Method of detecting memory leak causing portion and execution program thereof
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
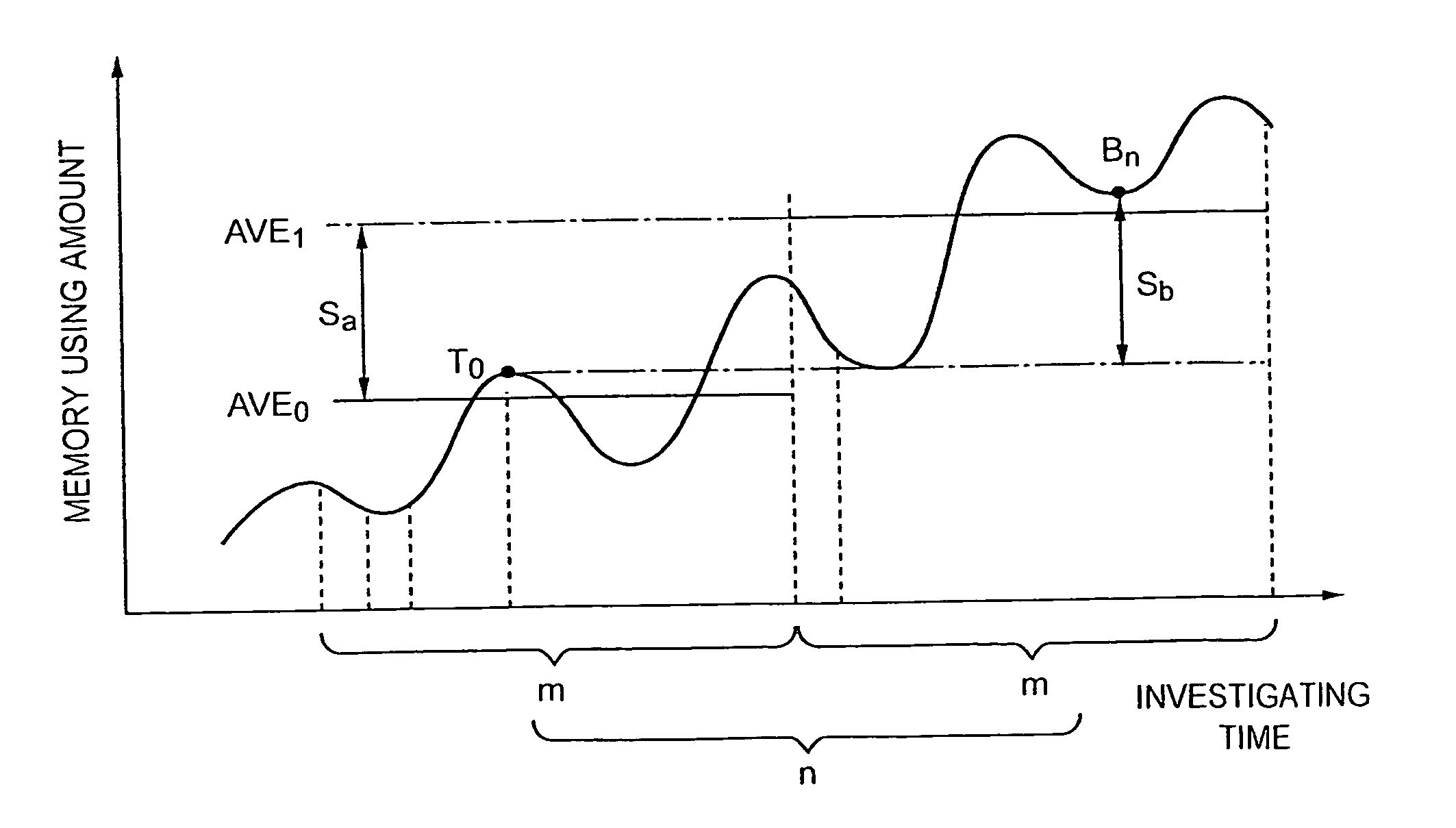
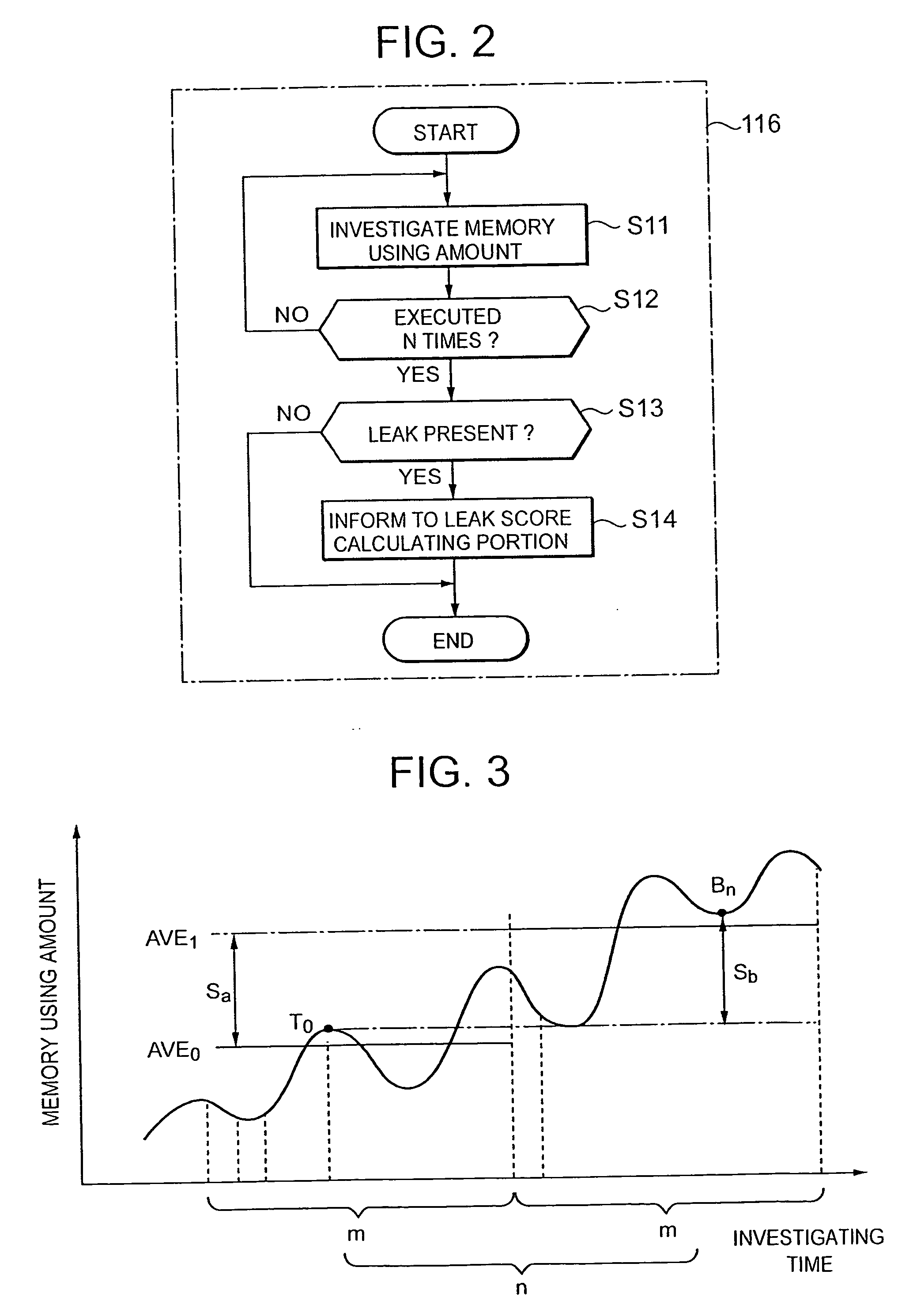
[0055] An embodiment of a method of detecting a memory leak causing portion according to the present invention will be now explained in the followings in reference to the drawings.
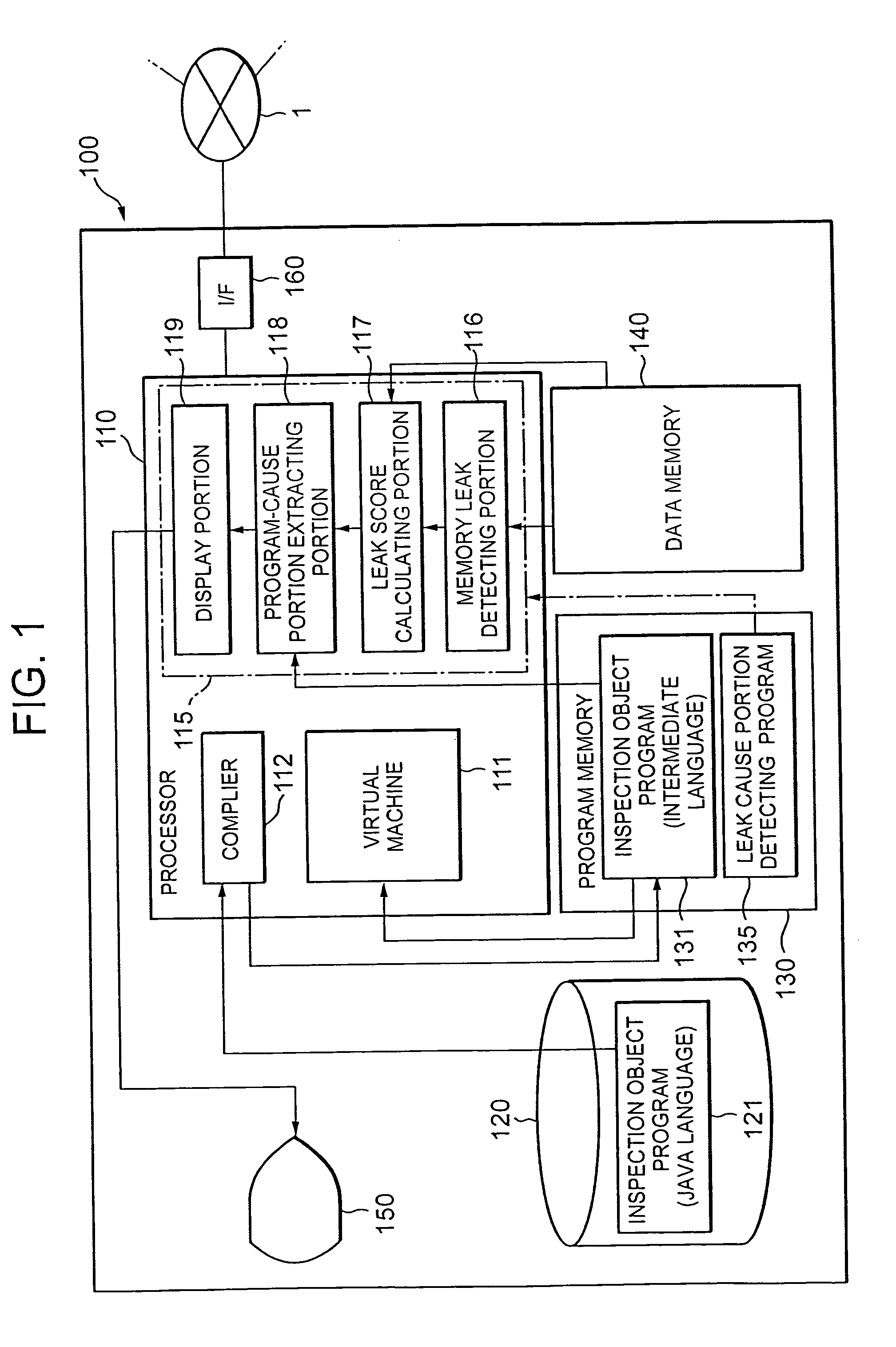
[0056]FIG. 1 is a view showing a configuration of a computer 100 executing a method of detecting a memory leak causing portion according to the embodiment.
[0057] The computer 100 is a server connected to a network 1. The server 100 is provided with a processor 110 for executing various processings, a program memory 130 stored with various programs 131, 135 executed by the processor 110, a data memory 140 stored with various data, an external storage device 120, a display device 150, an interface 160 for communicating with other device via the network 1.
[0058] The external storage device 120 is stored with a program 121 for executing a Web service provided by the server 100. The program 121 is described in Java language.
[0059] The program memory 130 is stored with a program 131 in which the program 121 ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com