.Net program protection method and system
A program protection and program technology, applied in the field of information security, can solve problems such as heavy workload, high cost, and tedious development cycle, and achieve the effects of reducing development cost, improving development efficiency, and simplifying the development process
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
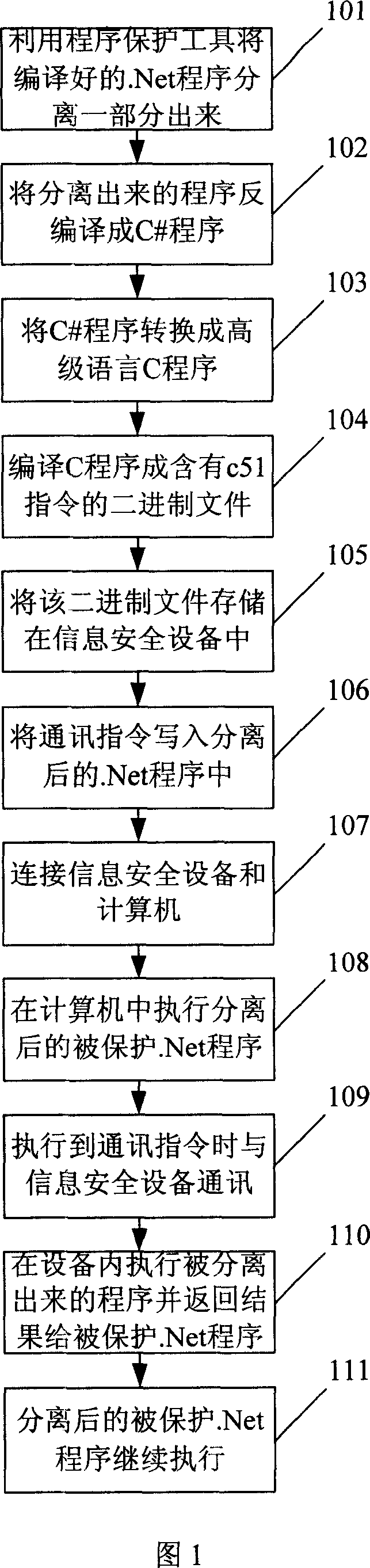
[0064] In the present embodiment, the information security device can realize the c51 virtual machine function. Referring to FIG. 1, the present invention provides a method for .Net program protection, first perform the following steps:
[0065] Step 101: using a program protection tool to automatically separate a part of the compiled protected .Net program;
[0066] The separation refers to automatically searching and separating the qualified program segments according to the class or function name, and the separated program segments are part of the compiled .Net program (which contains the IL instruction text); conditional block;
[0067] Step 102: The program protection tool decompiles the separated program into a C# program, and can also be decompiled into other programs based on the .Net architecture, such as C++.net, J#, VB.net, etc.;
[0068] Step 103: the program protection tool converts the C# program into a high-level language C program using a syntax analyzer;
[...
Embodiment 2
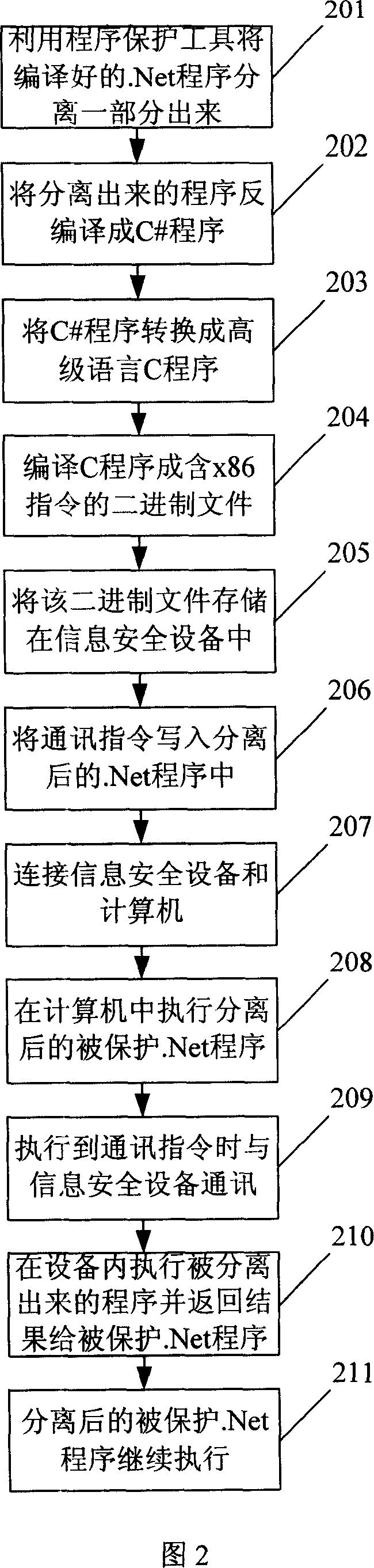
[0142] In this embodiment, the information security device can realize the x86 virtual machine function. Referring to FIG. 2, the present invention also provides a method for .Net program protection, first perform the following steps:
[0143] Step 201: using a program protection tool to automatically separate a part of the compiled protected .Net program;
[0144] The separation refers to automatically searching and separating the qualified program segments according to the class or function name, and the separated program segments are part of the compiled .Net program (which contains the IL instruction text); conditional block;
[0145] Step 202: The program protection tool decompiles the separated program into a C# program, and can also be decompiled into other programs based on the .Net architecture, such as C++.net, J#, VB.net, etc.;
[0146] Step 203: the program protection tool converts the C# program into a high-level language C program using a syntax analyzer;
[01...
Embodiment 3
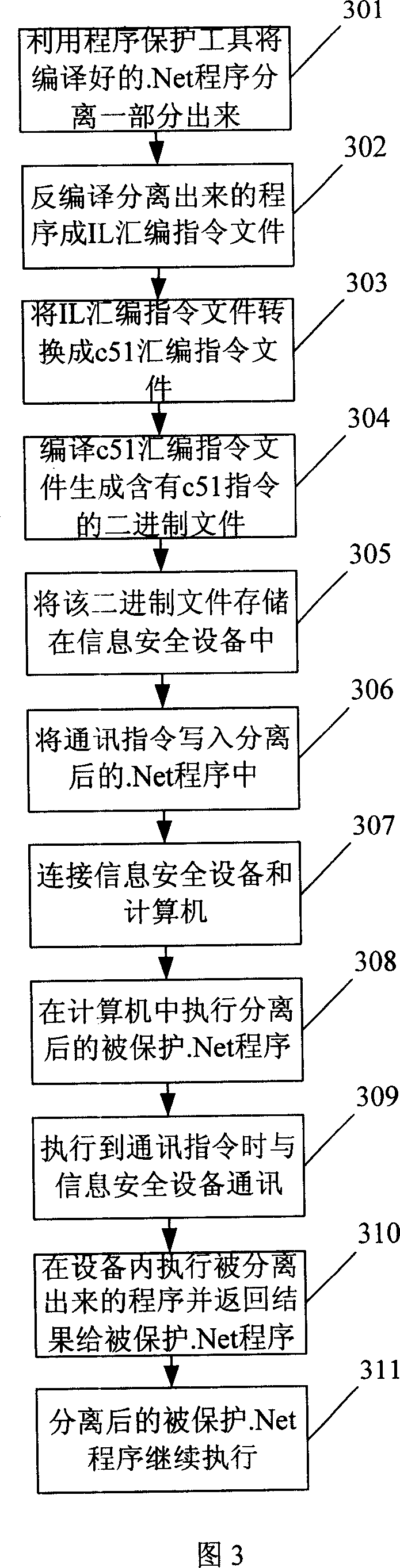
[0159] In this embodiment, the information security device can realize the c51 virtual machine function. Referring to FIG. 3, the present invention also provides a method for .Net program protection, first perform the following steps:
[0160] Step 301: using a program protection tool to automatically separate a part of the compiled protected .Net program;
[0161] The separation refers to automatically searching and separating the qualified program segments according to the class or function name, and the separated program segments are part of the compiled .Net program (which contains the IL instruction text); conditional block;
[0162] Step 302: the program protection tool decompiles the separated program into an IL assembly instruction file;
[0163] Step 303: the program protection tool converts the IL assembly instruction file into a c51 assembly instruction file by using a syntax analyzer;
[0164] Step 304: the program protection tool uses the keil c51 compiler to co...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com