A method, apparatus and software product for detecting rogue access points in a wireless network
A wireless network, deceptive technology, used in the direction of security devices, wireless communications, electrical components, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
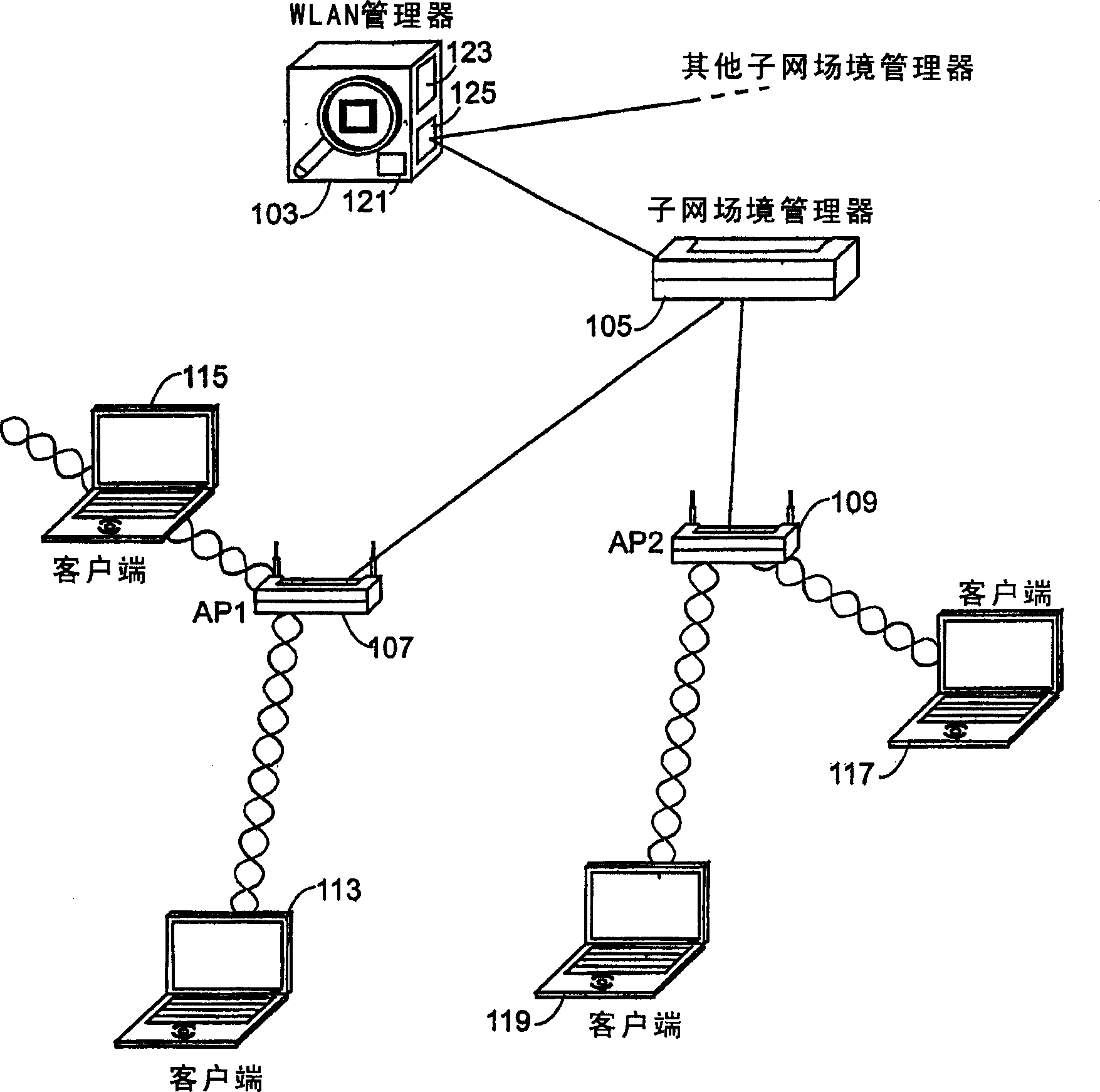
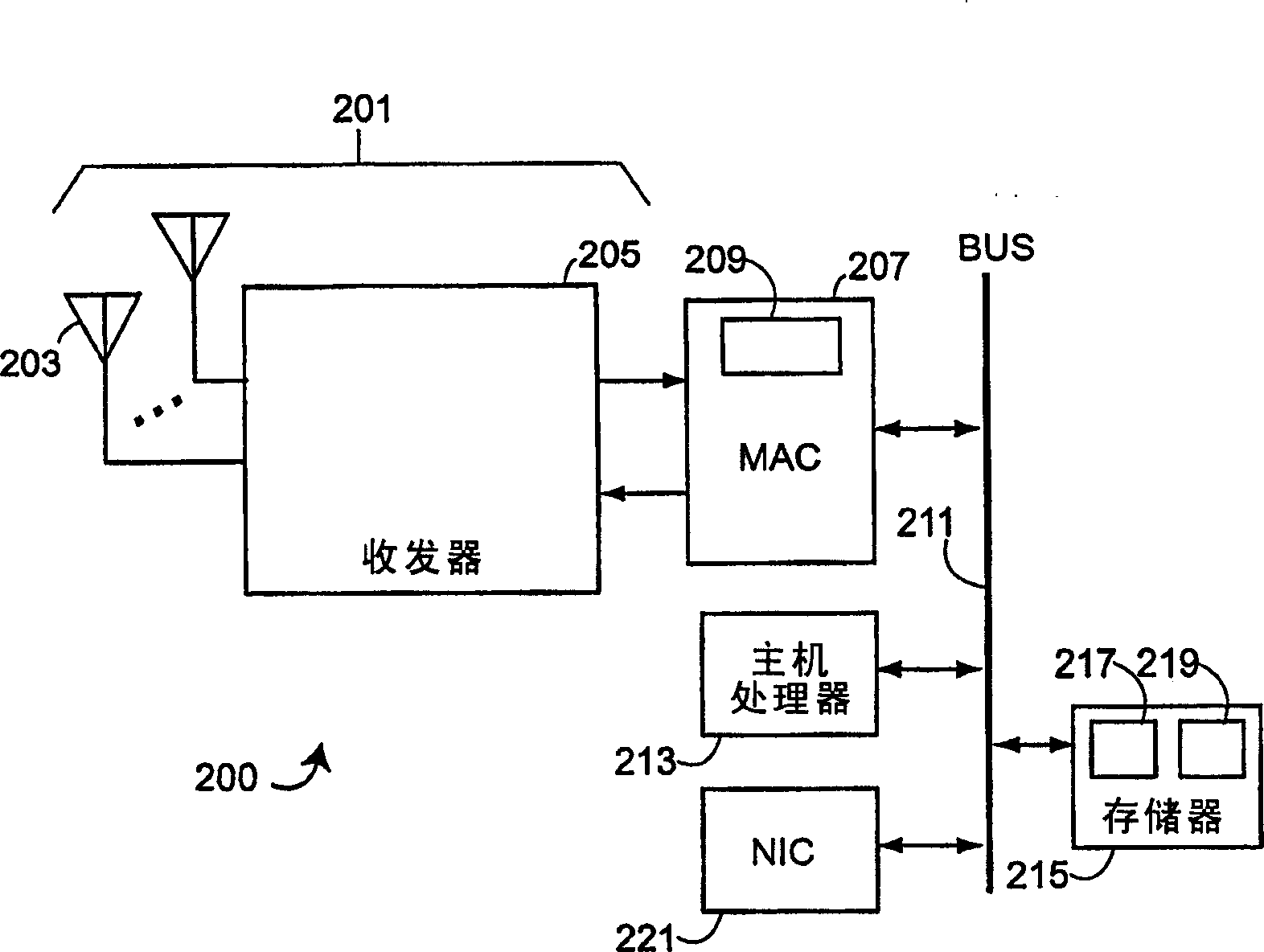
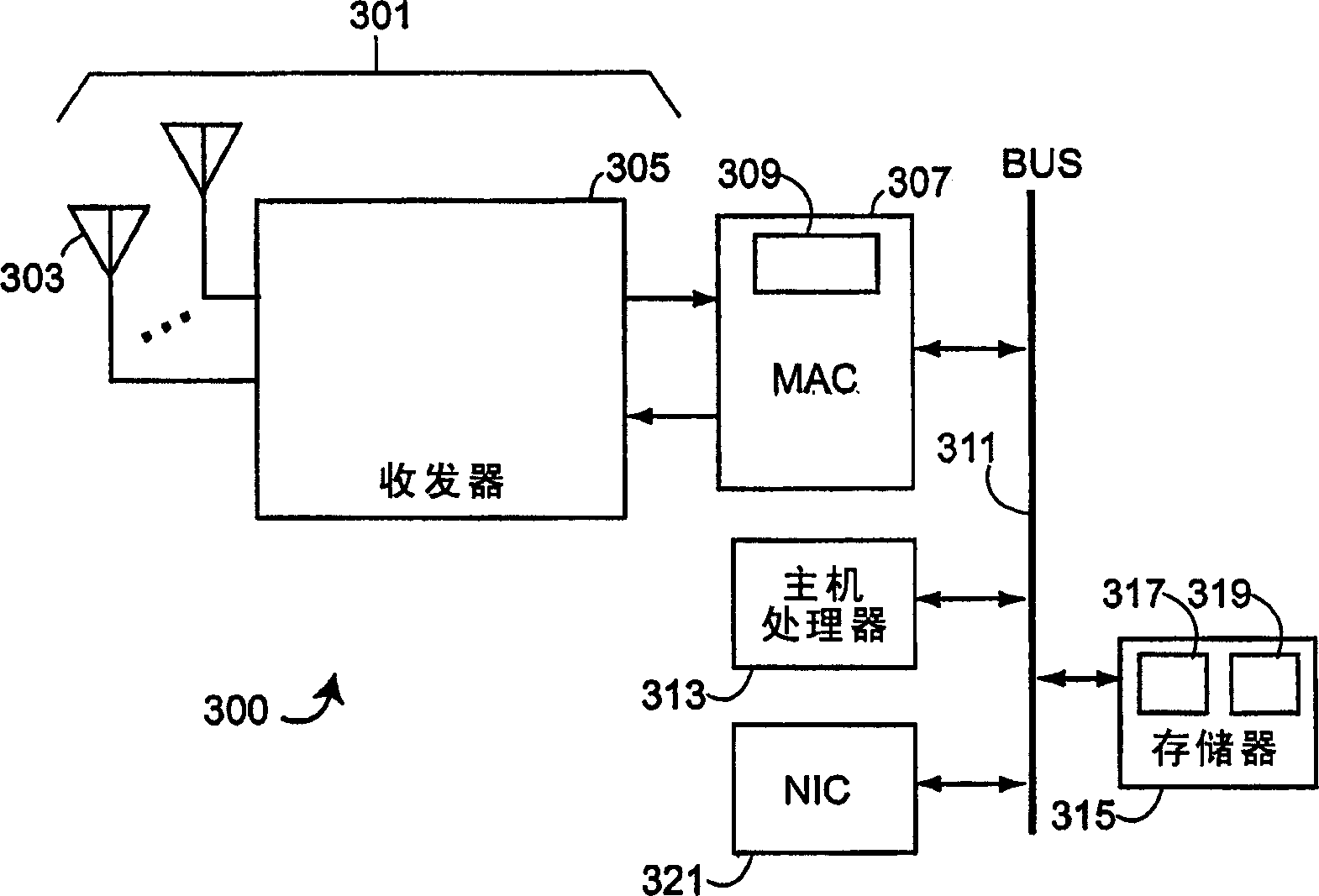
[0030] A method for detecting rogue access points, including rogue and non-rogue access points, is described here. The invention will be described in the context of the IEEE 802.11 standard for WLANs. However, the present invention is not limited to WLANs conforming to the IEEE 802.11 standard.
[0031] managed wireless network
[0032] One embodiment of the present invention operates in a managed wireless network where APs and their clients are managed by a central management entity. Depending on size and complexity, the managed network is either a set of APs with a central control entity, or a hierarchical structure with a set of hierarchical control domains. Each control domain is managed by a management entity which we call a manager here. The number of levels in the hierarchical hierarchy depends on the complexity and / or size of the network, such that not all managed networks have all levels of control. For example, a simple managed network may have only one level of ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com