Methods and systems for securing content played on mobile devices
a mobile device and content technology, applied in the field of mobile device identification and authentication, can solve the problems of limited profiles based on that usage, content targeting methods that face various challenges, and misleading profiles,
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
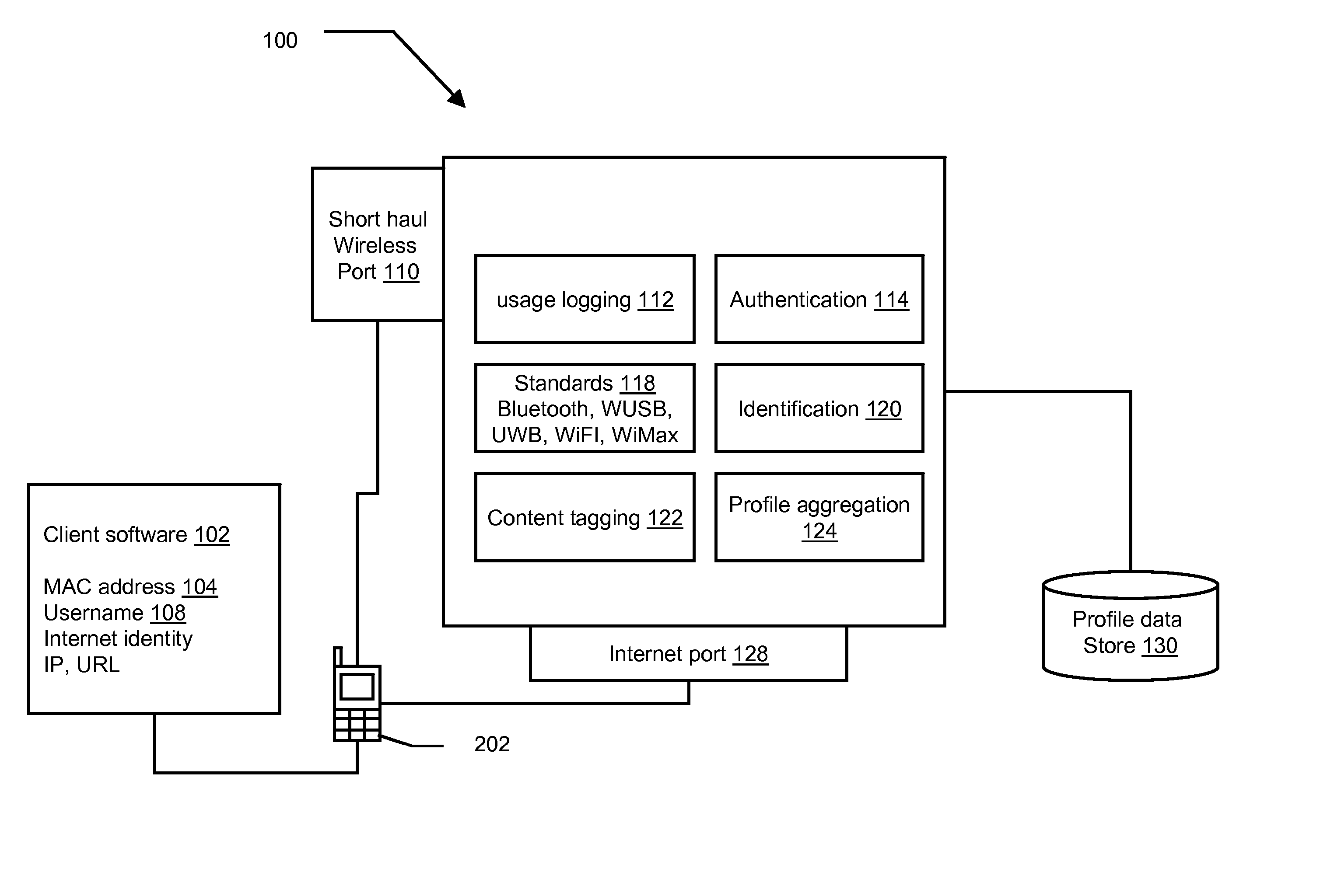
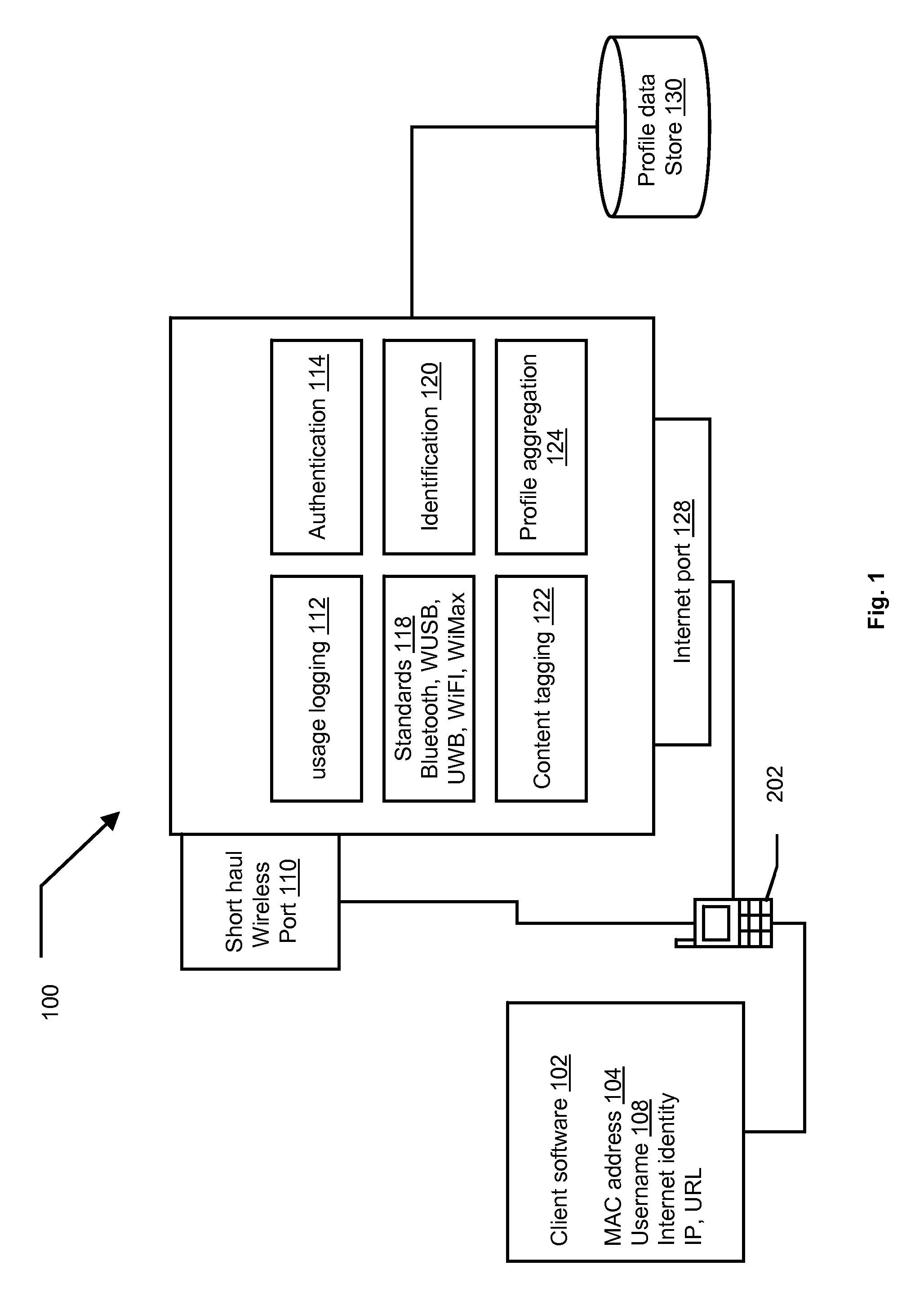
[0056] Referring to FIG. 1, in certain preferred embodiments of the methods and systems disclosed herein, a DSI-based authentication / identification platform 100 may include profile aggregation 124, content tagging 122, user identification 120, authentication 114, usage logging 112, a standards facility 118, a short haul wireless port 110, a profile database 130, an internet port 128, client software 102, device MAC addresses 104, and a device username 108. A mobile device 202 may include some portions and functionality of the platform 100. The mobile device 202 may also be connected to the platform 100 through the short haul wireless port 110 and / or through the Internet port 128.
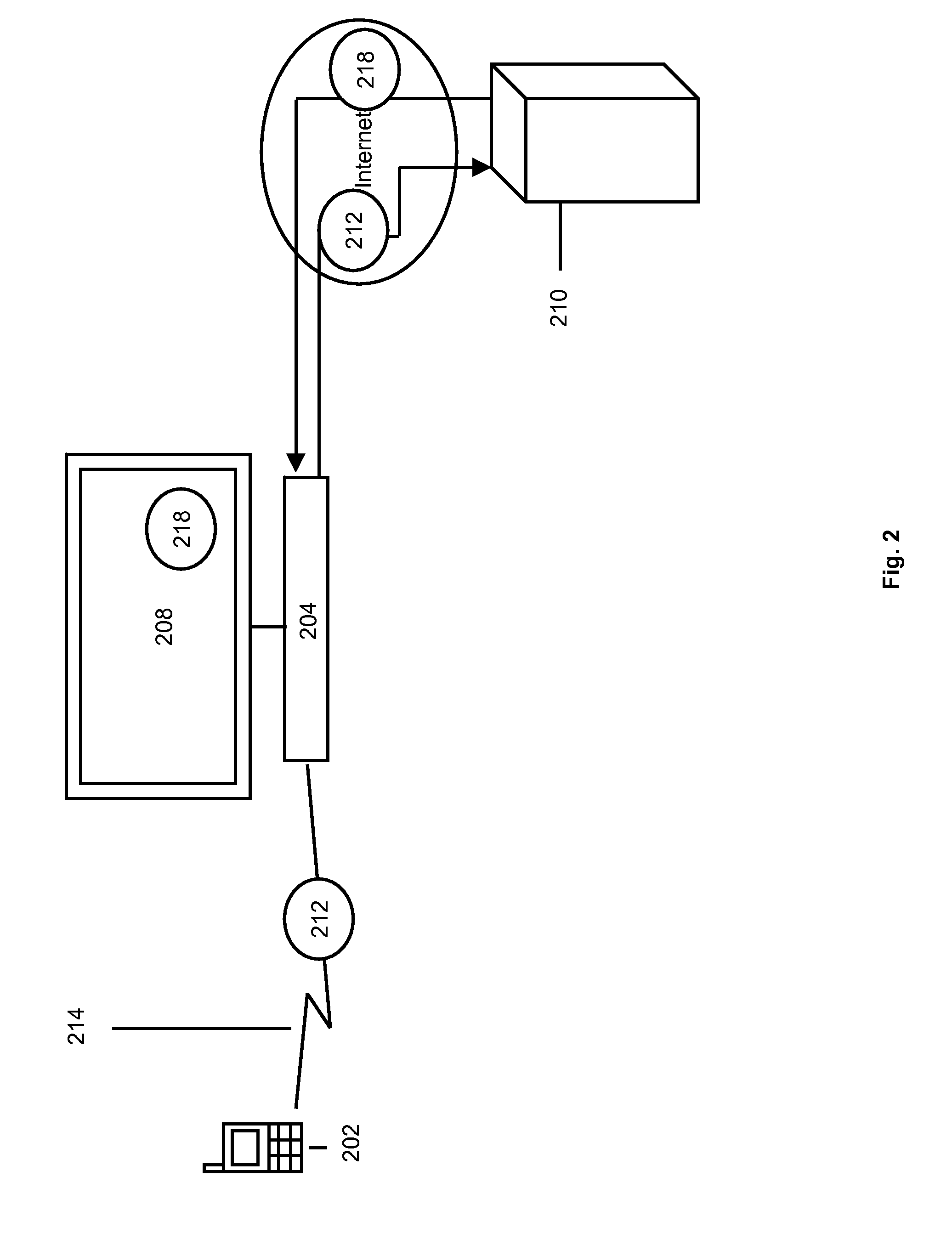
[0057]FIG. 2 depicts using a mobile handset DSI to facilitate delivery of targeted television advertising 218. A mobile handset 202 may be in communication with a set-top box 204 or other Internet-connected device that is controlling a television 208. The mobile handset 202 may be in communication with the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com