Secure firmware updates for remote vehicles
a technology for remote vehicles and secure firmware updates, applied in the direction of securing communication, digital transmission, instruments, etc., can solve the problems of difficult to efficiently securely transfer firmware update files without expensive or hard-to-scale infrastructure, etc., to improve the functionality of digital hardware components and efficiently securely transfer firmware update files.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0015]Following below are more detailed descriptions of various concepts related to, and implementations of, methods, apparatuses, and systems of network-based path generation for a vehicle controller. The various concepts introduced above and discussed in greater detail below may be implemented in any of numerous ways.
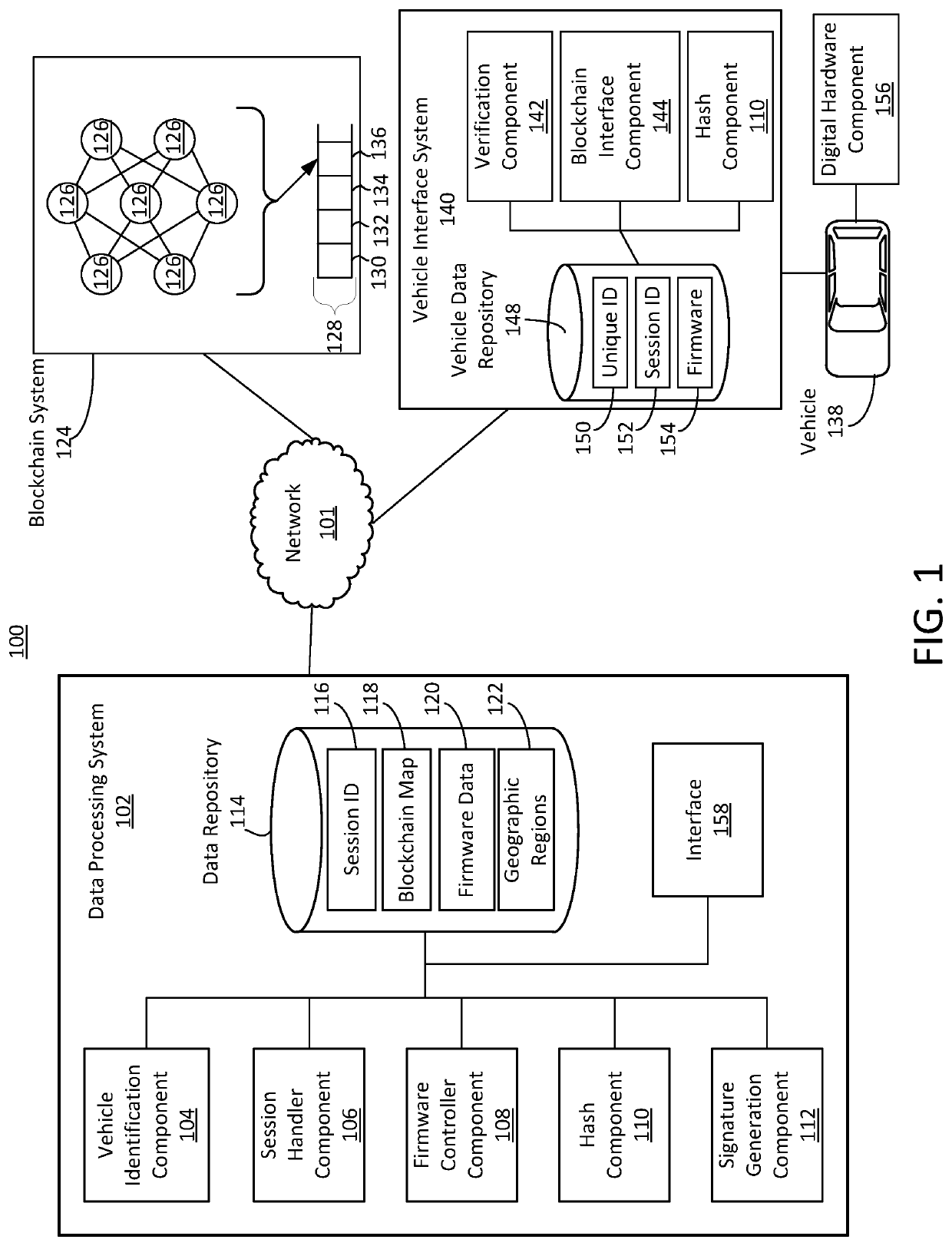
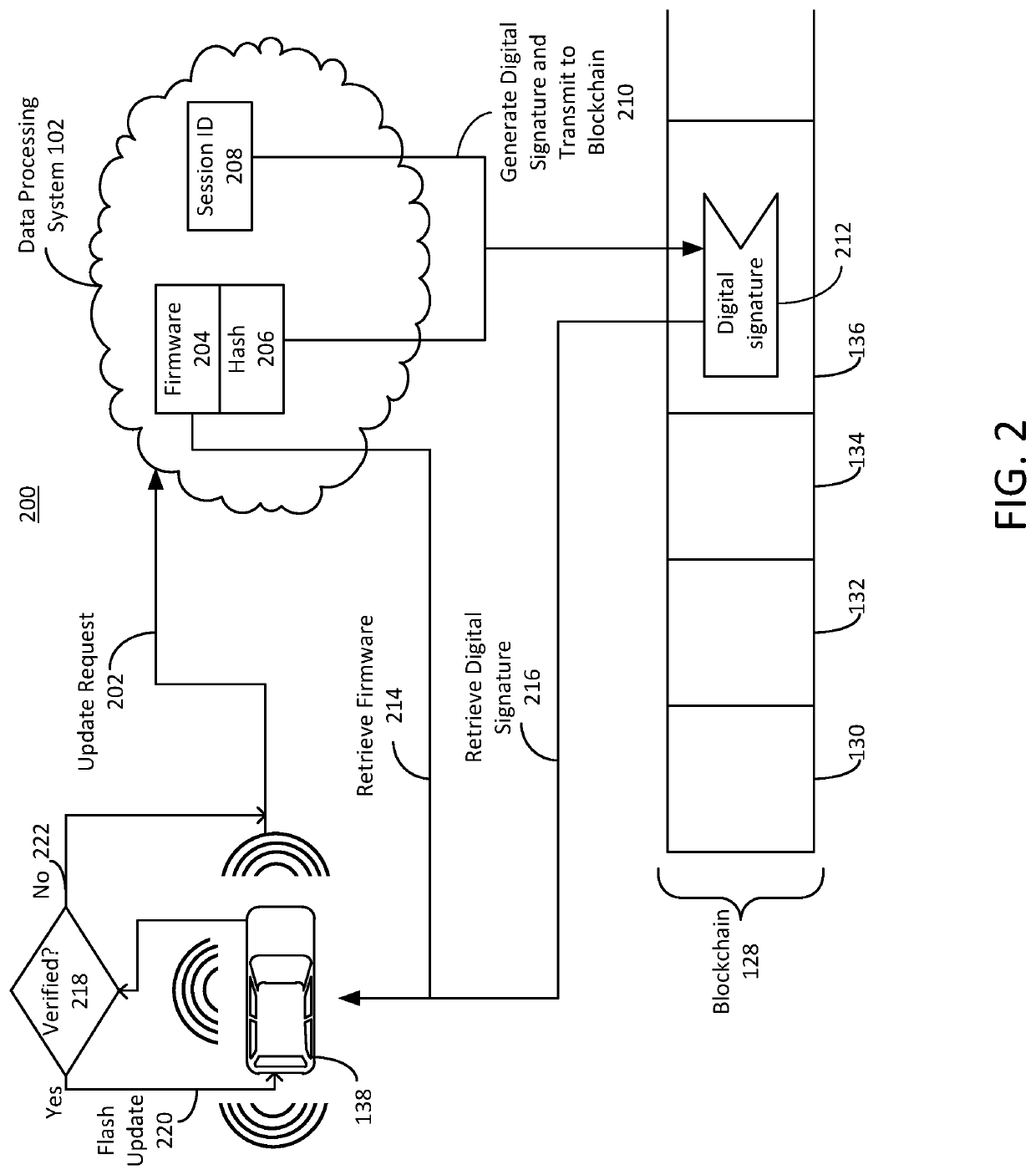
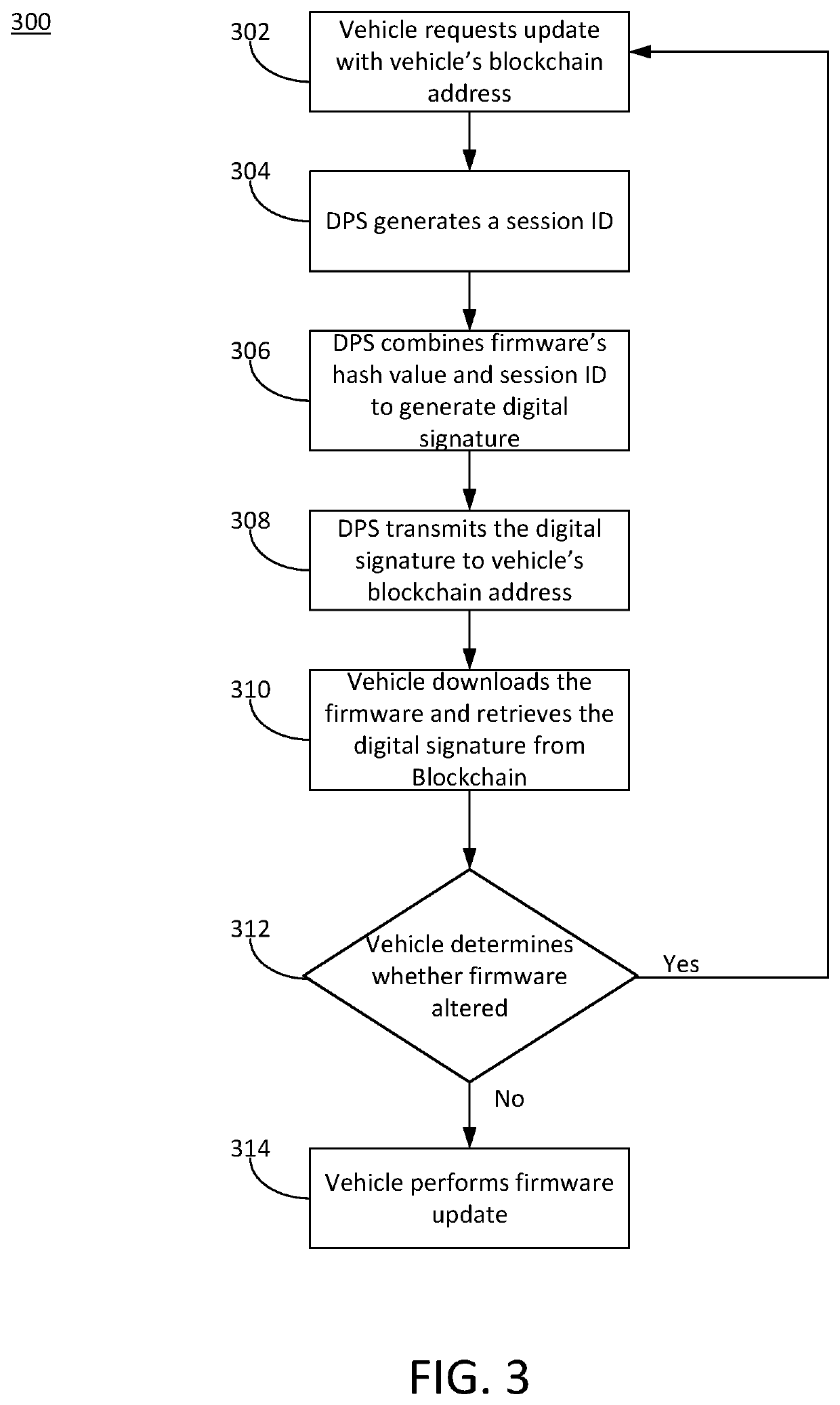
[0016]The present disclosure is directed to systems and methods of secure firmware updates for remote vehicles. Vehicles such as automobiles can include numerous digital hardware components that run or execute firmware. The digital hardware components can perform critical functions of the vehicle or be integral to critical vehicle systems. The firmware run by the digital hardware components can be updated periodically to improve the functionality of the digital hardware components. As errors, faults, issues, or improvements are identified for the hardware component, a server can transfer a firmware update for the component. However, due to the vehicle being remote fro...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com