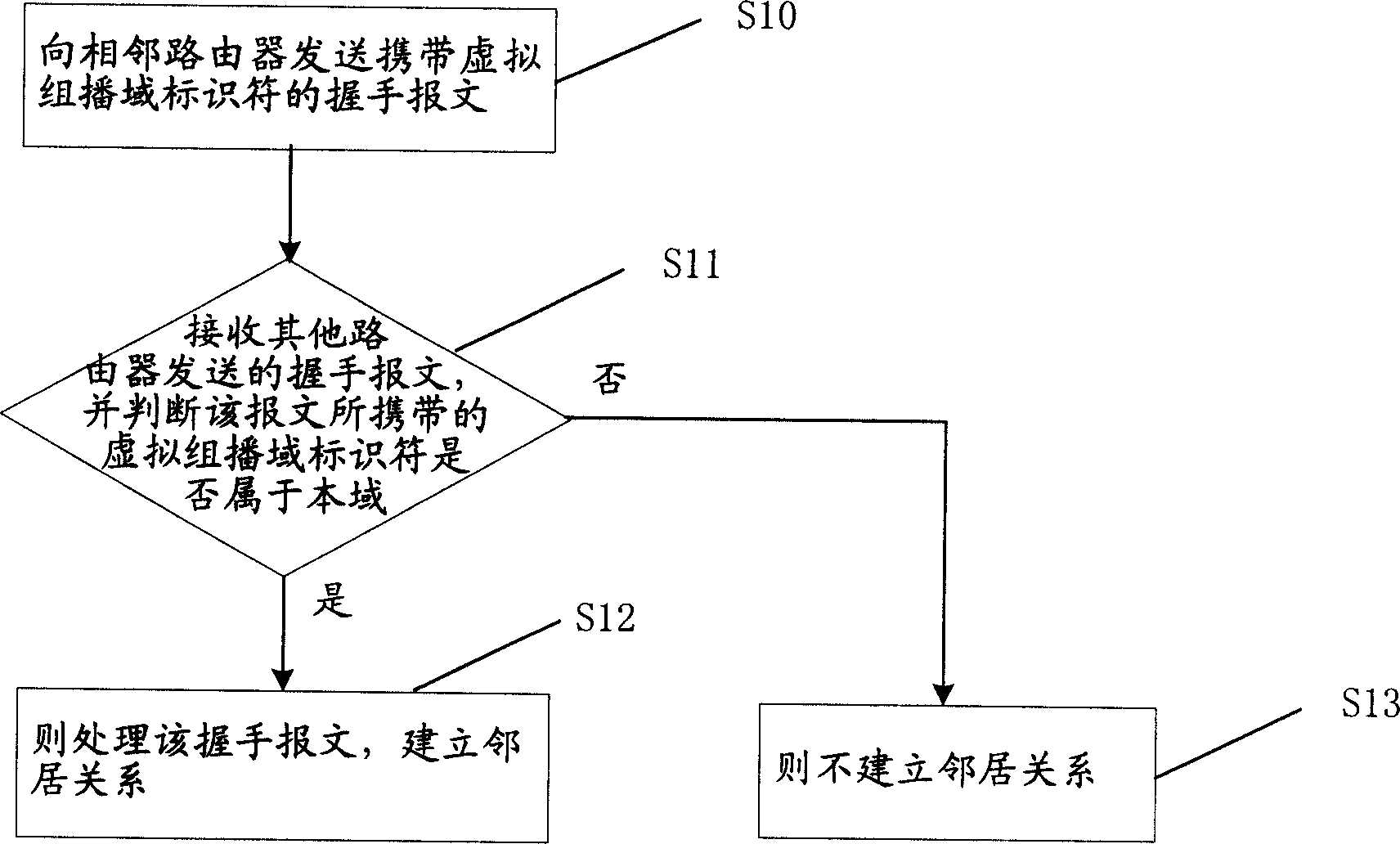
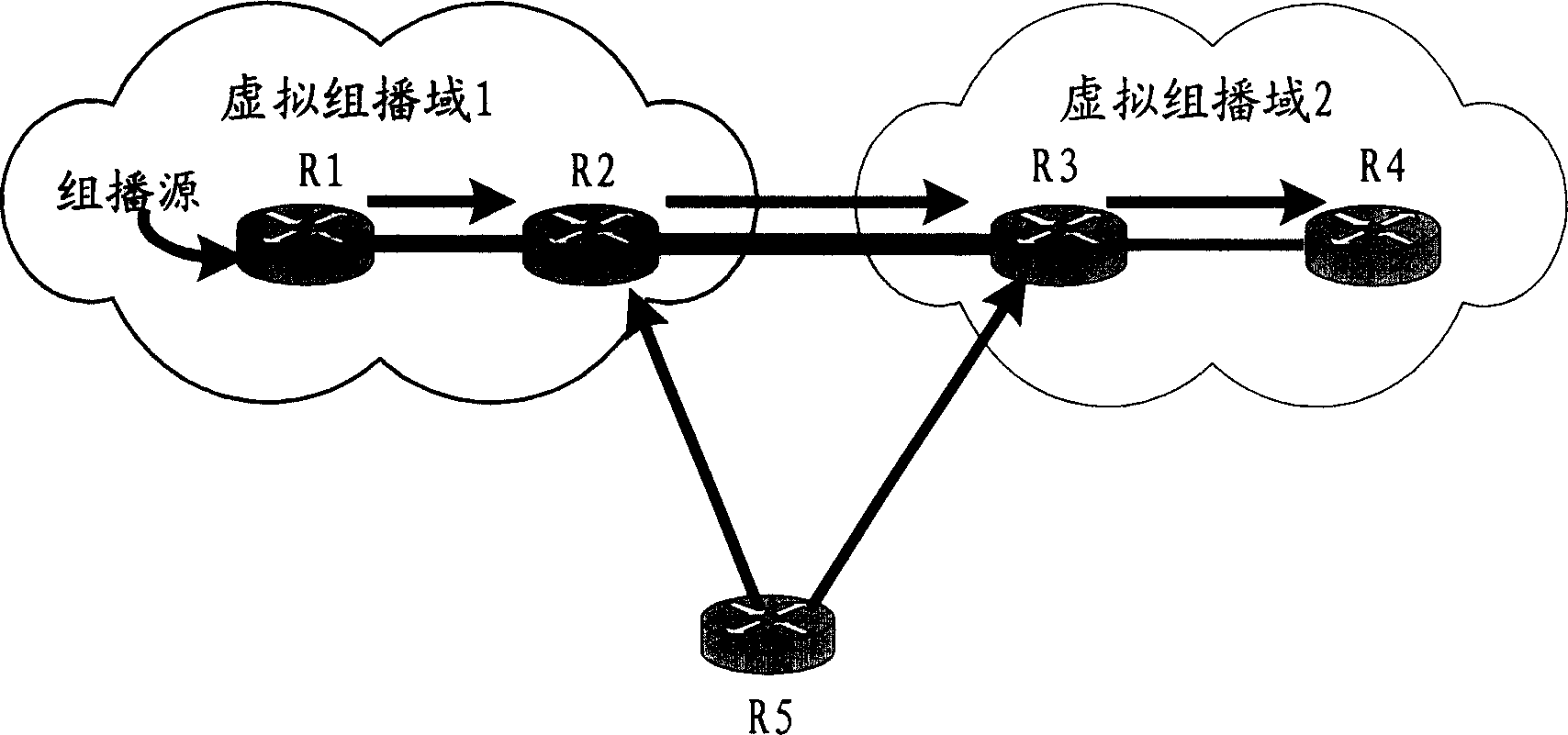
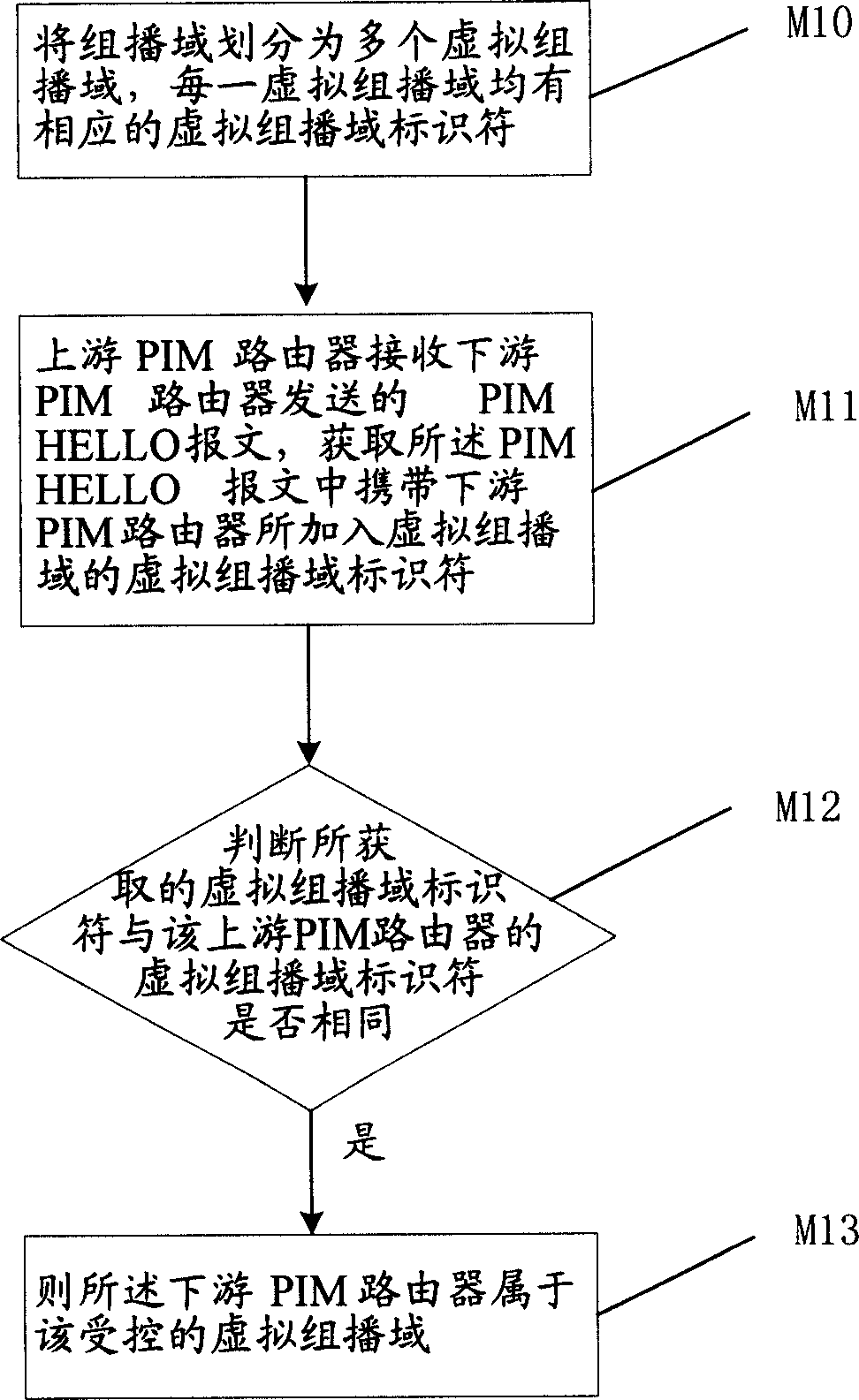
[0029] The core of the present invention is: the administrator divides the multicast domain into multiple virtual multicast domains according to the network topology, and assigns a globally unique virtual multicast identifier for each virtual multicast domain; adds the designated downstream PIM router to the designated In the virtual multicast domain, and the downstream PIM router periodically sends the PIM HELLO message with the virtual multicast domain identifier of the additional option; when the upstream PIM router receives the PIMHELLO message, by judging the PIM HELLO message to detect whether the joined downstream PIM router belongs to the virtual multicast domain where the upstream PIM router is located. And perform corresponding authentication and management on the downstream PIM router according to the judgment result. Through the scheme of the present invention, the problem that the PIM router in the multicast network is illegally attacked by the outside can be bett...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com