Automated identification of phishing, phony and malicious web sites
a technology of automatic identification and malicious web sites, applied in the computer system field, can solve the problem of requiring tremendous skill to detect the fakeness of the websi
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
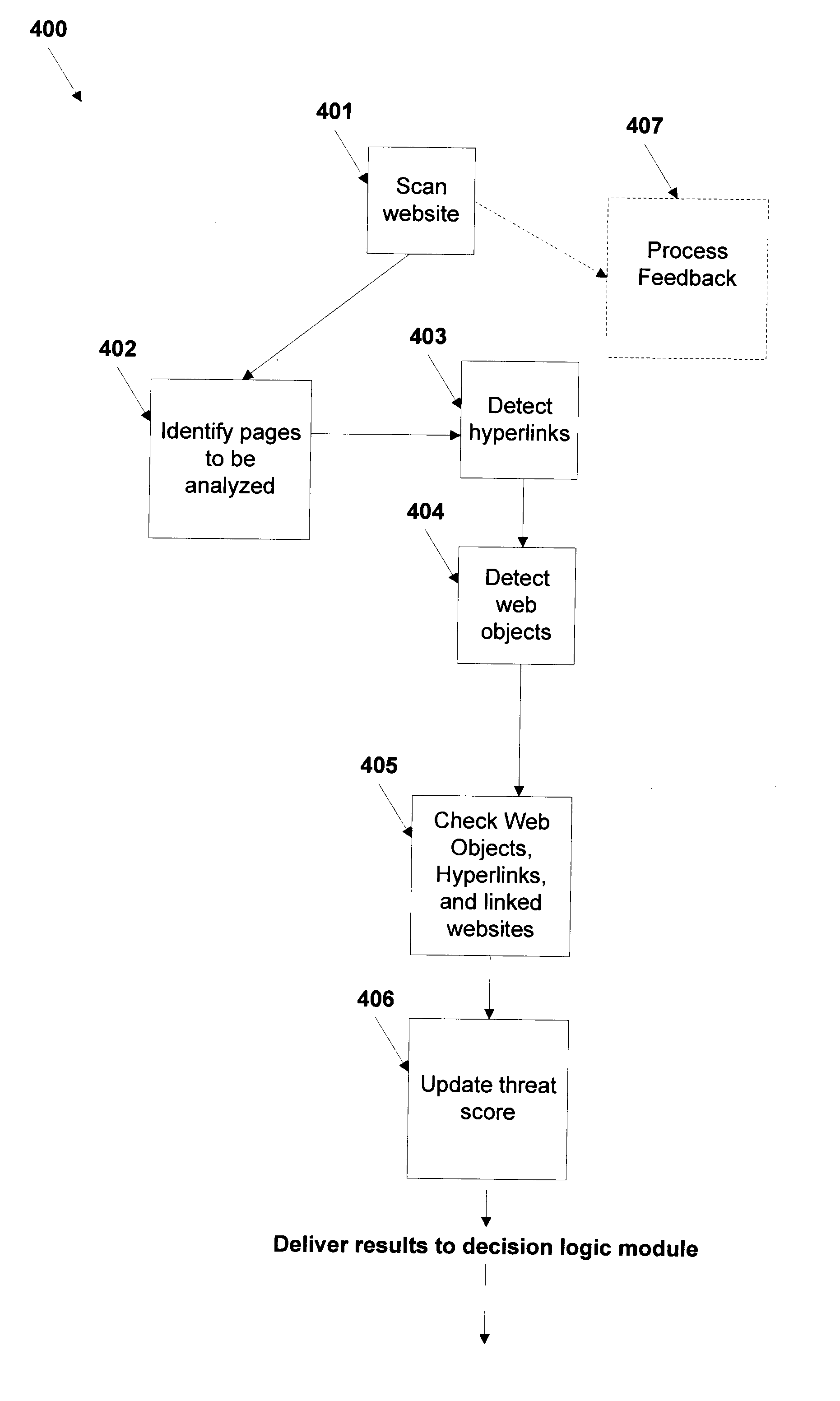
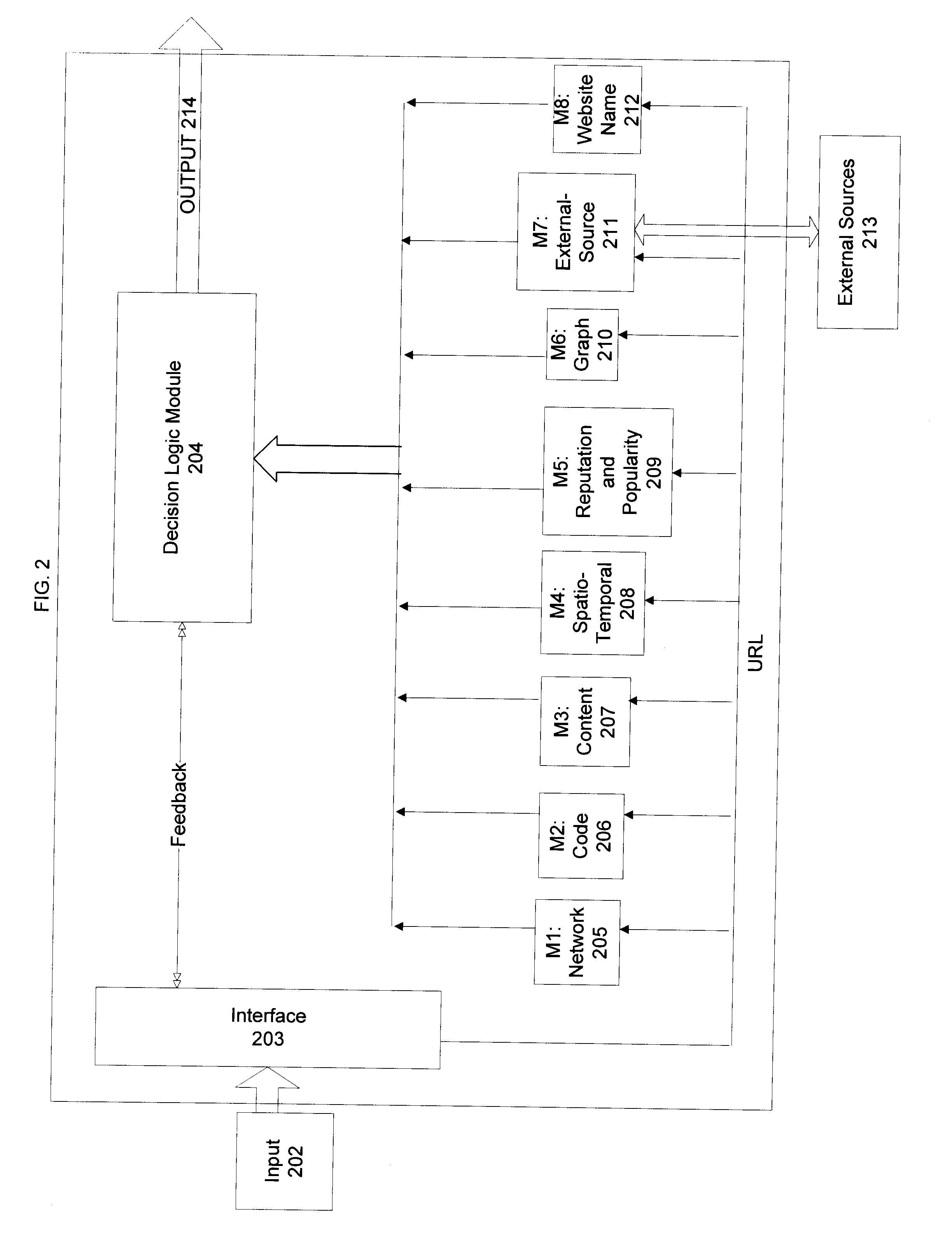
[0023]A method and system for automated identification of phishing, phony, and malicious web sites are disclosed. According to one embodiment, a computer implemented method, comprises receiving a first input, the first input including a universal resource locator (URL) for a webpage. A second input is received, the second input including feedback information related to the webpage, the feedback information including an indication designating the webpage as safe or unsafe. A third input is received from a database, the third input including reputation information related to the webpage. Data is extracted from the webpage. A safety status is determined for the webpage, including whether the webpage is hazardous by using a threat score for the webpage and the second input, wherein calculating the threat score includes analyzing the extracted data from the webpage. The safety status for the webpage is reported.
[0024]The present method and system assess the safety and suitability of a we...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com