Identification-based encryption system
An identity and public key technology, applied in transmission systems, digital transmission systems, public keys for secure communication, etc., can solve problems such as uncomfortable communication
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
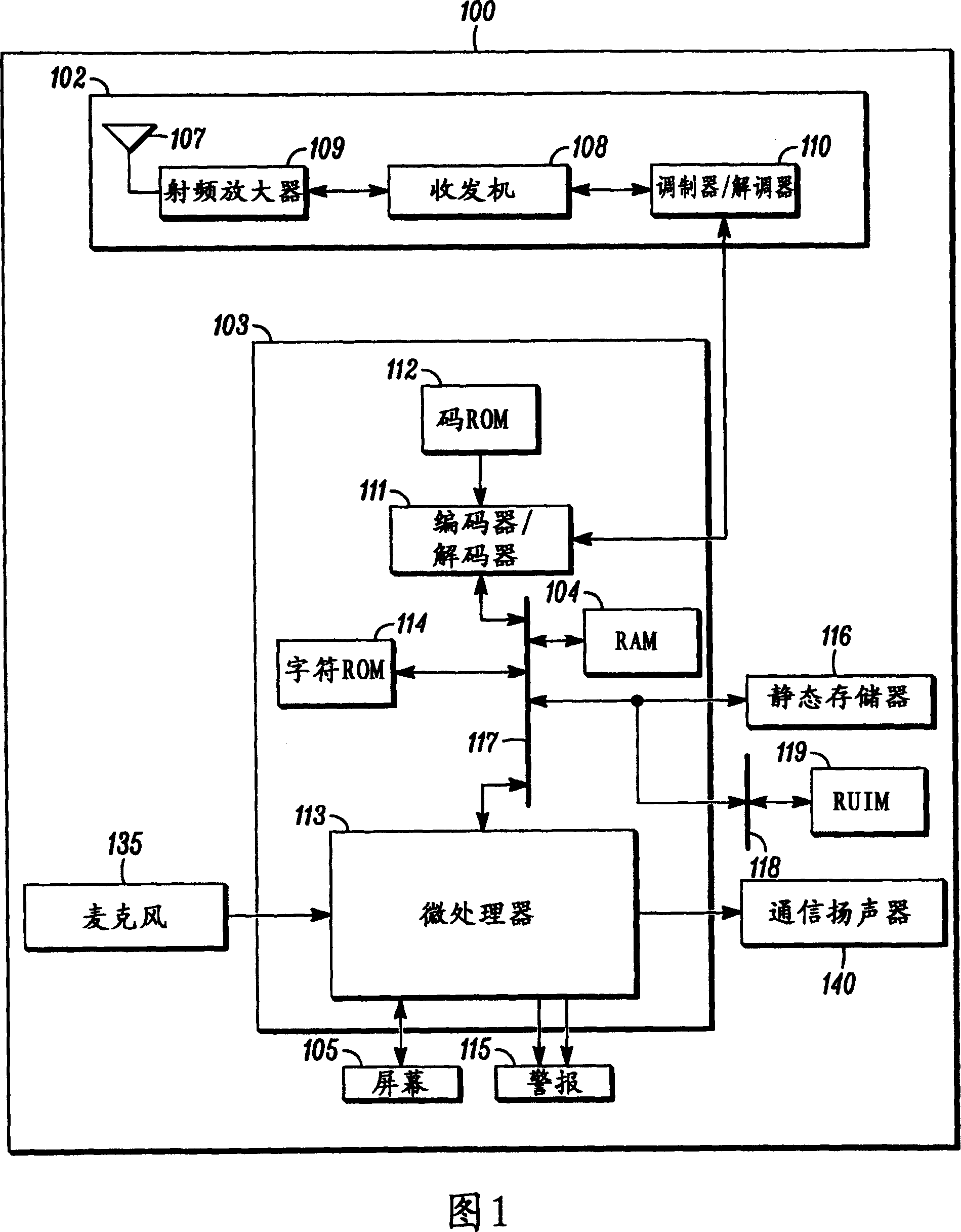
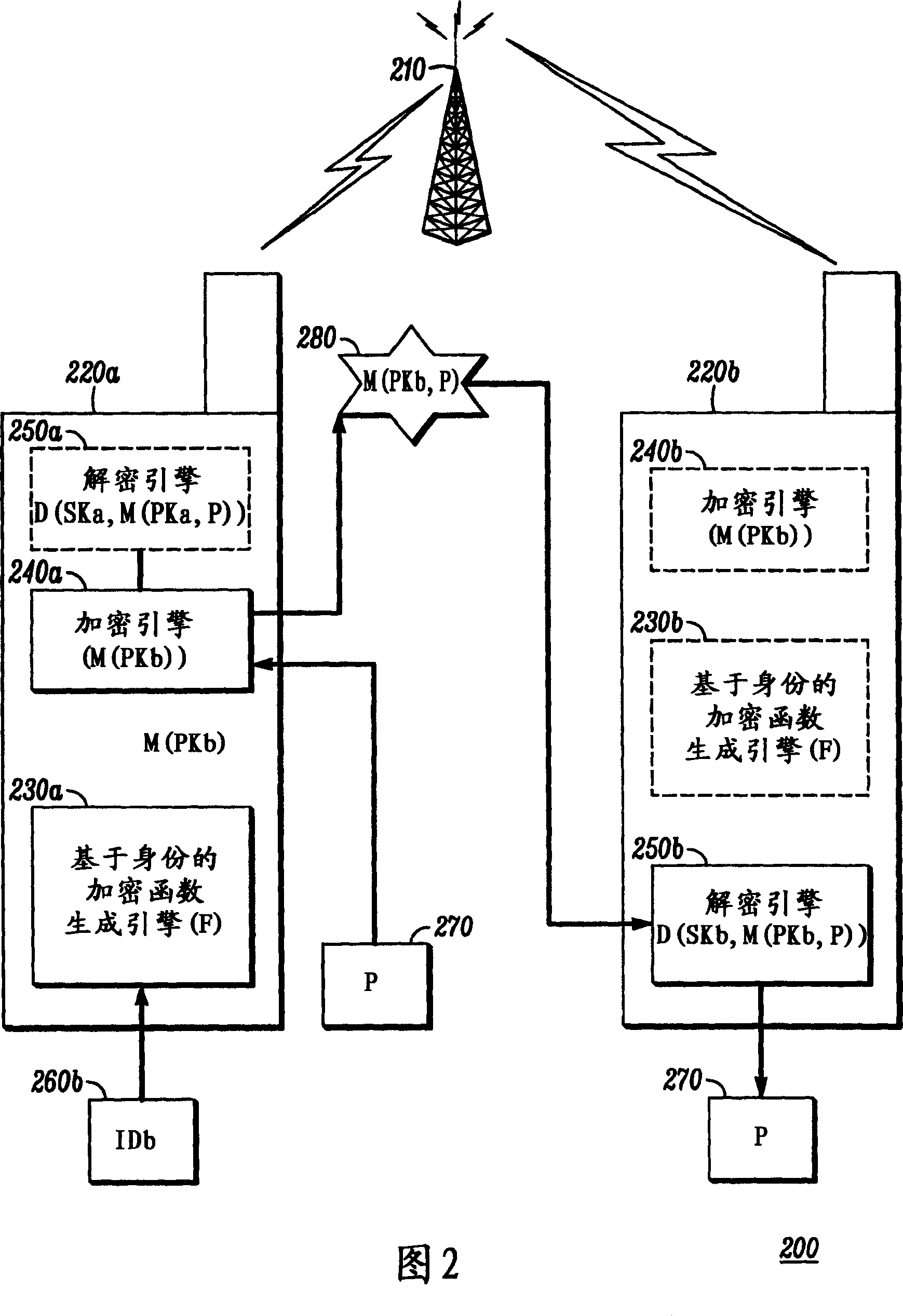
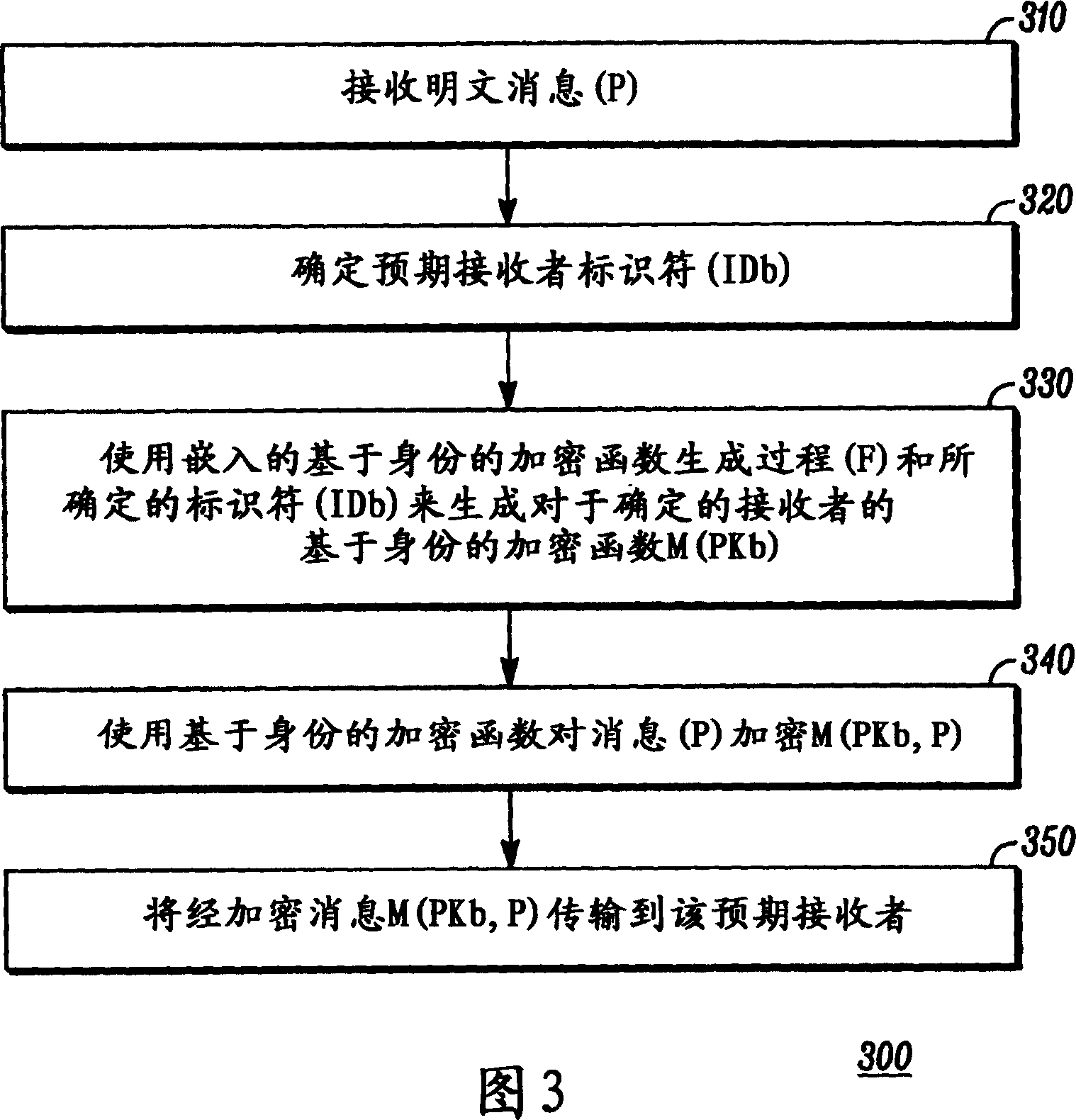
[0015] Before describing in detail embodiments according to the present invention, it should be noted that embodiments reside primarily in combinations of method steps and in apparatus components related to the activation and deactivation of the restricted service provider mode in an electronic device. Accordingly, apparatus components and method steps are reproduced using conventional symbols in the drawings and only those specific details that are relevant to an understanding of the embodiments of the invention are shown so as not to overwhelm those of ordinary skill in the art with the general knowledge described herein. Bright details obscure the disclosure.
[0016] In this document, relational terms such as first and second, top and bottom, etc., may be used solely to distinguish one entity from another, or one action from another, without requiring or implying any relationship between these entities or actions. Any actual such relationship or sequence. The term "compri...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com