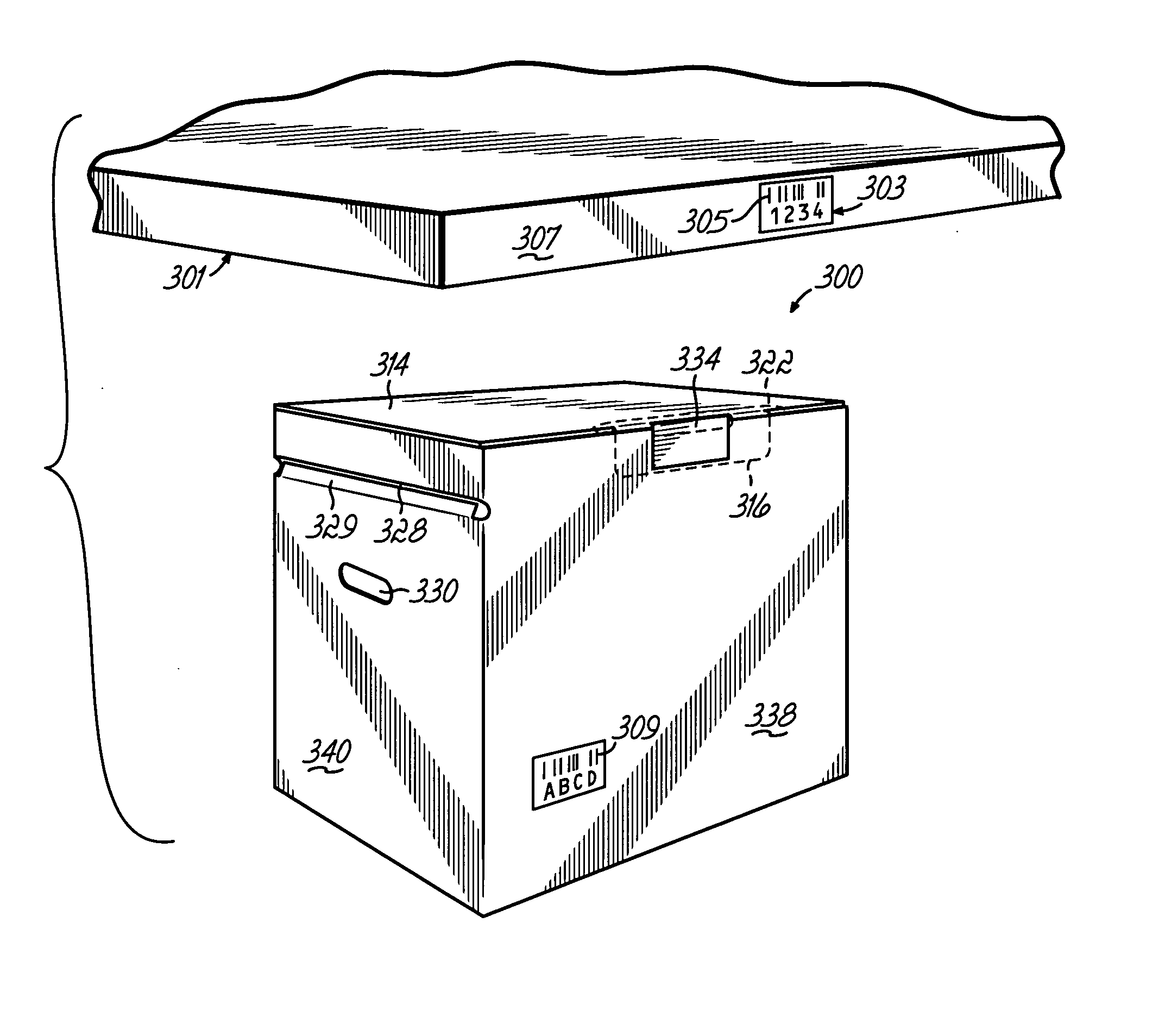
Item collection bin and disposal method
a technology for items and bins, applied in the field of collection and confidential disposal of items, can solve problems such as unauthorised removal, and achieve the effect of improving the security of the collection process
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
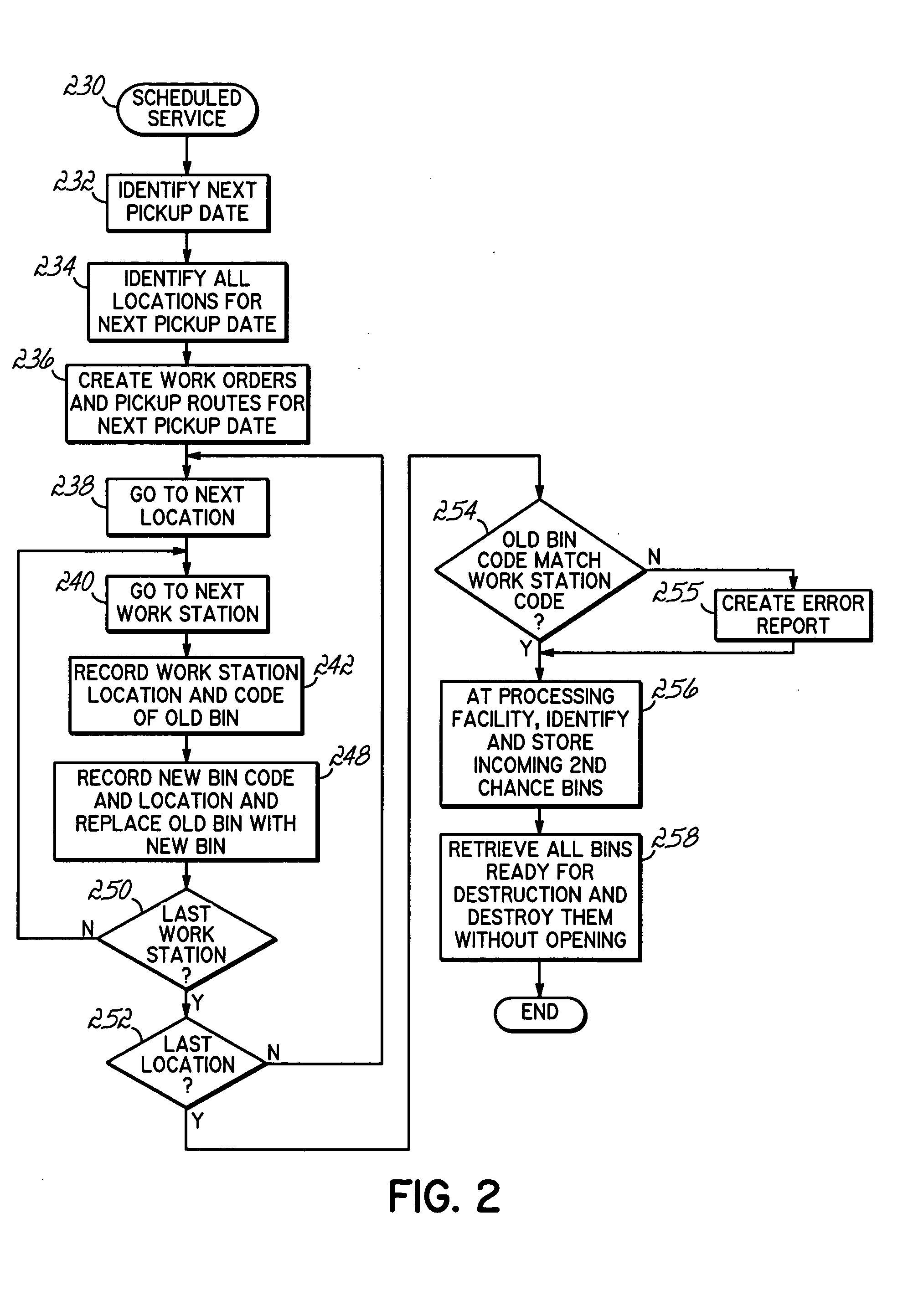
[0017] The confidential items collection and disposal process of the present invention has several different embodiments.
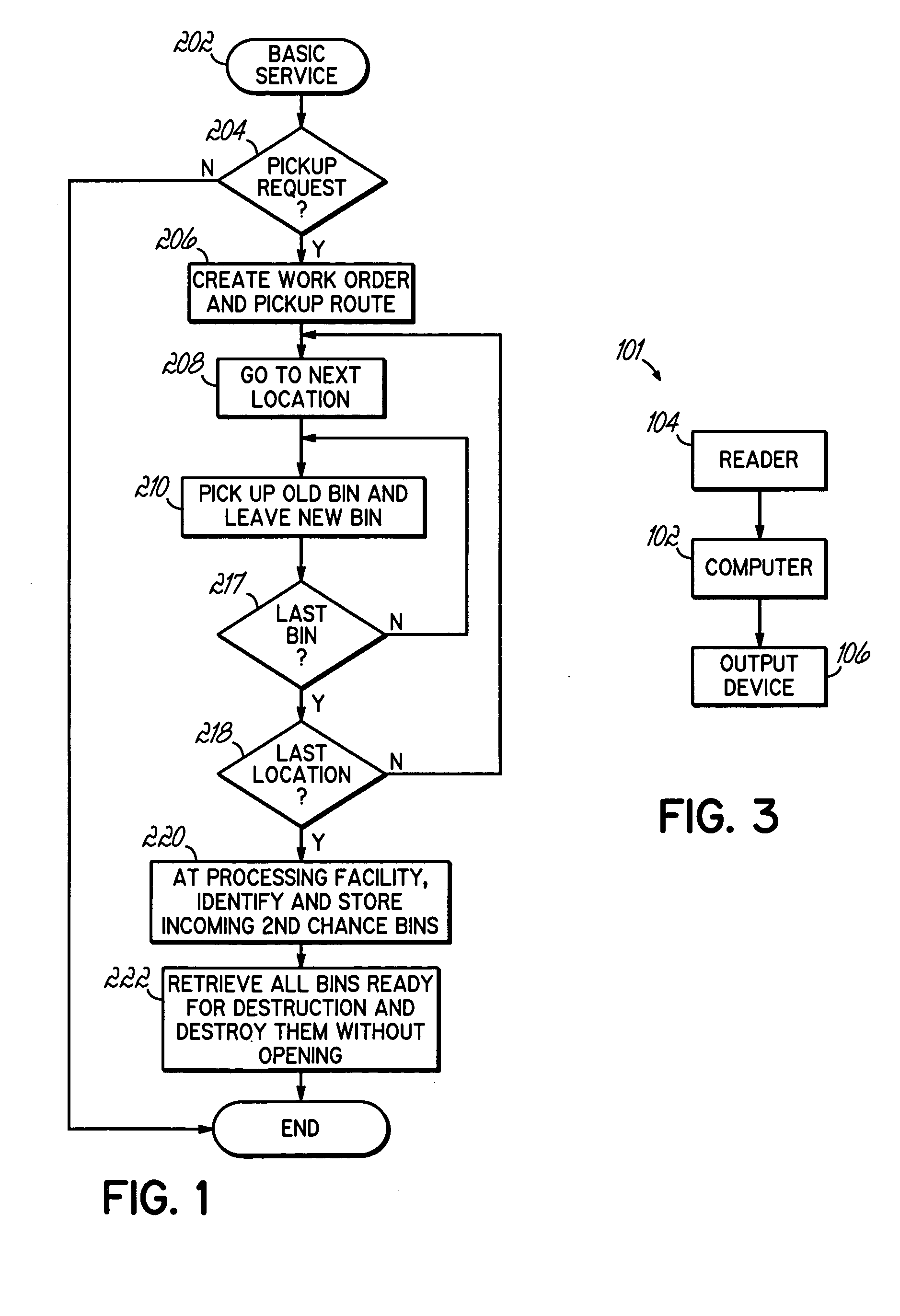
[0018] Basic Service
[0019] As with many item collection and disposal services, a user is able to select different levels of service. One embodiment of the present invention contemplates a collection and disposal process that is initiated substantially by the user on an as-needed basis.
[0020] The flowchart of FIG. 1 illustrates an exemplary process flowchart of the activities and functions that occur with the Basic Service. With the Basic Service, the collection and disposal service receives a pickup request (step 204) from the user. The user often makes the pickup request when their item collection bins are relatively full. Typically, a lead-time of one or more days is helpful, so that different customer destination stops can be scheduled in an efficient manner. However, requests can also be handled on a near real-time basis, such that a pickup request is handl...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com