Method and device for improving utilization security of network information product
A technology for network information and information security, applied in transmission systems, user identity/authority verification, electrical components, etc., can solve problems such as cumbersome operations and poor security, and achieve the effects of improving security, preventing losses, and being easy to popularize.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
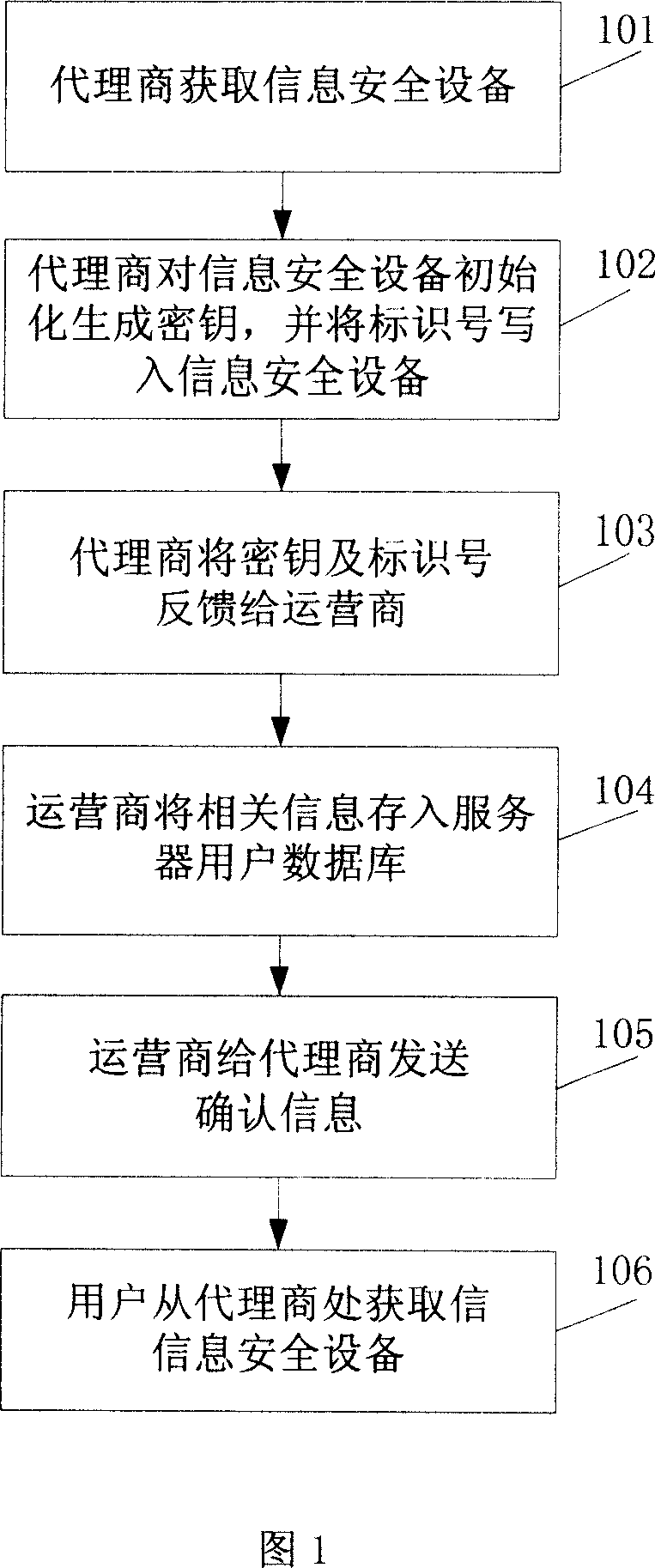
[0051] As shown in Figure 1, the method for initializing information security equipment specifically includes the following steps:
[0052] Step 101: The game agent obtains information security equipment from an information security equipment manufacturer.
[0053] Step 102: The agent initializes the information security device, that is, generates a key inside the information security device, and writes the identification number into the information security device.
[0054]There may be more than one key, and an identification number may correspond to only one key, or may correspond to multiple keys. There is more than one identification number written in an information security device, and it is selected according to the specific situation. The identification number includes the user account number, hardware serial number or specific data contained in the network information product. In this embodiment, the identification number is the user account number, which is mainly us...
Embodiment 2
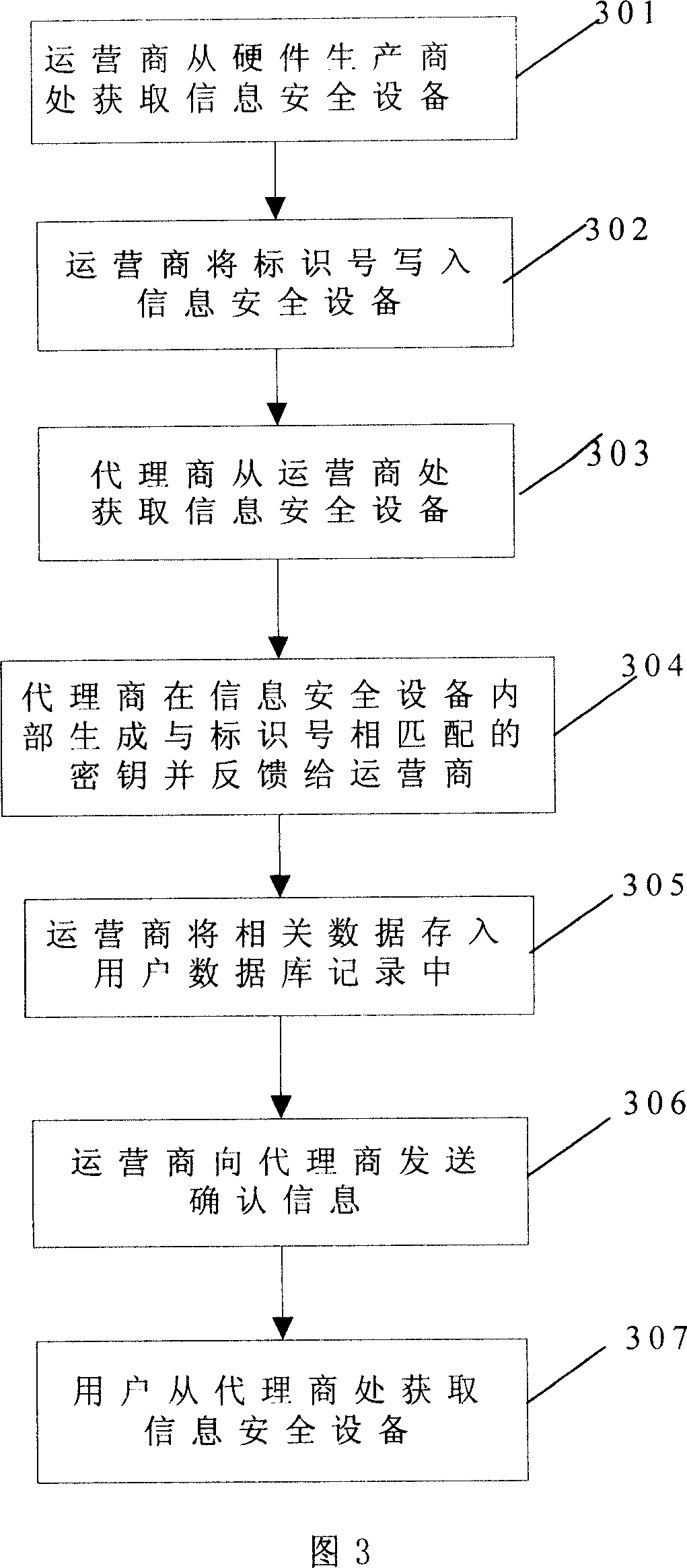
[0080] In this embodiment, the process for the user to use the information security device is the same as in embodiment 1, but in this embodiment, the information security device obtained by the game agent from the operator has pre-written the identification number inside, as shown in Figure 3 Show:
[0081] Step 301: The online game operator obtains information security equipment from the hardware manufacturer.
[0082] Step 302: The game operator writes the identification number inside the information security device, and stores it in the database of the game server.
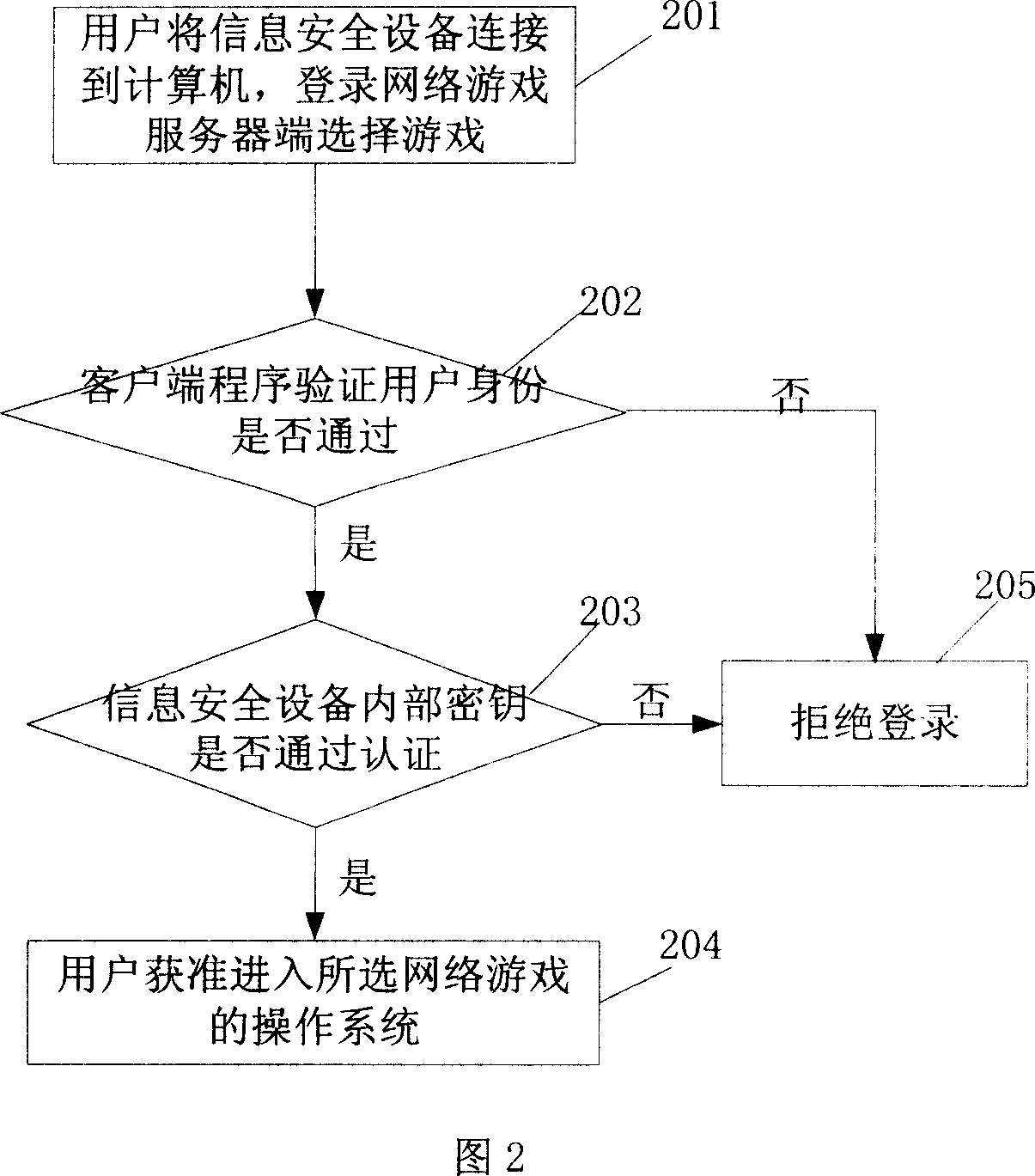
[0083] In this embodiment, the identification number is mainly used when the user logs in to the online game server for key verification. The game server program detects the matching key pre-stored in the user database through the identification number, and through the client program Access the information security device and verify the corresponding internal key.
[0084] Step 303: the agent obtains informa...
Embodiment 3
[0091] Referring to Fig. 4, the present invention also improves a system for improving the safety of using network information products, including:
[0092] Information security equipment, used to store network information products or user information;
[0093] The agent initialization module is used for the agent to initialize the information security device to generate a key after obtaining the information security device;
[0094] The operator stores information module, which is used to store keys and identification numbers;
[0095] The key authentication module is used for the server to use the key on the information security device to authenticate the user.
[0096] Wherein, the agent initialization module is also used for the agent to write the identification number inside the information security device.
[0097] Information security equipment specifically includes:
[0098] The user identity authentication module is used to internally verify whether the user is the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com