Mobile computer security cabinet
a computer and mobile technology, applied in the field of office equipment theft prevention, can solve the problems of theft, computer, control or monitoring the operation of the conveyer belt on the factory floor, and the unattended computer of the operator, and achieve the effect of preventing theft, reducing the cost of replacement of computer equipment, and reducing the cost of replacemen
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
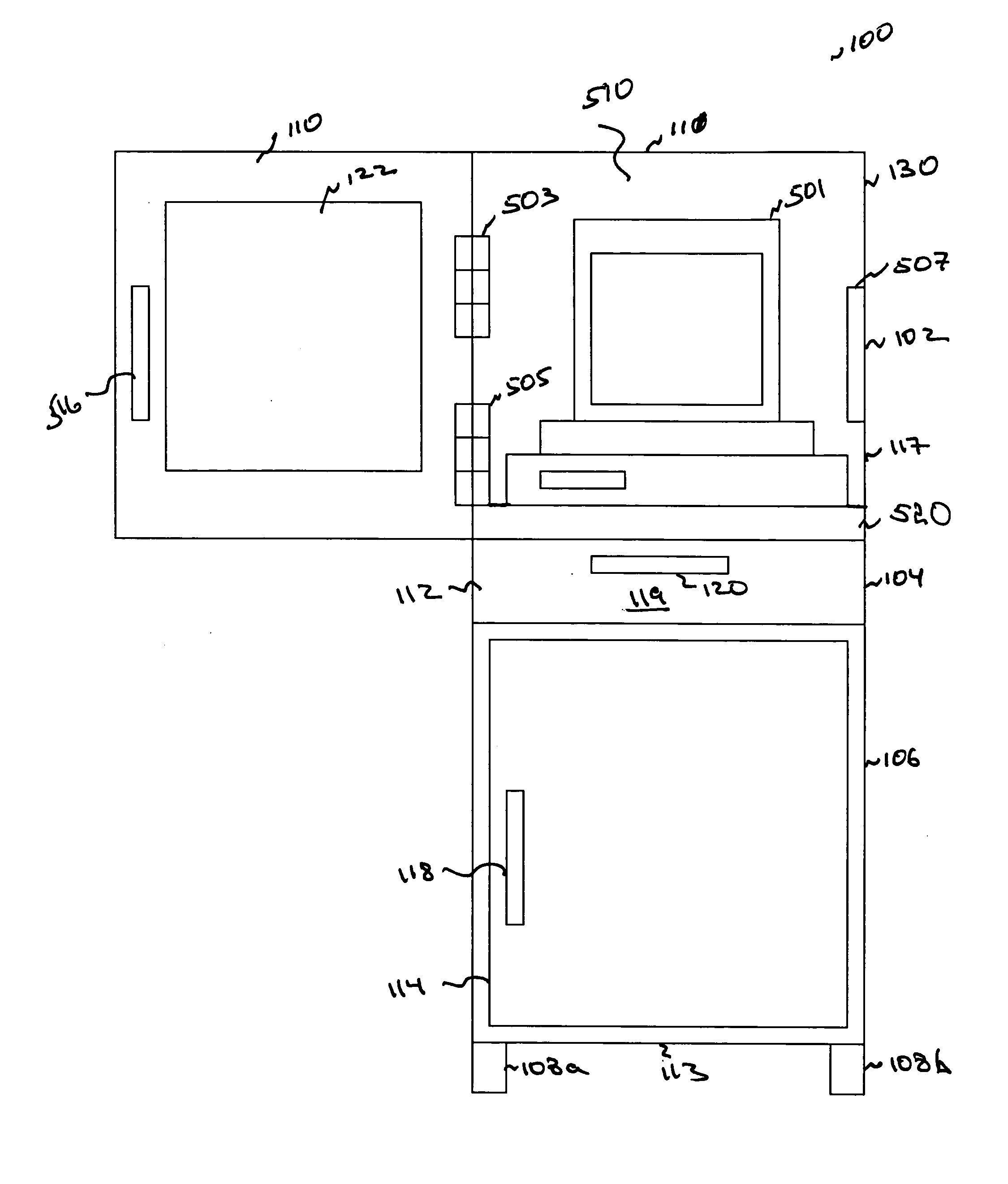
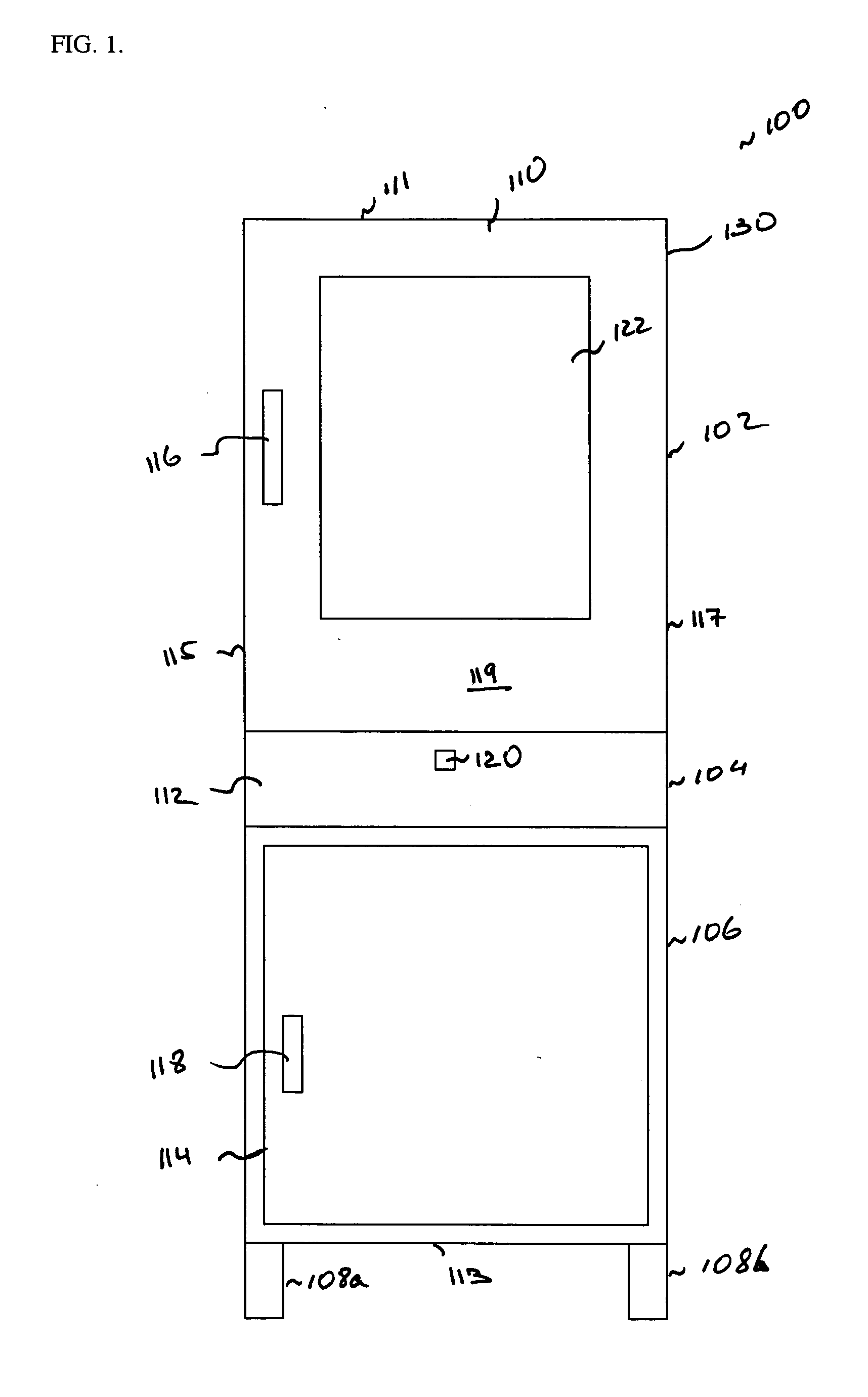
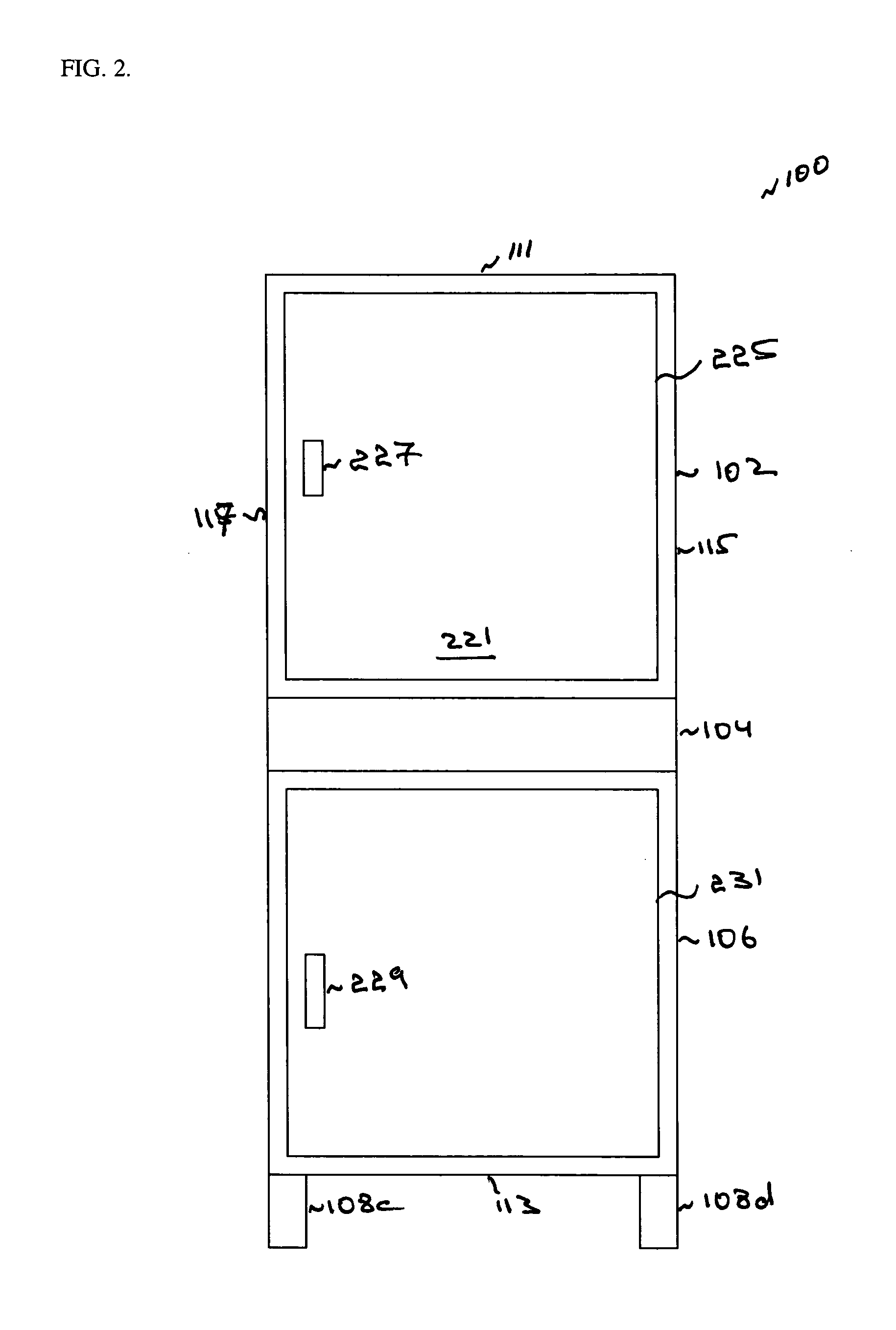
[0020] The present invention is a mobile computer security cabinet. The computer cabinet includes three enclosures. The enclosures accommodate a computer or other computer related equipment and paraphernalia. A first enclosure accommodates a monitor. A second enclosure accommodates keyboard and a mouse. A third enclosure accommodates a central processing unit, printer, computer manuals, and other things. The second enclosure is spaced between the first and the third enclosures. The three enclosures communicate with each other using a channel composed of a plurality of openings made in interior portions of the three enclosures. Wires connecting the computer equipment can be placed in the channel. Such arrangement provides greater security to the computer equipment placed in the cabinet. In an alternate embodiment, the enclosures can be designed so that one enclosure can be accessed through another. This arrangement provides lesser security and may be suitable for locations where maxi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com