Safe U disc storage system and method
A storage system and security technology, applied in information storage, static storage, digital storage information, etc., can solve problems such as difficult management and use, loss of security protection of classified information, mixed storage of ordinary information and classified information, etc., to prevent The effect of leaking confidential information
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
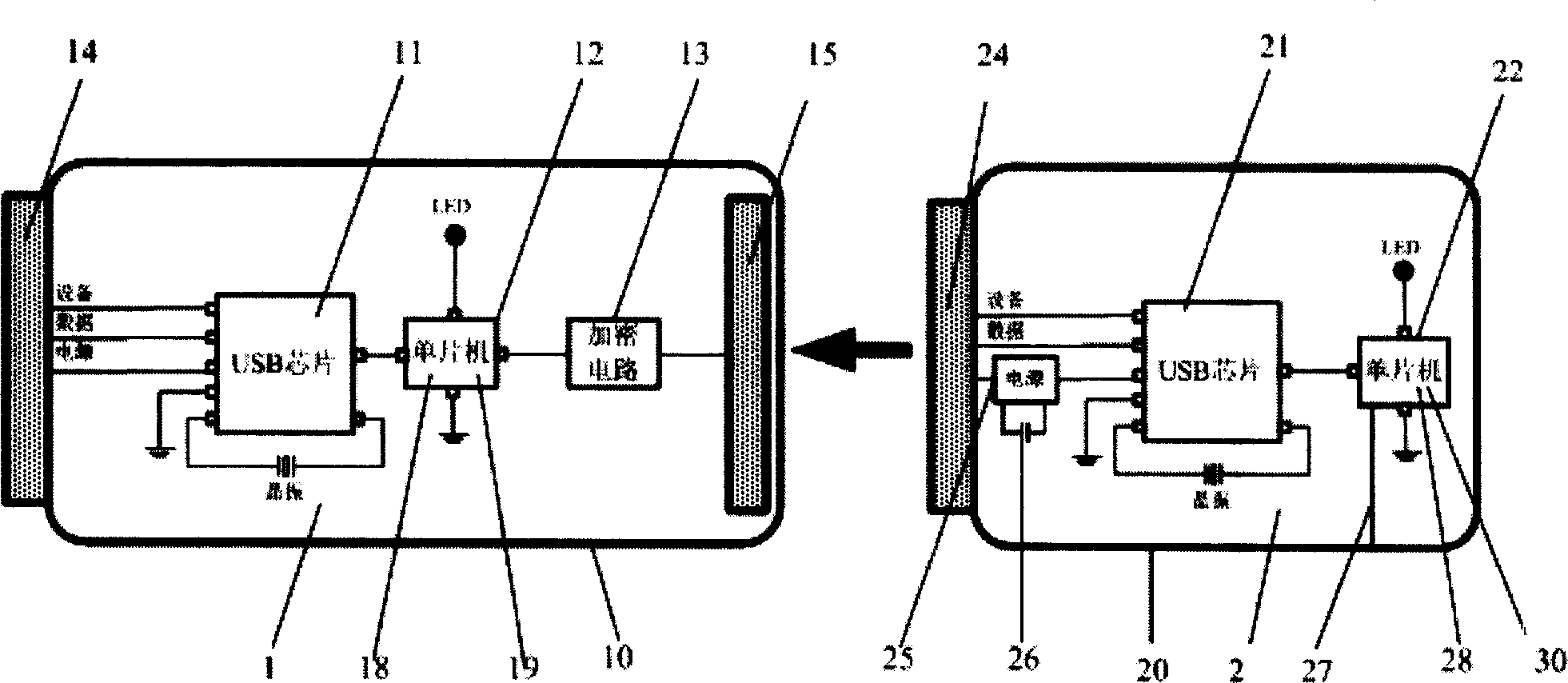
[0024] see figure 1 . This embodiment illustrates the basic structure of the secure U disk storage system device of the present invention. The safety U disk storage system device of the present invention adopts a paired composite U disk structure, which is composed of a main disk 1 and a secondary disk 2. The encryption circuit 13 connected to the output port of 12, the front plug-in 14 at the front of the housing 10 and the rear plug-in 15 at the rear of the housing 10 are composed of the power line contacts, equipment line contacts and data on the front plug-in 14 The line contact is connected with the corresponding port of the USB chip 11, and the rear plug-in 15 is connected with the output port of the encryption circuit. The front plug-in 24 of the sub-disk at the front part of the housing 20, wherein the sub-disk device line contacts and the sub-disk data line contacts on the sub-disk front plug-in 24 are connected to the corresponding ports of the sub-disk USB chip 21...
Embodiment 2
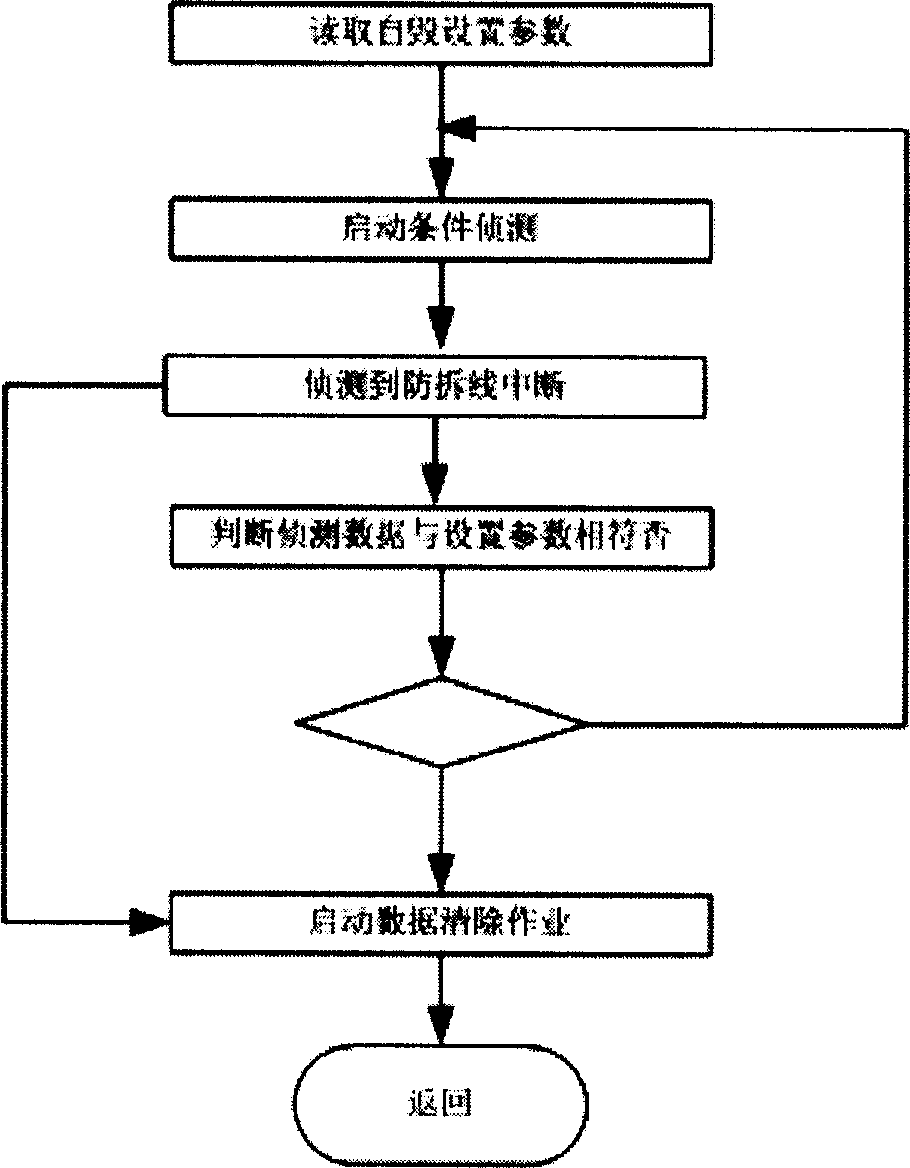
[0027] see figure 2 . This embodiment illustrates the processing flow of the secondary disk conditional self-destruct software.
Embodiment 3
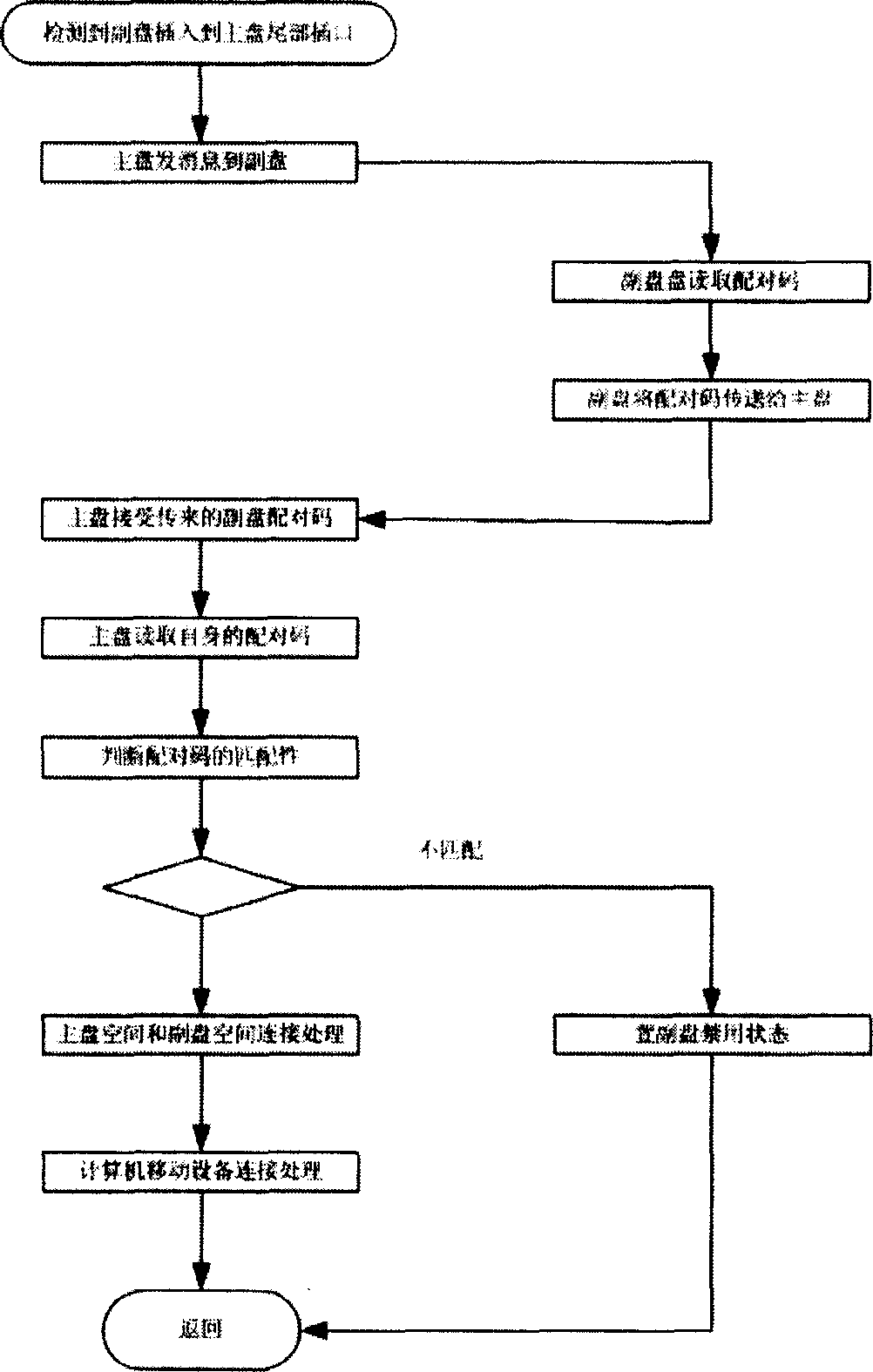
[0029] see image 3 . This embodiment illustrates the processing flow of the matching authentication software between the master disk 1 and the slave disk 2 .
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com