Method for recovering data damaged by virus programe, apparatus and virus clearing method
A technology for data recovery device and virus program, which is applied in the direction of electrical digital data processing, computer security device, digital data processing components, etc. recovery to wait
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
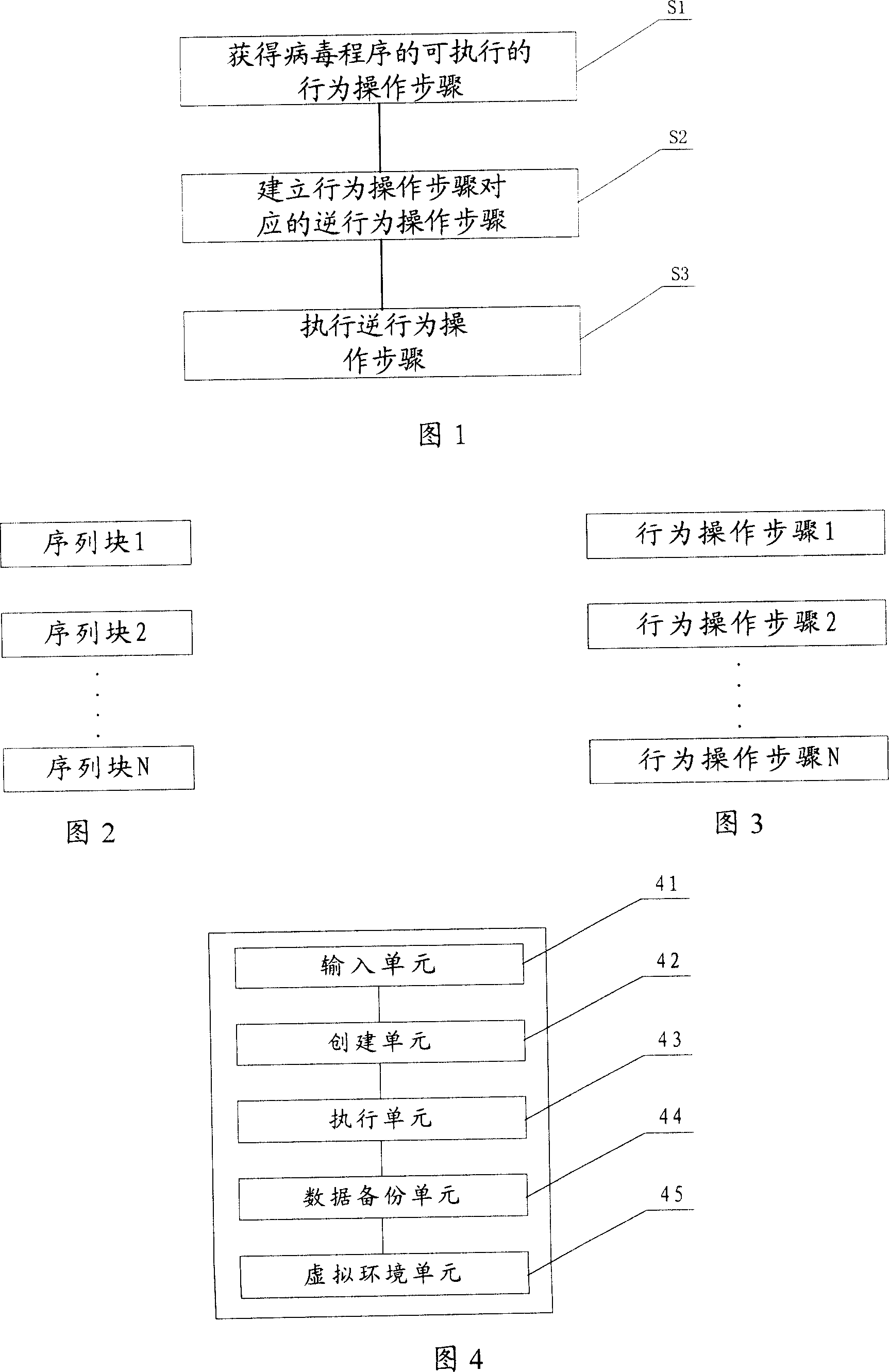
[0050] The core idea of the present invention is: according to the acquired destructive behavior operation steps of the virus program, establish the corresponding reverse behavior operation steps, and execute the reverse behavior operation steps, so as to realize the reverse operation of the virus program operation, and then realize the anti-virus Stripping of programs and recovery of data damaged by viruses.
[0051]Referring to FIG. 1 , it is a flow chart of steps of the method for recovering data damaged by virus programs according to the present invention, including the following steps.
[0052] Step s1, obtaining executable destructive behavior operation steps of the virus program;
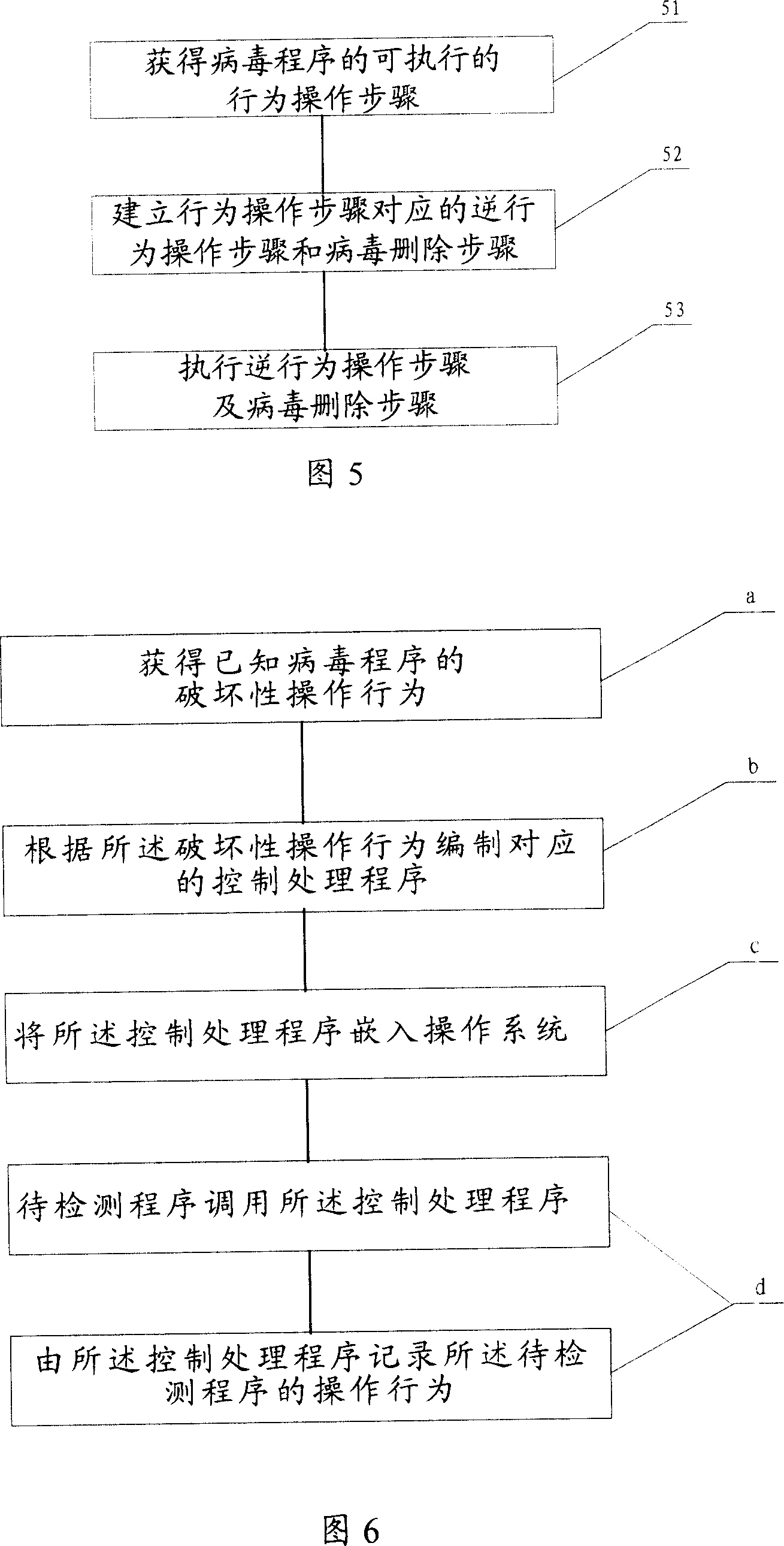
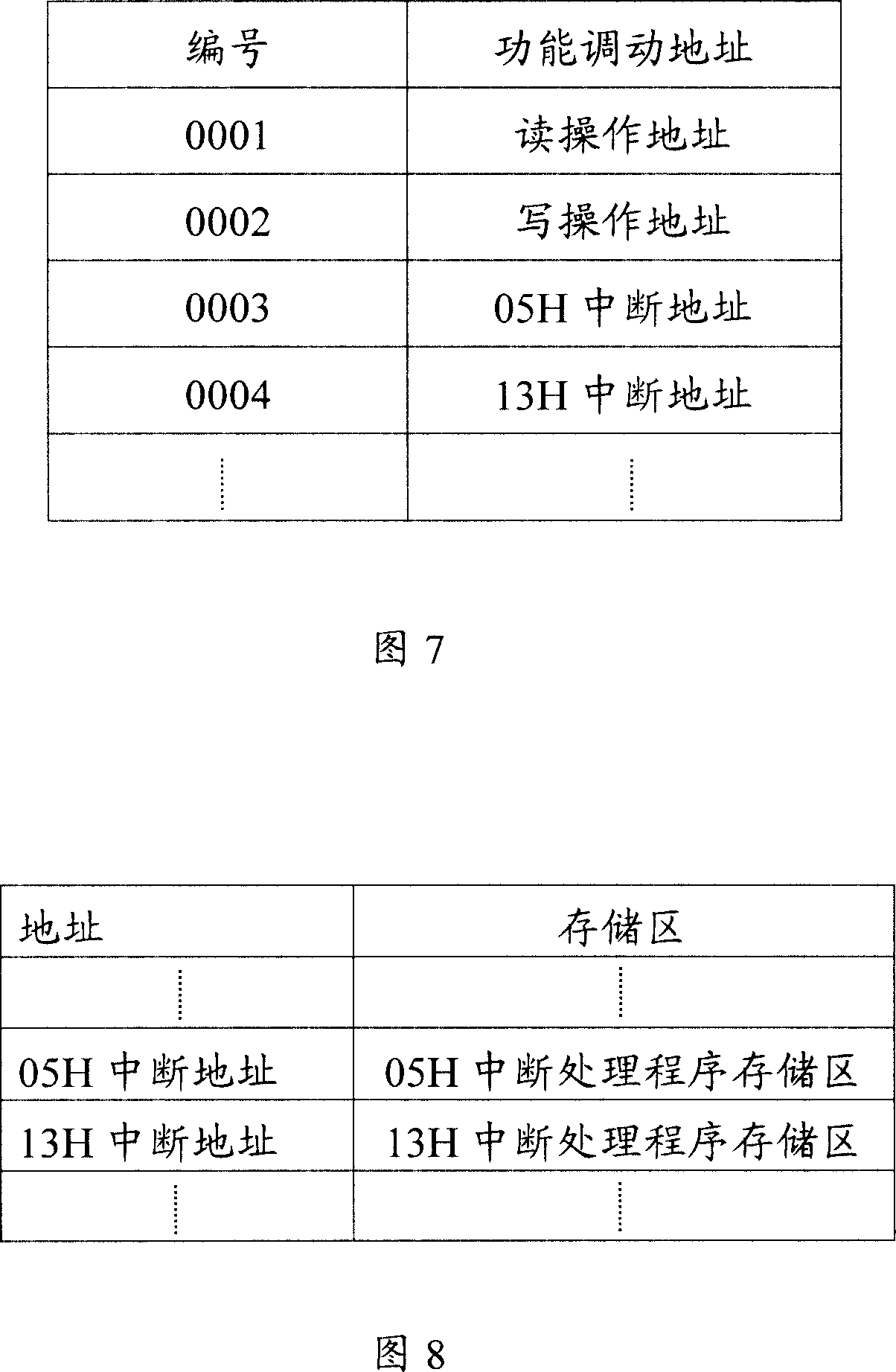
[0053] A virus program, like any computer program, has a series of source codes that can complete specific operations. A collection of multiple such source codes can be regarded as a source code sequence block that completes a specific function or result, as shown in Figure 2 A typical vir...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap