A method and system for consulting new authentication secret key
An authentication key and new key technology, which is applied in the field of negotiating new authentication keys, can solve problems such as leaking key data, no remedial measures, leaking root keys, etc., and achieve the effect of solving potential safety hazards
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
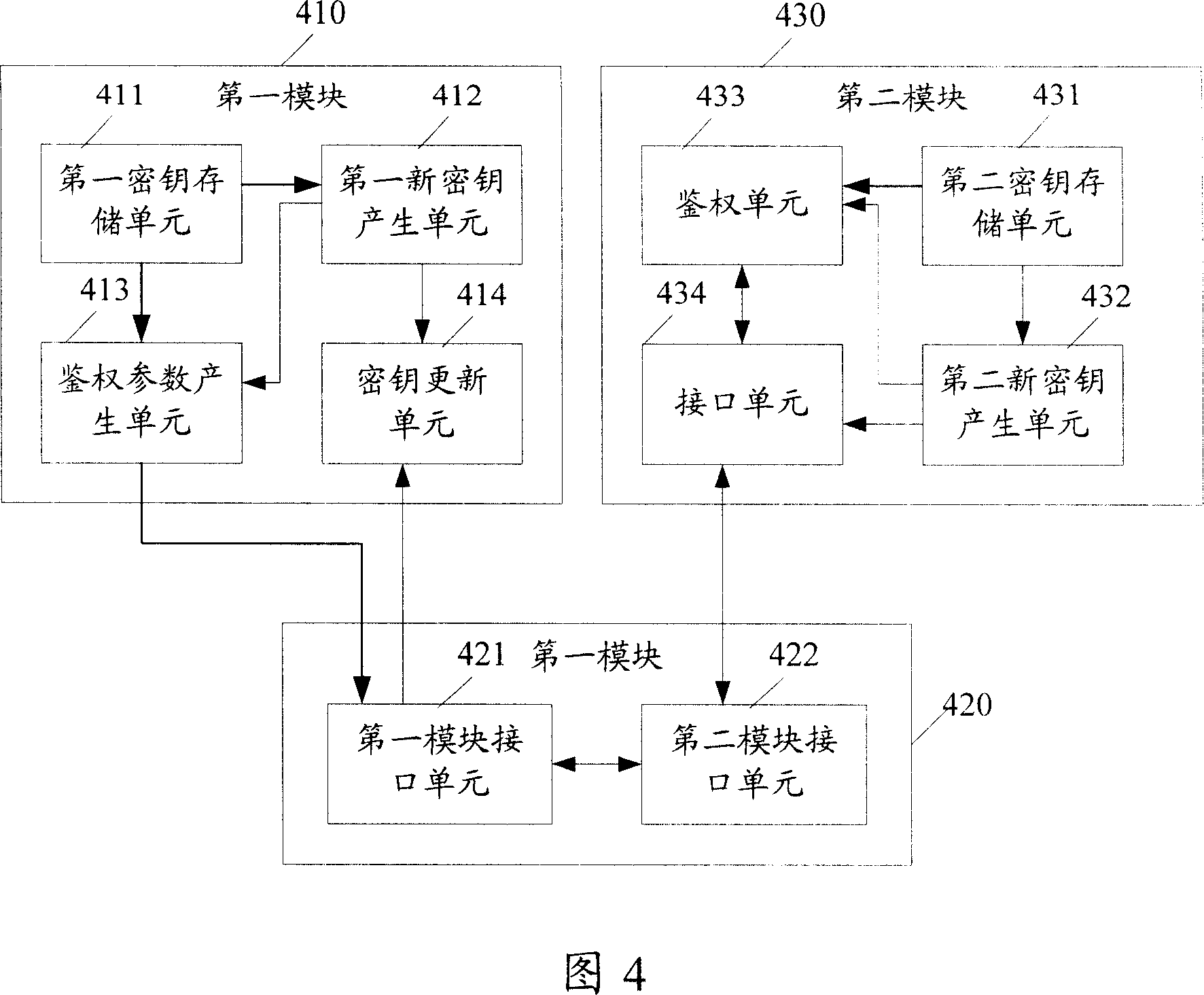
Image
Examples
Example Embodiment
[0049] Example one:
[0050] FIG. 3 is a flowchart of a method for negotiating a new authentication key in Embodiment 1 of the present invention. As shown in Figure 3, the process includes:
[0051] Step 301: The first module generates a random number RAND.
[0052] Step 302: Generate a first new key (NewAK1) and authentication parameters, and send the authentication parameters to the authentication agent.
[0053] In this step, the first module can generate NewAK1 according to RAND and the stored first key (AK1), or select one of multiple keys stored by itself as NewAK1; and the generated authentication parameters include RAND and MAC- A, and update key request information.
[0054] Wherein, in this embodiment, MAC-A is generated based on RAND and AK1 stored in the first module.
[0055] The key update request information can be represented by a bit in RAND, or can also be represented by a bit in MAC-A. When represented by a bit in RAND, the setting of this bit can be performed be...
Example Embodiment
[0085] Embodiment two:
[0086] In this embodiment, the first module further stores the first serial number SQN1, and the second module further stores the second serial number SQN2; the authentication parameters transmitted by the first module to the authentication agent further include the first serial number SQN1 and the desired authentication Right response (XRES), and the first module uses the serial number in the first module when generating the authentication parameters. When the authentication agent sends an authentication request to the second module, SQN1 is further carried, that is, RAND, MAC-A and SQN1 are carried, and the authentication of the first module to the second module is completed in the authentication agent.
[0087] Fig. 5 is a flowchart of the method for negotiating a new authentication key in the second embodiment of the present invention. As shown in Figure 5, the process includes:
[0088] Step 501: The first module generates a random number RAND.
[008...
Example Embodiment
[0120] Embodiment three:
[0121] In this embodiment, the generated authentication parameters further include the authentication management domain AMF.
[0122] Fig. 6 is a flowchart of the method for negotiating a new authentication key in the third embodiment of the present invention. As shown in Figure 6, the process includes:
[0123] In step 601, the first module generates a random number RAND.
[0124] Step 602: Generate a first new key (NewAK1) and authentication parameters, and send the authentication parameters to the authentication agent.
[0125] In this step, the first module can generate NewAK1 according to the generated RAND and the stored first key (AK1), or it can select one of the multiple keys stored by itself as NewAK1; and the generated authentication parameters include RAND, MAC-A and XRES, and update key request information.
[0126] Among them, in this embodiment, MAC-A is generated based on the random number RAND, AK1, SQN1 stored in the first module, and t...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap