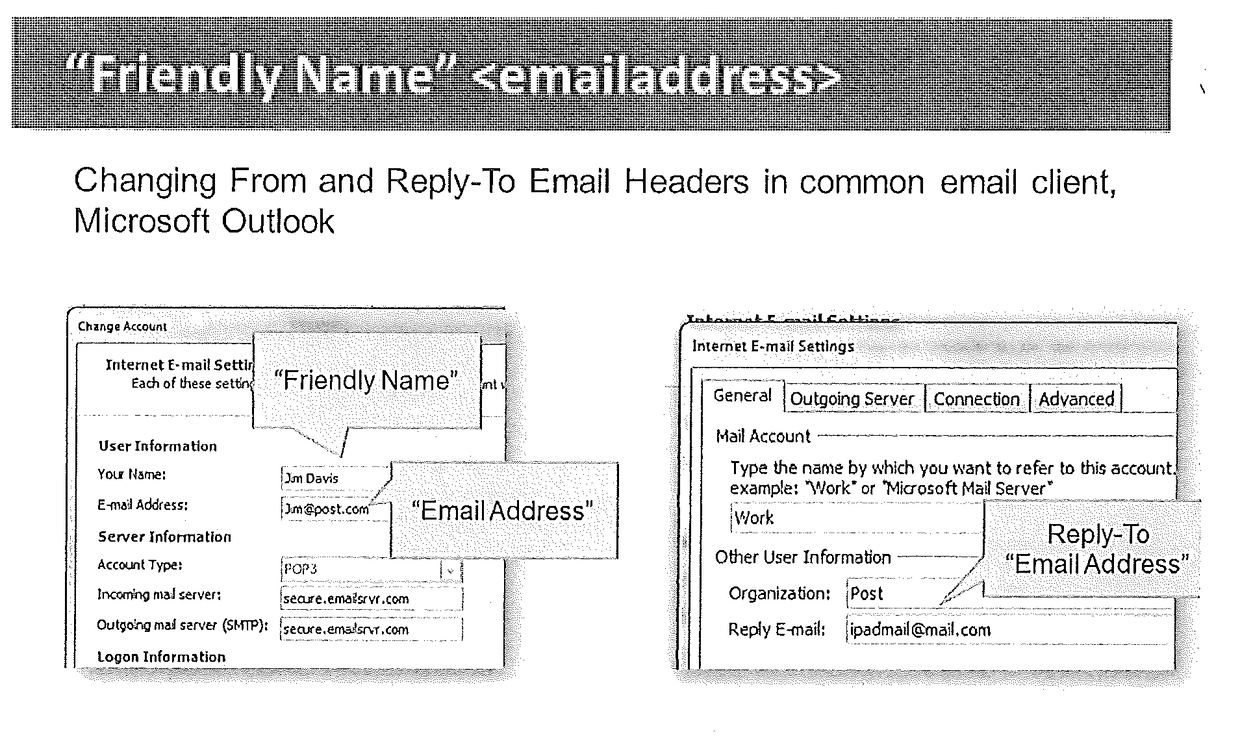
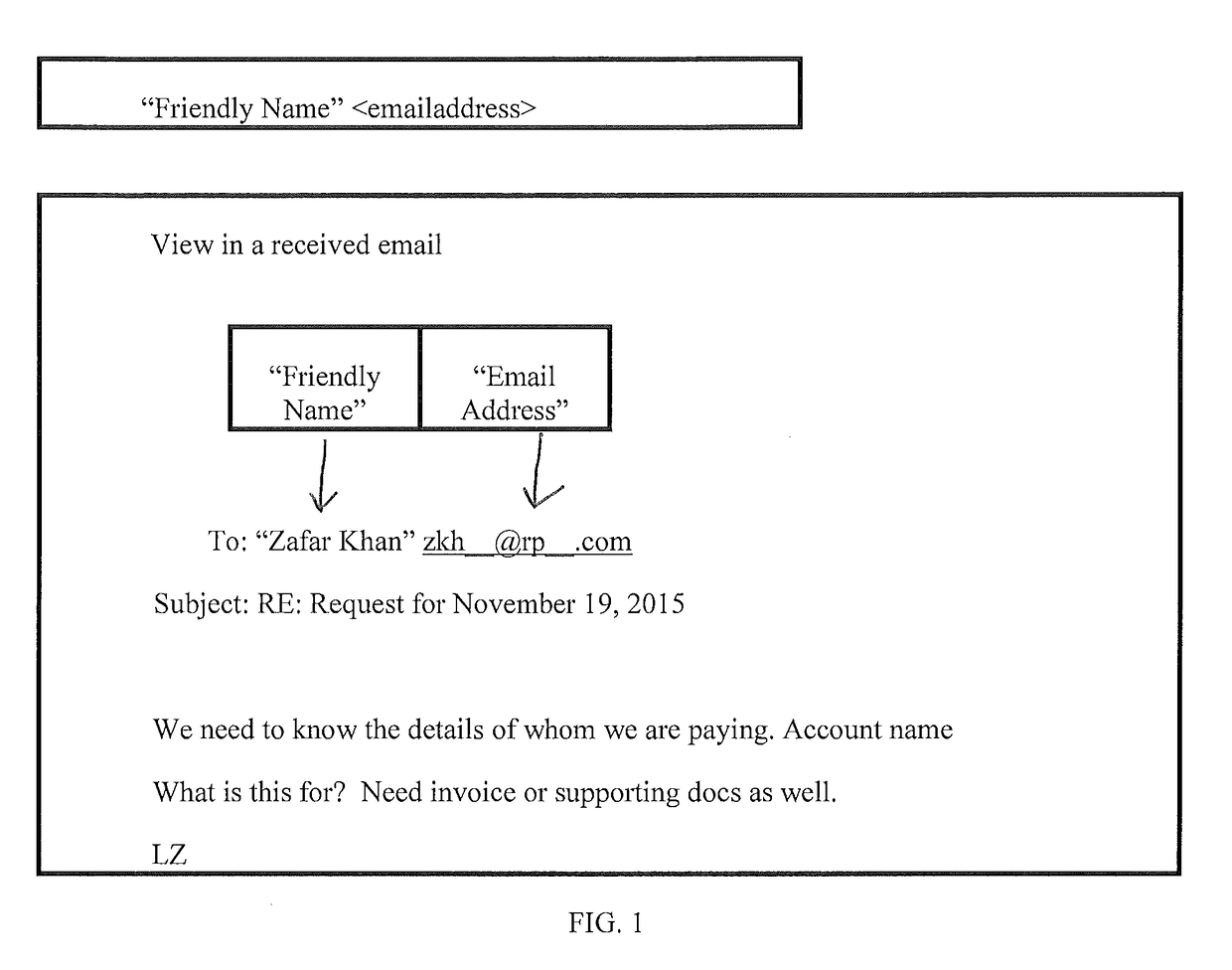
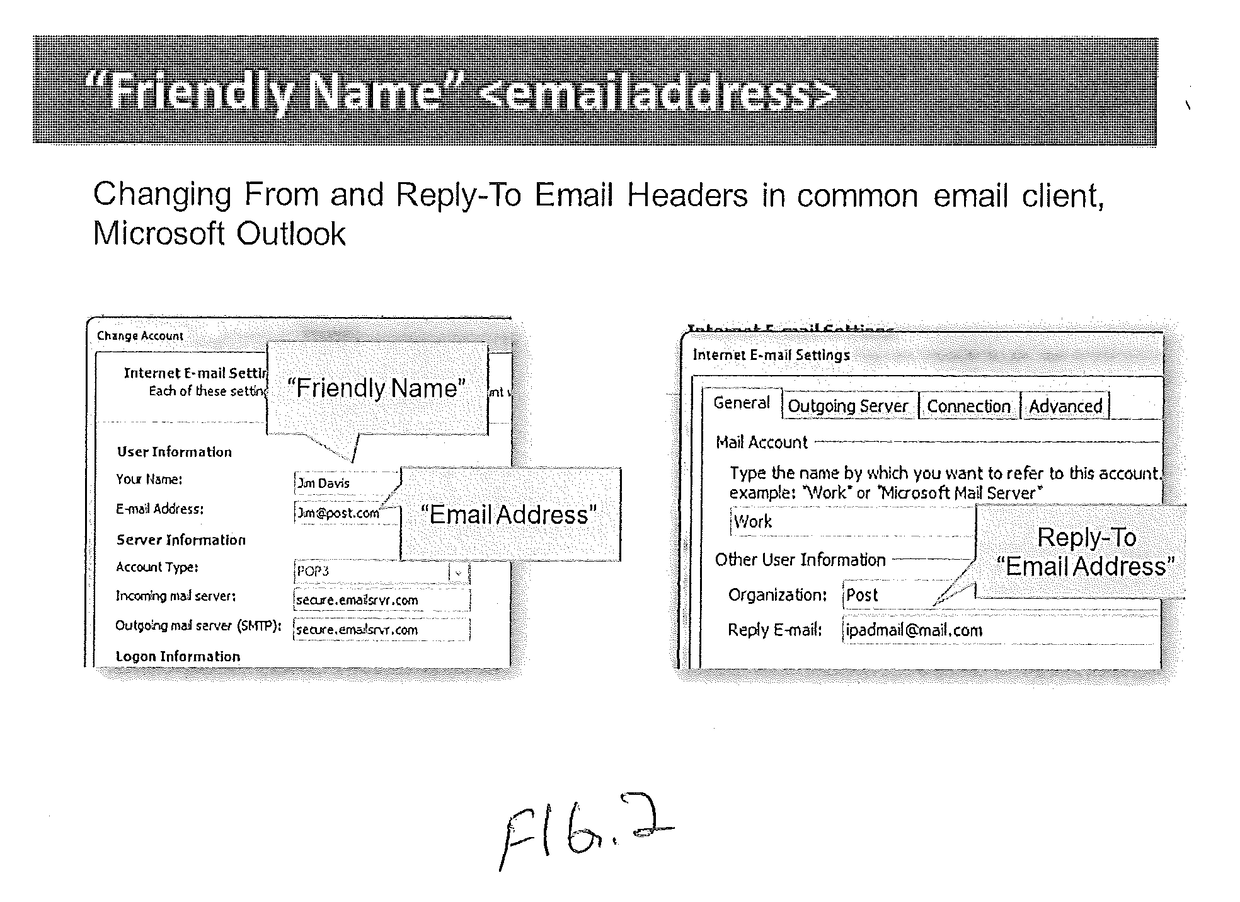
Email Sender and Reply-To Authentication to Prevent Interception of Email Replies
a technology for replying and email senders, applied in the field of electronic messaging security, can solve the problems of social media social media, easy to miss whaling attacks, and difficult to detect standard phishing attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
second embodiment
[0176]FIG. 6 is a flow chart illustrating the processes carried out by the invention. In this embodiment, the recipient desires a higher level of risk mitigation to avoid responding to a fraudulent received email message.
[0177]In this embodiment, the fraudulent email arrives in the target recipient's email inbox of the recipient's email client in box 100. If the target recipient opens the email and then clicks on the Reply or Reply-All buttons of the email client in box 102, the command to compose a reply message is intercepted by the programming commands of the first embodiment of the invention, and they analyzed to determine if the Reply-To email header field of the message contains an email address in box 104. If the Reply-To email header field does not contain an email address, the programming commands of the second embodiment of the invention terminate and the email client displays a typical reply email message format to the recipient, and then continues with normal electronic ...
third embodiment
[0182]Where the user wants a higher level of risk mitigation automated with actions taken before the sent message from the Internet criminal reaches that target recipient, software embodying the invention may be installed on a server separate from the sender that receives email before reaching the target recipient email box.
[0183]FIG. 7 is a graphic representation of email flow in the case where an email appears to come from an authentic sender, but in actuality comes from an Internet Criminal. Here, an email is sent from the Internet Criminal with Authentic Sender “From” information, and with the Internet Criminal's “Reply-To” information to a target recipient in box 130. The email is intercepted by a server that is located remote from the sender's email client in box 132. The server, operated by programming commands embodying the third embodiment of the invention, analyzes the header information of the email at box 134. If the server determines that the email is not fraudulent, th...
fourth embodiment
[0189]FIG. 9 is a flow chart illustrating an the various methods, processes, and logic carried out by the invention. As stated previously, these methods, processes, and logic are embodiment in software and hardware that runs on a recipient's email client.
[0190]In the fourth embodiment, the fraudulent email arrives in the target recipient's email inbox of the recipient's email client in box 160. If the target recipient opens the email and then clicks on the Reply or Reply-All buttons of the email client in box 162, the command to compose a reply message is intercepted by the programming commands of the first embodiment of the invention, and they analyzed to determine if the Reply-To email header field of the message contains an email address in box 164. If the Reply-To email header field does not contain an email address, the programming commands of the fourth embodiment of the invention terminate and the email client displays a typical reply email message format to the recipient, an...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com