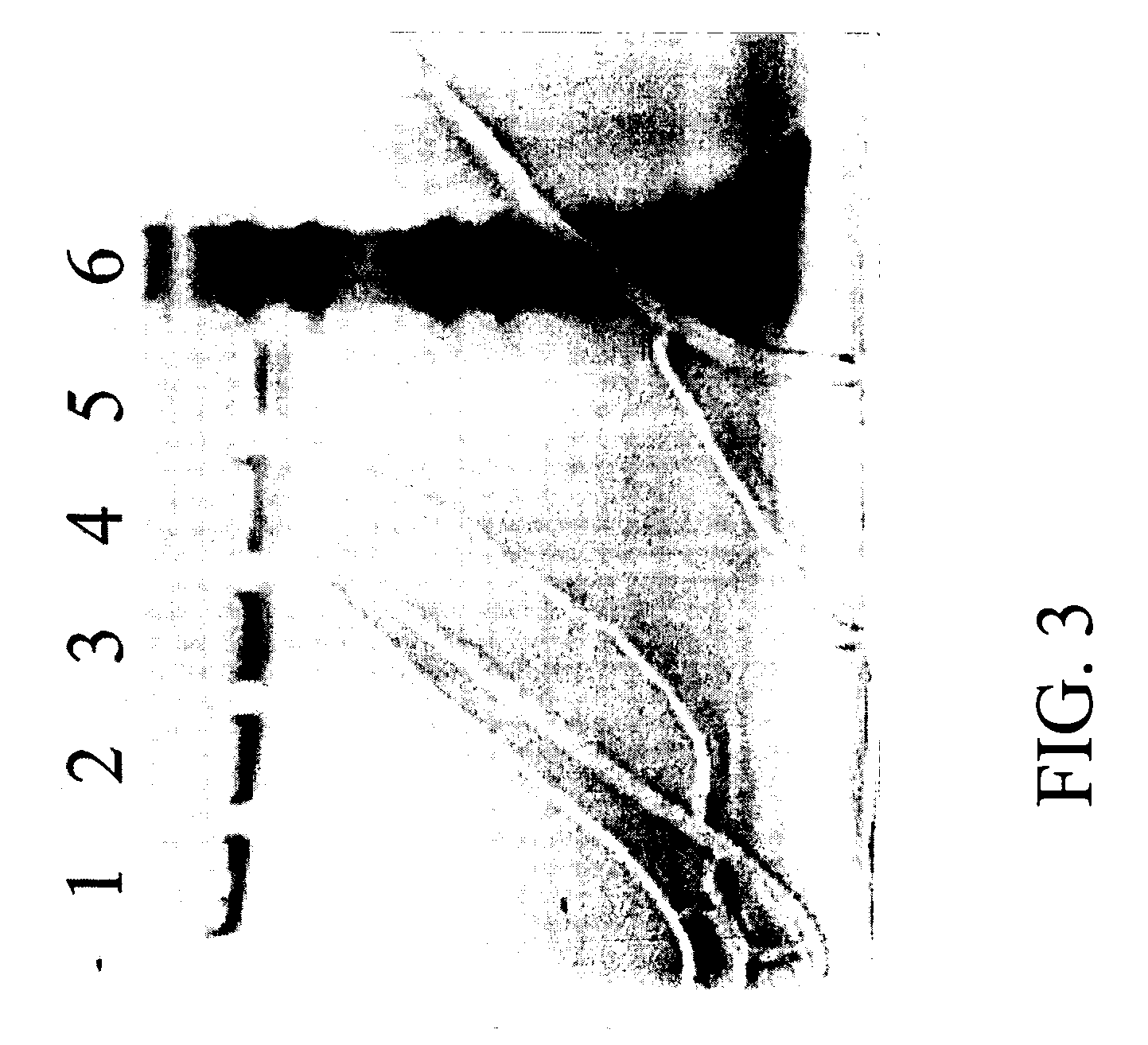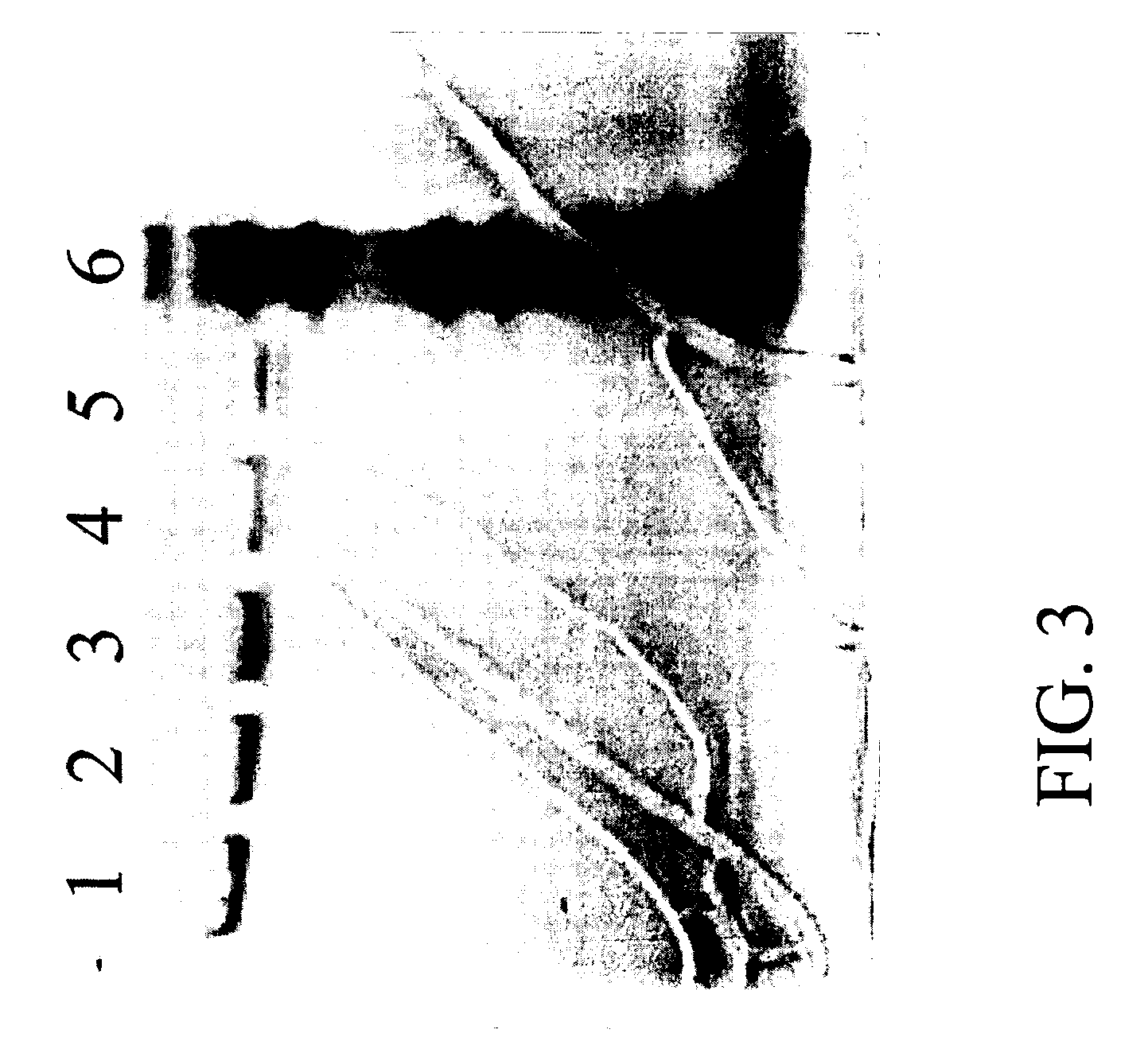Patents
Literature
37results about How to "Efficient and scalable" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
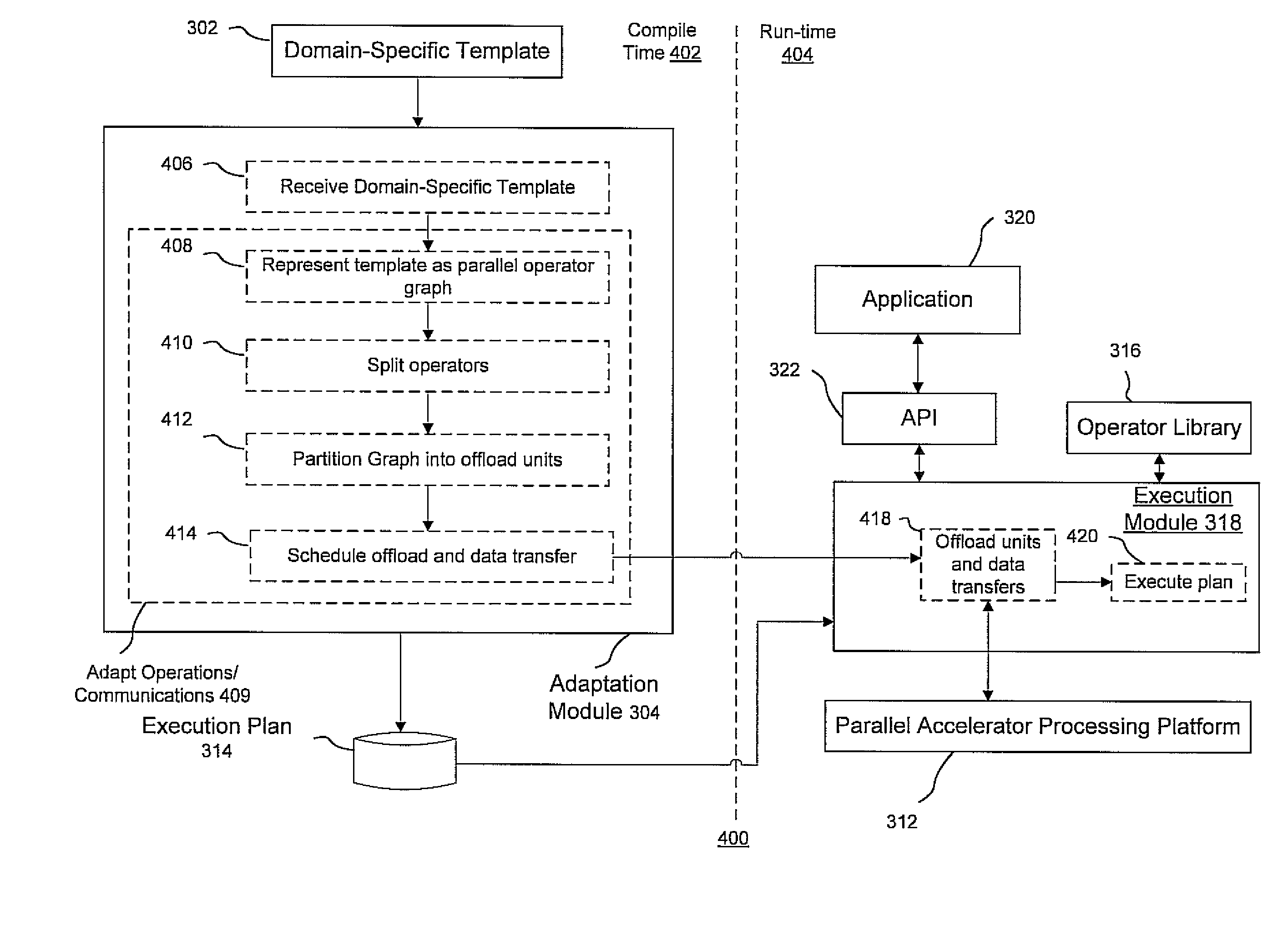
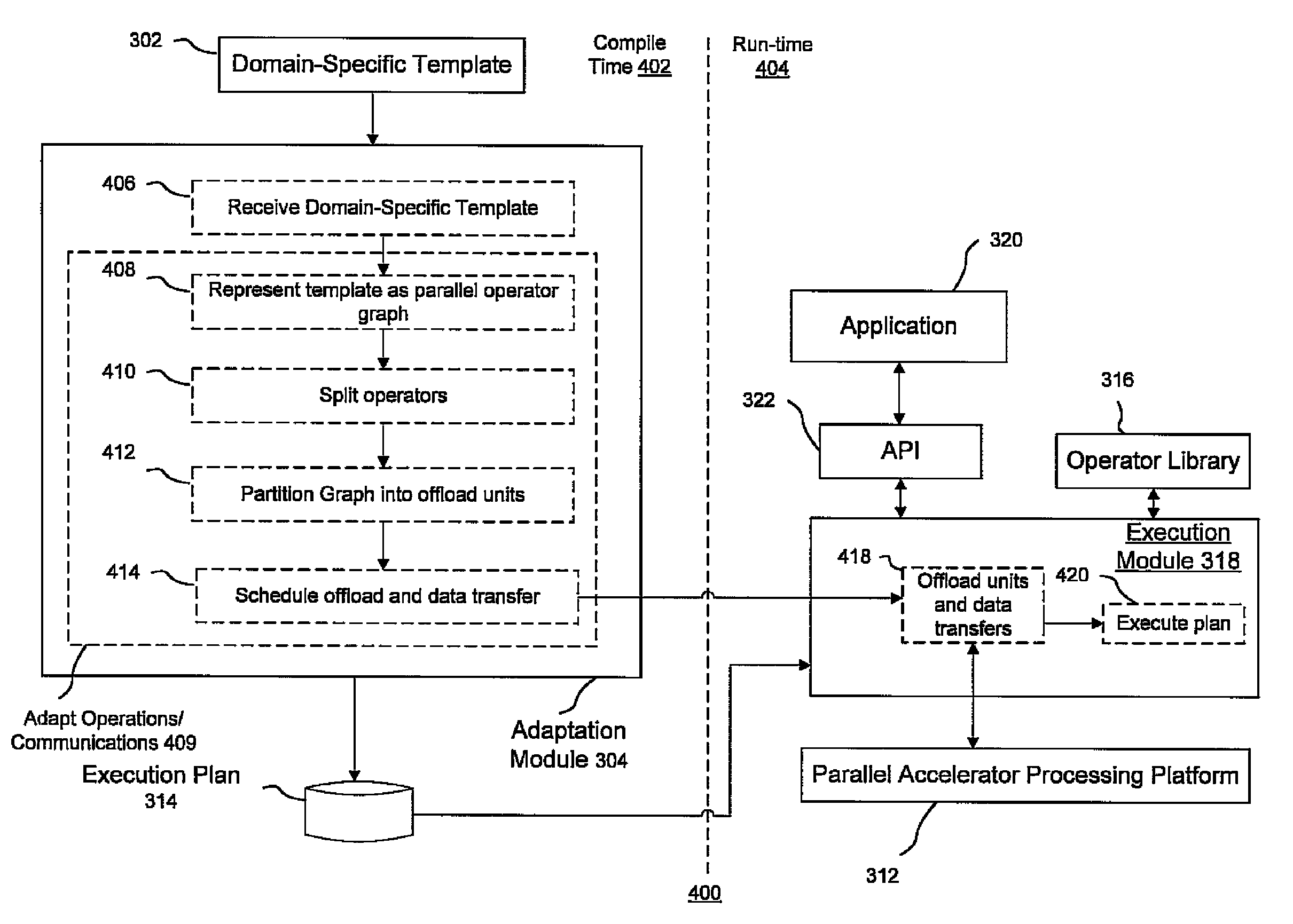
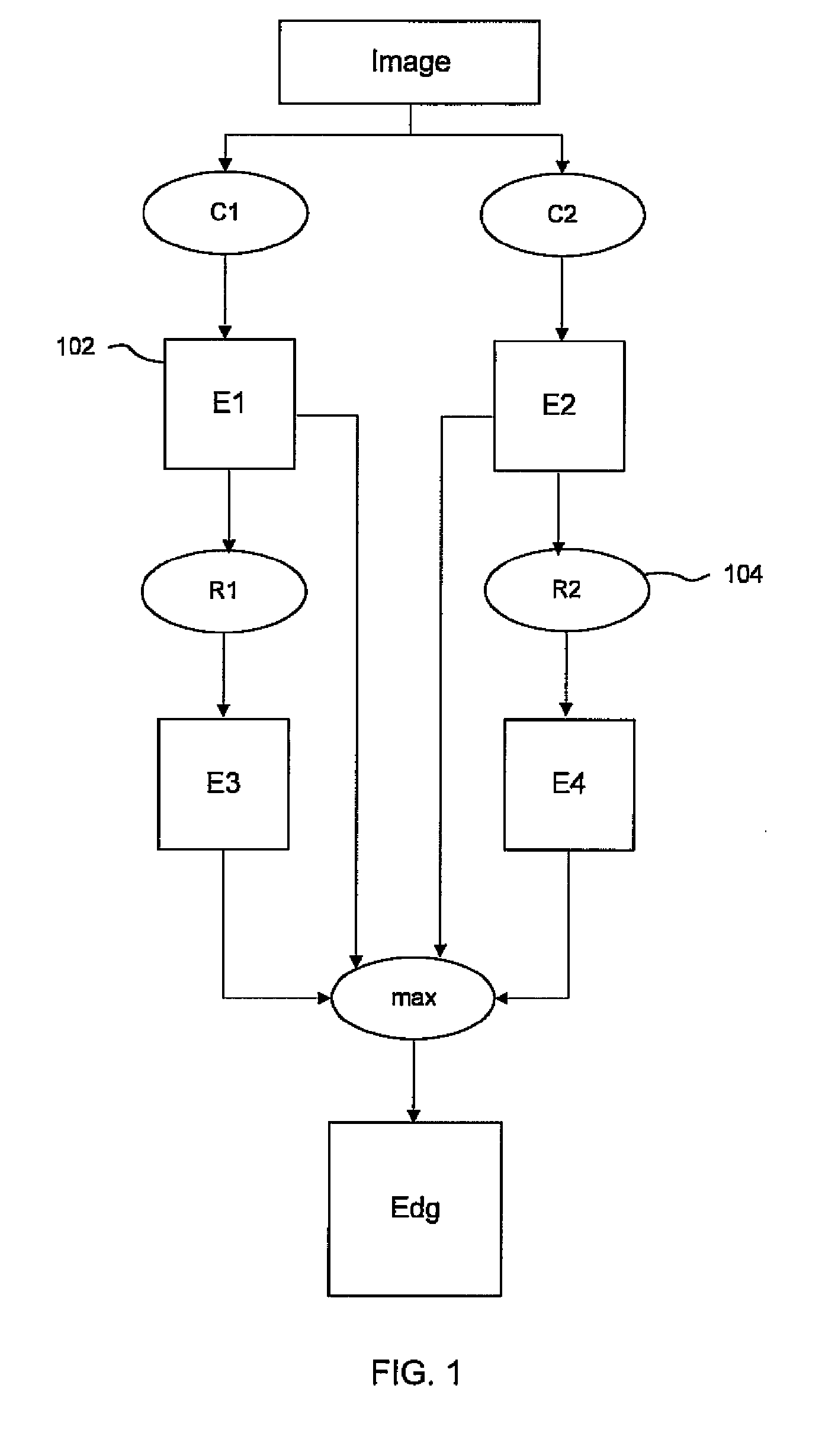
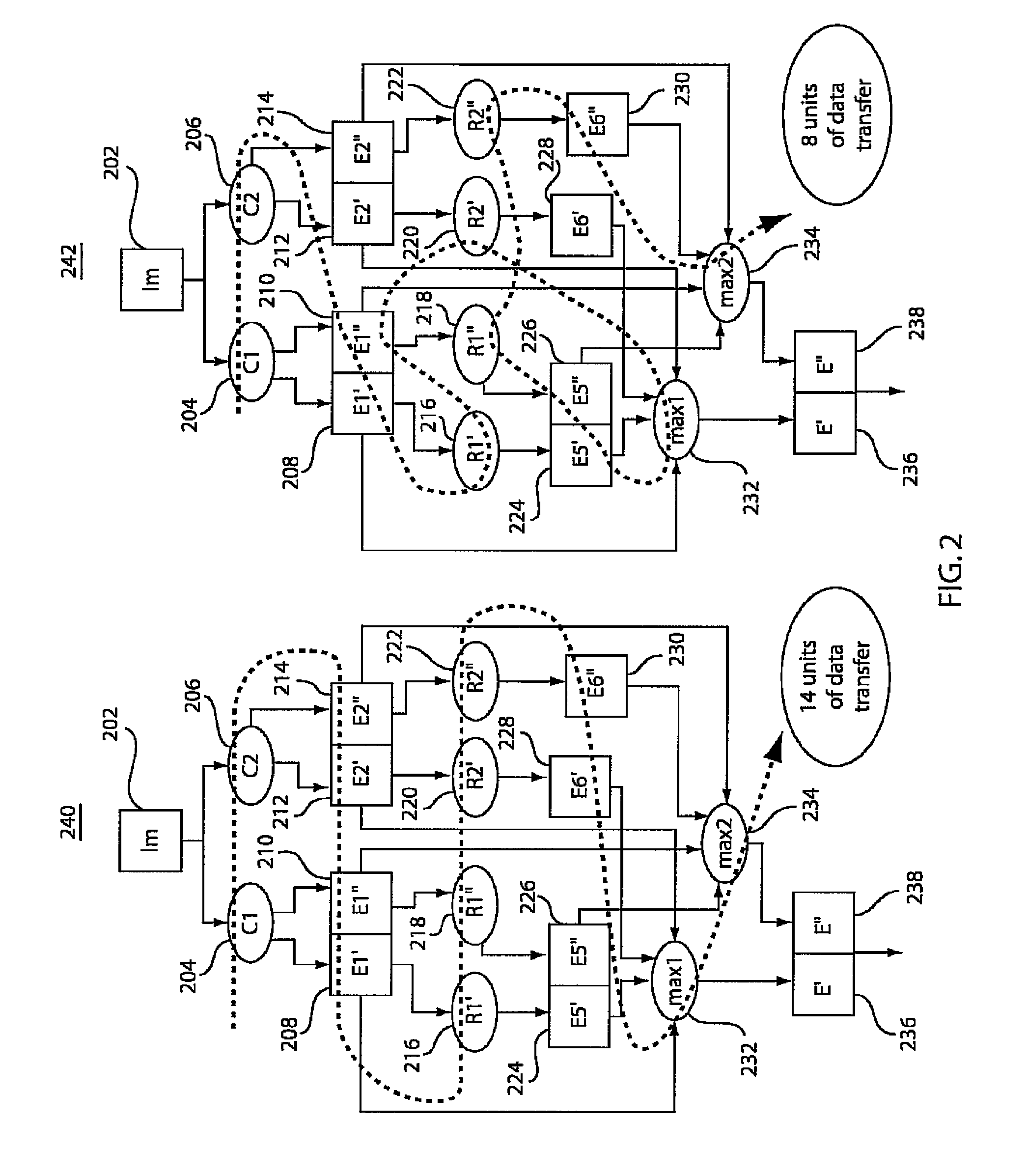
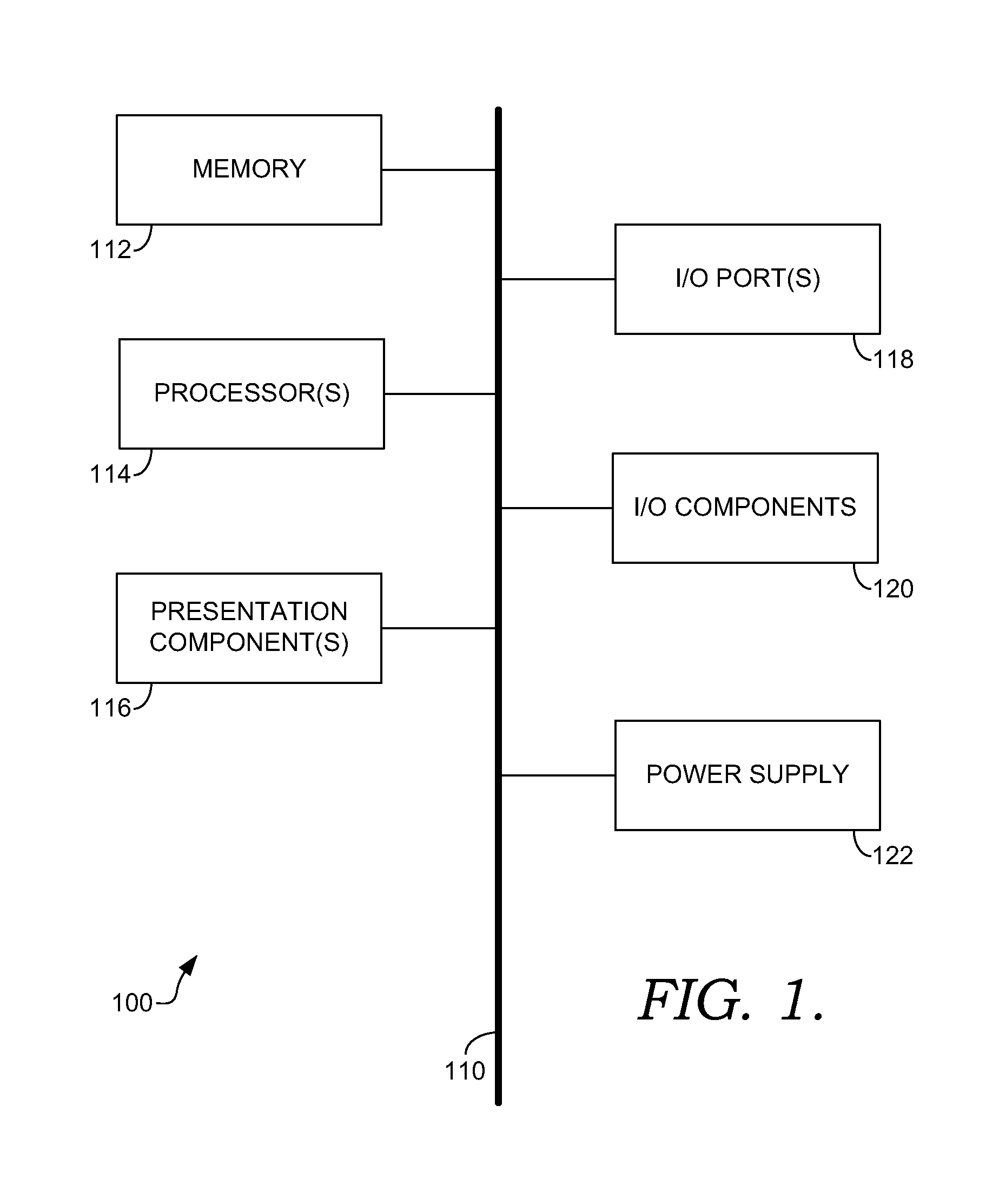
Methods and systems for managing computations on a hybrid computing platform including a parallel accelerator
ActiveUS20100088490A1Improve convenienceEfficient data transferProgram control using stored programsGeneral purpose stored program computerParallel computingData transmission
In accordance with exemplary implementations, application computation operations and communications between operations on a host processing platform may be adapted to conform to the memory capacity of a parallel accelerator. Computation operations may be split and scheduled such that the computation operations fit within the memory capacity of the accelerator. Further, the operations may be automatically adapted without any modification to the code of an application. In addition, data transfers between a host processing platform and the parallel accelerator may be minimized in accordance with exemplary aspects of the present principles to improve processing performance.
Owner:NEC CORP
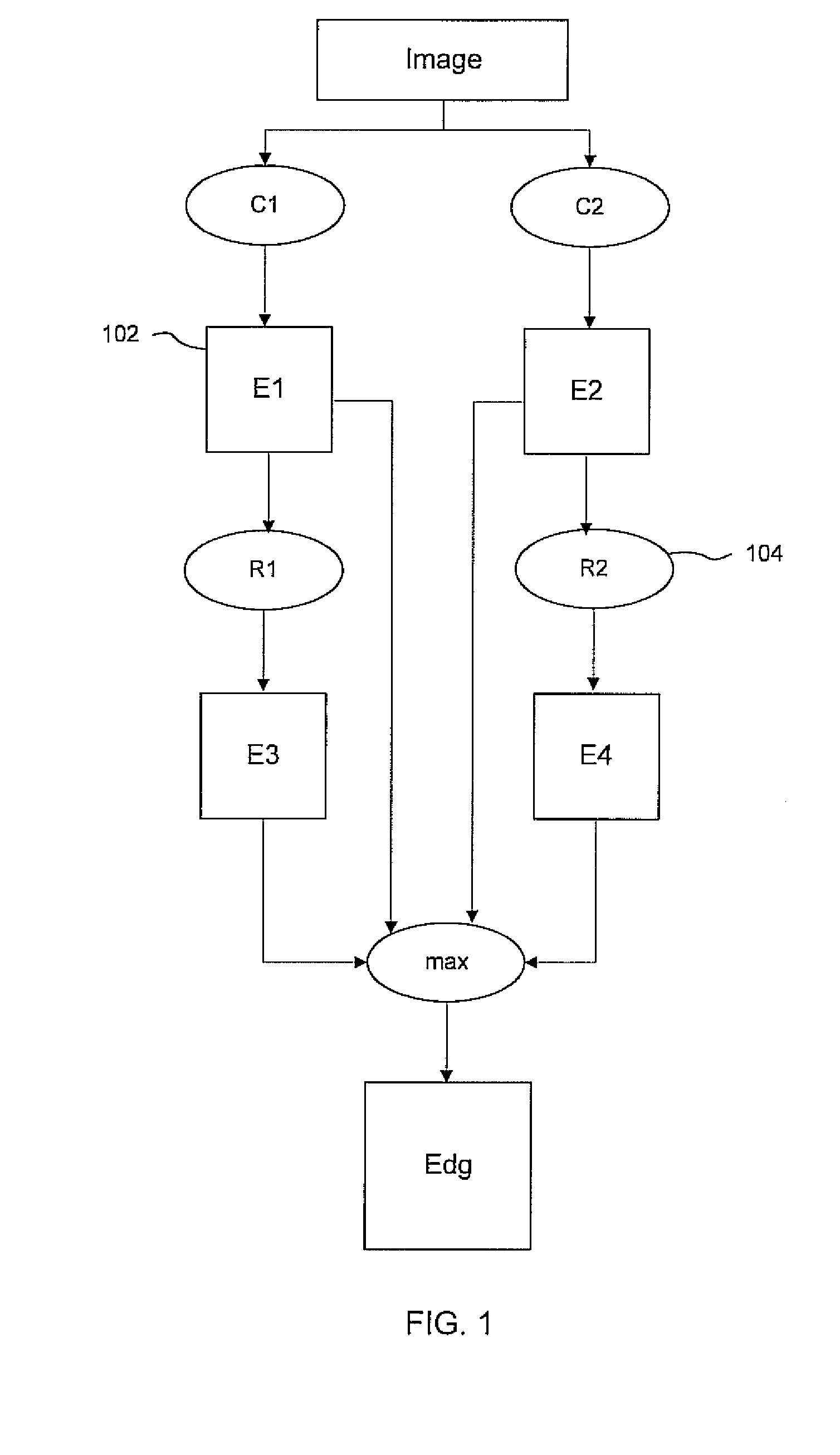
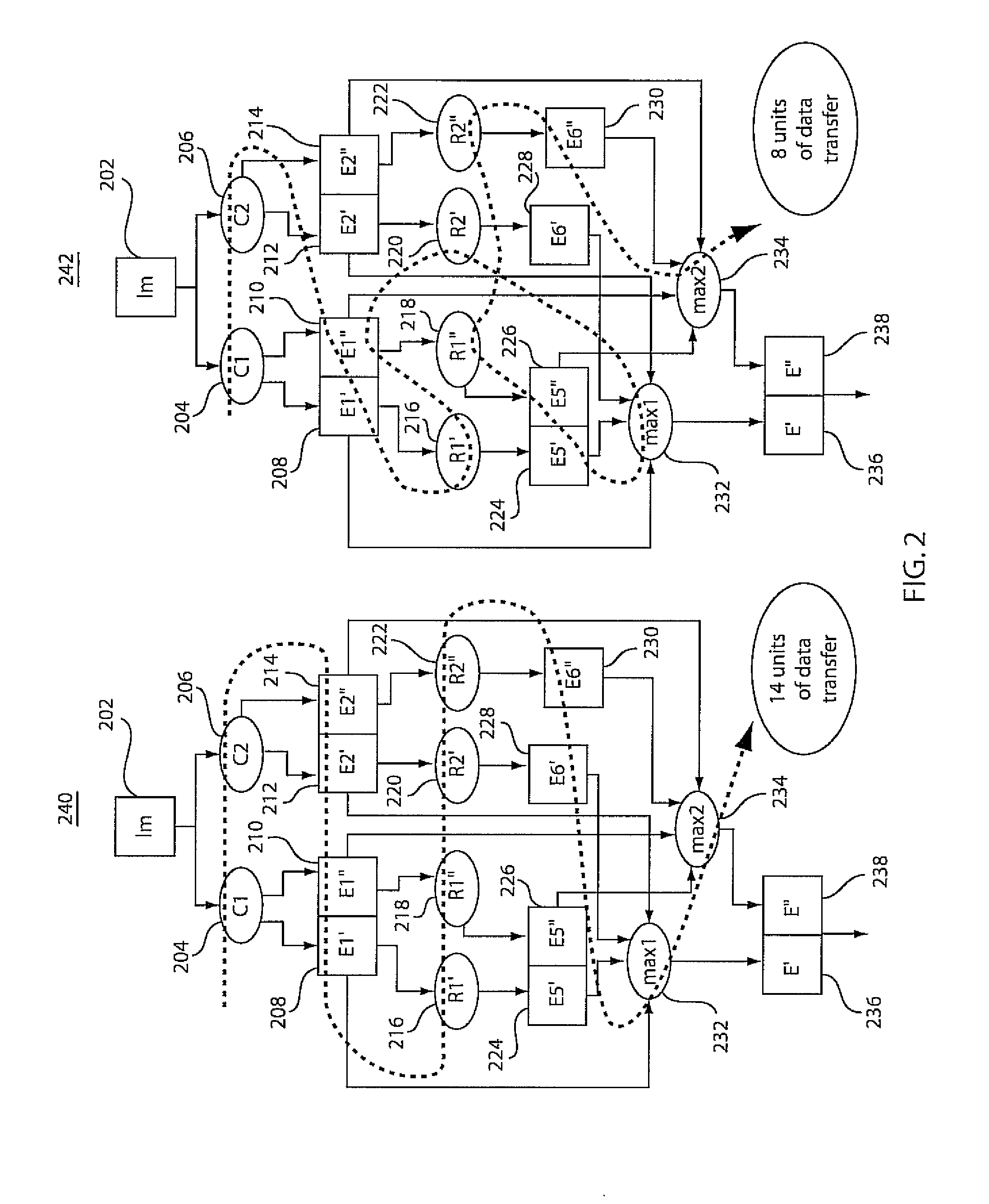
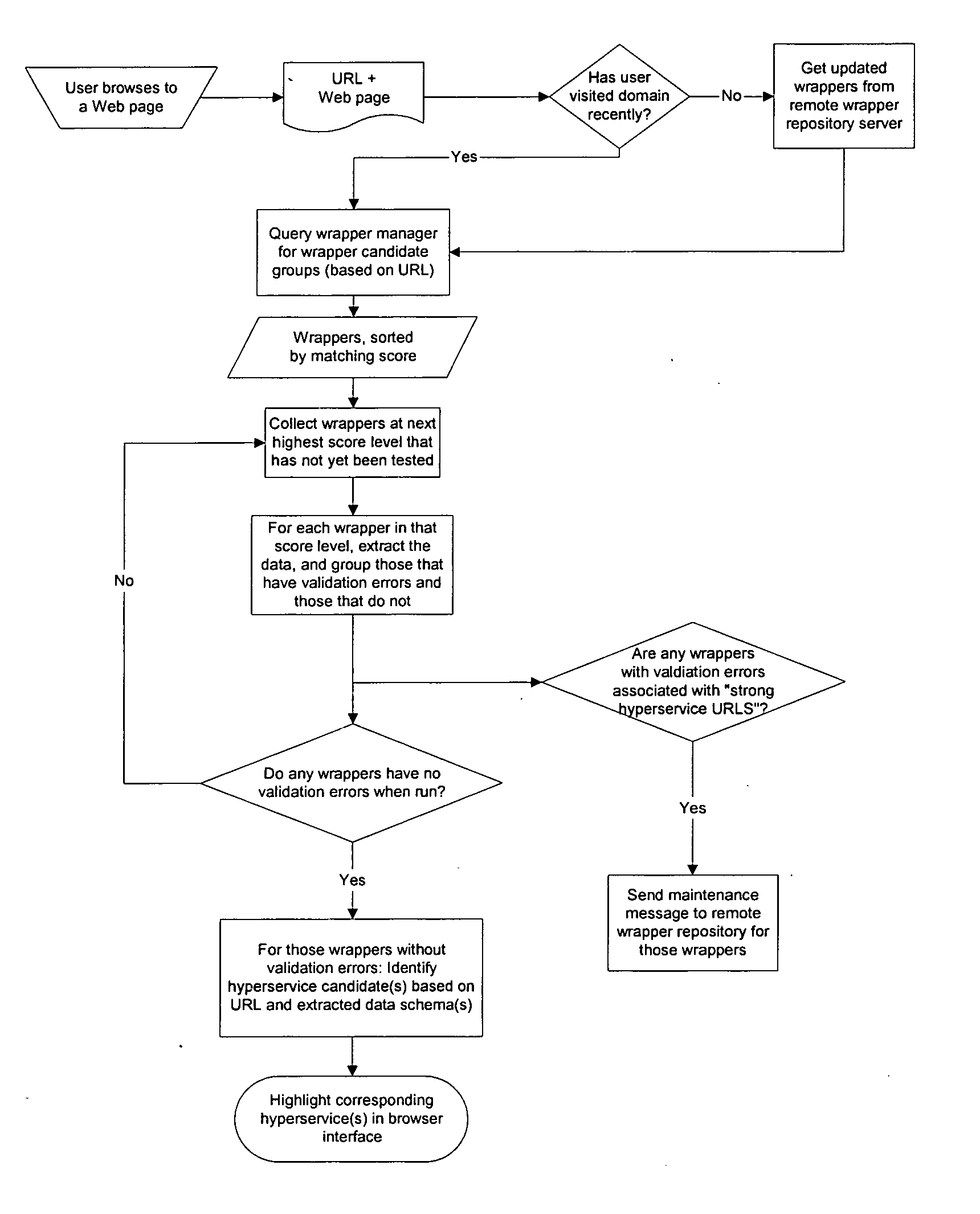
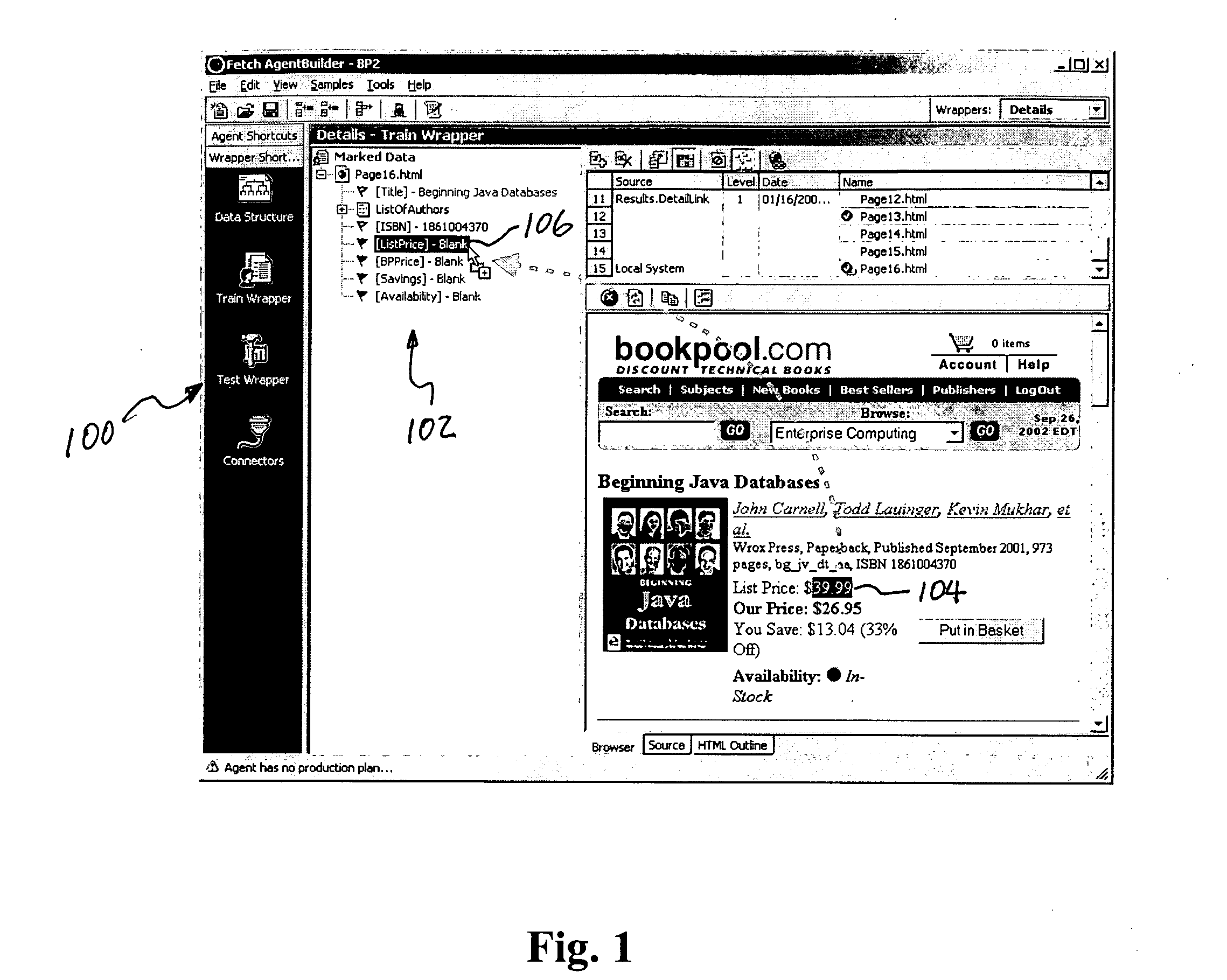
Client-centric information extraction system for an information network
InactiveUS20050165789A1Improves “ intelligence ”Efficient and scalableDigital data processing detailsWebsite content managementThe InternetInformation networks
A client-centric online navigation architecture that extracts relevant data from documents as a user is interacting with an information network, proposes related information services based on the types of data and data values extracted from the current viewed document, and presents a menu of related information. A browser plug-in extracts data from a web page as a user browses the Internet, and provides additional services to the web user as he browses. Data extraction wrappers created by a developer are distributed to the client machines. The wrapper supported information extraction process occurs apart from the content server, e.g., on the client machine or a proxy server. Extracted data can trigger the launching of services, called “hyperservices”, either on the local machine or remote machines.
Owner:FETCH TECH
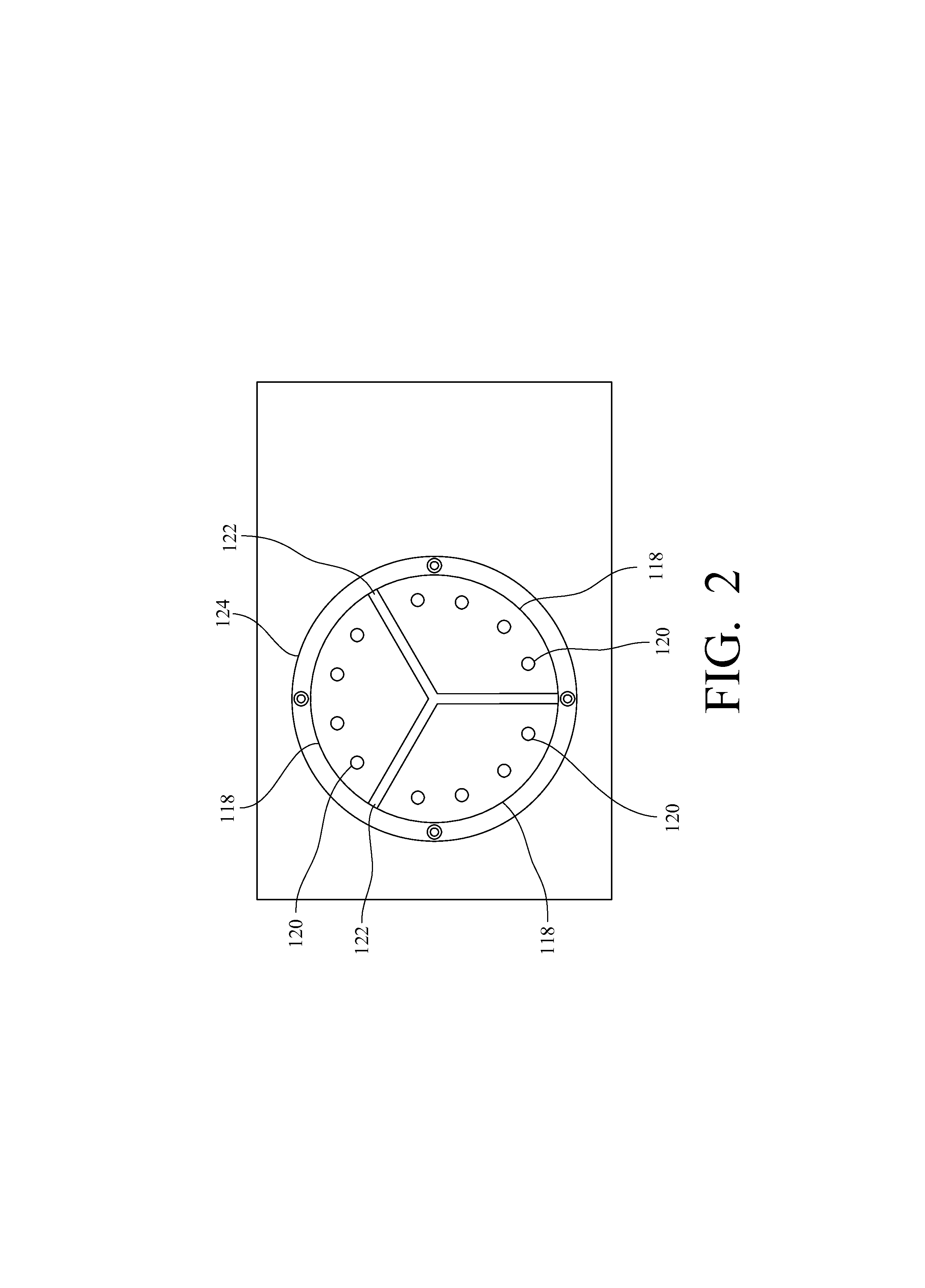
Apparatus and method for a continuous rapid thermal cycle system
ActiveUS20090325234A1Easy to adaptLow production costBioreactor/fermenter combinationsHeating or cooling apparatusTemperature controlChiller
A thermal cycle system and method suitable for mass production of DNA comprising a temperature control body having at least two sectors. Each sector has at least one heater, cooler, or other means for changing temperature. A path traverses the sectors in a cyclical fashion. In use, a piece of tubing or other means for conveying is placed along the path and a reaction mixture is pumped or otherwise moved along the path such that the reaction mixture is repetitively heated or cooled to varying temperatures as the reaction mixture cyclically traverses the sectors. The reaction mixture thereby reacts to form a product. In particular, polymerase chain reaction reactants may continuously be pumped through the tubing to amplify DNA. The temperature control body is preferably a single aluminum cylinder with a grooved channel circling around its exterior surface, and preferably has wedge-shaped or pie-shaped sectors separated by a thermal barrier.
Owner:MARSHALL UNIV RES
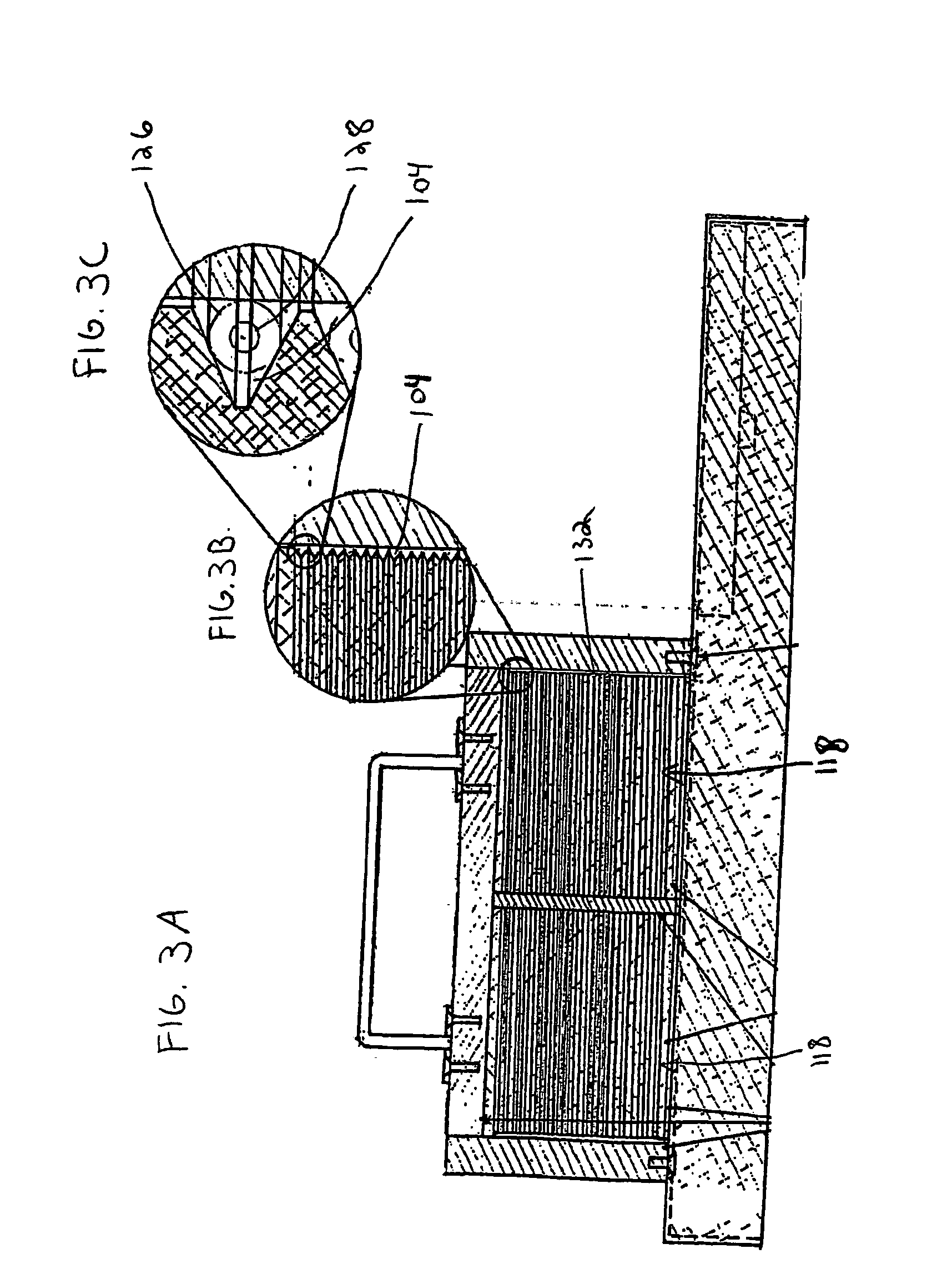
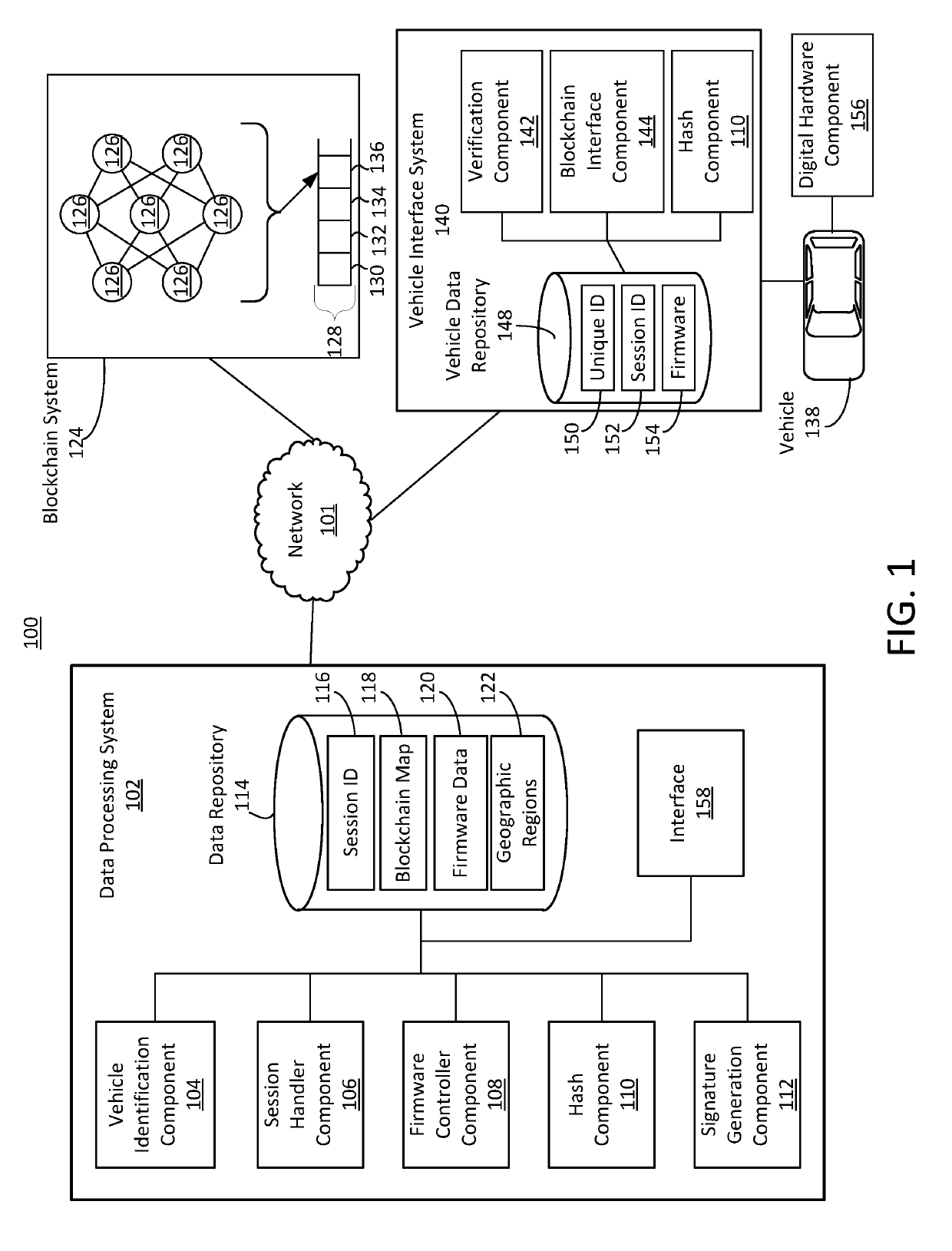
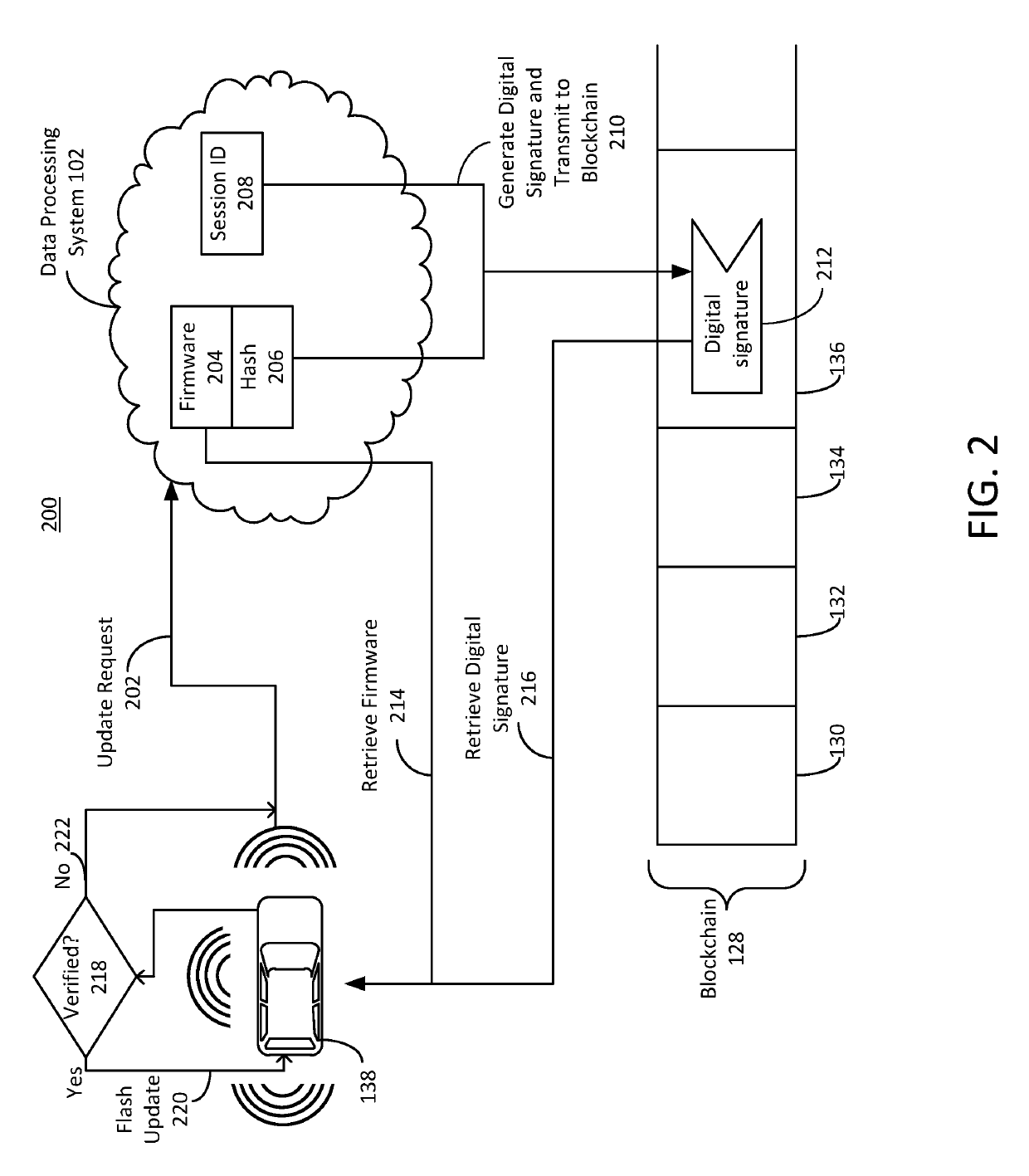
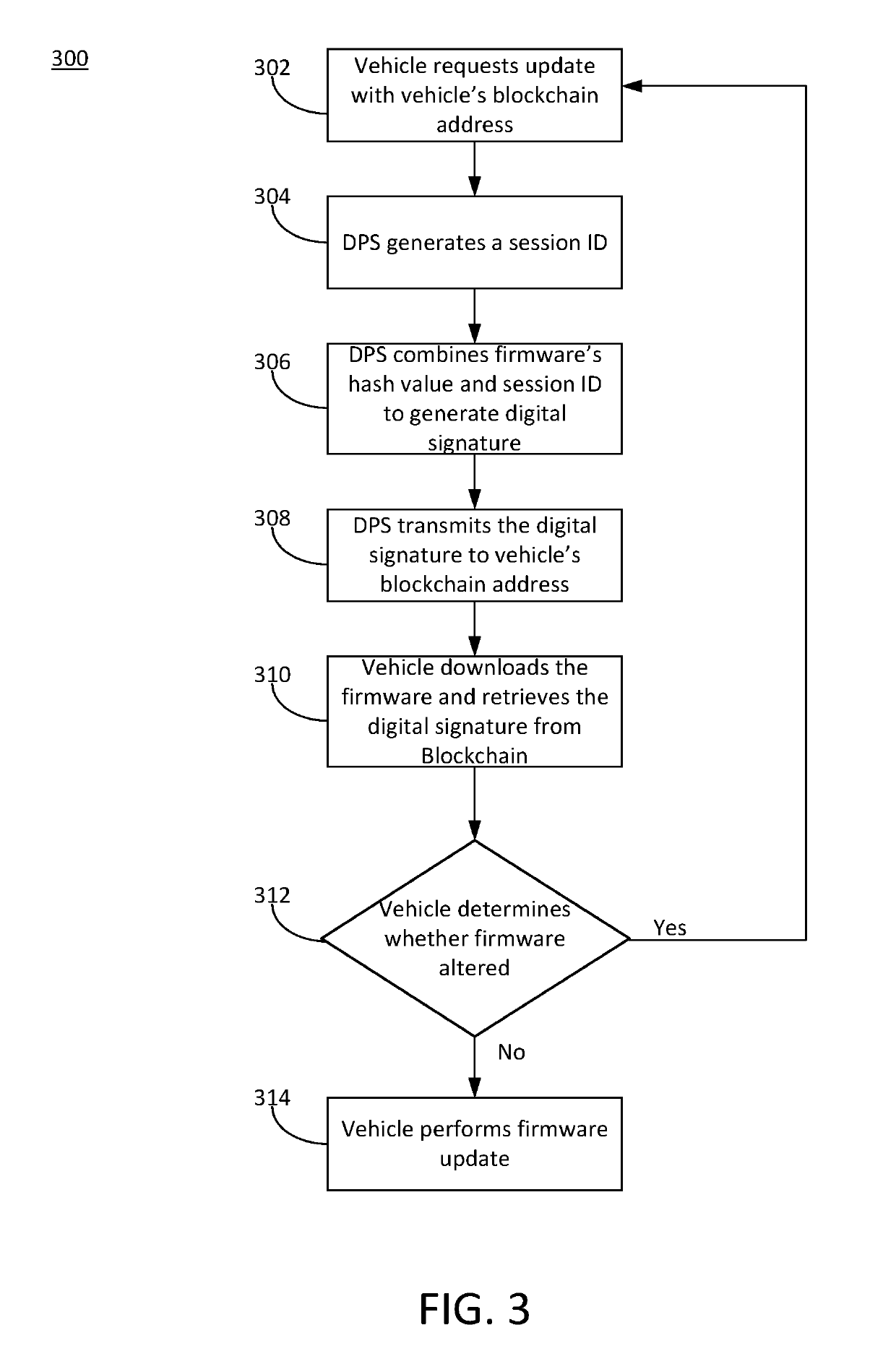
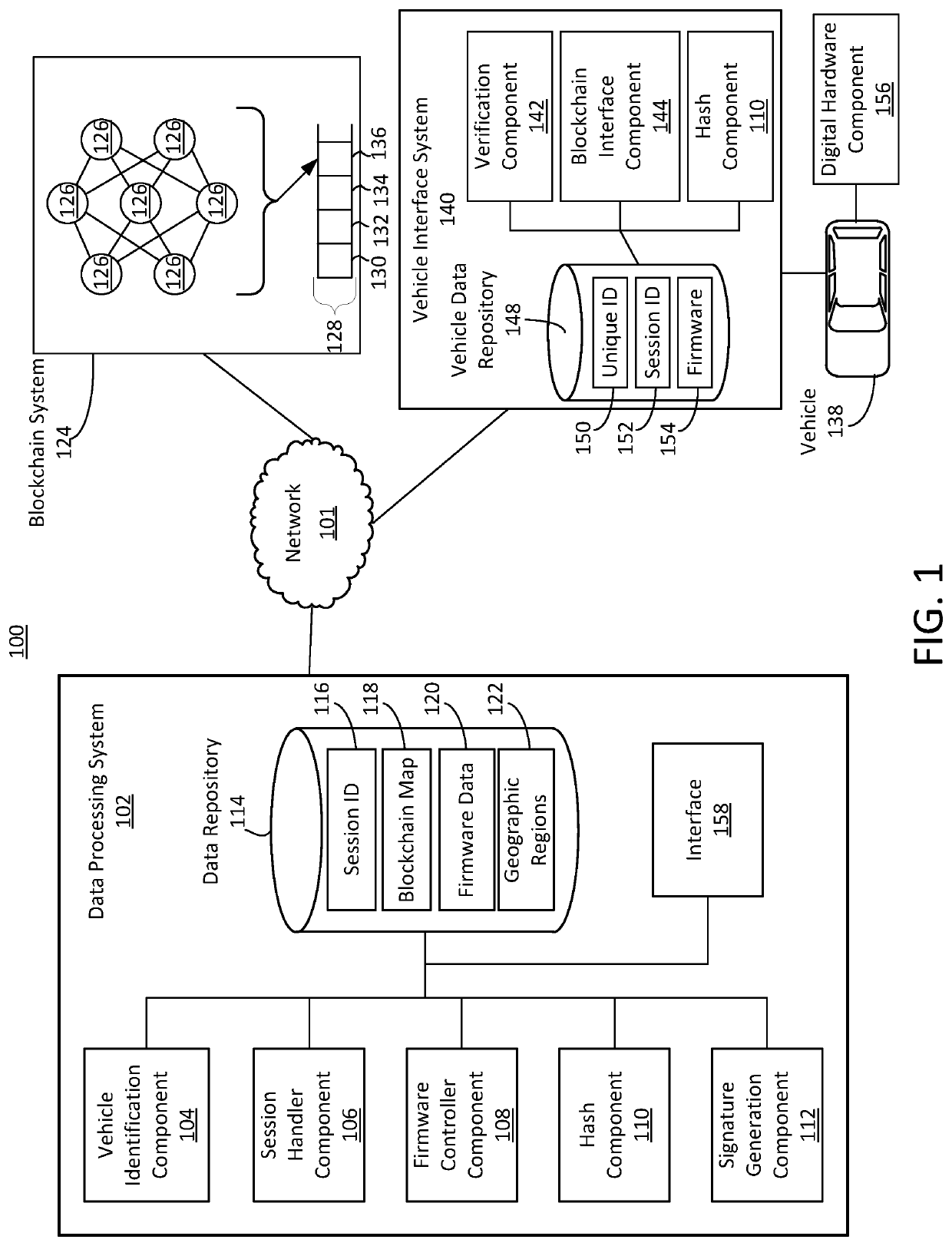
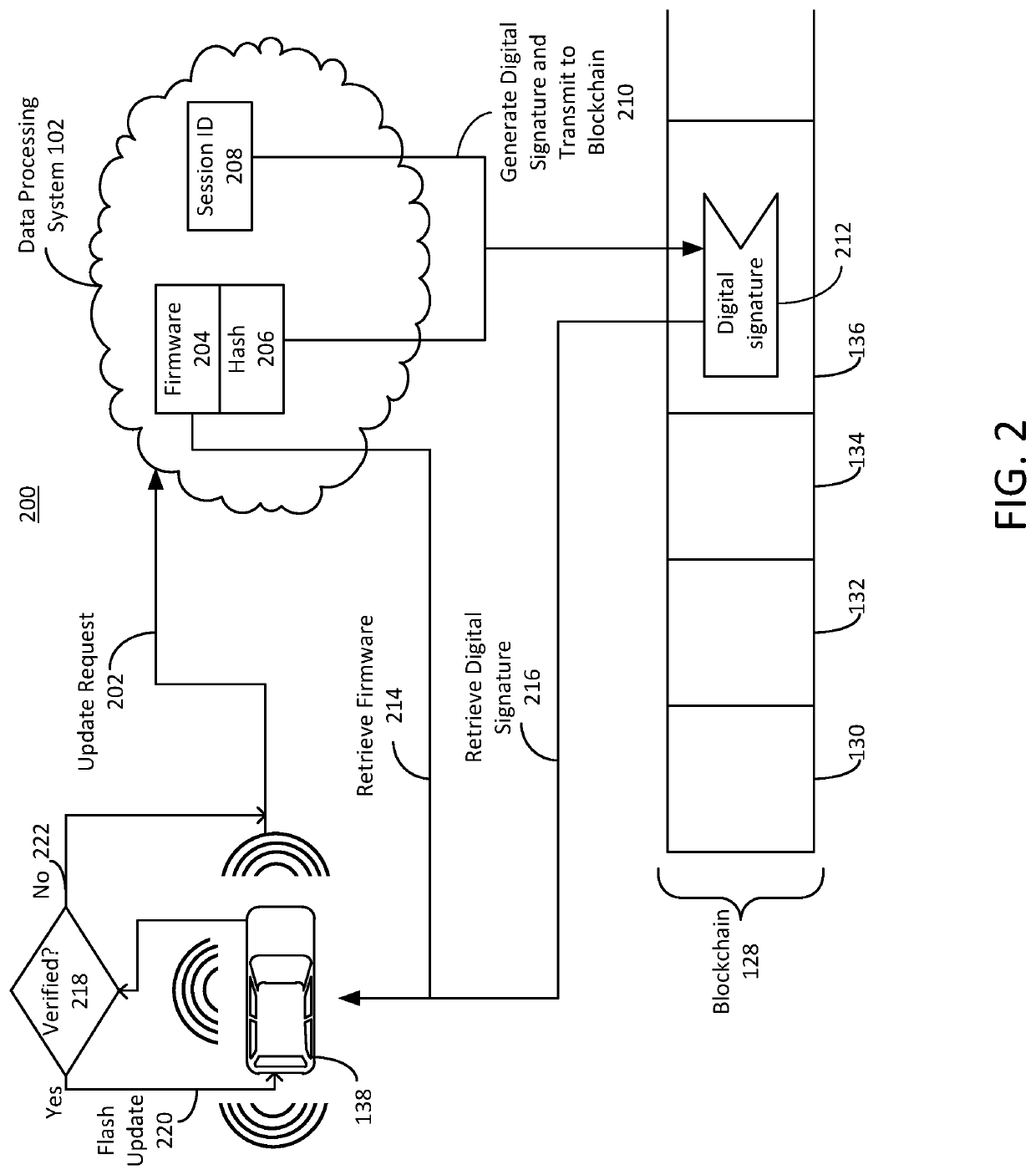
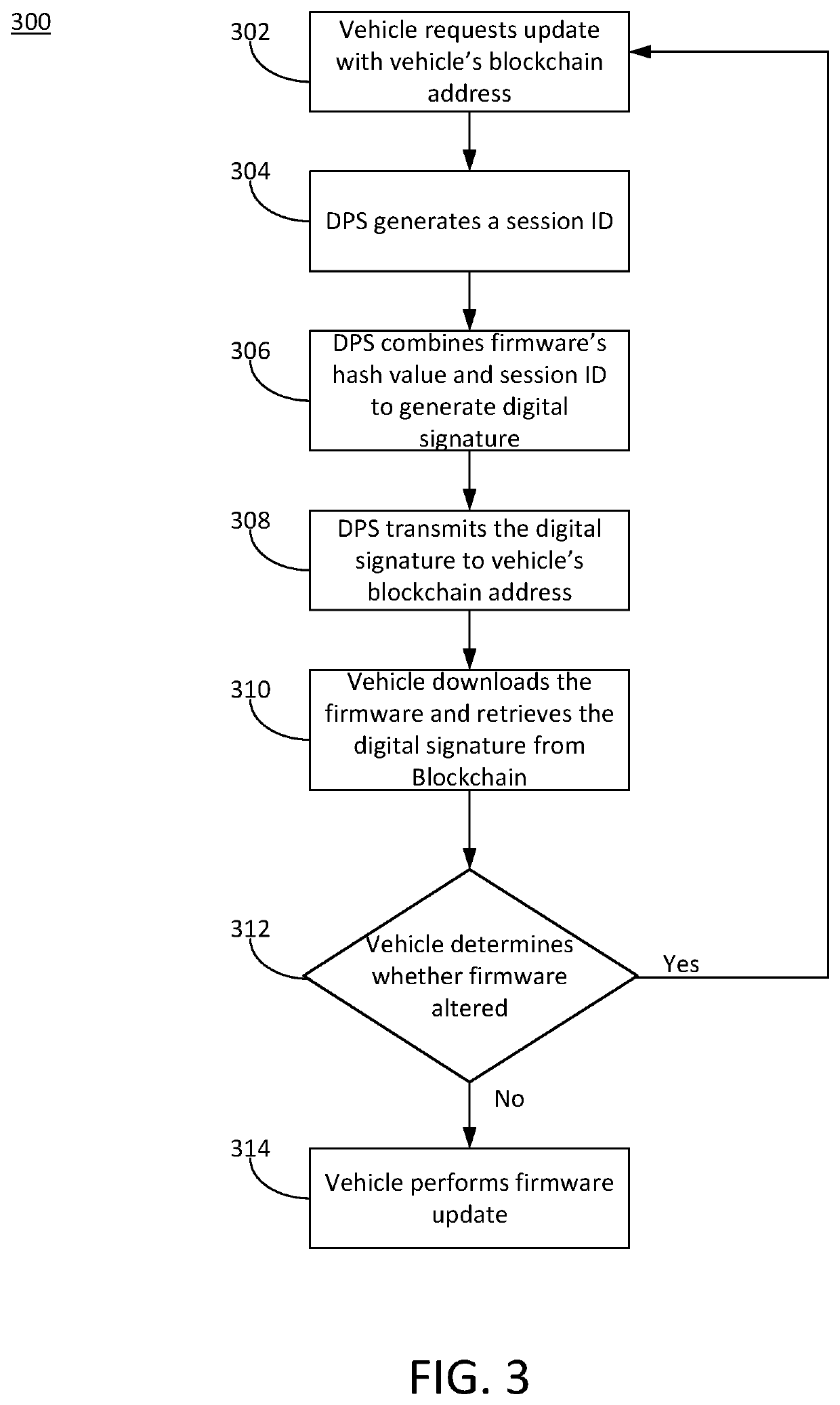
Secure firmware updates for remote vehicles
ActiveUS10447483B1Function increaseEfficiently securely transferEncryption apparatus with shift registers/memoriesUser identity/authority verificationData processing systemDigital signature
Systems and methods of secure firmware updates on remote vehicles are provided. The system receives a request from a vehicle for an update to vehicle firmware, and identifies a blockchain address for the vehicle. The system generates a session identifier and identifies a firmware update file. The system generates a digital signature based on a combination of the session identifier and a first hash value of the firmware update file. The system provides, for storage in a block at the blockchain address, the digital signature. The system transmits the session identifier to the vehicle. The system transfers the firmware update file to the vehicle. The vehicle verifies the firmware update file using the digital signature retrieved from the block at the blockchain address, a second hash value of the firmware update file received from the data processing system, and the session identifier received from the data processing system.
Owner:CHONGQING JINKANG NEW ENERGY VEHICLE CO LTD +1
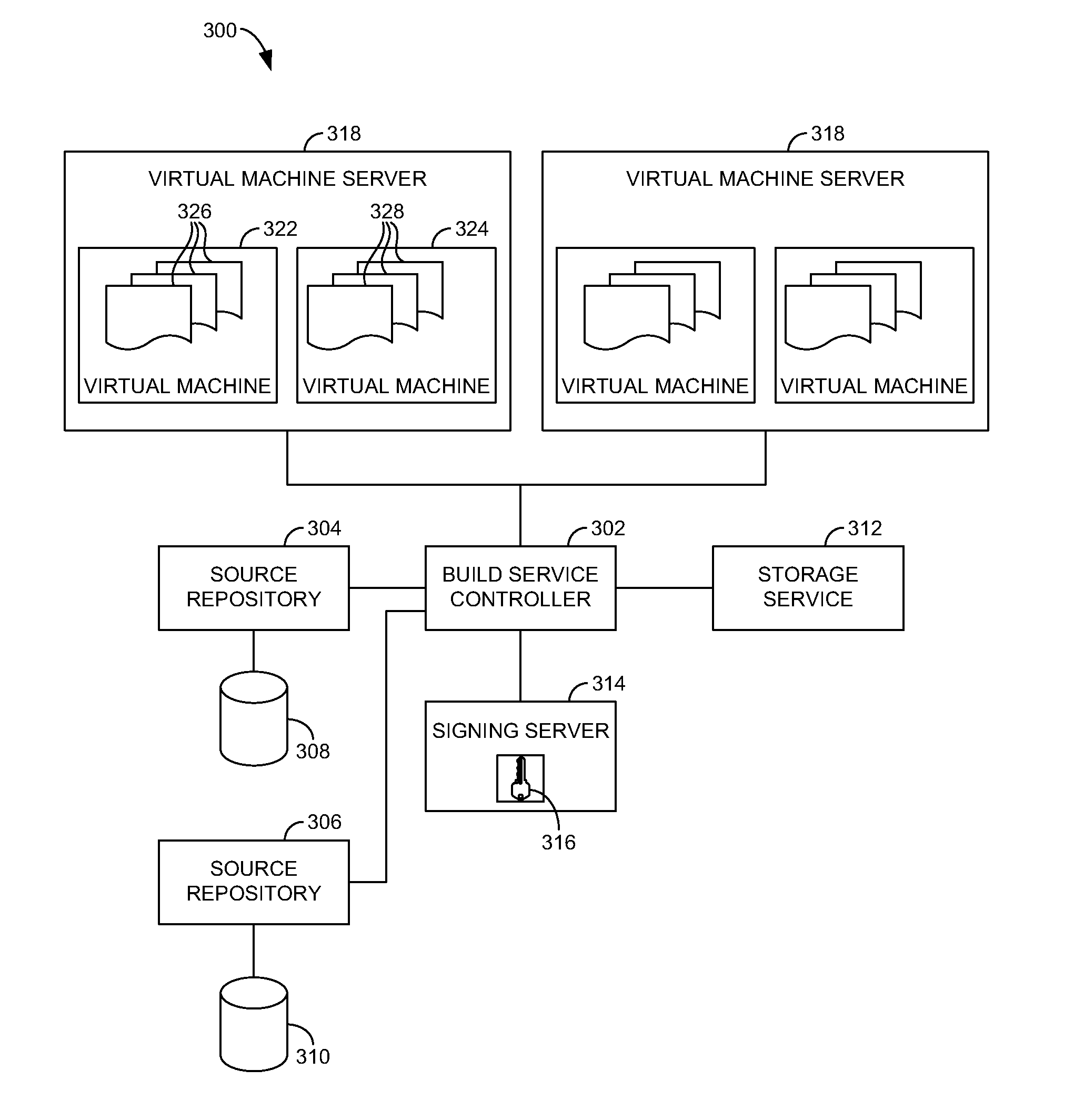
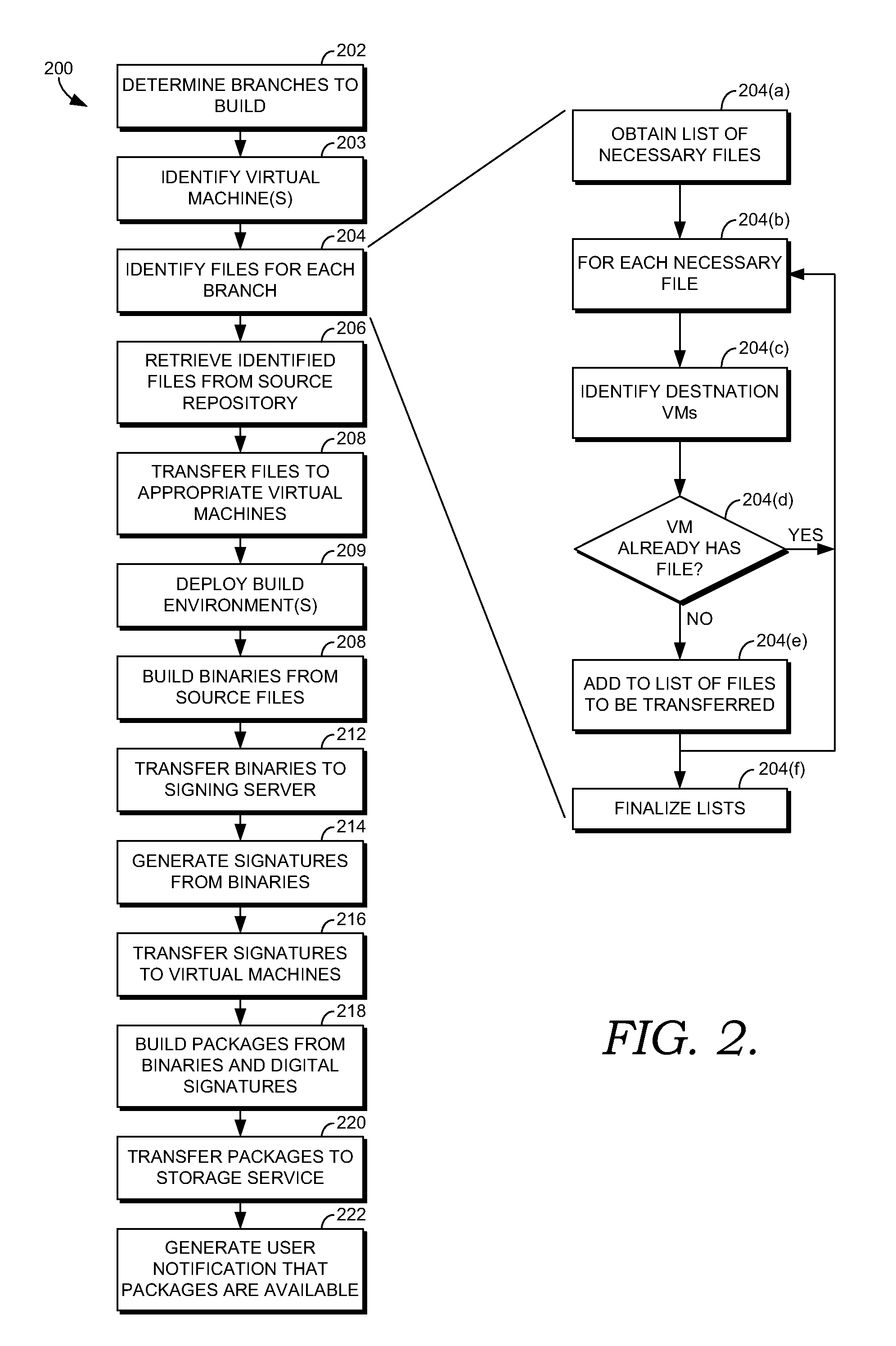
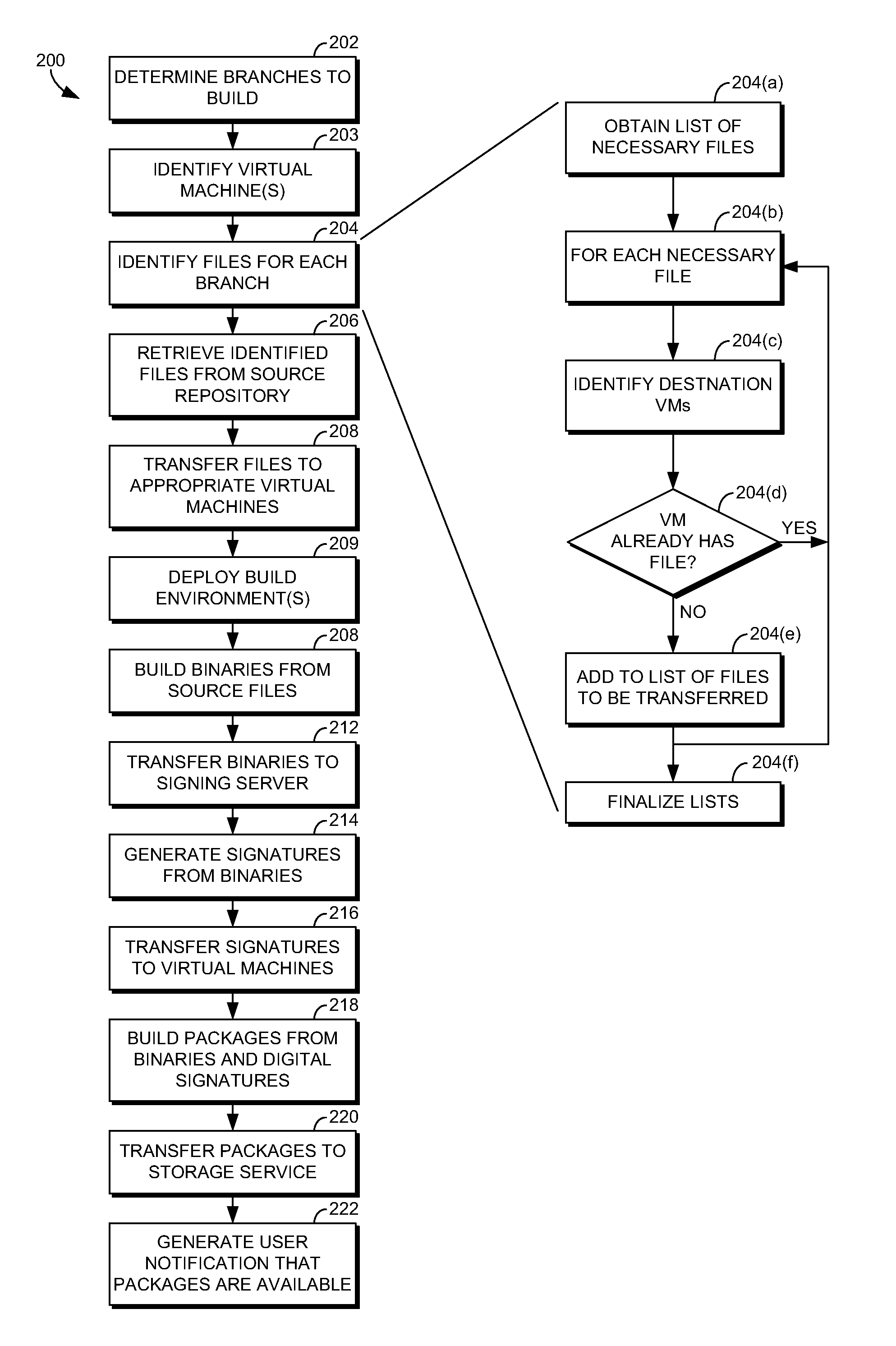
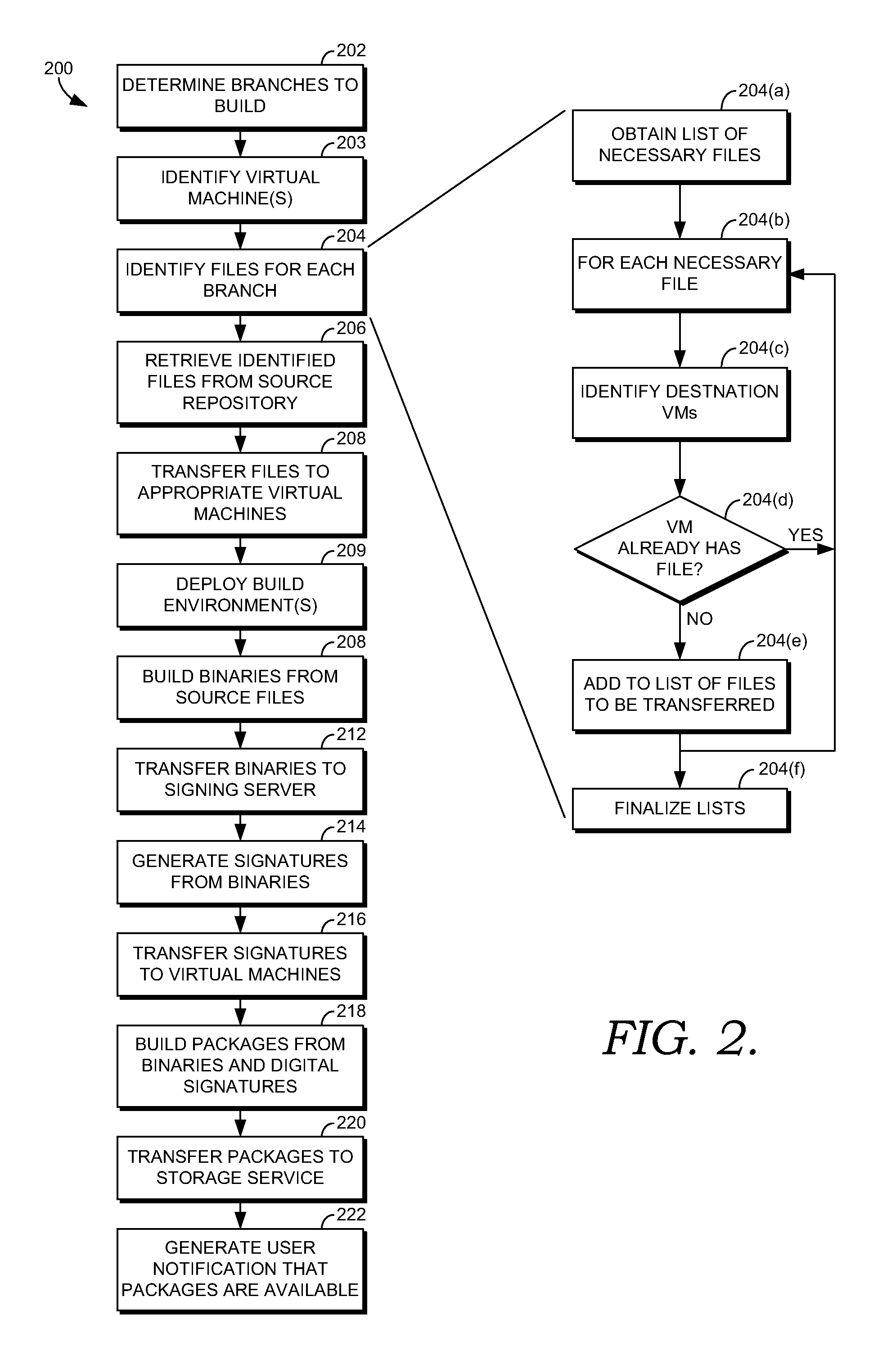
Cloud-based build service
ActiveUS20130055253A1Highly available and dynamically scalable and efficient build serviceExcess capacityVersion controlSoftware simulation/interpretation/emulationCloud baseScalable distributed
Building binary packages for software products, particularly large-scale software products, is a highly computation intensive process. Thus, it is desirable to distribute the workload over a large number of computing nodes so as to have the build process complete in an optimal period of time. One environment providing compute resources that can be utilized for a highly available and dynamically scalable distributed build process is an elastic compute cloud. In such an environment, virtual machines can be instantiated and destroyed as the resource requirements of the build process dictate. This has the advantage that dedicated hardware is unneeded, and excess capacity on the hardware employed can be employed for other computation tasks when the build process is idle. Presented herein are systems, methods and computer storage media for distributing a highly available and scalable build service, suitable for use in an elastic compute environment or other distributed environment.
Owner:MICROSOFT TECH LICENSING LLC
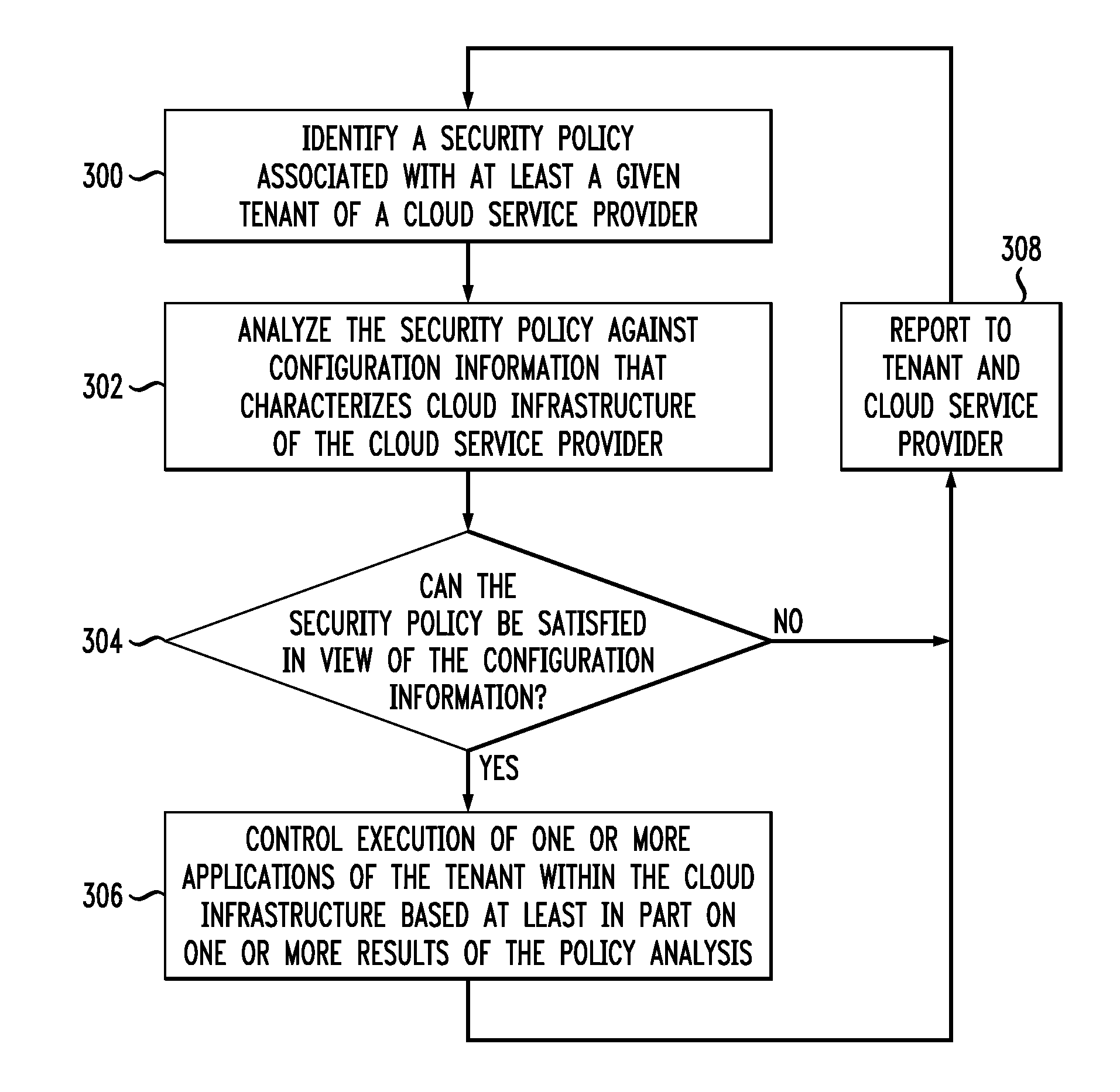
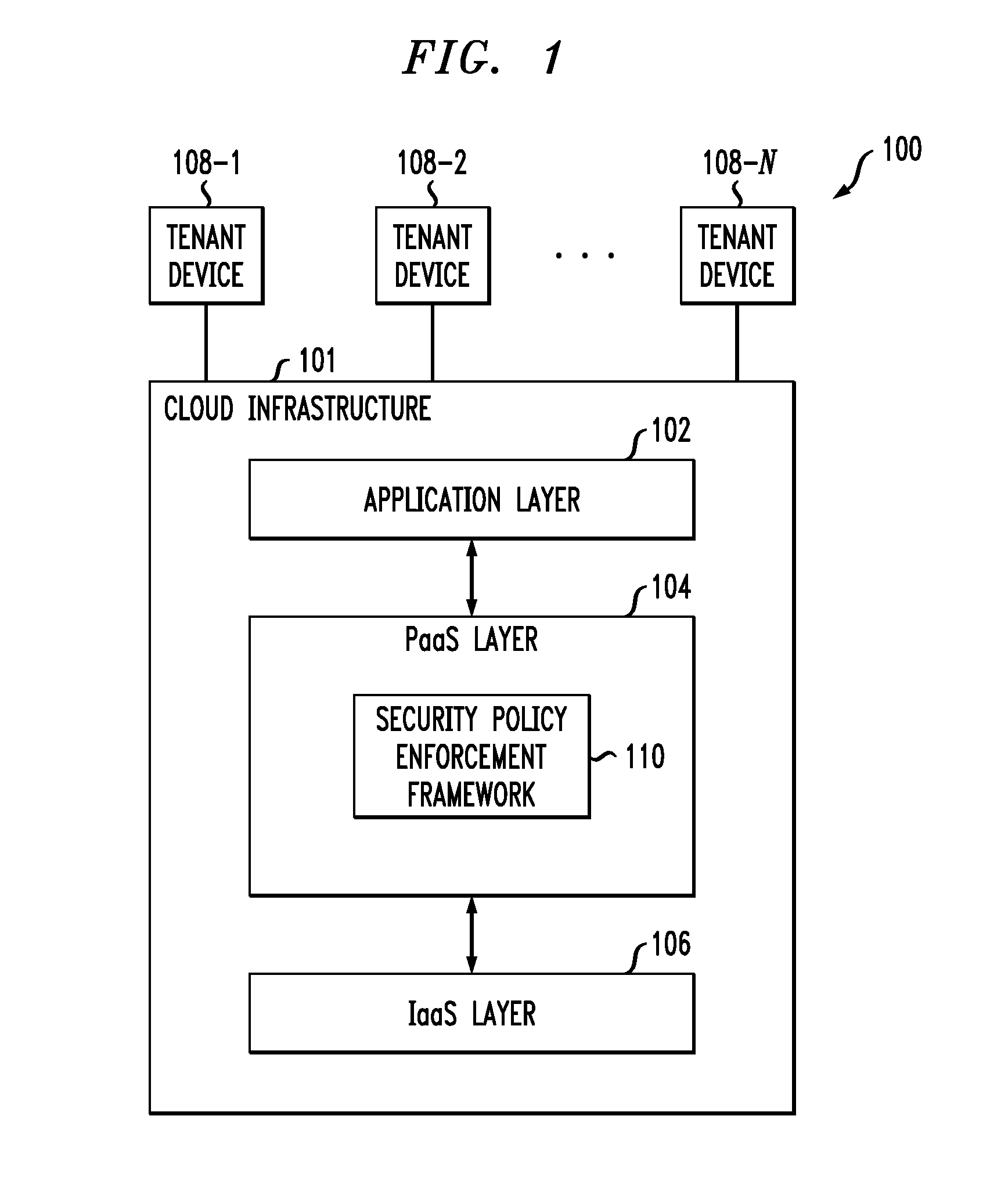
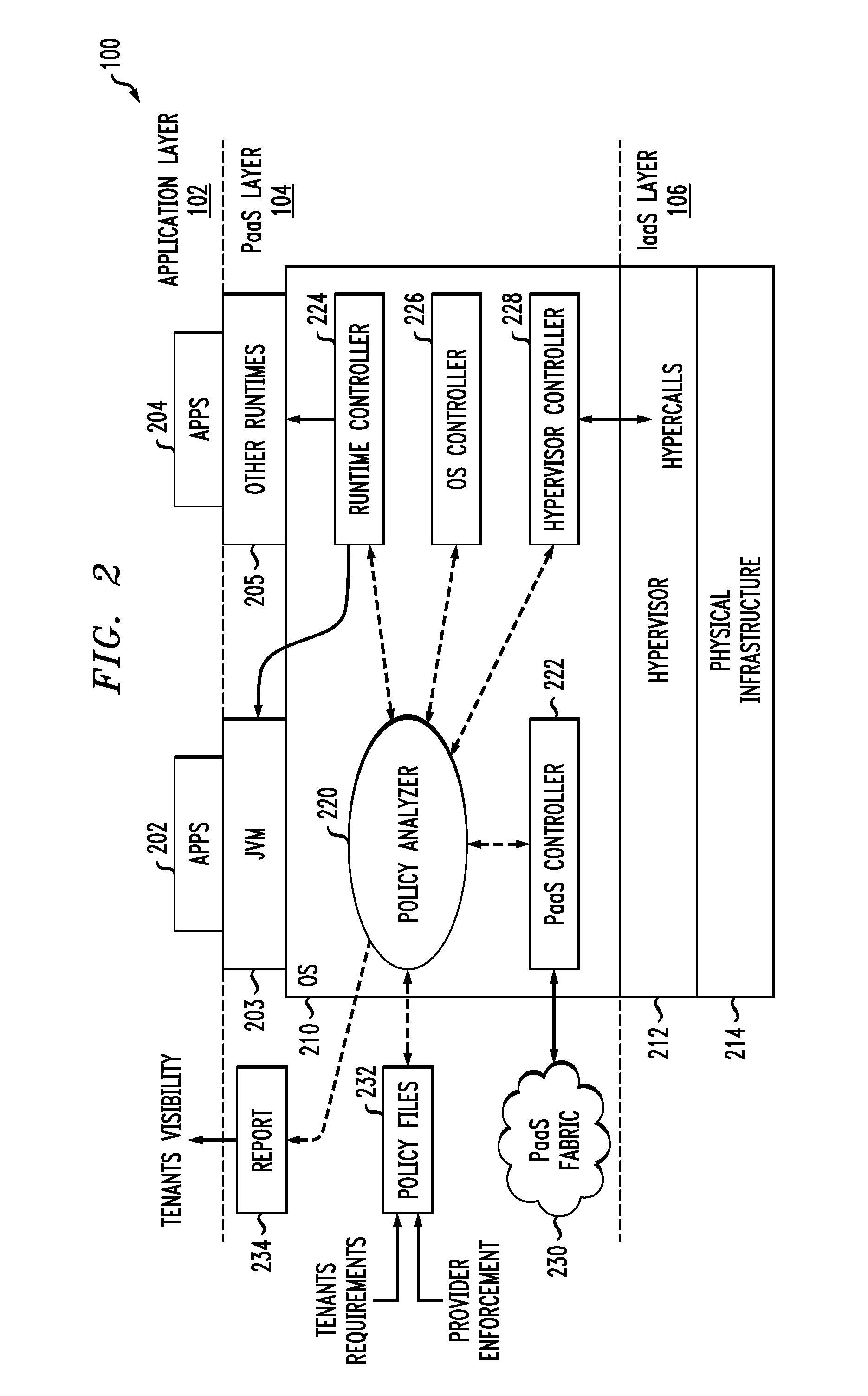
Security policy enforcement framework for cloud-based information processing systems
ActiveUS8689282B1Overcome difficultiesAvoid the needDigital data processing detailsAnalogue secracy/subscription systemsCloud service providerPlatform as a service
Cloud infrastructure of a cloud service provider comprises a processing platform implementing a security policy enforcement framework. The security policy enforcement framework comprises a policy analyzer that is configured to identify at least one security policy associated with at least one tenant of the cloud service provider, to analyze the security policy against configuration information characterizing the cloud infrastructure of the cloud service provider, and to control execution of one or more applications of said at least one tenant within the cloud infrastructure in accordance with the security policy, based at least in part on one or more results of the analysis of the security policy. The security policy enforcement framework may be implemented in a platform-as-a-service (PaaS) layer of the cloud infrastructure, and may comprise a runtime controller, an operating system controller, a hypervisor controller and a PaaS controller.
Owner:EMC IP HLDG CO LLC +1
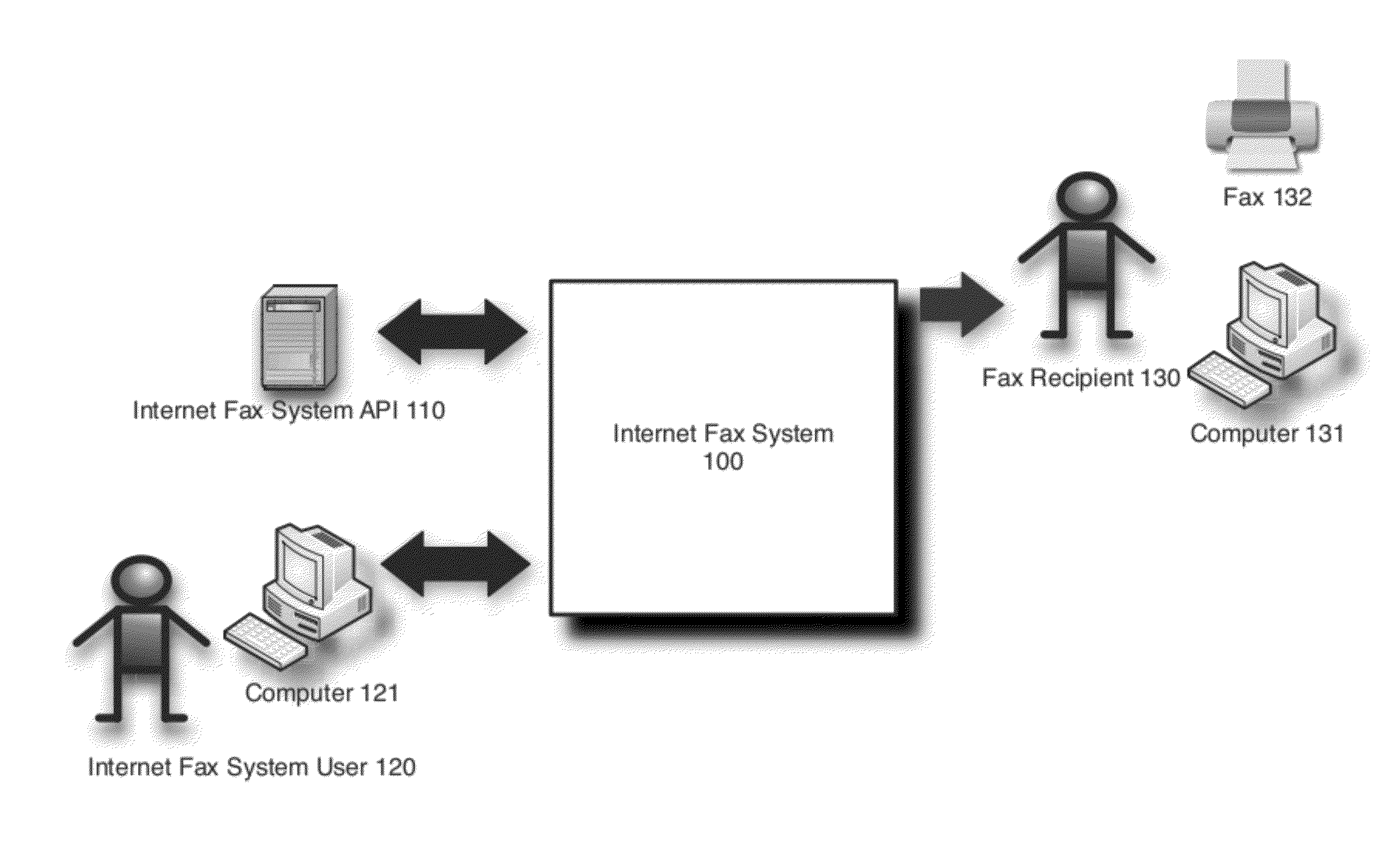
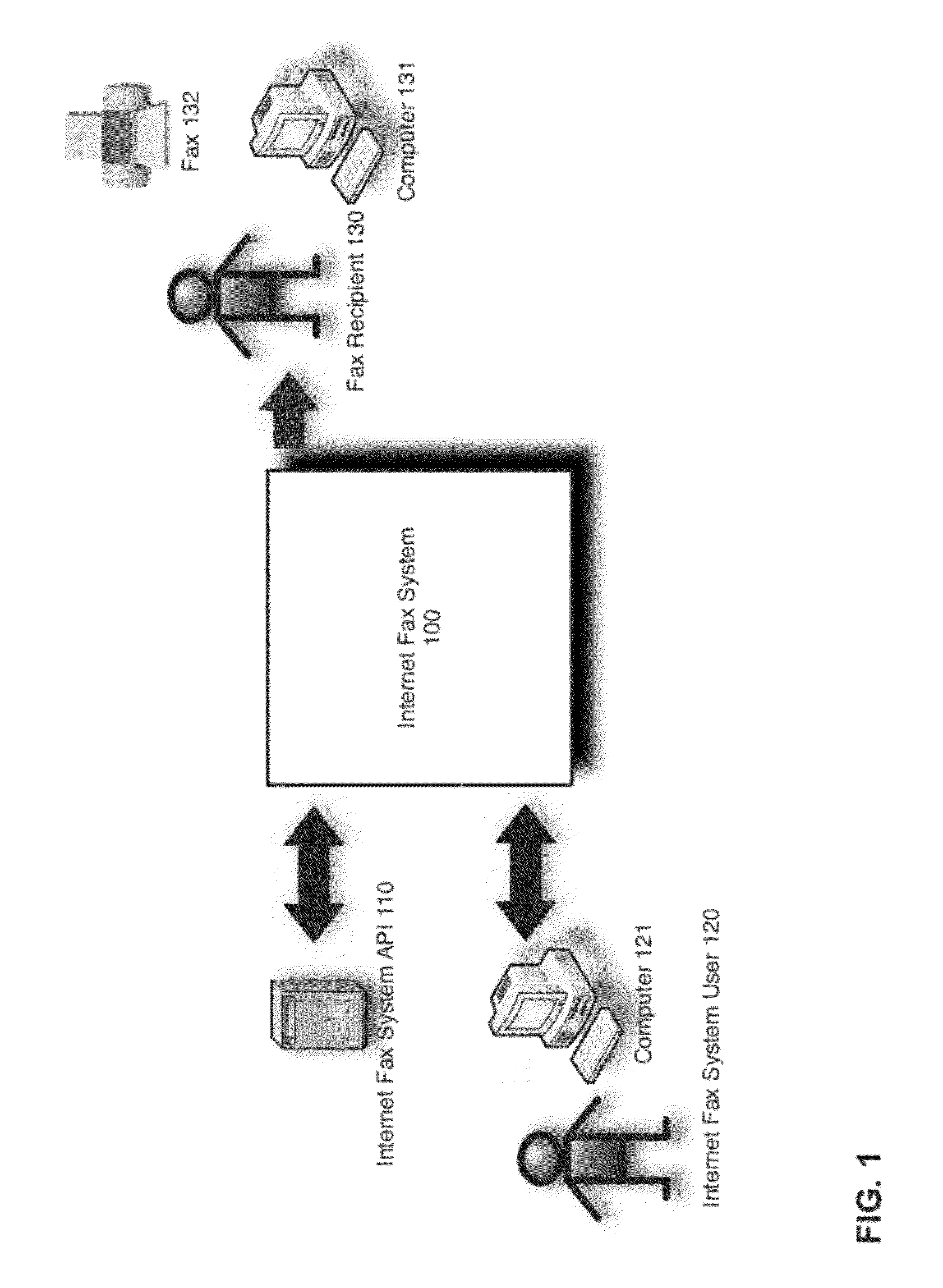
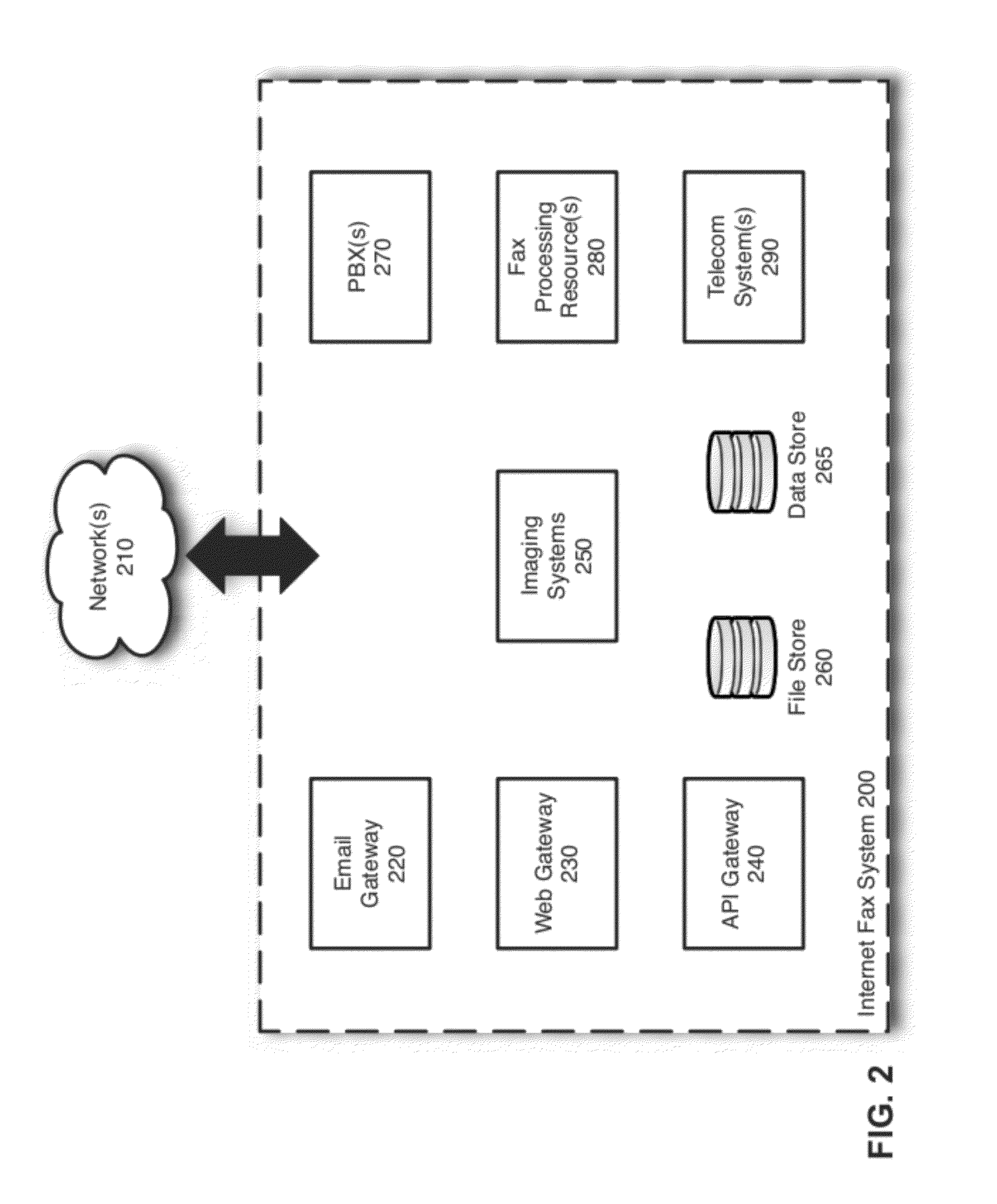
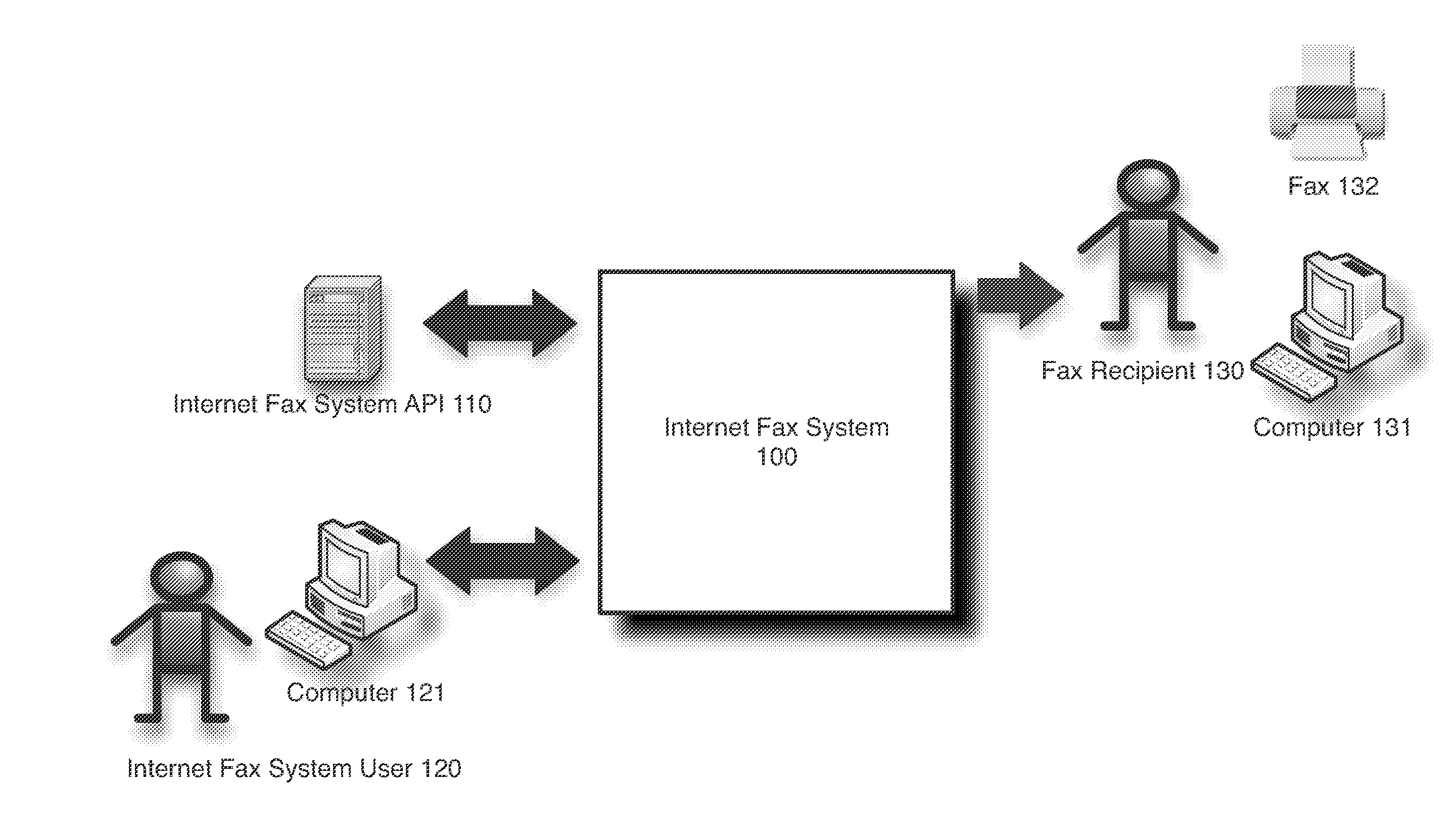
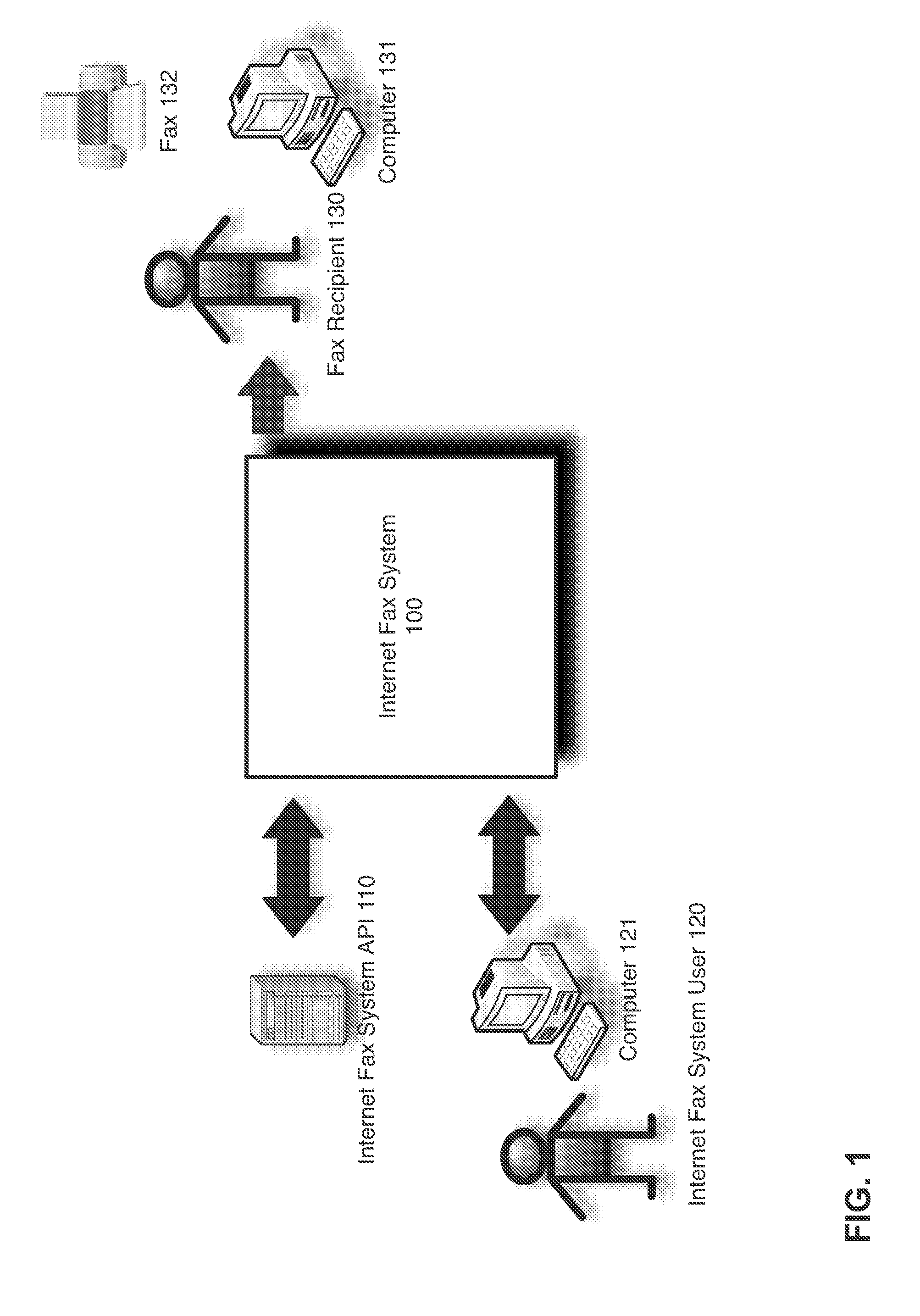
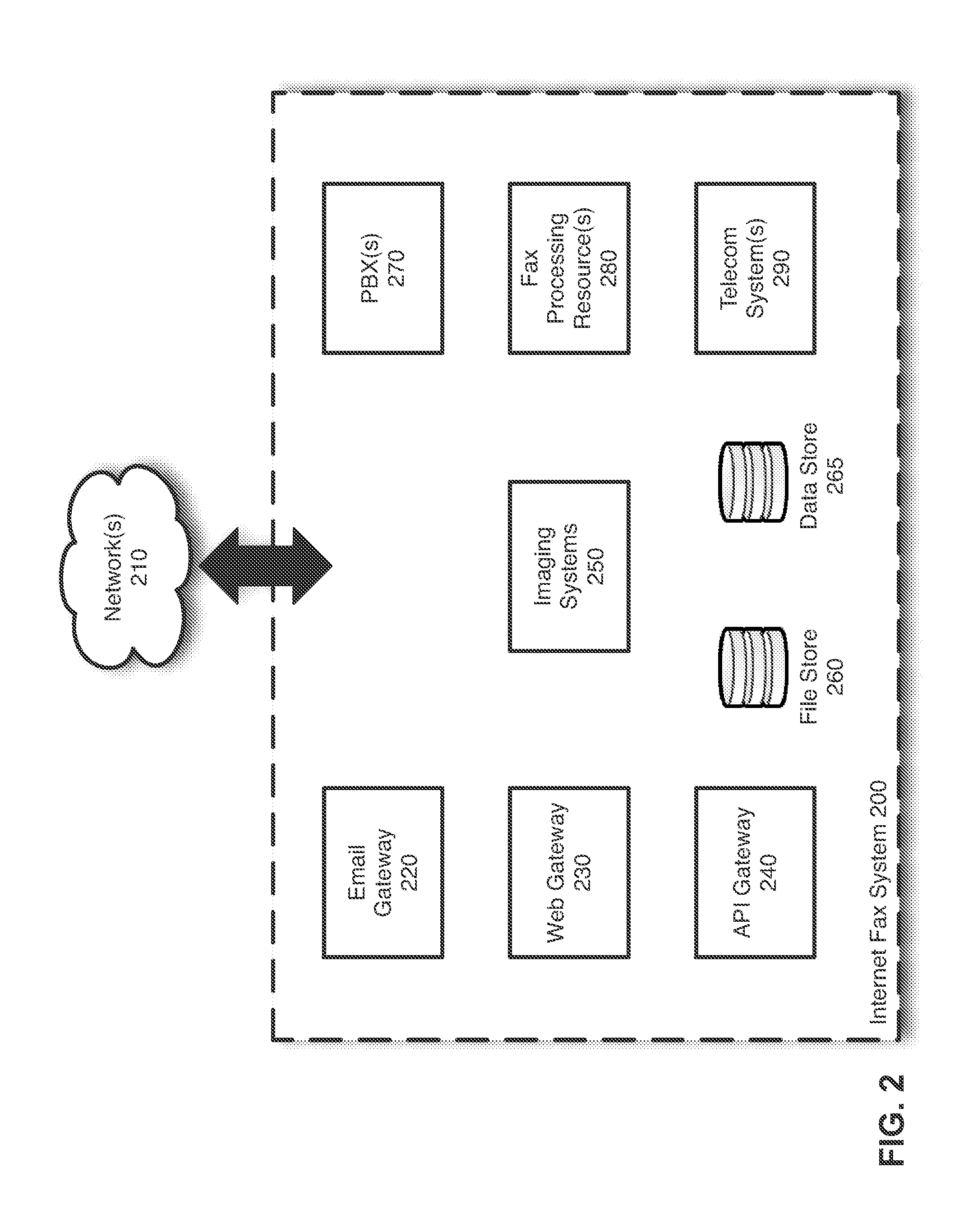
Scalable and flexible internet fax architecture for processing outbound fax messages
ActiveUS8254538B1Efficient and scalableData switching networksTelephone data service arrangmentsModem deviceTTEthernet
Owner:J2 CLOUD SERVICES LLC
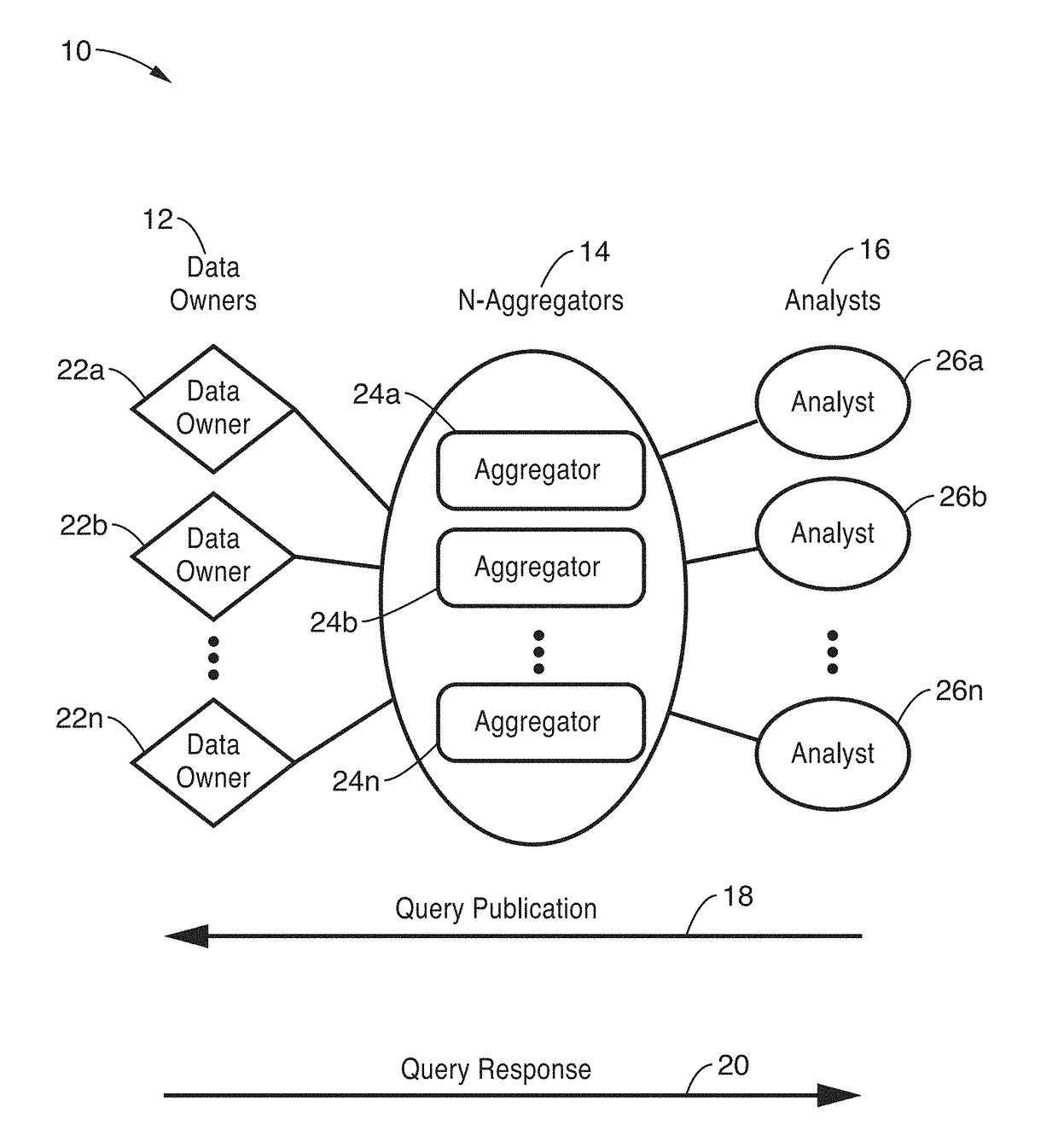
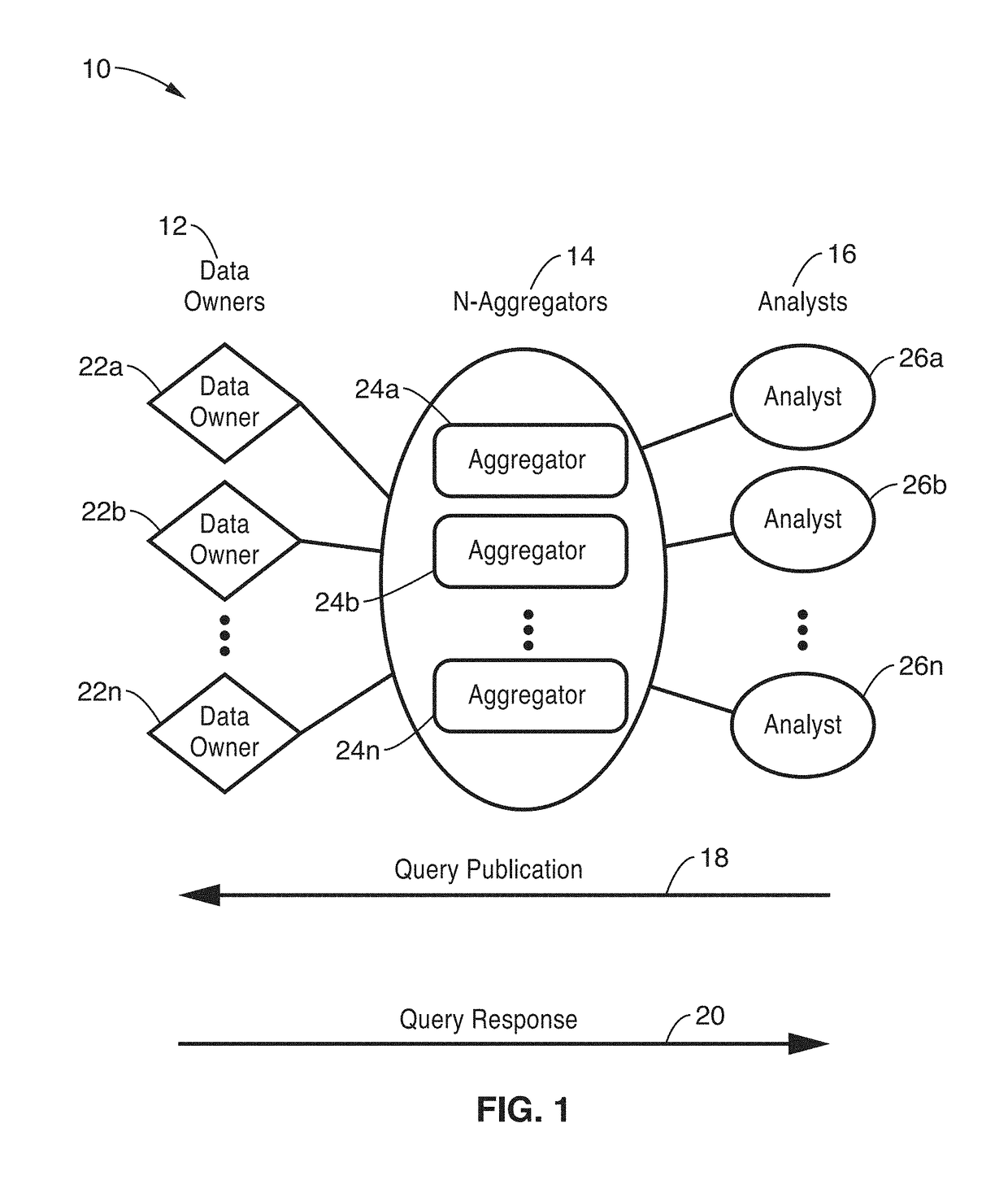
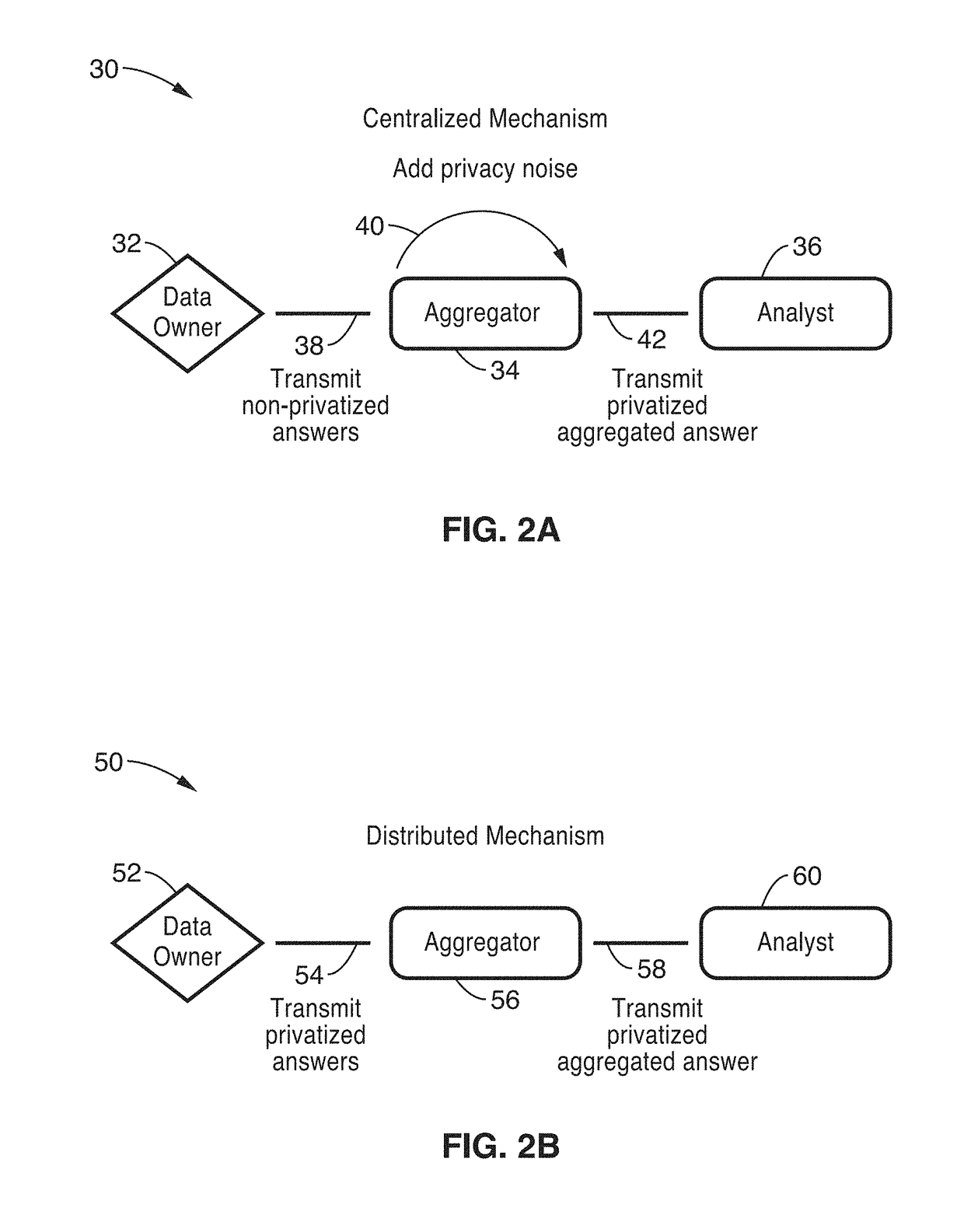
Privacy-preserving stream analytics
ActiveUS20170353855A1Shorten the timeIncrease profitDigital data protectionTransmissionInternet privacyThe Internet
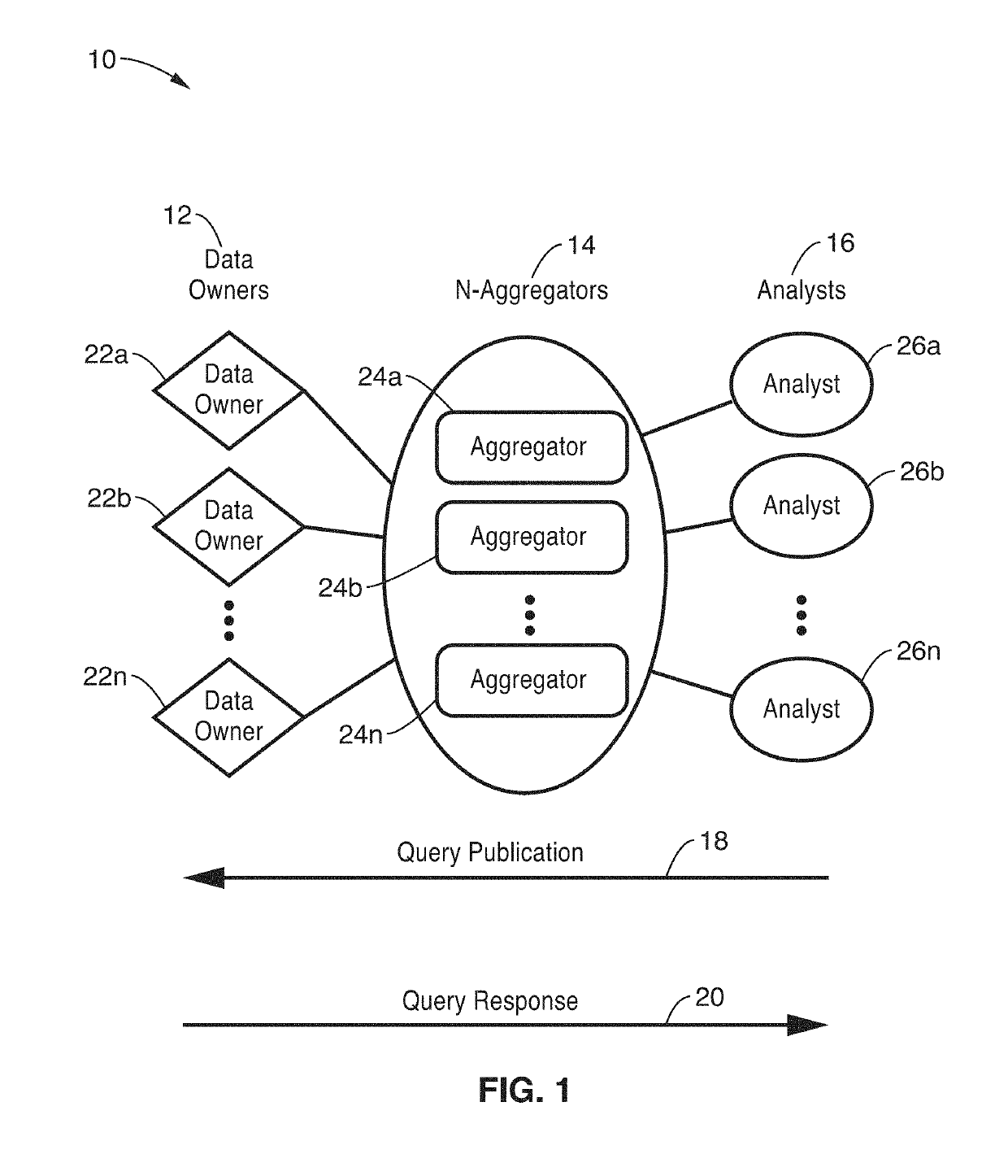
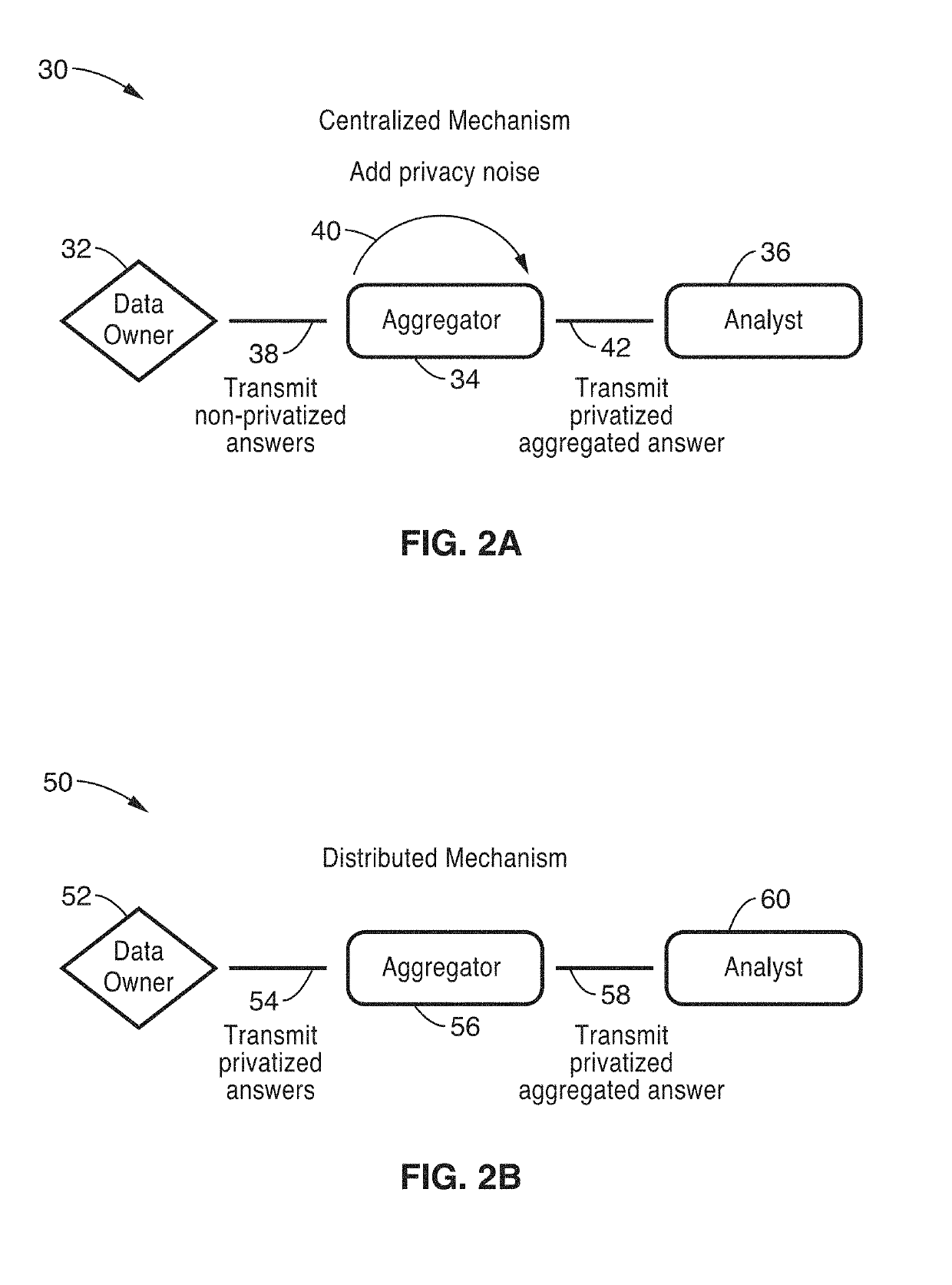
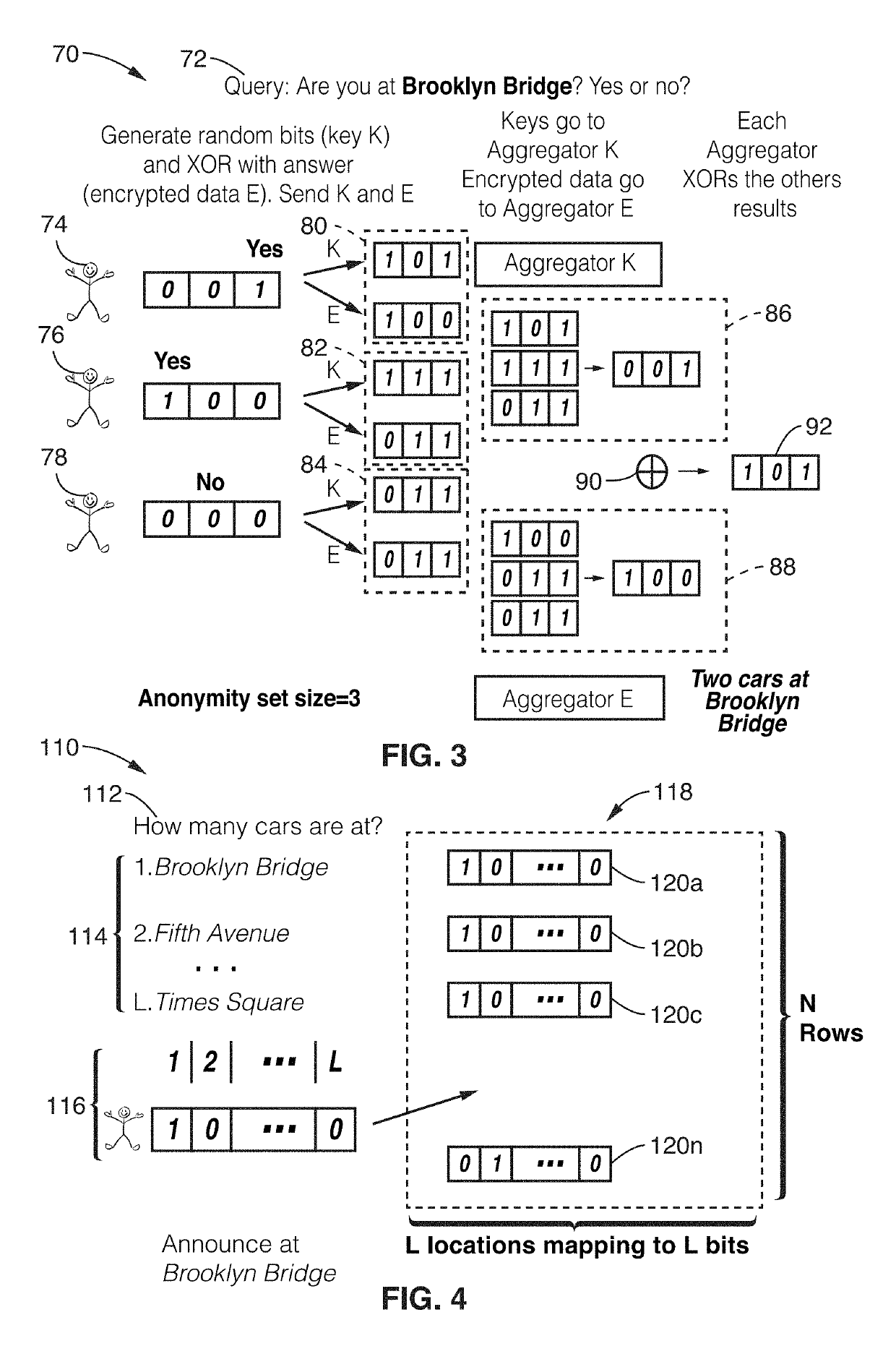
Privacy-preserving stream analytics (personal data collection method, apparatus, and / or system) from an electronic (e.g., mobile) device providing communications, such as to a network (e.g., Internet). Data queries from a data analyst are received but not directly answered with a truthful query response. Truthful responses are privatized and anonymized based on a randomized response mechanism which releases privatized data and not the original answer. Anonymously transmitting randomized responses from the data owner to data aggregator using shares, each share of which is individually transmitted to an independent aggregator, which is configured for independently and asynchronously process each share, and sharing results with one another to arrive at a query response over an aggregate number of data owners.
Owner:RGT UNIV OF CALIFORNIA
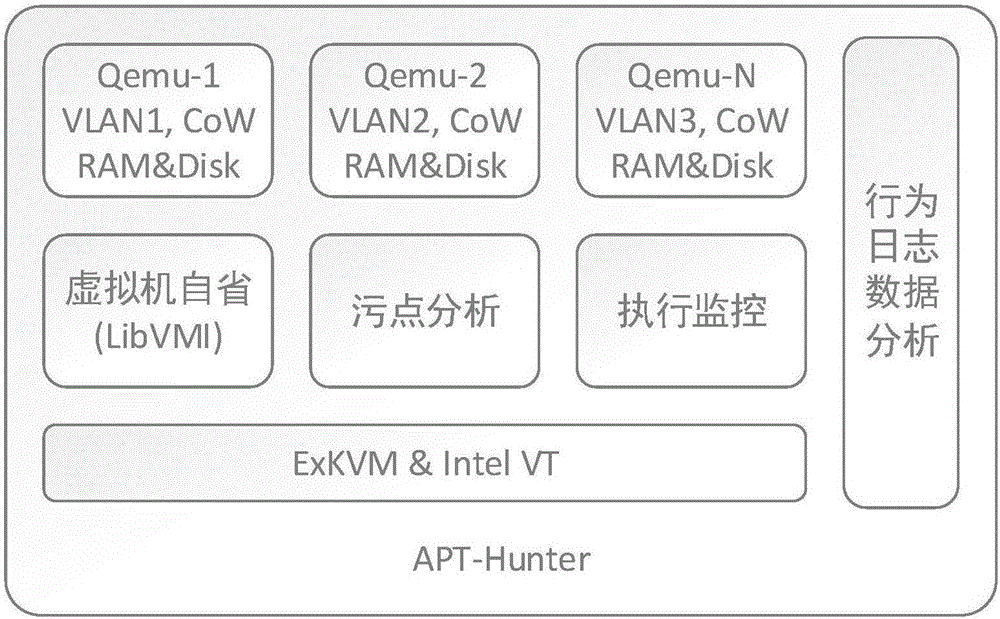
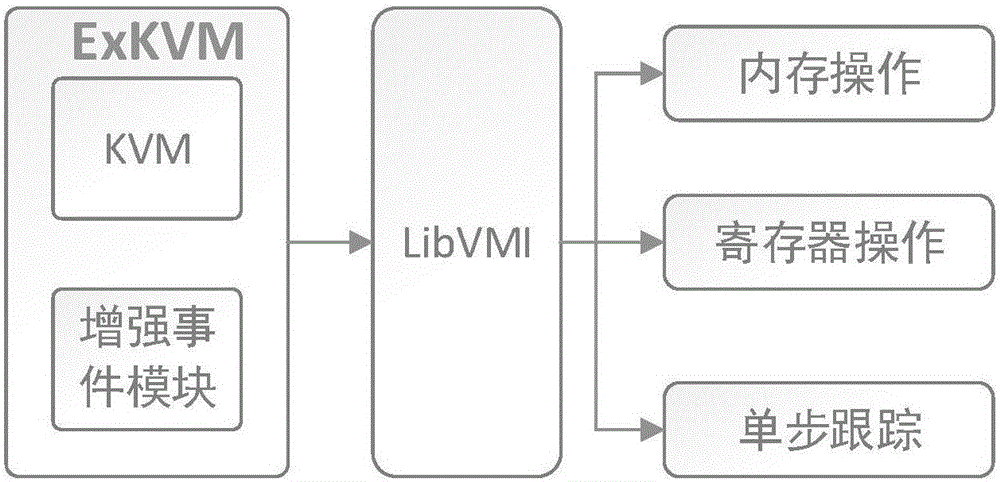
Detection method for APTs (Advanced Persistent Threat) based on instruction monitoring
ActiveCN106850582AImprove efficiencyImprove scalability and reliabilityPlatform integrity maintainanceTransmissionVirtual machine introspectionVirtual machine
The invention discloses a detection method for APTs (Advanced Persistent Threat) based on instruction monitoring. The method is characterized in that identification for virtual machine execution behaviors on an Hypervisor level is realized through an ExKVM and a virtual machine introspection library LibVMI, monitoring outside a virtual machine for an operating state of a malicious code in the virtual machine is realized and vulnerability exploitation attacks are discovered by use of a dynamic offline taint analysis method; monitoring for a user-layer API and kernel-layer API execution is carried out without an invasion by use of a #BP address injection method outside the virtual machine; and tracking for kernel stack allocation is realized through the injection of the kernel memory allocation function and the kernel module structure operating function of Windows. The offline taints are analyzed and the malicious behaviors are discovered through tracking and recording write, exchange and branch instructions between a memory and a register during the malicious code execution. According to the invention, the vulnerability exploitation during the APT attack can be monitored effectively and the detection rate of malicious samples is improved.
Owner:CHINA ELECTRONICS TECH CYBER SECURITY CO LTD
Secure firmware updates for remote vehicles
InactiveUS20190394046A1Function increaseEfficiently securely transferEncryption apparatus with shift registers/memoriesUser identity/authority verificationData processing systemDigital signature
Systems and methods of secure firmware updates on remote vehicles are provided. The system receives a request from a vehicle for an update to vehicle firmware, and identifies a blockchain address for the vehicle. The system generates a session identifier and identifies a firmware update file. The system generates a digital signature based on a combination of the session identifier and a first hash value of the firmware update file. The system provides, for storage in a block at the blockchain address, the digital signature. The system transmits the session identifier to the vehicle. The system transfers the firmware update file to the vehicle. The vehicle verifies the firmware update file using the digital signature retrieved from the block at the blockchain address, a second hash value of the firmware update file received from the data processing system, and the session identifier received from the data processing system.
Owner:CHONGQING JINKANG NEW ENERGY VEHICLE CO LTD +1
Methods and systems for managing computations on a hybrid computing platform including a parallel accelerator
ActiveUS8225074B2Efficient managementImprove convenienceGeneral purpose stored program computerPhysical realisationParallel computingData transmission
In accordance with exemplary implementations, application computation operations and communications between operations on a host processing platform may be adapted to conform to the memory capacity of a parallel accelerator. Computation operations may be split and scheduled such that the computation operations fit within the memory capacity of the accelerator. Further, the operations may be automatically adapted without any modification to the code of an application. In addition, data transfers between a host processing platform and the parallel accelerator may be minimized in accordance with exemplary aspects of the present principles to improve processing performance.
Owner:NEC CORP
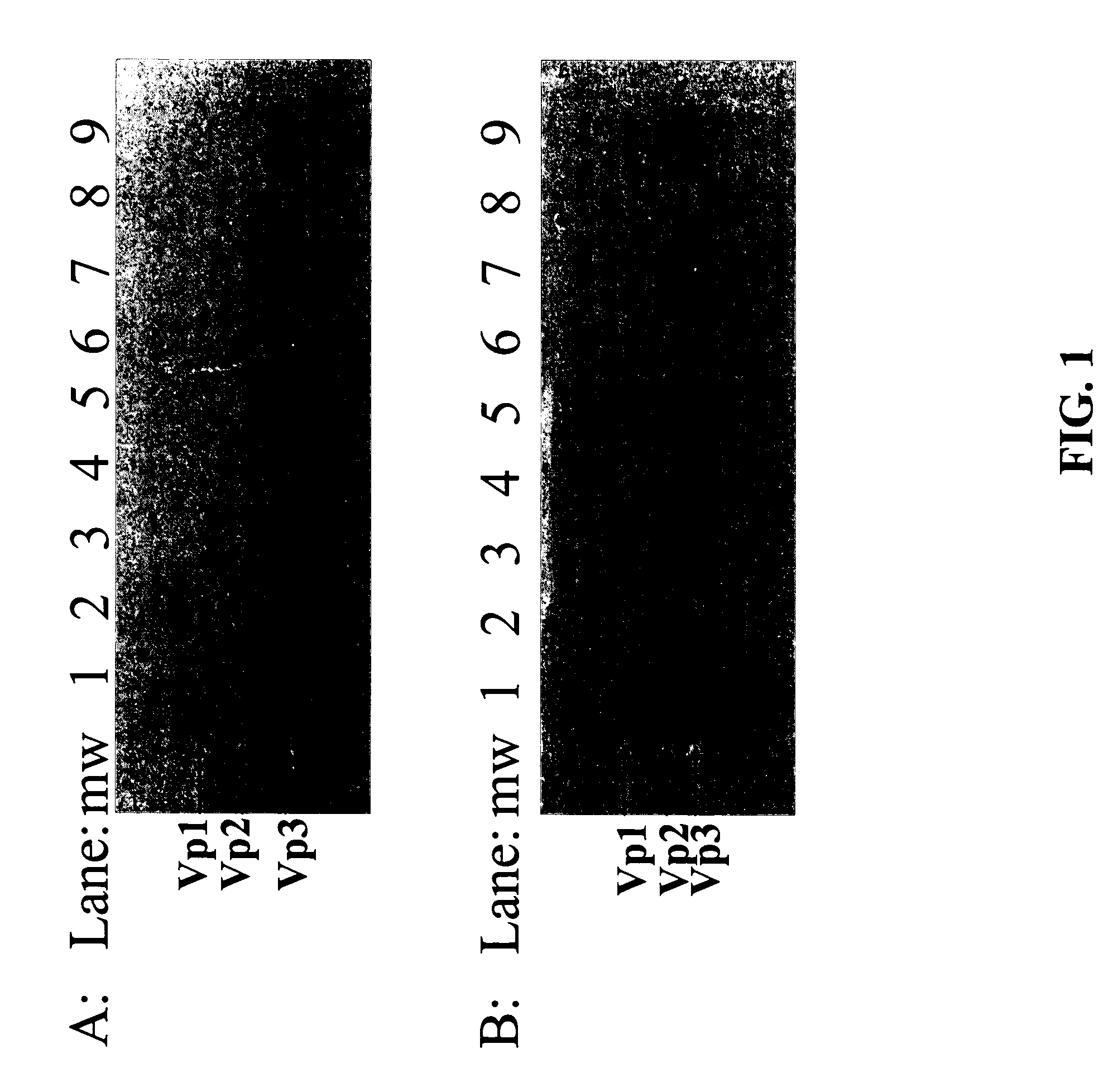
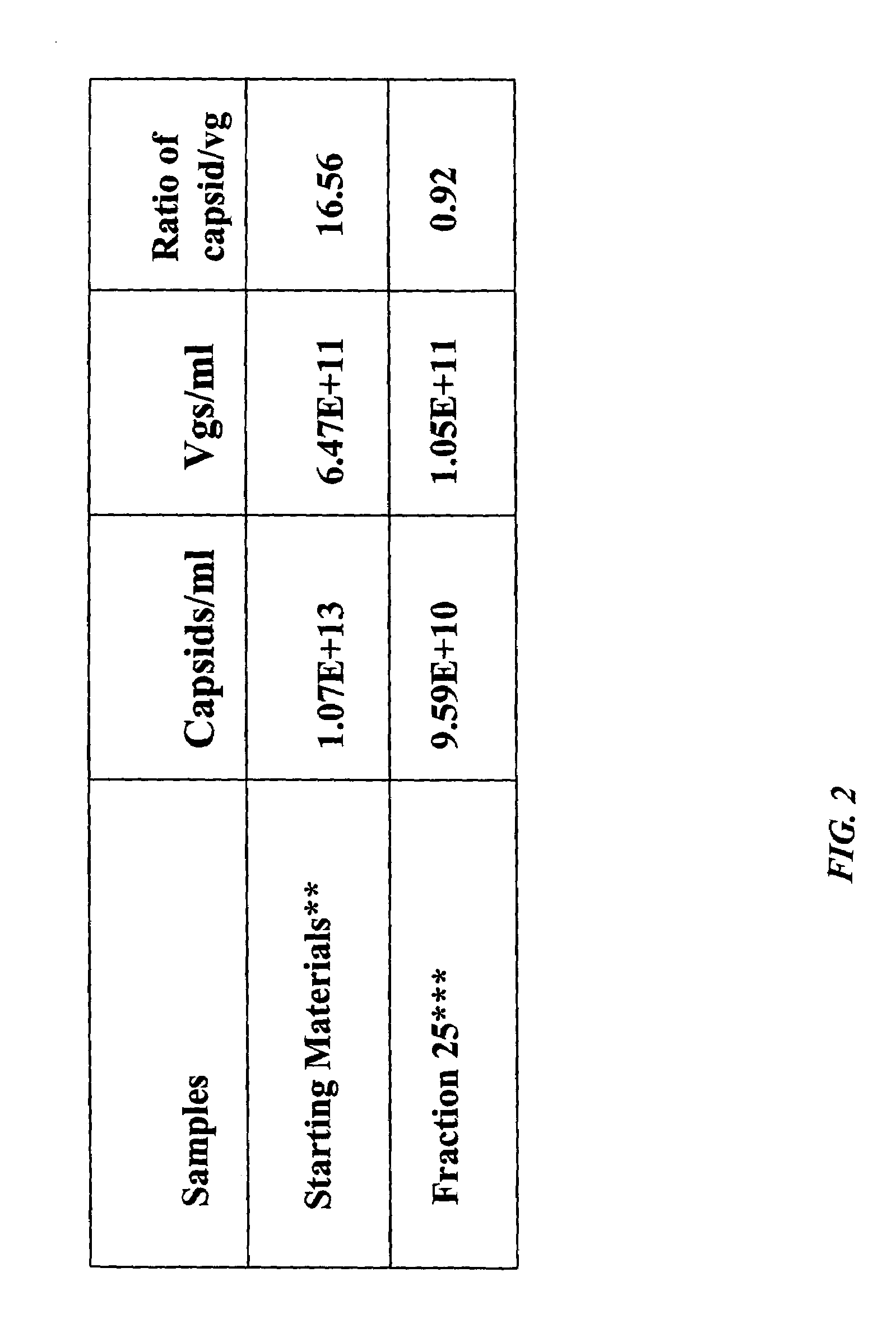
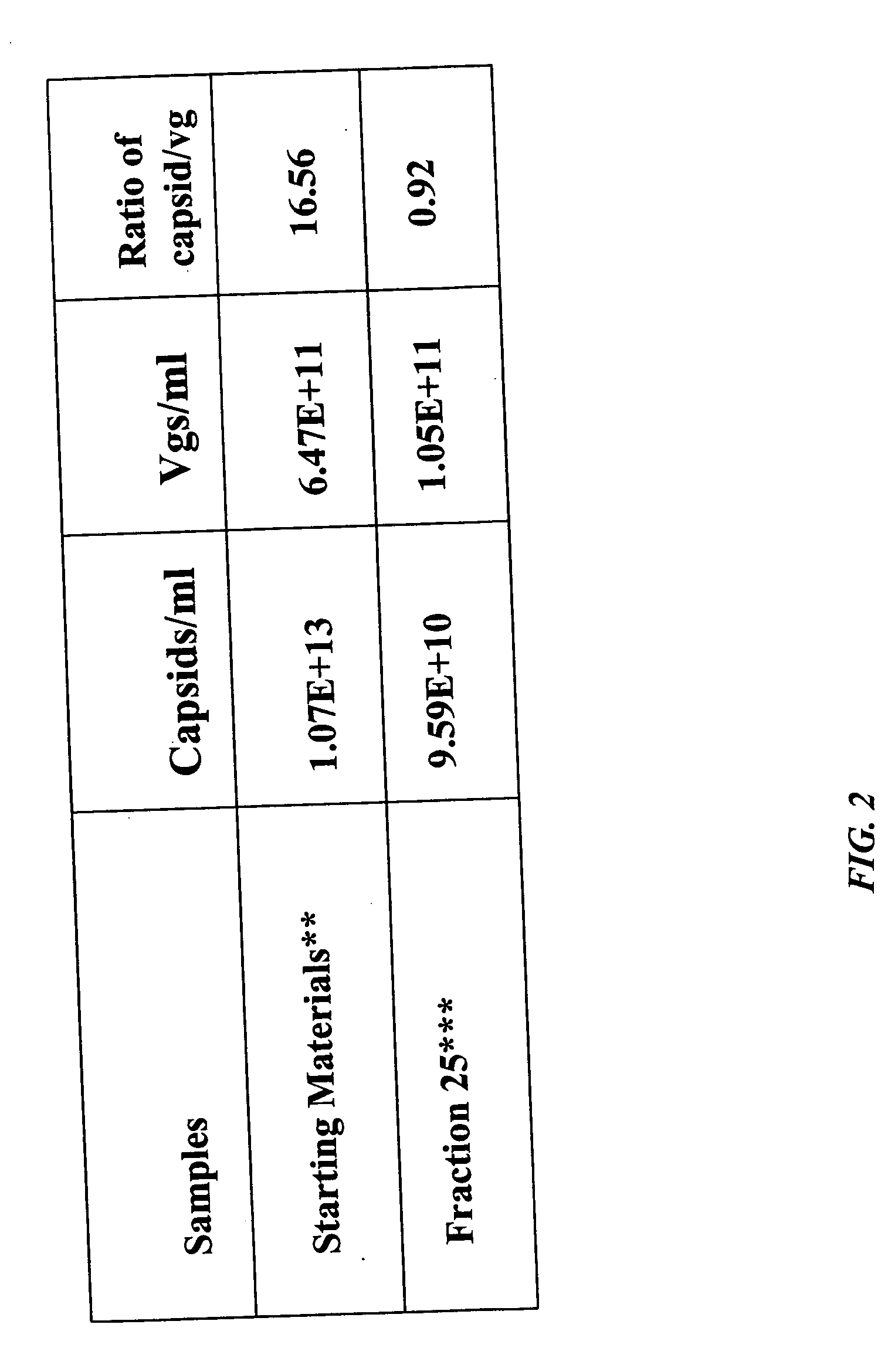
Methods for producing preparations of recombinant AAV virions substantially free of empty capsids
ActiveUS7261544B2Reduce the amount requiredEfficient and scalableSsRNA viruses negative-senseCeramic shaping apparatusBiotechnologyCapsid
Methods for separating AAV empty capsids from mixtures of AAV vector particles and AAV empty capsids are described. The methods use column chromatography techniques and provide for commercially viable levels of recombinant AAV virions.
Owner:GENZYME CORP
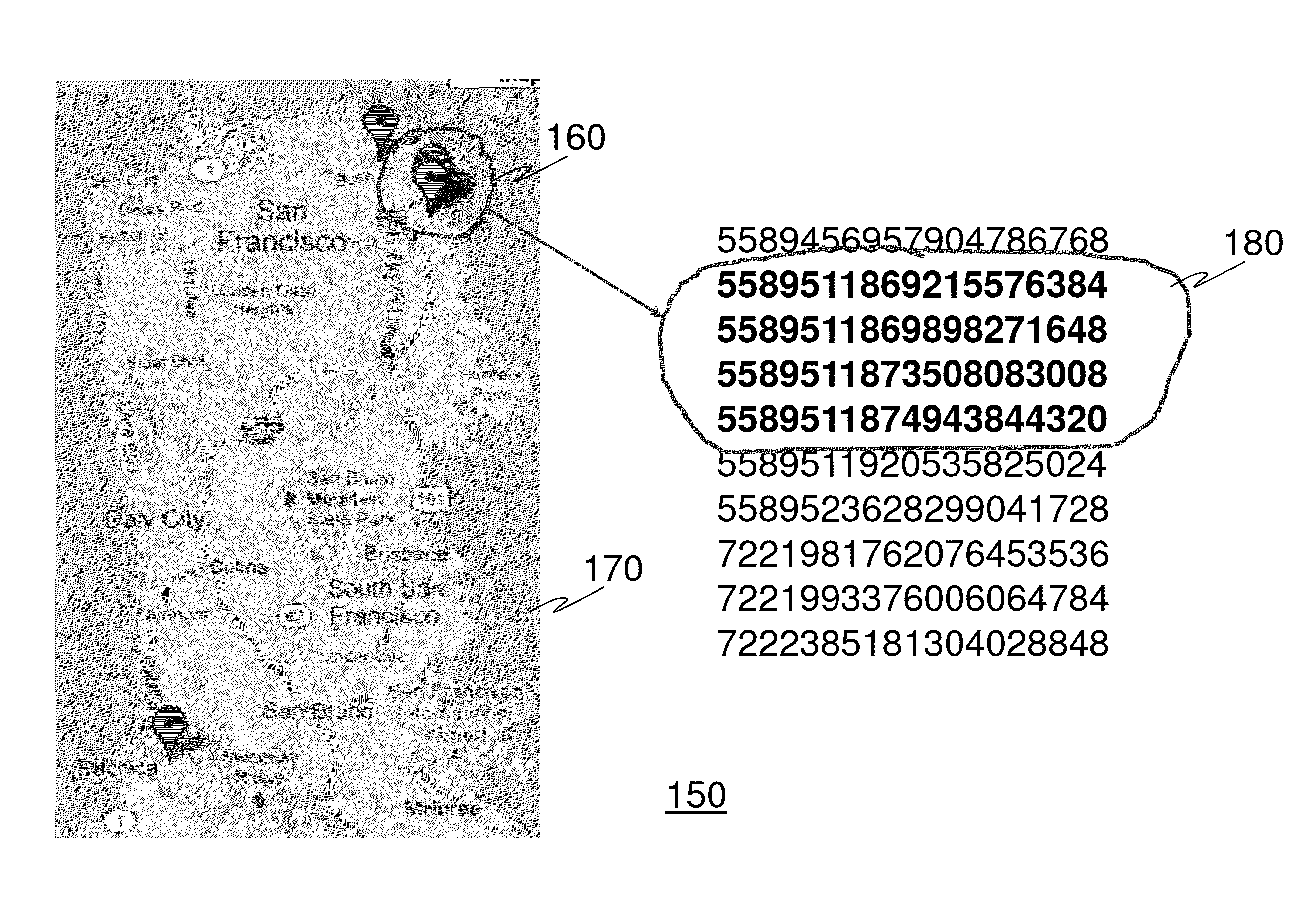
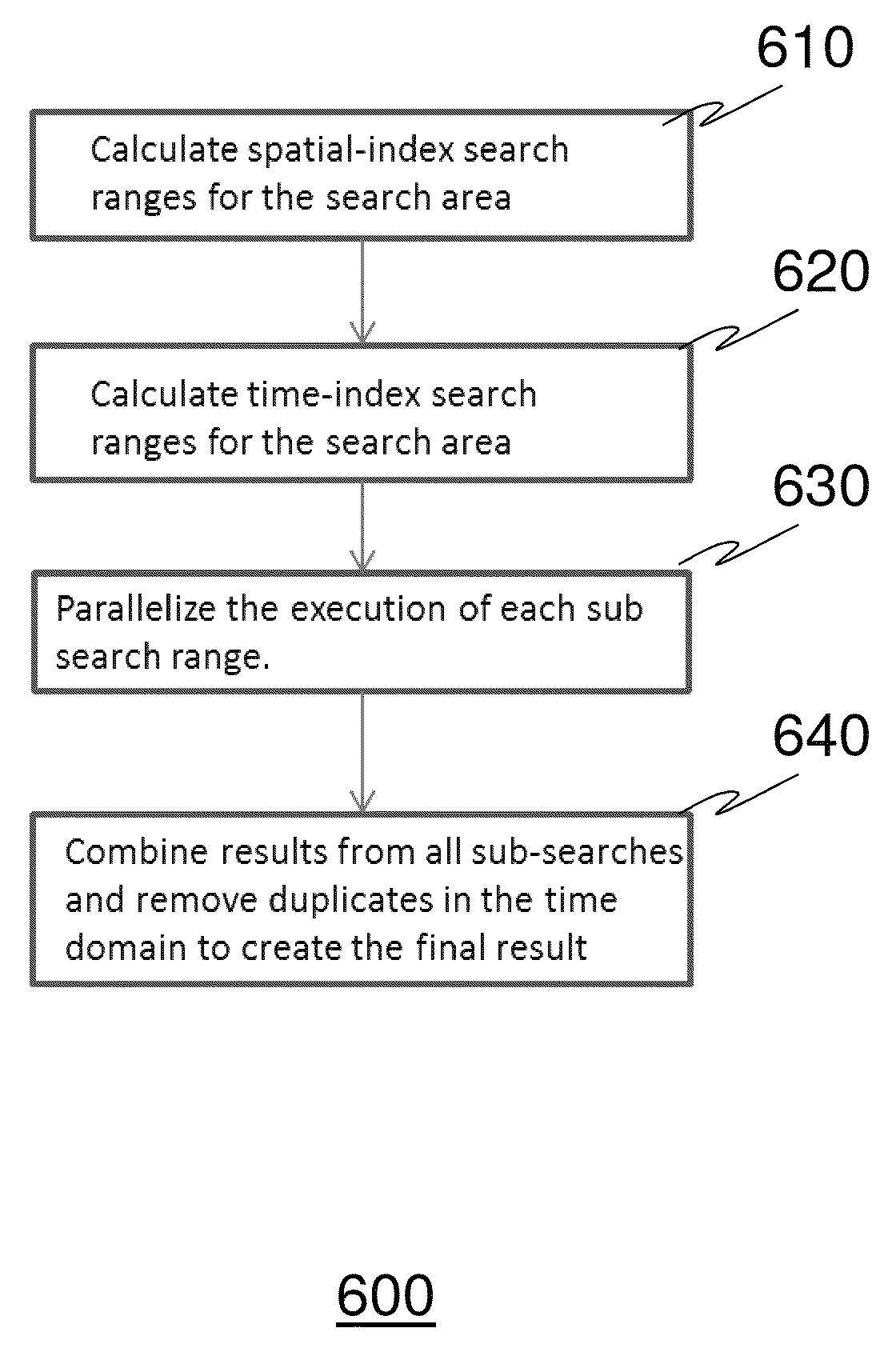
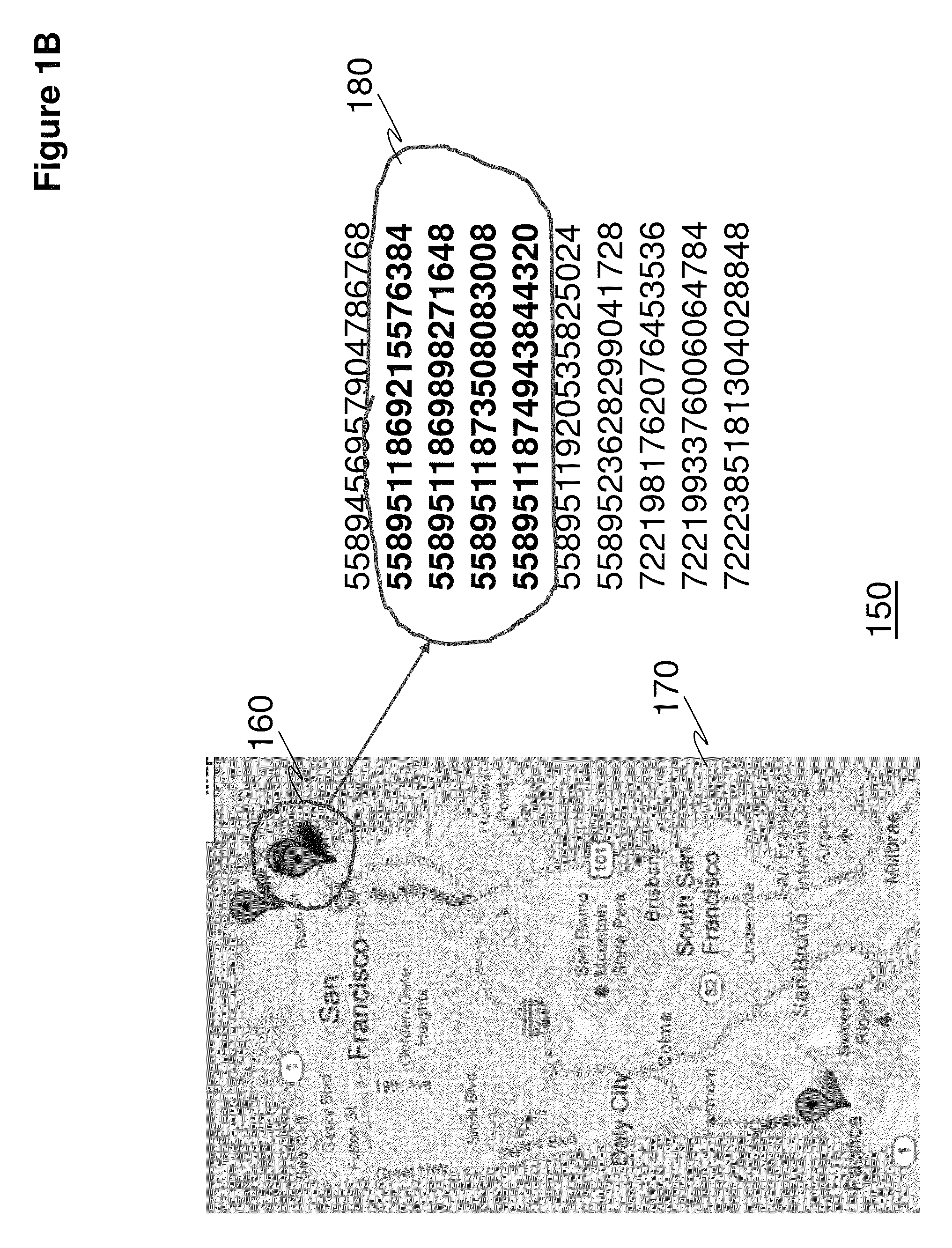
System and method for large-scale and near-real-time search of mobile device locations in arbitrary geographical boundaries
ActiveUS20130225201A1Efficient and scalablePosition fixationWireless communicationLine searchReal-time Search
A system and method for generating a one-dimensional spatial index and a temporal index in relation to one or more two-dimensional location points of one or more mobile devices to enable near-real-time searching of devices having fast-changing location information is provided for. The present invention may be used in a variety of implementations including being used in conjunction with searching for mobile devices within a geographical area for a time period; finding nearby devices within a time period; tracking device movement within a time period; determining clusters of devices for identification and location across different geographical regions at once.
Owner:AERIS COMM
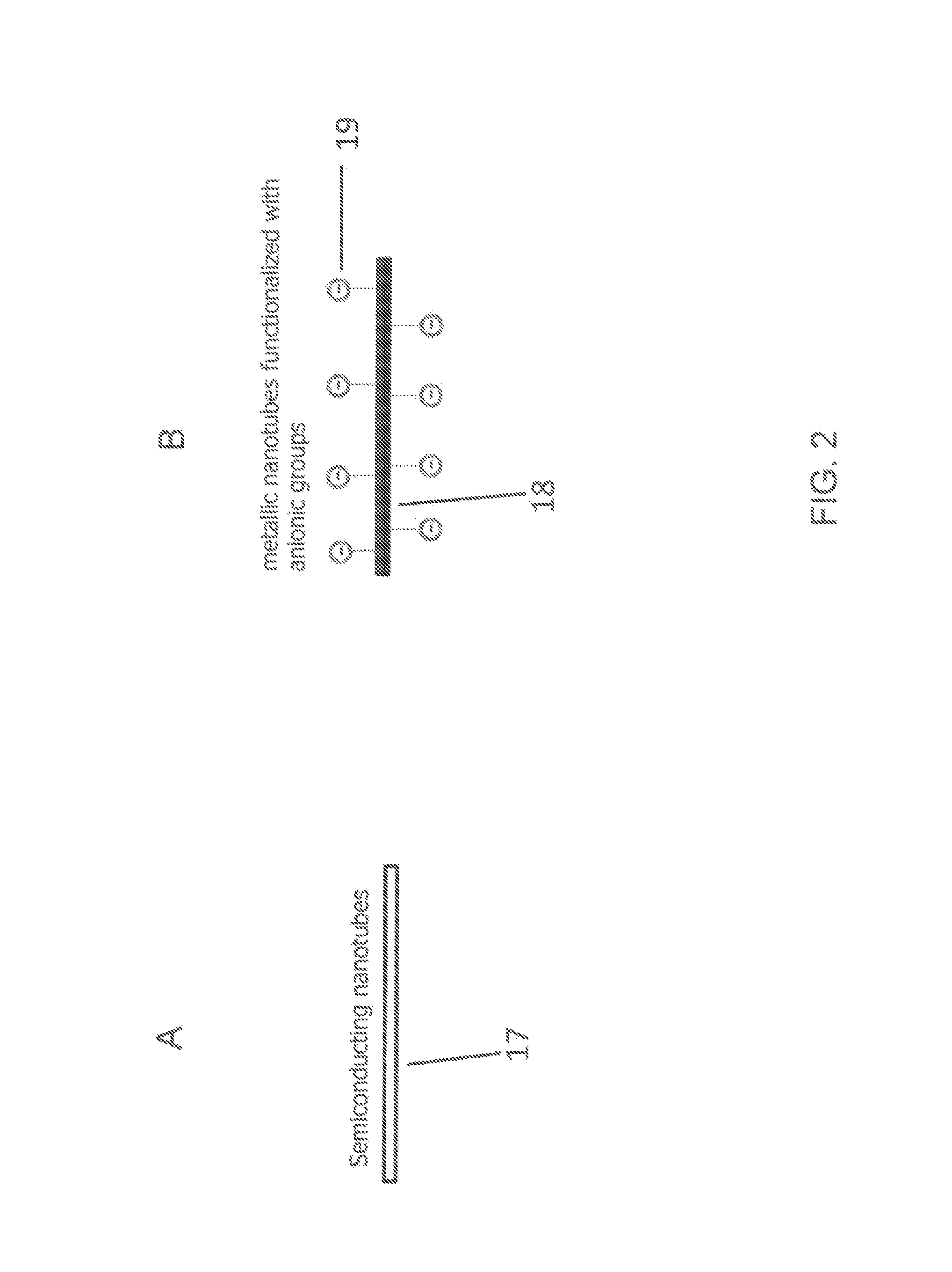
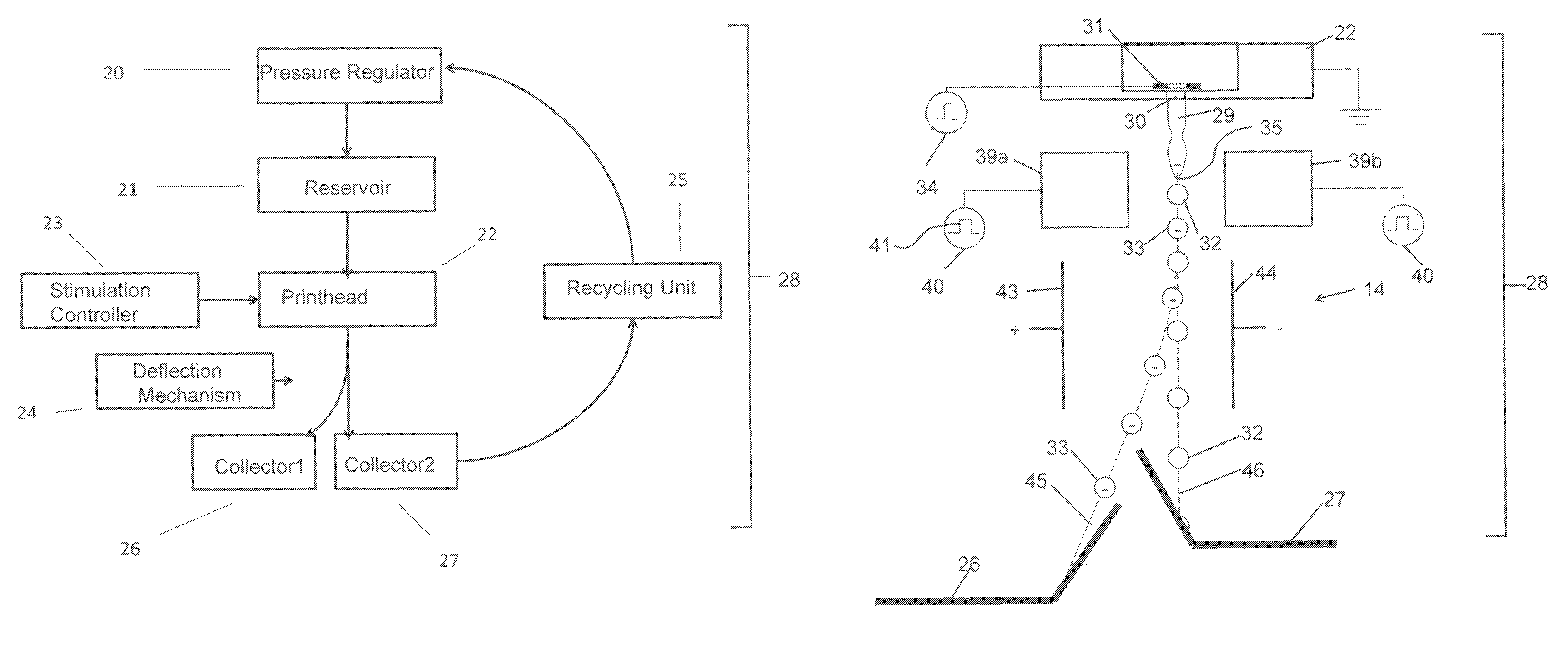
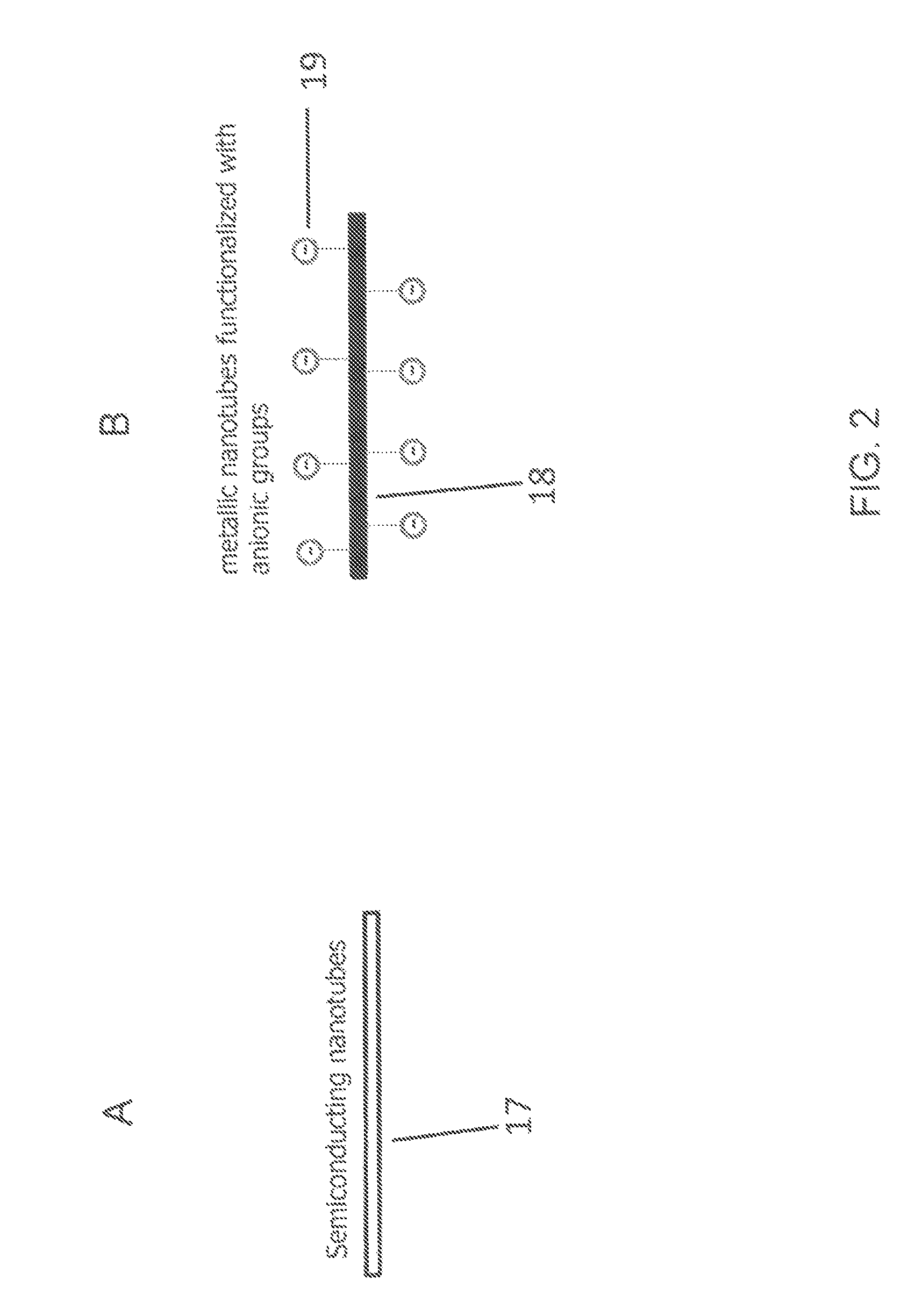
Metallic and semiconducting carbon nanotube sorting
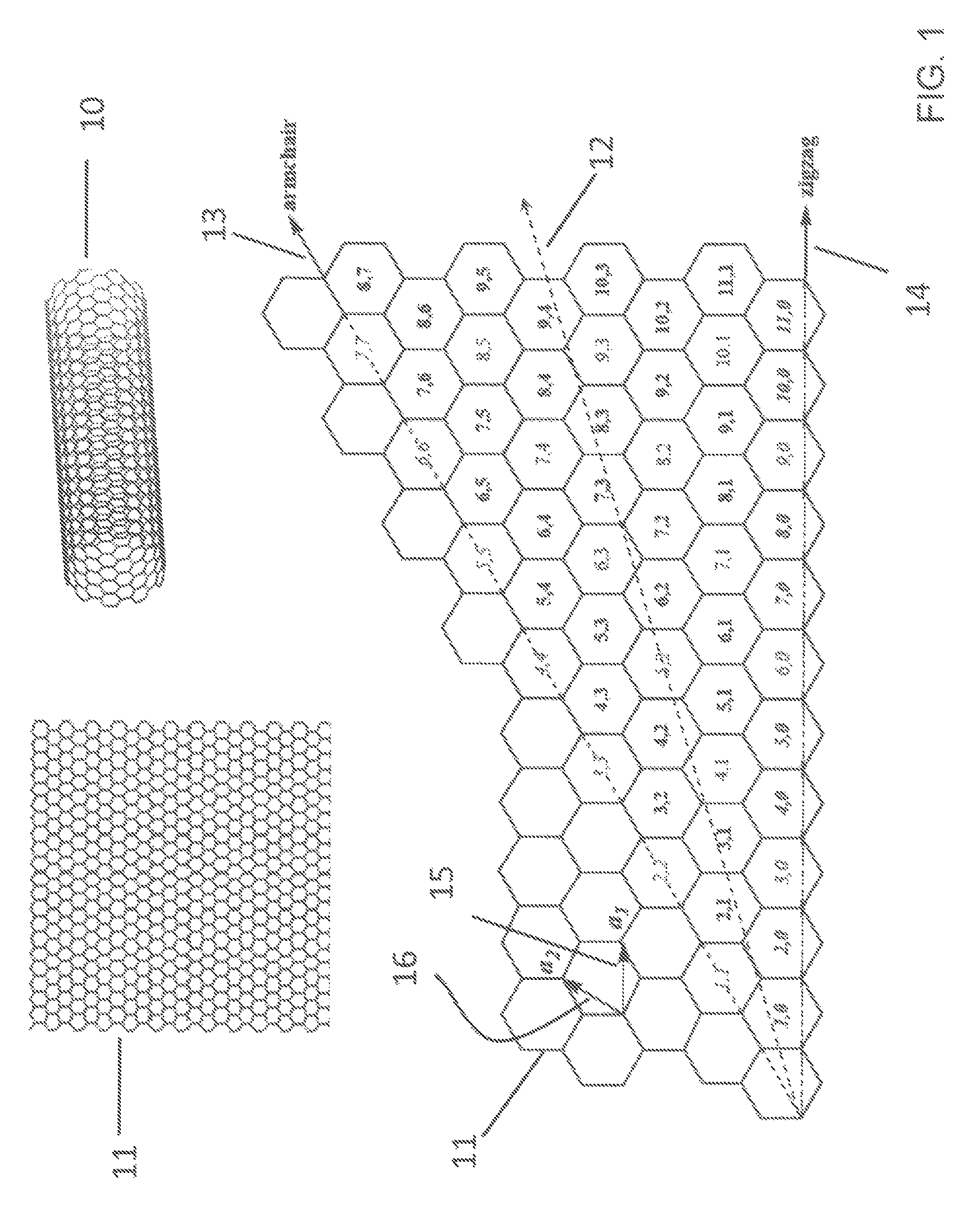
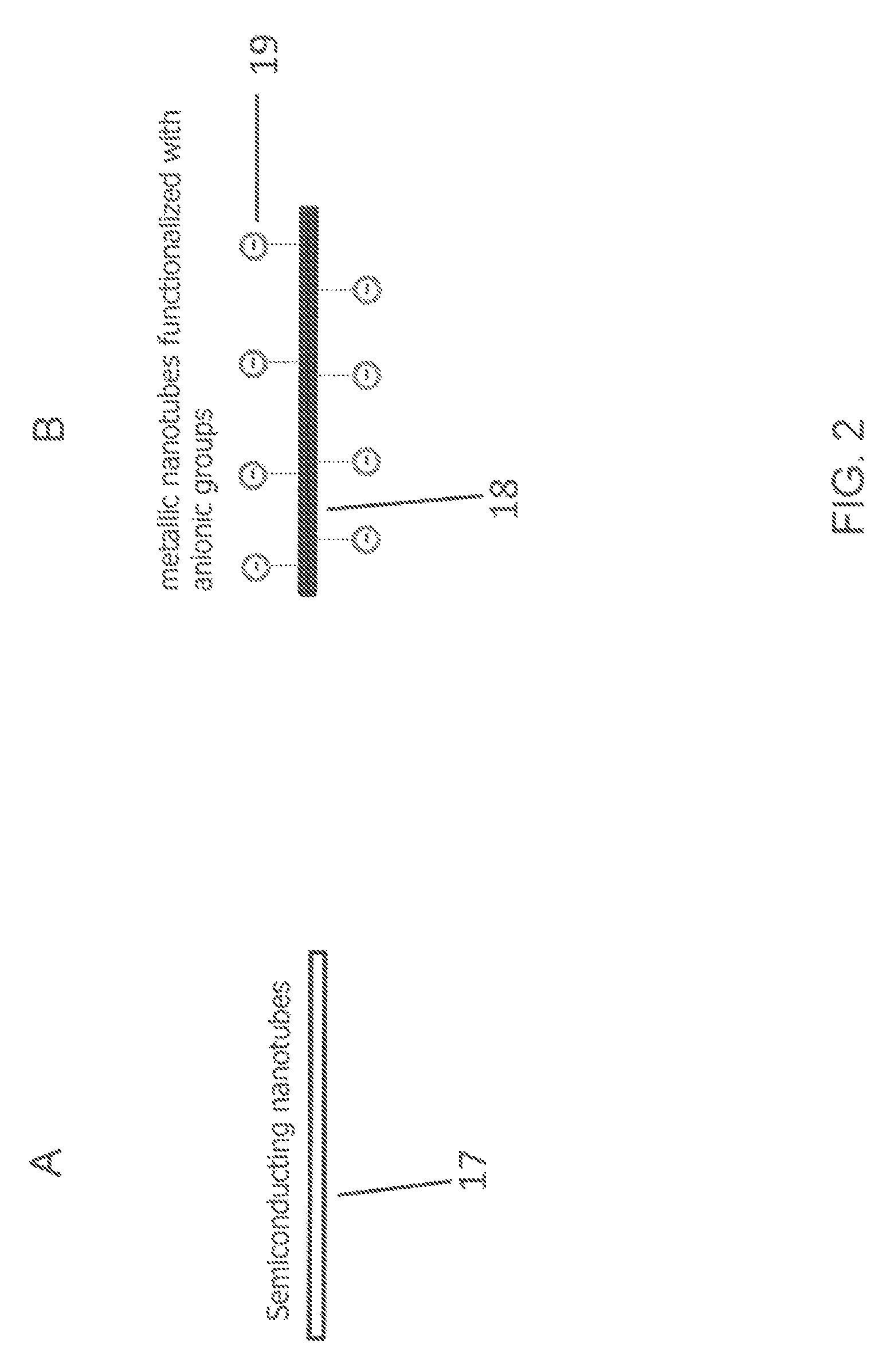
ActiveUS20140262972A1Fast and efficientReduce needElectrostatic separationMaterial analysis by electric/magnetic meansSpray nozzleElectric field
A method of separating metallic semiconducting carbon nanotubes includes providing a source of a mixture of semiconducting and metallic carbon nanotubes in a carrier liquid with one of the semiconducting and metallic carbon nanotubes being functionalized to carry a charge. The mixture is pressurized to cause a liquid jet of the mixture to be emitted through a nozzle. A drop formation mechanism modulates the liquid jet to form from the jet first and second drops traveling along a path. An electric field modulating device, positioned relative to the jet, produces first and second electric fields. A deflection device applies the first electric field as the first drop is formed to concentrate the functionalized carbon nanotubes in the first drop and applies the second electric field as the second drop is formed. The deflection device causes the first or second drop to begin traveling along another path.
Owner:EASTMAN KODAK CO
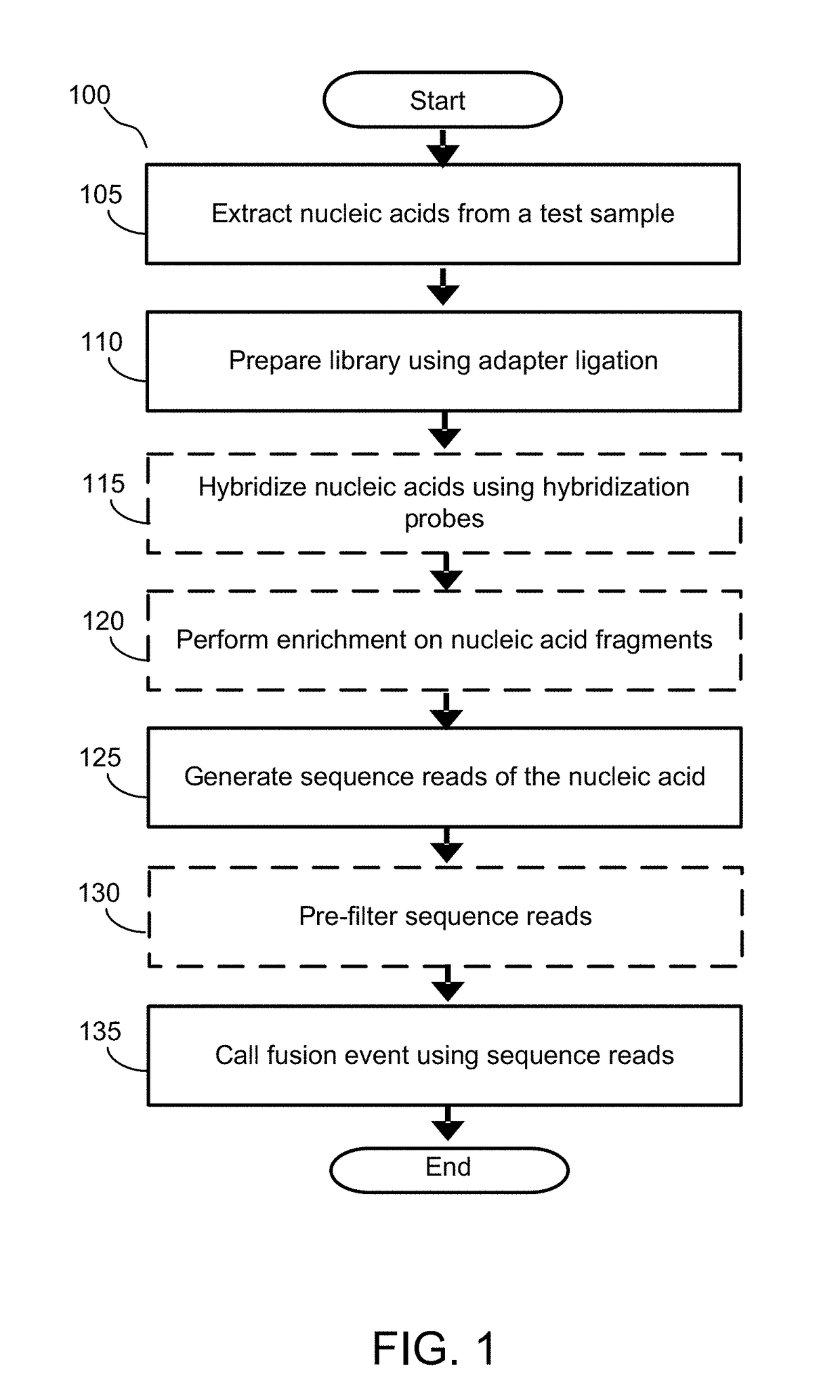
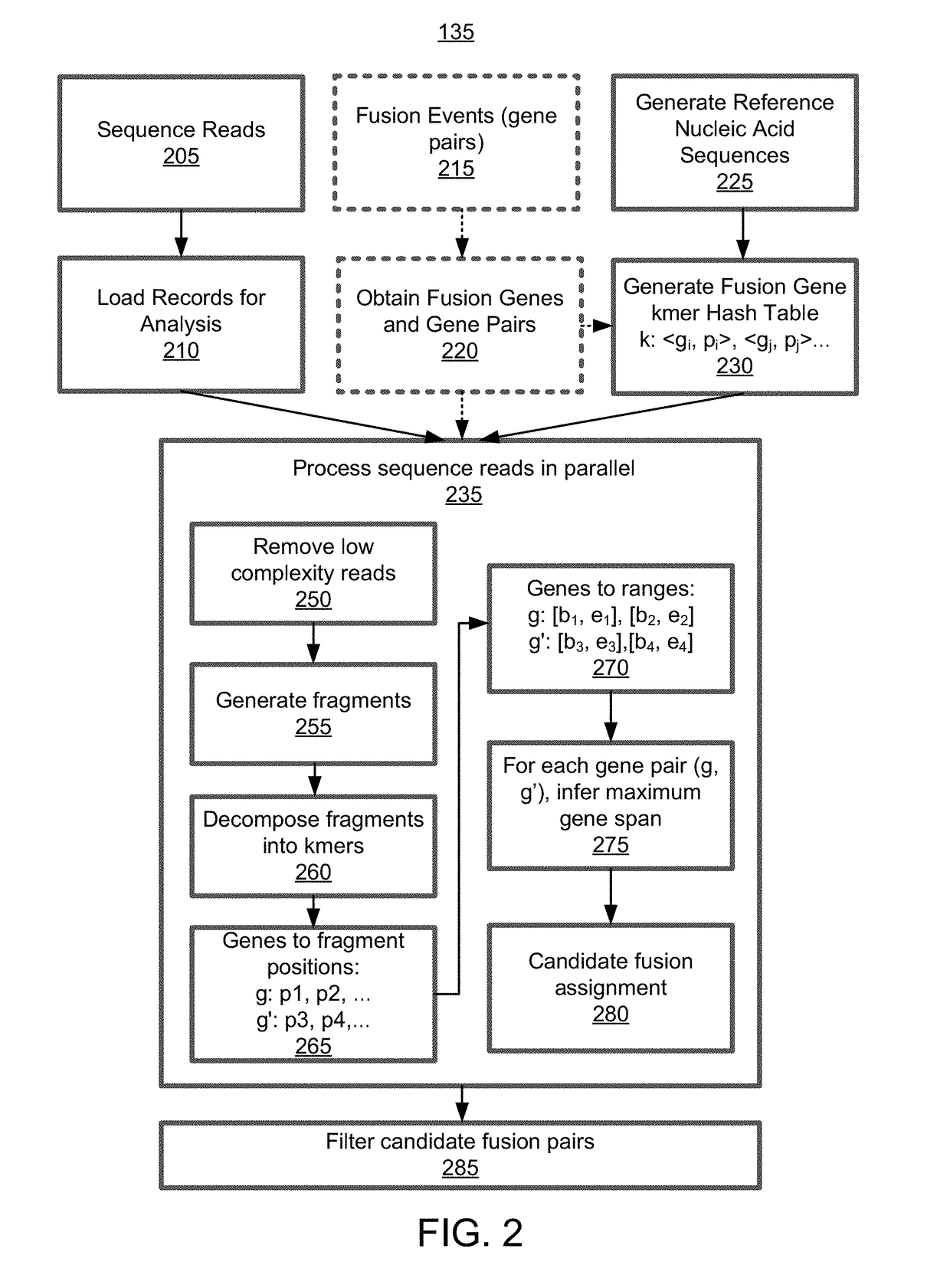
Alignment free filtering for identifying fusions
ActiveUS20180355423A1Efficient and scalableReduce computing costData visualisationBiostatisticsTest sampleNucleic acid sequencing
Cell free nucleic acids from a test sample obtained from an individual are analyzed to identify possible fusion events. Cell free nucleic acids are sequenced and processed to generate fragments. Fragments are decomposed into kmers and the kmers are either analyzed de novo or compared to targeted nucleic acid sequences that are known to be associated with fusion gene pairs of interest. Thus, kmers that may have originated from a fusion event can be identified. These kmers are consolidated to generate gene ranges from various genes that match sequences in the fragment. A candidate fusion event can be called given the spanning of one or more gene ranges across the fragment.
Owner:GRAIL LLC
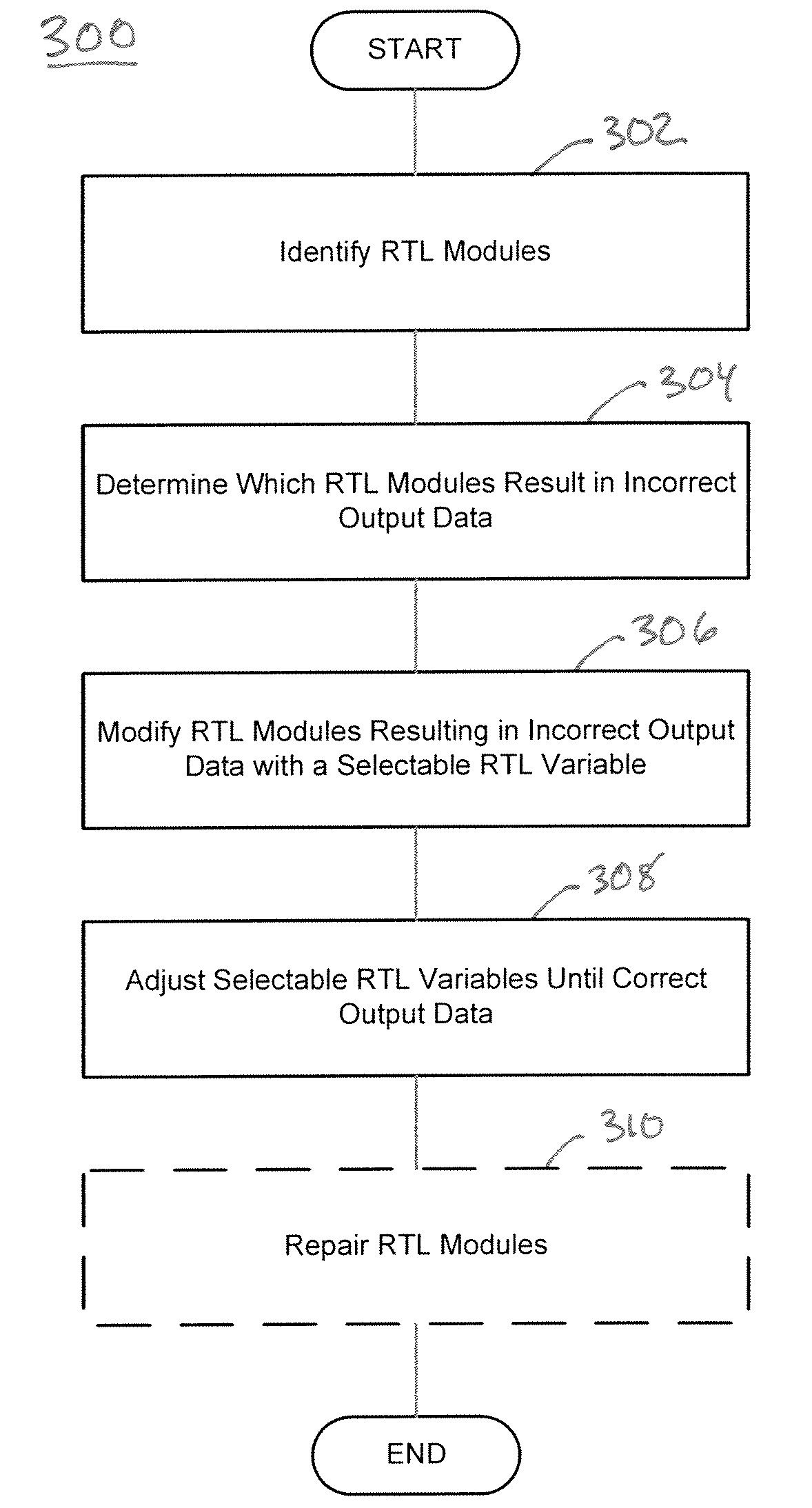
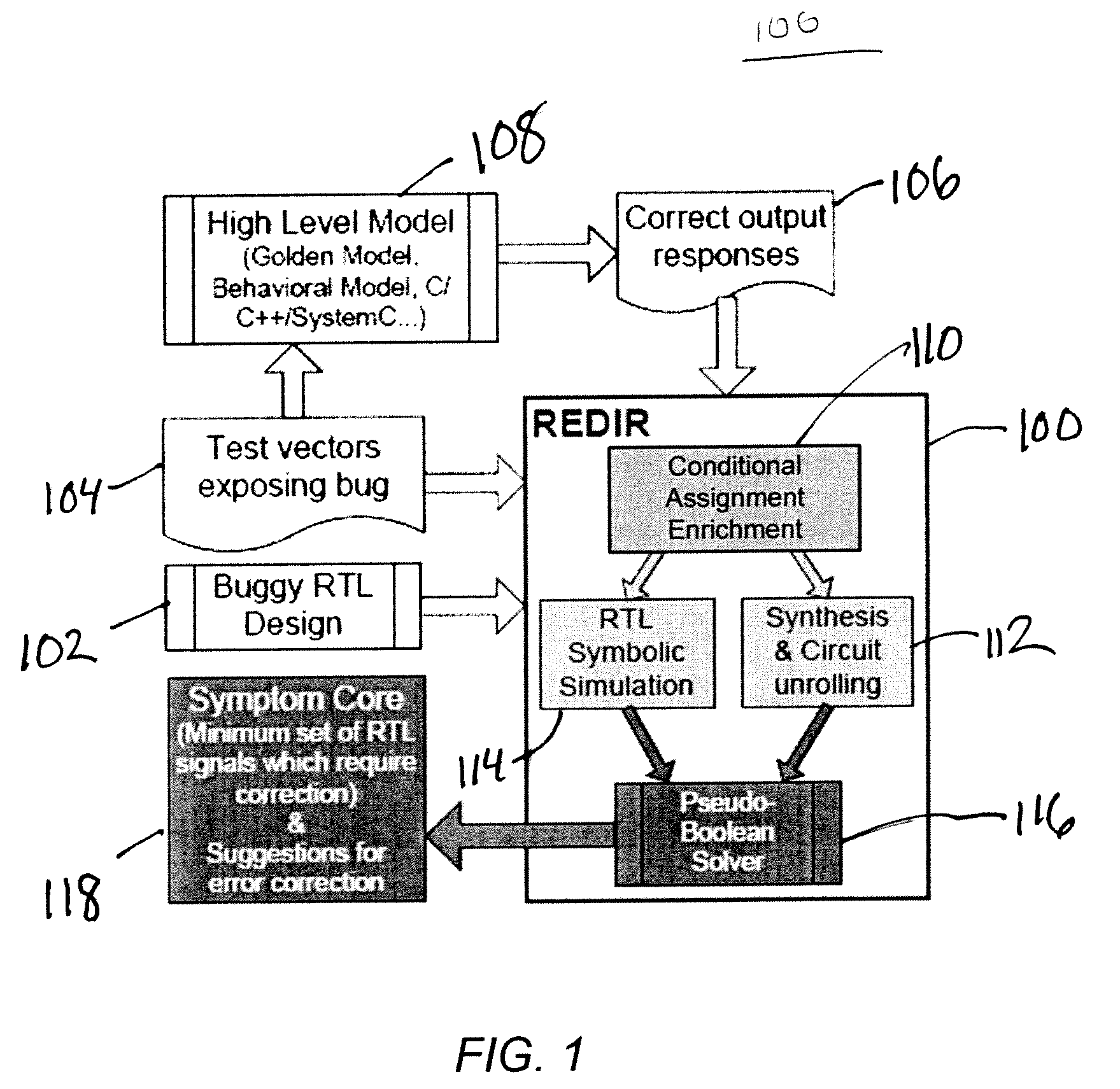
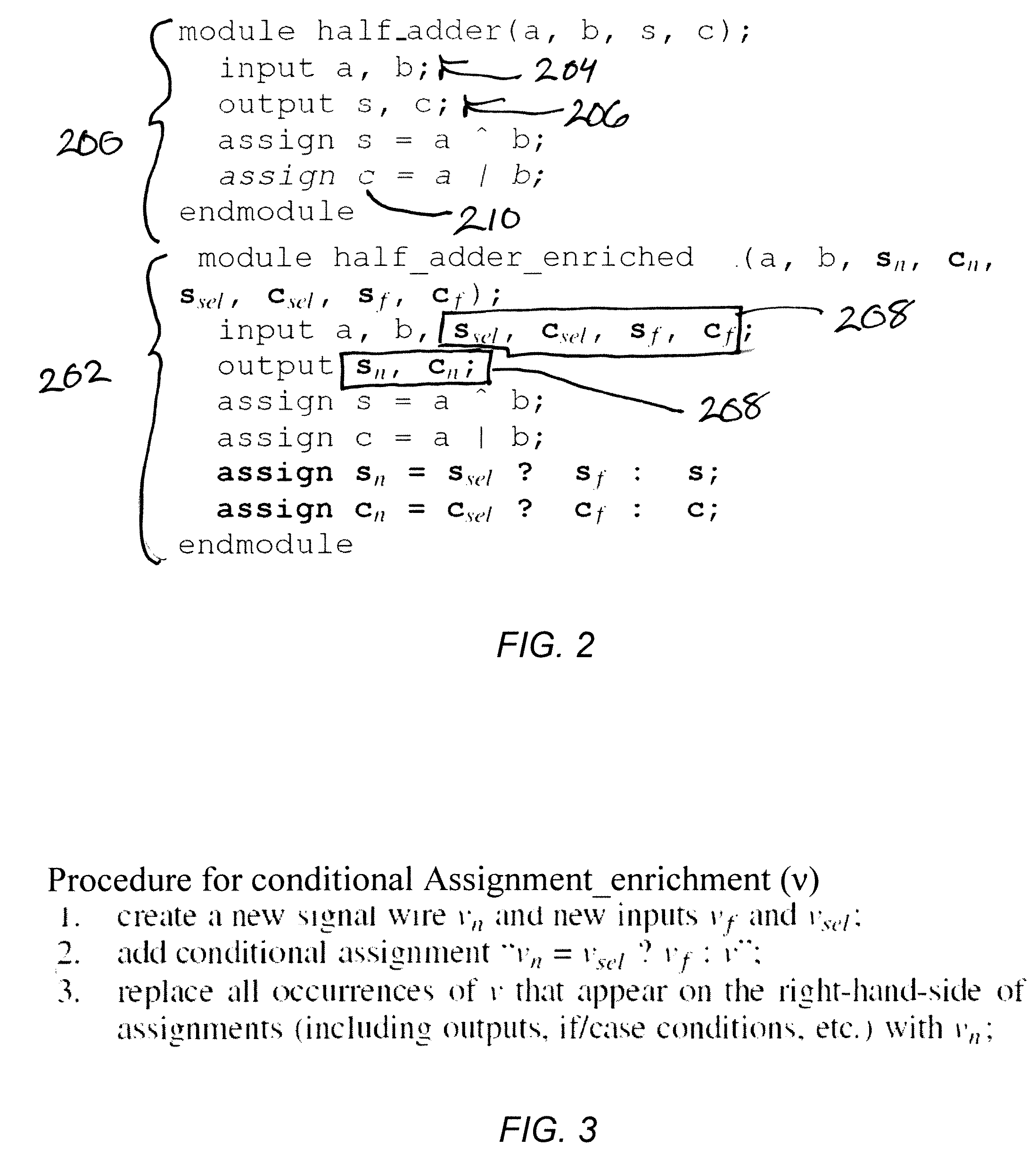
Automatic error diagnosis and correction for RTL designs
InactiveUS8365110B2Efficient and scalableEasy to debugComputer programmed simultaneously with data introductionCAD circuit designExtensibilityEngineering
A computer executable tool facilitates integrated circuit design and debugging by working directly at the Register Transfer Level, where most design activities take place. The tool determines when an integrated circuit design produces incorrect output responses for a given set of input vectors. The tool accesses the expected responses and returns the signal paths in the integrated circuit that are responsible for the errors along with suggested changes for fixing the errors. The tool may operate at the RTL, which is above the gate-level abstraction which means that the design errors will be much more readily understood to the designer, and may improve scalability and efficiency.
Owner:RGT UNIV OF MICHIGAN
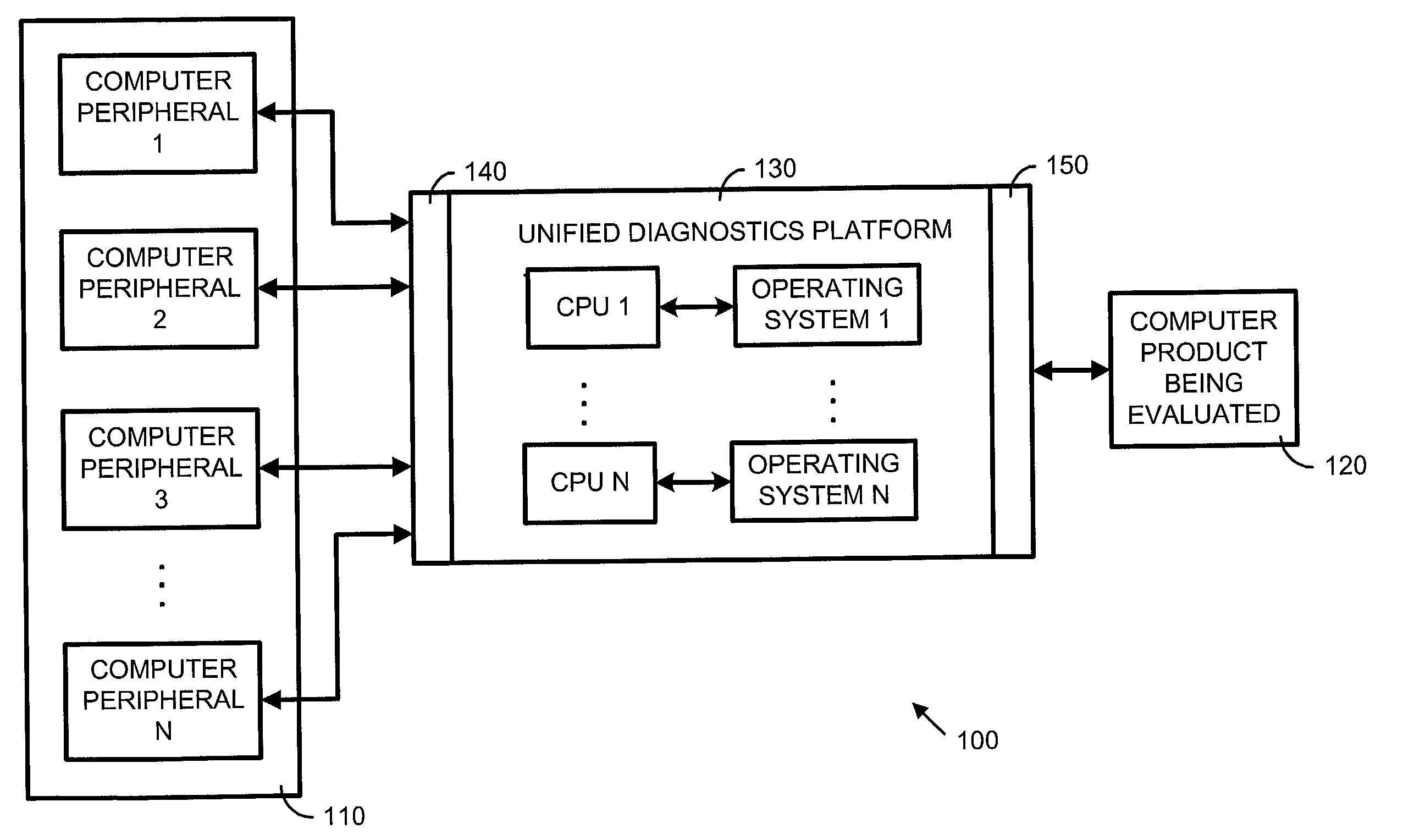
Unified diagnostics platform system and method for evaluating computer products
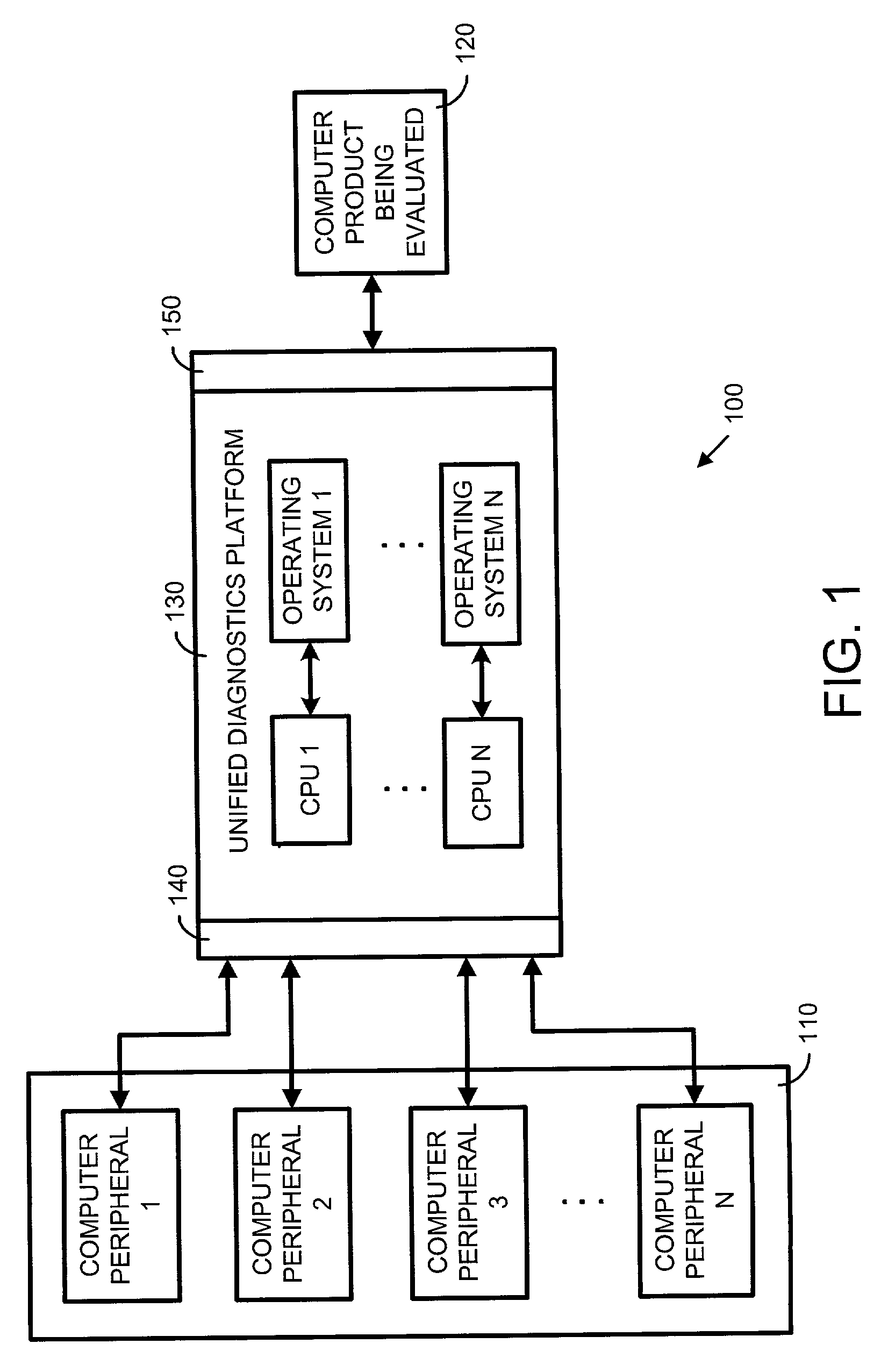
InactiveUS6980947B2Eliminate duplicationReduce duplicationNuclear monitoringDigital computer detailsAssessment methodsPeripheral
An evaluation system and method for computer products that uses a unified diagnostics platform having a switching multiplexor to generate a plurality of computer systems and computer environments. The evaluation system of the present invention includes a unified diagnostics platform that facilitates a variety of different computer systems by connecting computer peripherals, processors and operating systems. The switching multiplexor may be a plurality of switches allowing multiple combinations and configurations of devices connected to the unified diagnostics platform. The switching multiplexor is controlled using a controller that may be a hardware or a software selector. The evaluation method of the present invention includes a method for evaluating a computer product on a plurality of computer systems using the unified diagnostics platform.
Owner:IBM CORP
Methods for producing preparations of recombinant AAV virions substantially free of empty capsids
ActiveUS20050042740A1Reduce the amount requiredEfficient and scalableSsRNA viruses negative-senseCeramic shaping apparatusBiotechnologyCapsid
Methods for separating AAV empty capsids from mixtures of AAV vector particles and AAV empty capsids are described. The methods use column chromatography techniques and provide for commercially viable levels of recombinant AAV virions.
Owner:GENZYME CORP
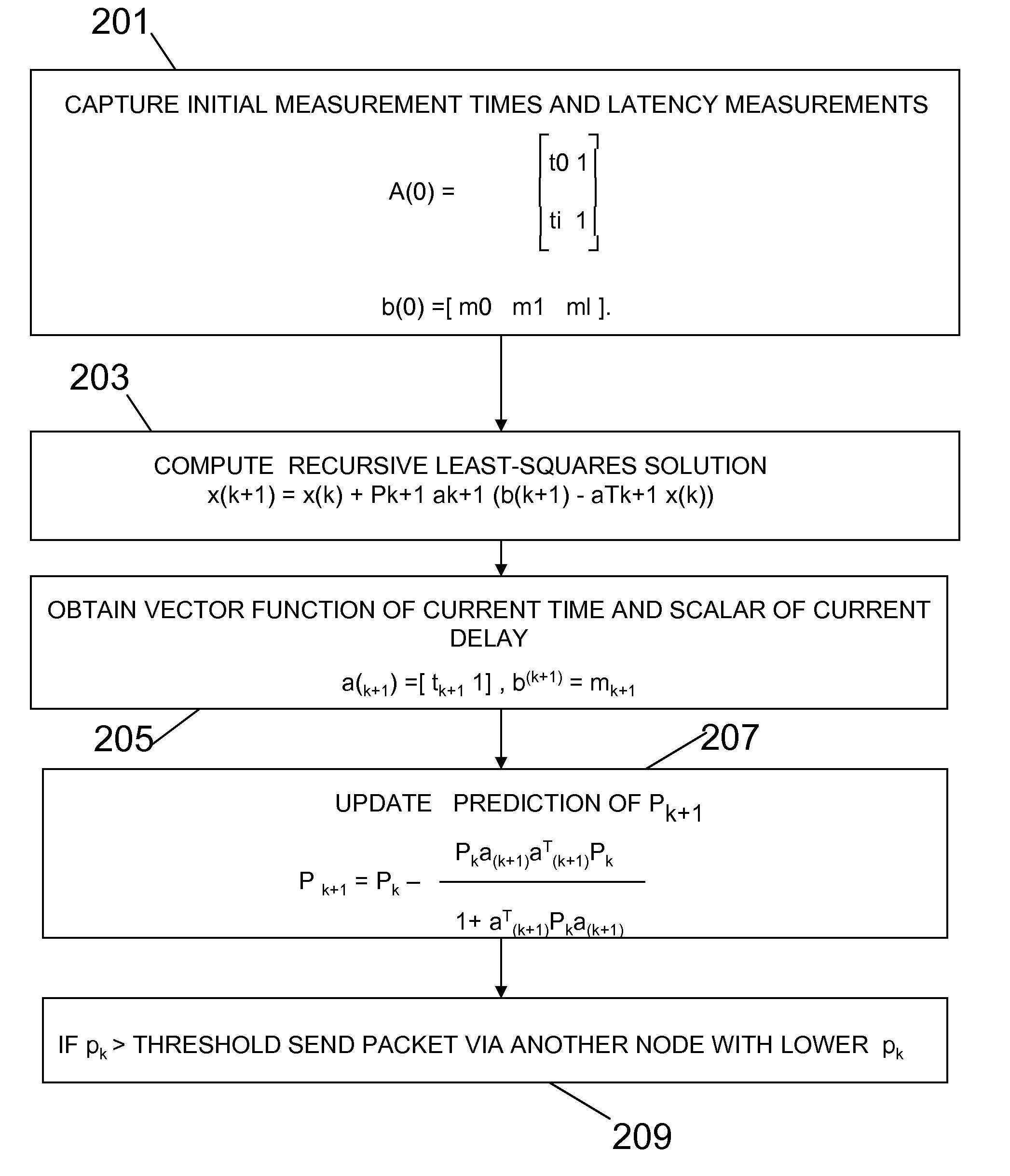
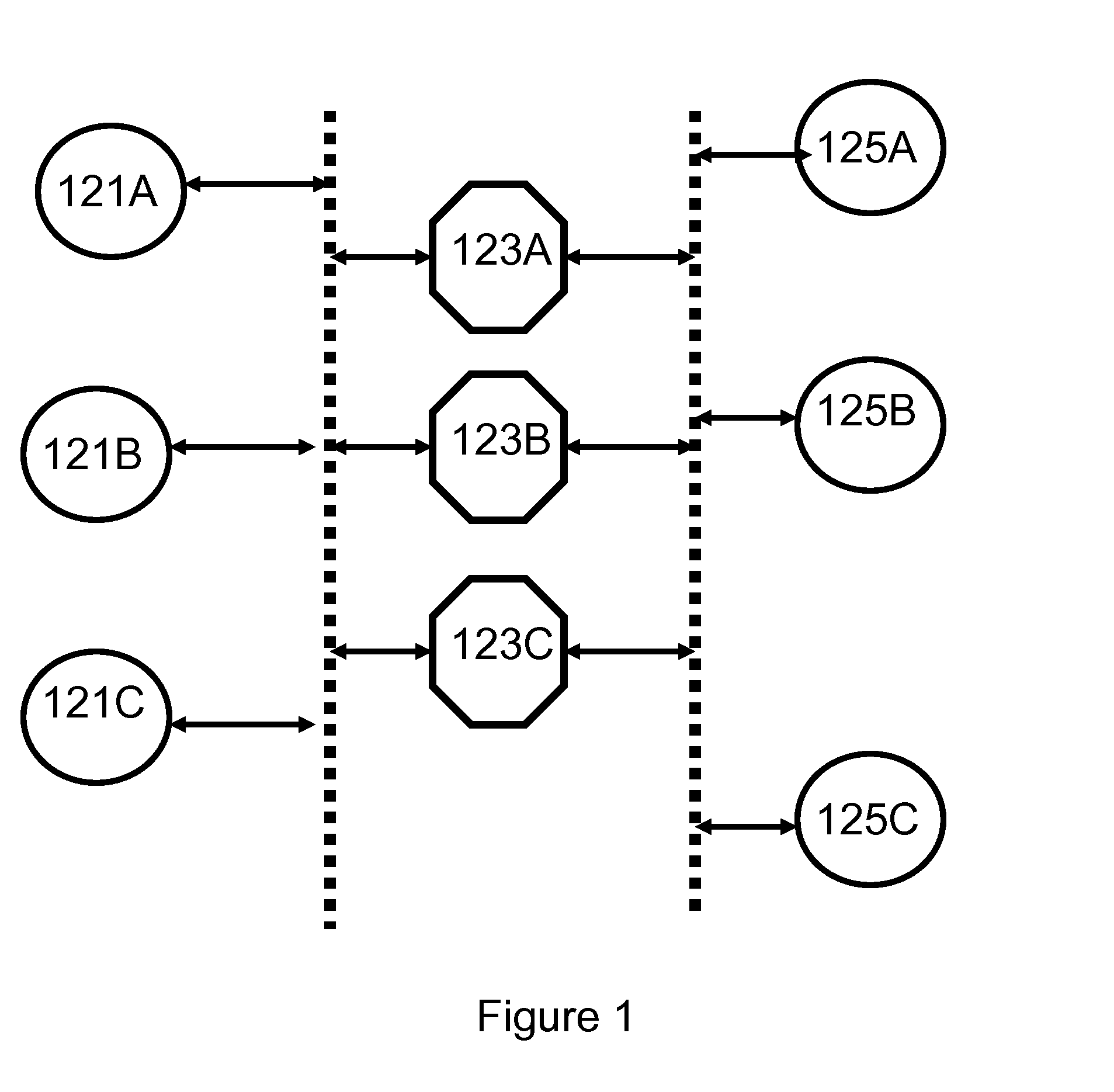
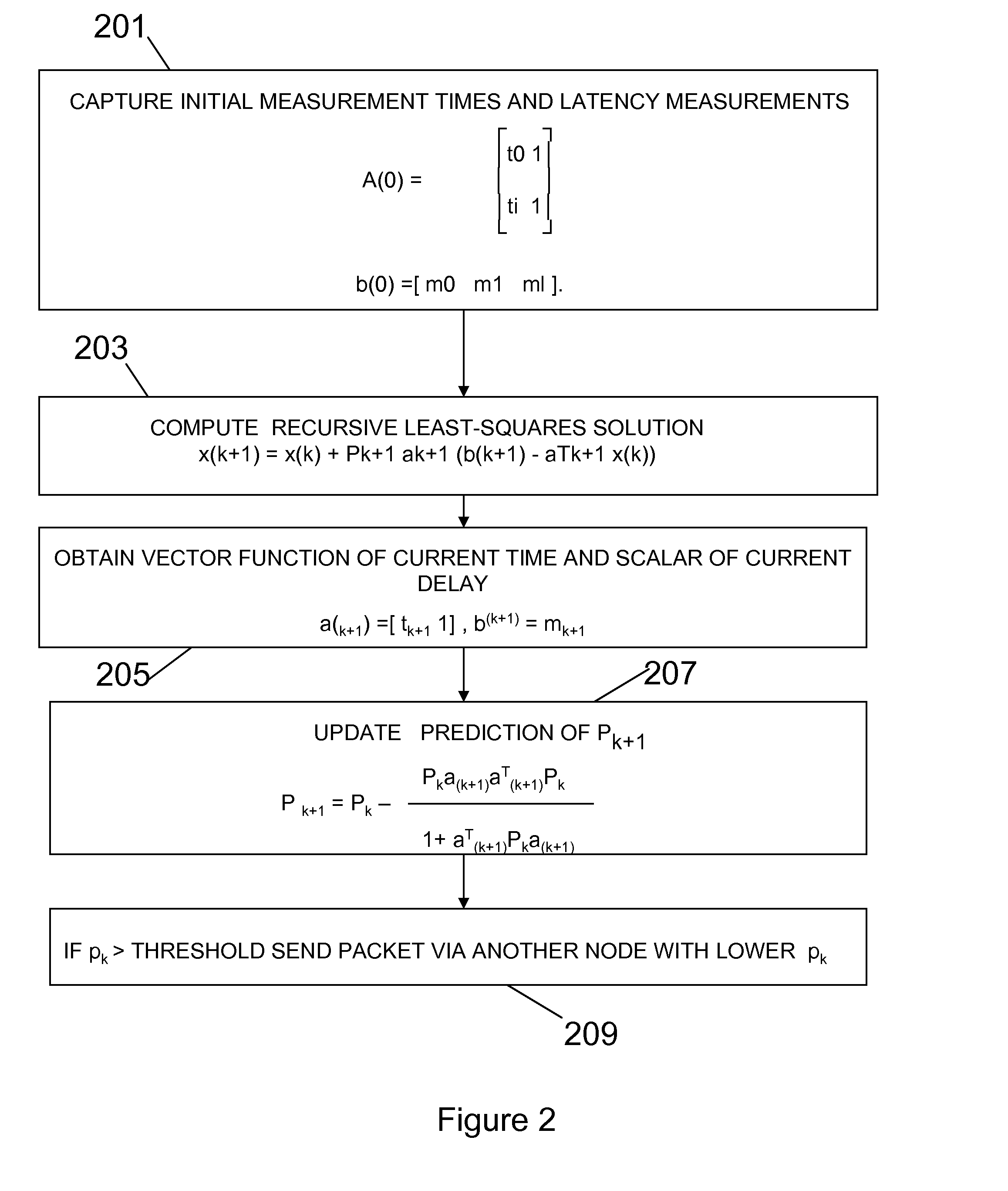
Distributed message routing in a virtualized messaging system using recursive least squares links cost estimation with choke points
ActiveUS20080137546A1Minimize message latencyEfficient and scalableError preventionFrequency-division multiplex detailsMessage routingEngineering
Routing data packet traffic in packet networks, expediting the flow of the data packets and reducing the effects of congestion at nodes is accomplished by capturing latency data for nodes for initial measurement times; and computing a least squares estimate of the delay as a recursive least-squares solution.
Owner:TWITTER INC
Scalable and flexible internet fax architecture for processing outbound fax messages
ActiveUS20130223602A1Efficient and scalableData switching networksPictoral communicationModem deviceWorld Wide Web
Methods and systems for processing outbound fax messages in an efficient and scalable manner are provided. According to one embodiment, an Internet fax system receives a request to deliver a fax message. Source files representing content to be included as part of the fax message are stored to a shared storage area accessible by imaging systems and fax processing resources. An imaging system is selected to convert the source files into a digital representation suitable for faxing. A work request identifying the selected imaging system is stored on a centralized work queue within a database. The imaging systems poll the centralized work queue to retrieve pending work requests. Responsive to identifying the work request, the selected imaging system converts the source files, associates the resulting digital representation with an outbound fax job and causes the fax message to be delivered by submitting the outbound fax job to a fax modem.
Owner:J2 CLOUD SERVICES LLC
Apparatus and method for a continuous rapid thermal cycle system
ActiveUS8293471B2Low production costEfficient and scalableBioreactor/fermenter combinationsBiological substance pretreatmentsTemperature controlAmplification dna
A thermal cycle system and method suitable for mass production of DNA comprising a temperature control body having at least two sectors. Each sector has at least one heater, cooler, or other means for changing temperature. A path traverses the sectors in a cyclical fashion. In use, a piece of tubing or other means for conveying is placed along the path and a reaction mixture is pumped or otherwise moved along the path such that the reaction mixture is repetitively heated or cooled to varying temperatures as the reaction mixture cyclically traverses the sectors. The reaction mixture thereby reacts to form a product. In particular, polymerase chain reaction reactants may continuously be pumped through the tubing to amplify DNA. The temperature control body is preferably a single aluminum cylinder with a grooved channel circling around its exterior surface, and preferably has wedge-shaped or pie-shaped sectors separated by a thermal barrier.
Owner:MARSHALL UNIV RES
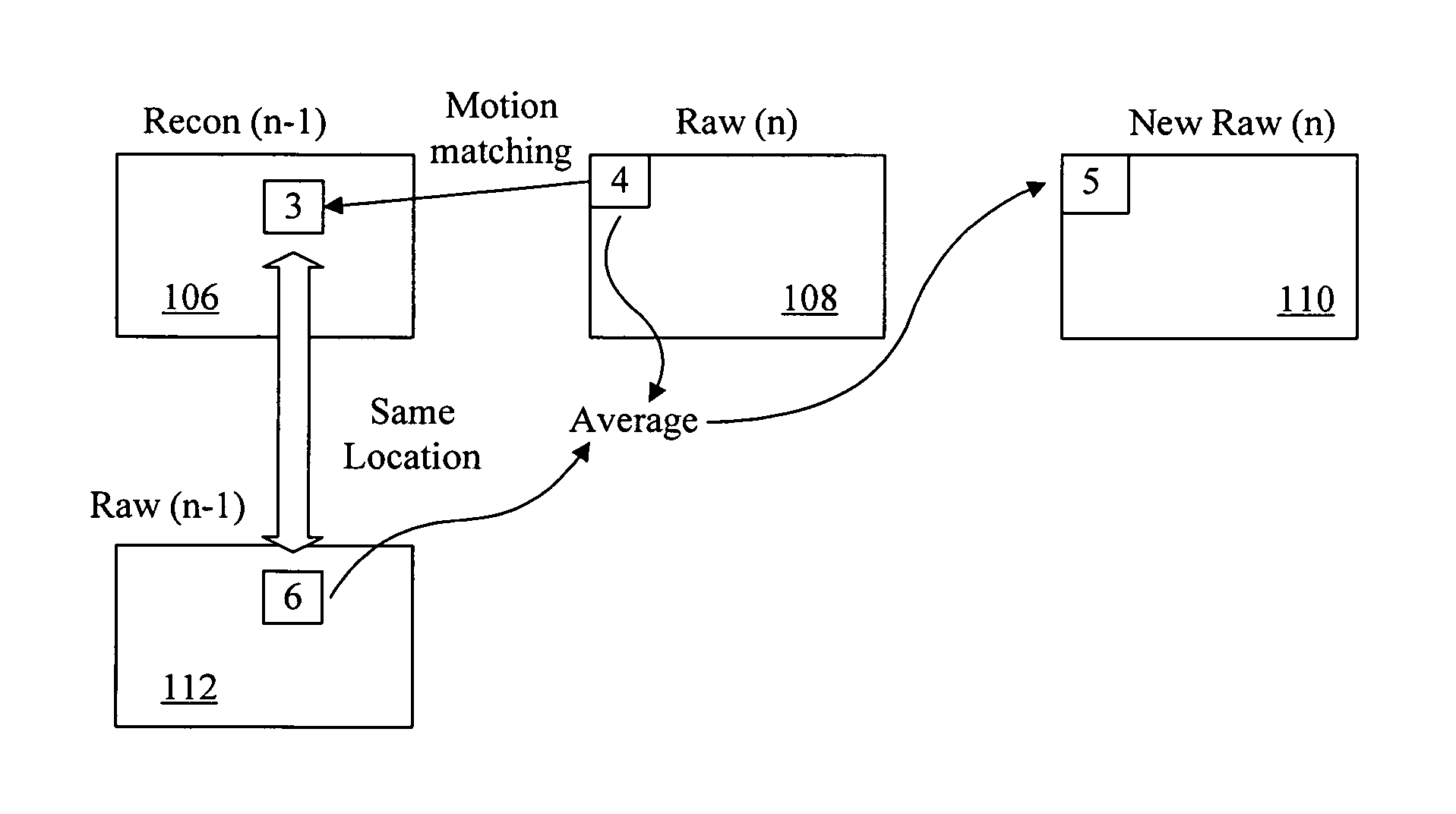
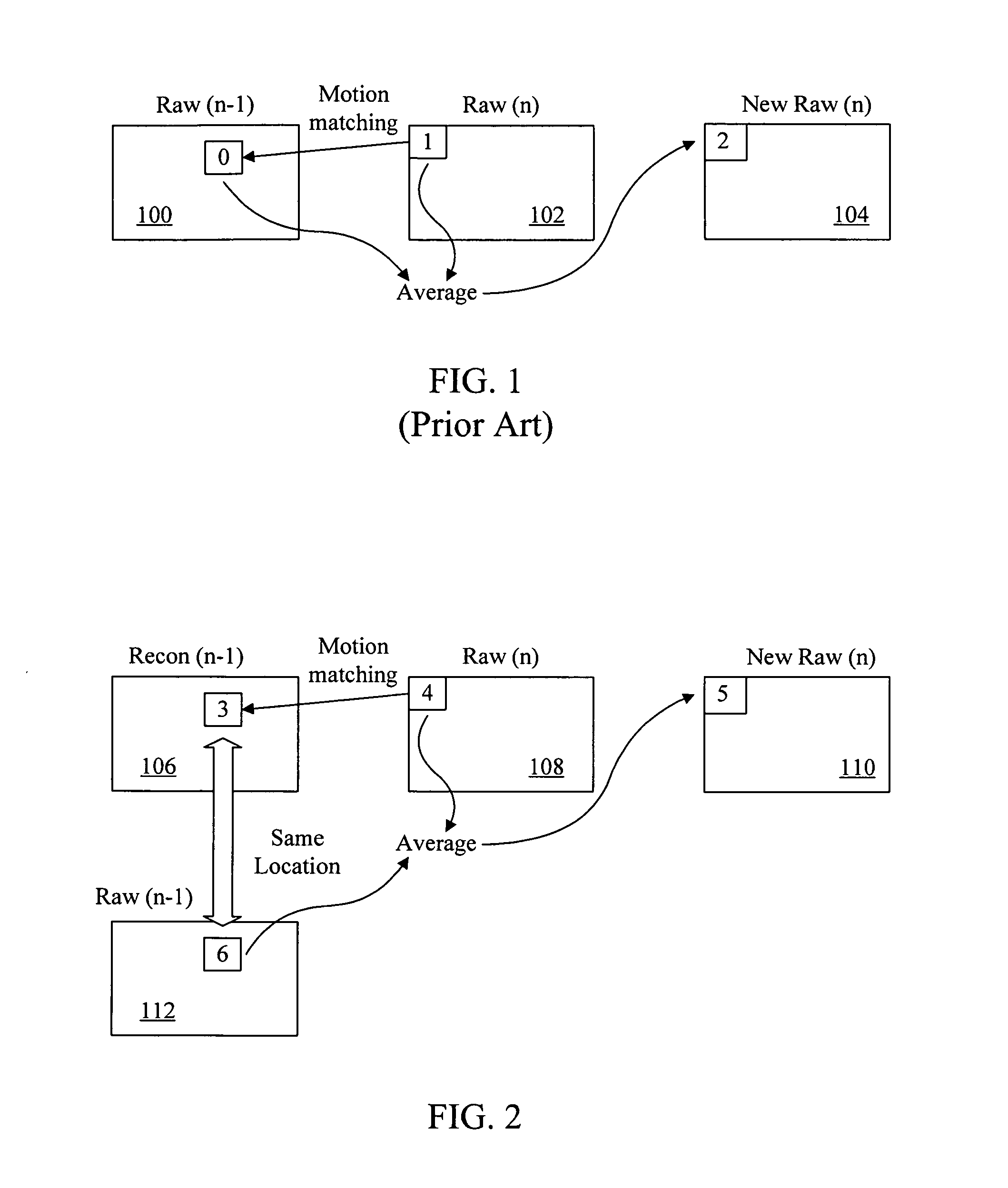
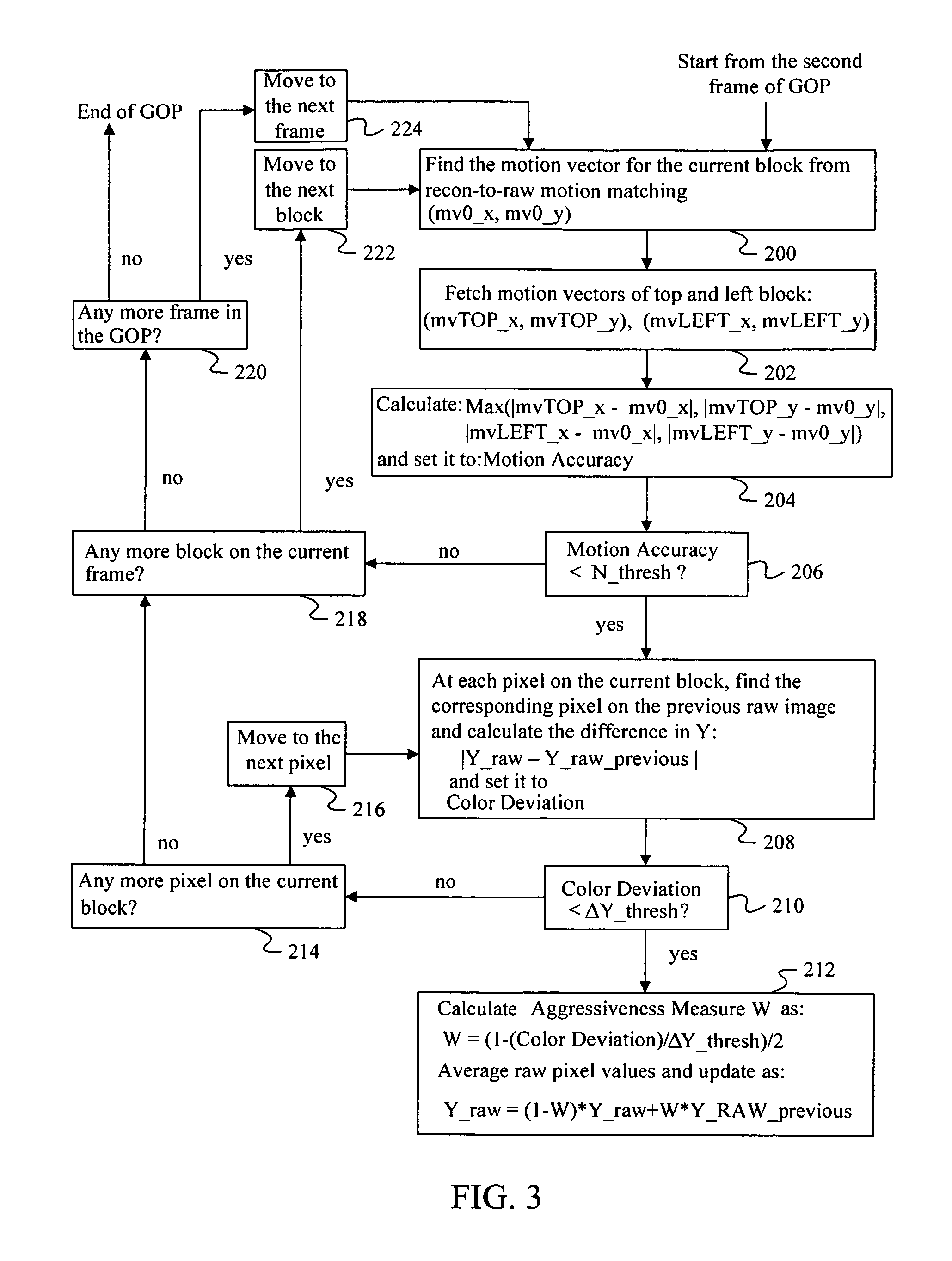
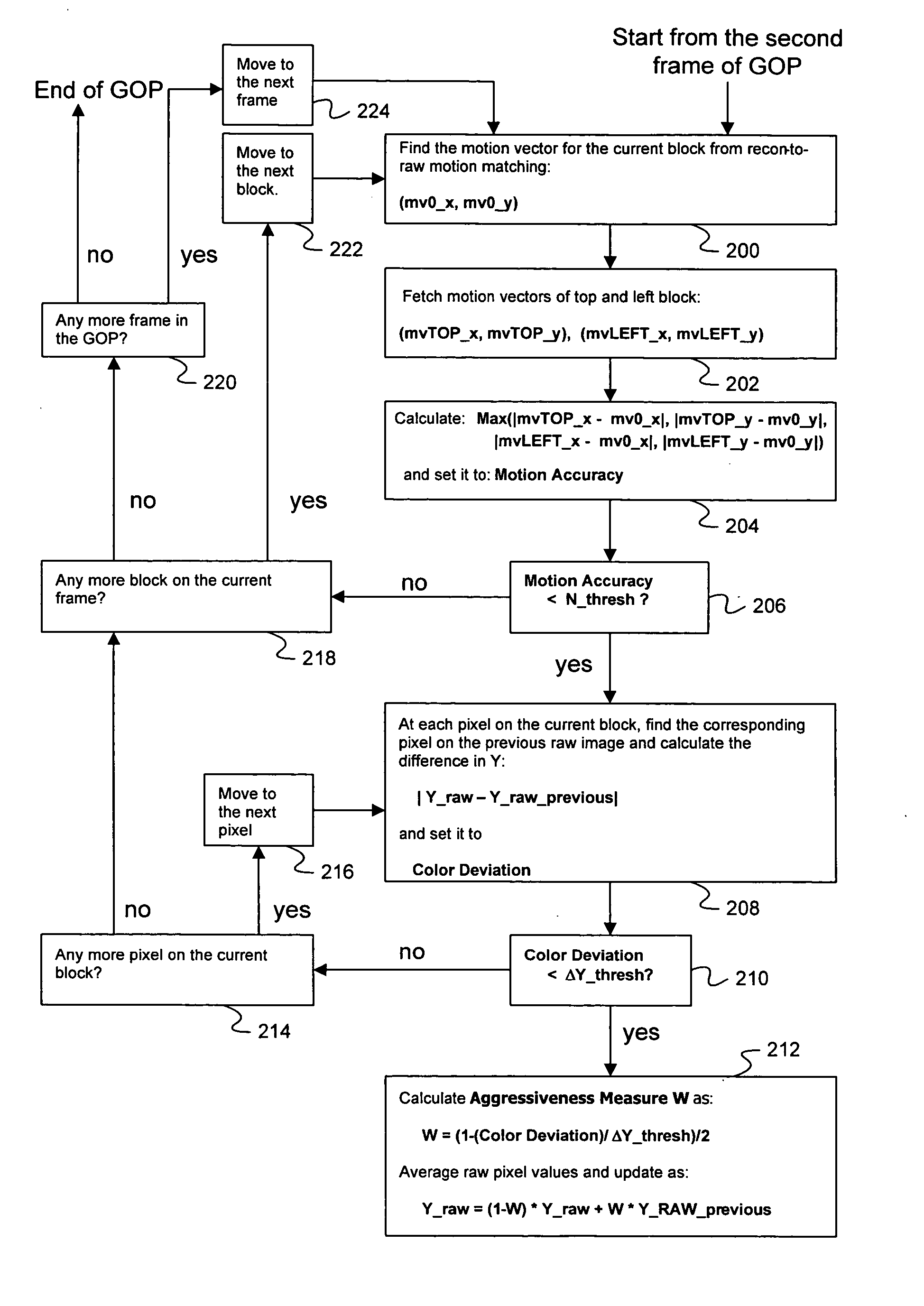
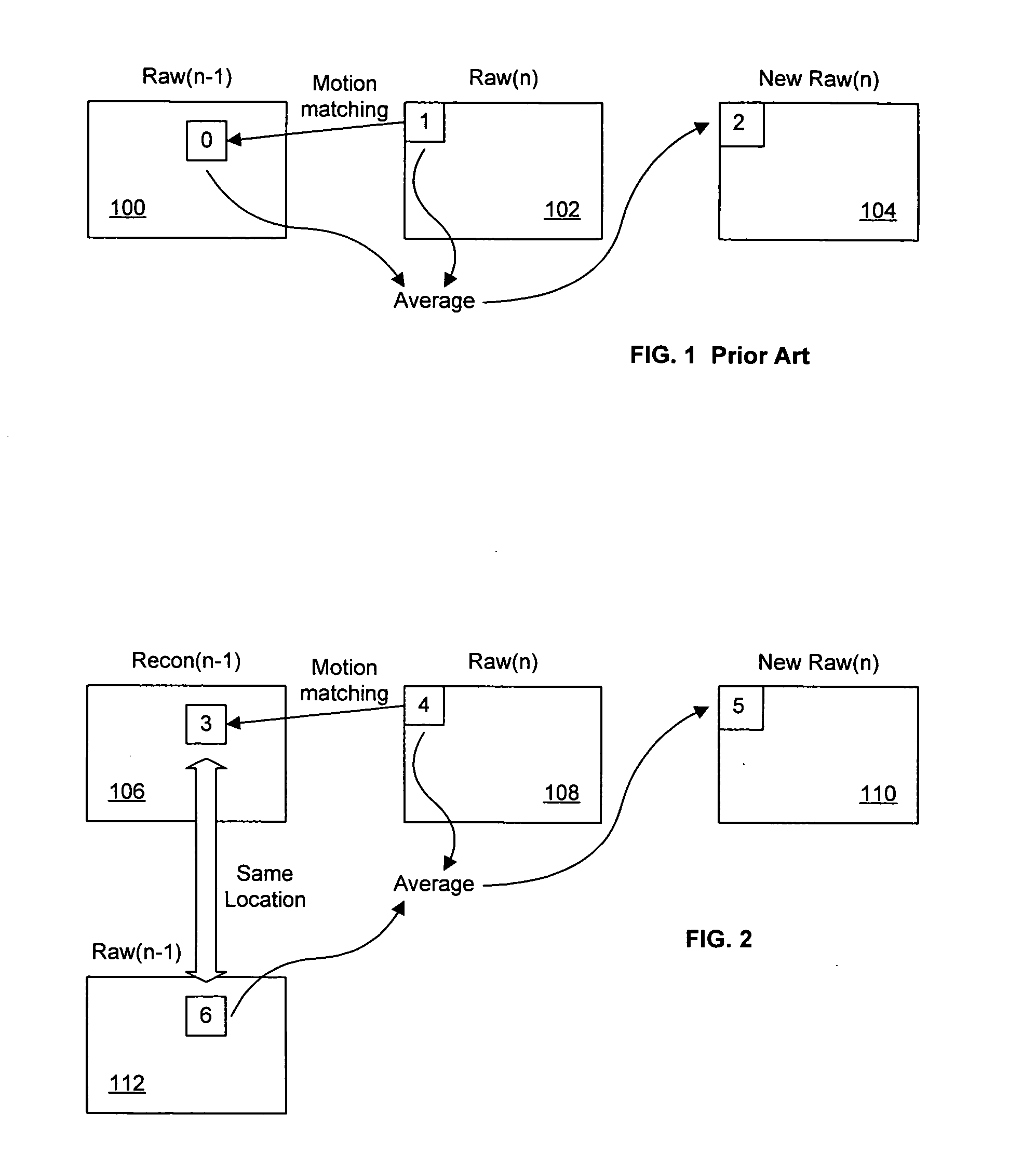
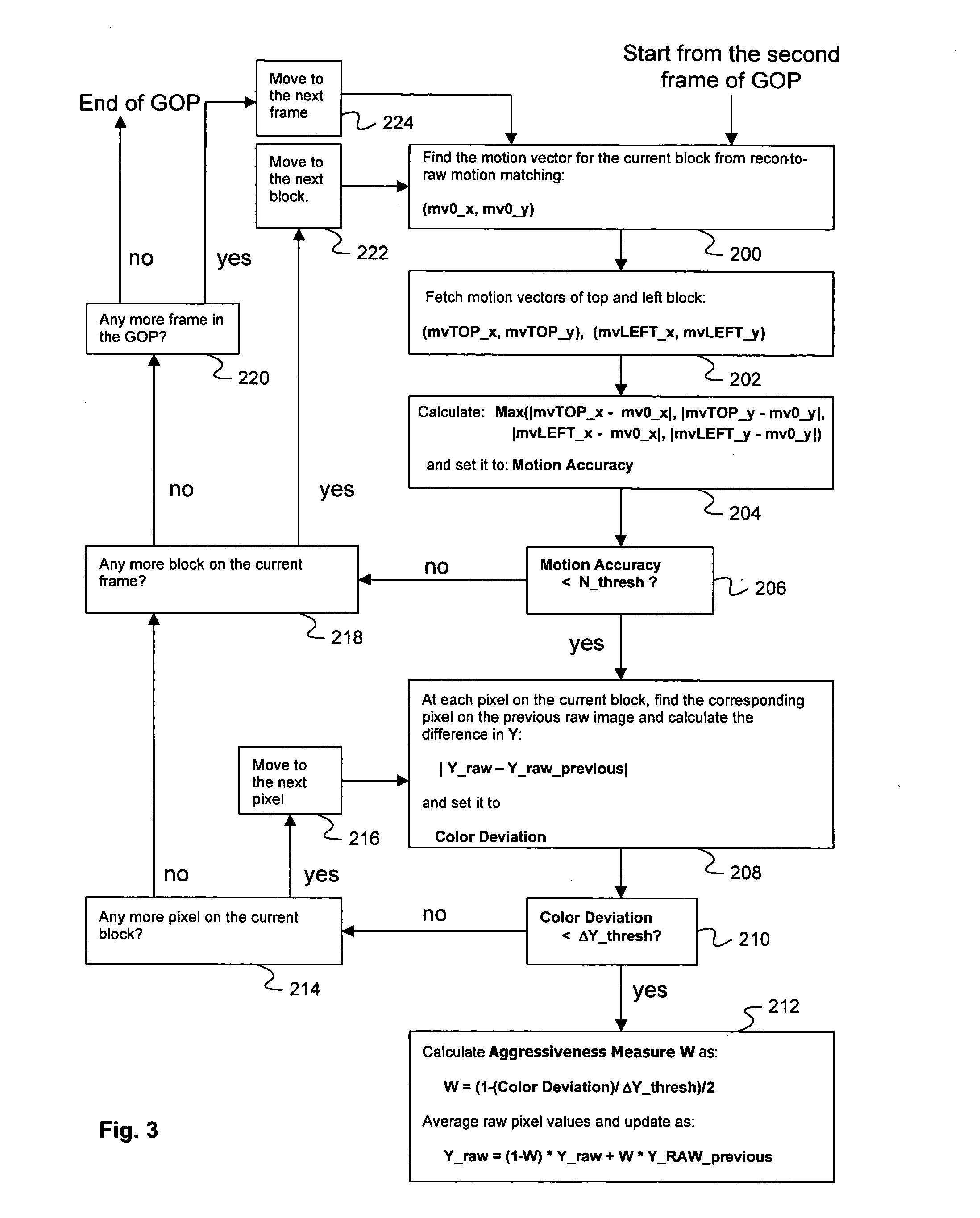
Image flow knowledge assisted latency-free in-loop temporal filter
InactiveUS20100272182A1Minimize temporal noiseEfficient and scalableTelevision system detailsColor television with pulse code modulationTemporal filterCMOS sensor
Digital image acquisition device such as CCD / CMOS sensors often introduces random temporal noise into digital video sequences. Temporal noise generally carries high frequency components in both the spatial and temporal domains and is also random in nature. Because of these properties, they are generally very expensive to encode and would substantially degrade coding efficiency. It is therefore important to eliminate or suppress such temporal noise in video inputs prior to encoding. The present invention provides a methodology to achieve such a goal in a highly cost-effective manner where coding performance, latency, computational cost, and memory requirements are optimized. This methodology can be efficiently implemented as part of digital video compression algorithm and scales nicely for various bitrates.
Owner:SIGMA DESIGNS
Image flow knowledge assisted latency-free in-loop temporal filter
InactiveUS20050286638A1Noise minimizationEfficient and scalableTelevision system detailsColor television with pulse code modulationDigital videoCMOS sensor
Digital image acquisition device such as CCD / CMOS sensors often introduces random temporal noise into digital video sequences. Temporal noise generally carries high frequency components in both the spatial and temporal domains and is also random in nature. Because of these properties, they are generally very expensive to encode and would substantially degrade coding efficiency. It is therefore important to eliminate or suppress such temporal noise in video inputs prior to encoding. The present invention provides a methodology to achieve such a goal in a highly cost-effective manner where coding performance, latency, computational cost, and memory requirements are optimized. This methodology can be efficiently implemented as part of digital video compression algorithm and scales nicely for various bitrates.
Owner:QUANTA INT
System and method for large-scale and near-real-time search of mobile device locations in arbitrary geographical boundaries
ActiveUS8868106B2Efficient and scalableUnauthorised/fraudulent call preventionEavesdropping prevention circuitsLine searchReal-time Search
A system and method for generating a one-dimensional spatial index and a temporal index in relation to one or more two-dimensional location points of one or more mobile devices to enable near-real-time searching of devices having fast-changing location information is provided for. The present invention may be used in a variety of implementations including being used in conjunction with searching for mobile devices within a geographical area for a time period; finding nearby devices within a time period; tracking device movement within a time period; determining clusters of devices for identification and location across different geographical regions at once.
Owner:AERIS COMM
Cloud-based build service
ActiveUS8635607B2Highly available and dynamically scalable and efficient build serviceExcess capacityVersion controlSoftware simulation/interpretation/emulationCloud baseScalable distributed
Owner:MICROSOFT TECH LICENSING LLC
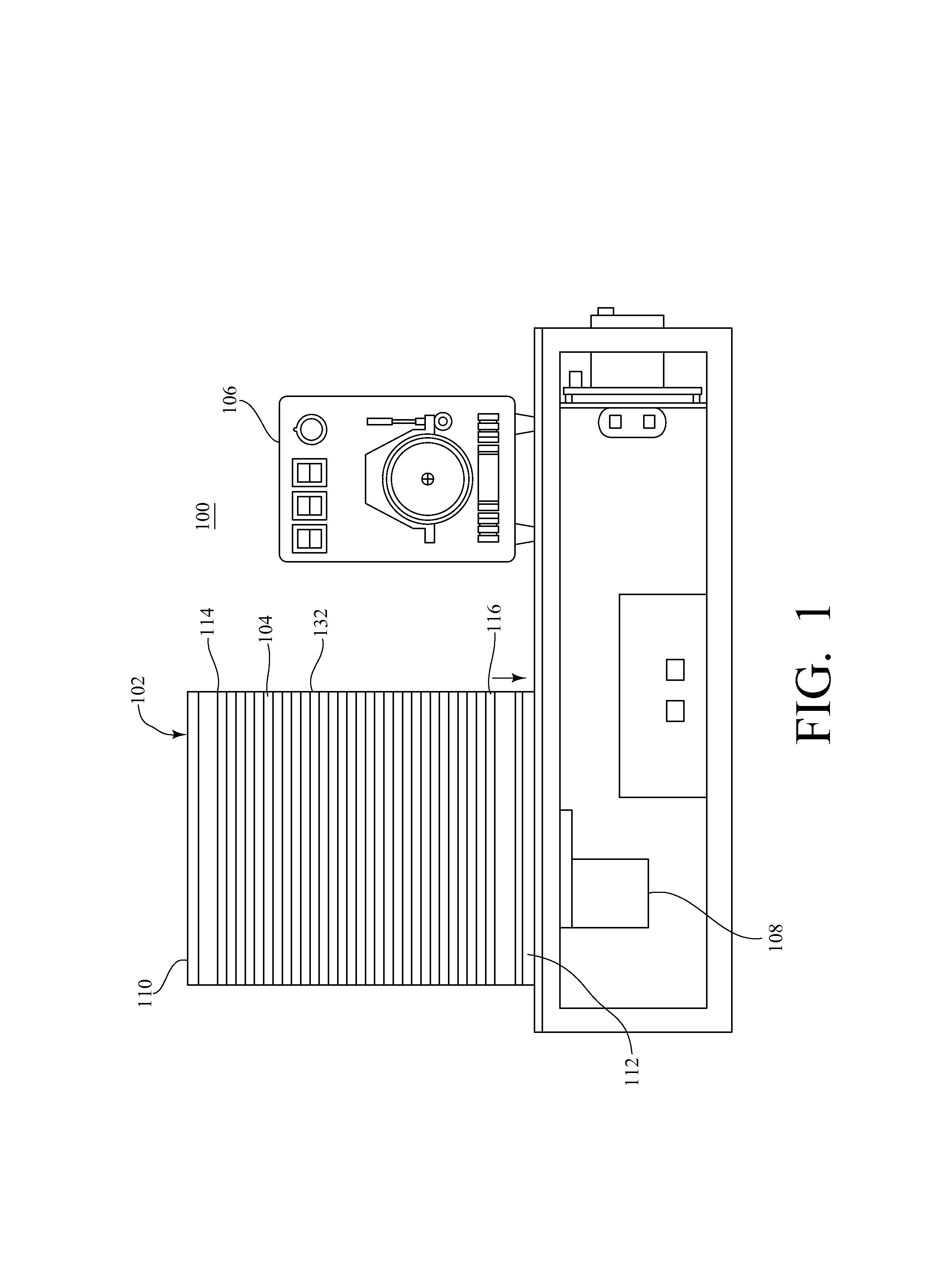
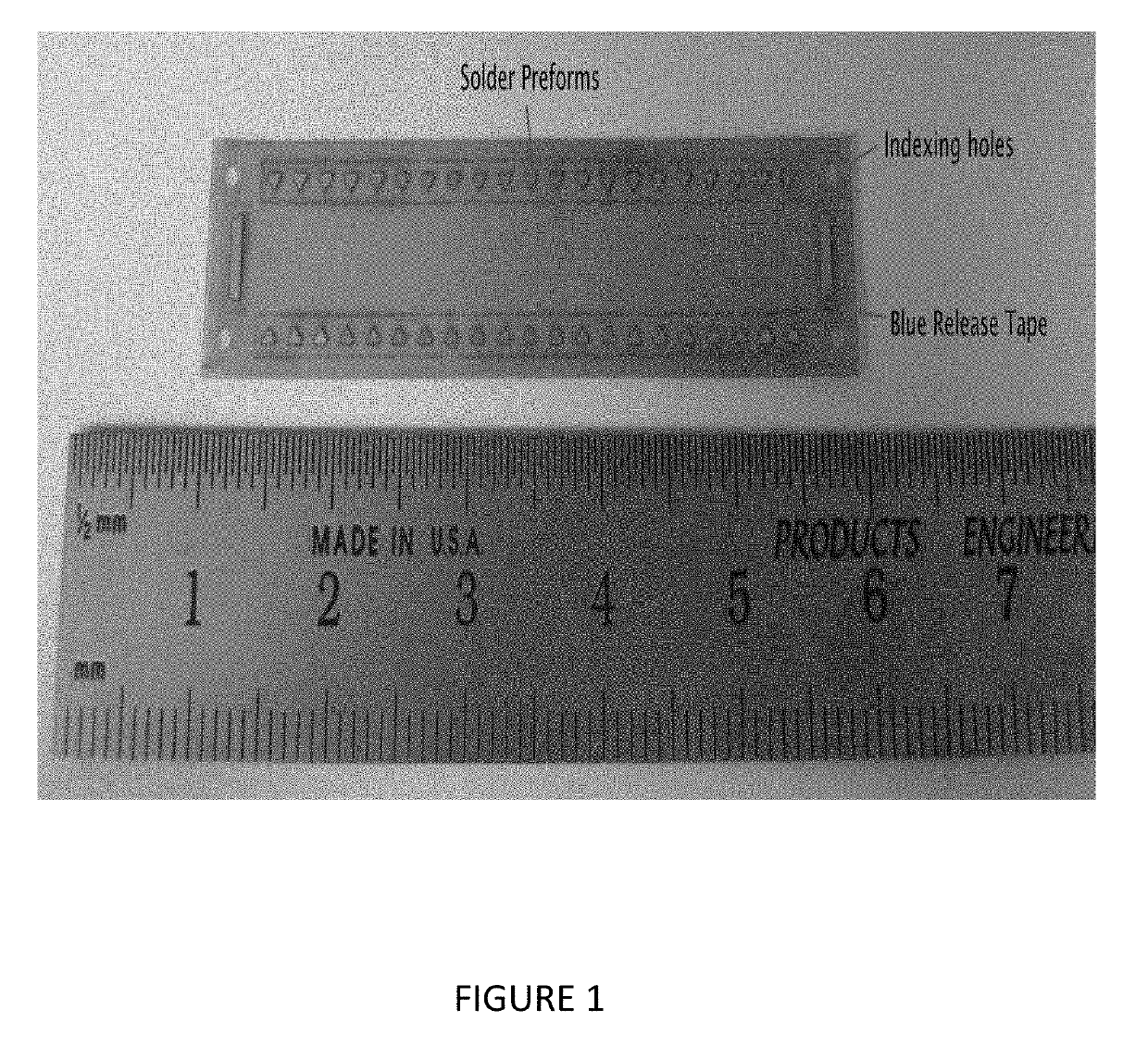
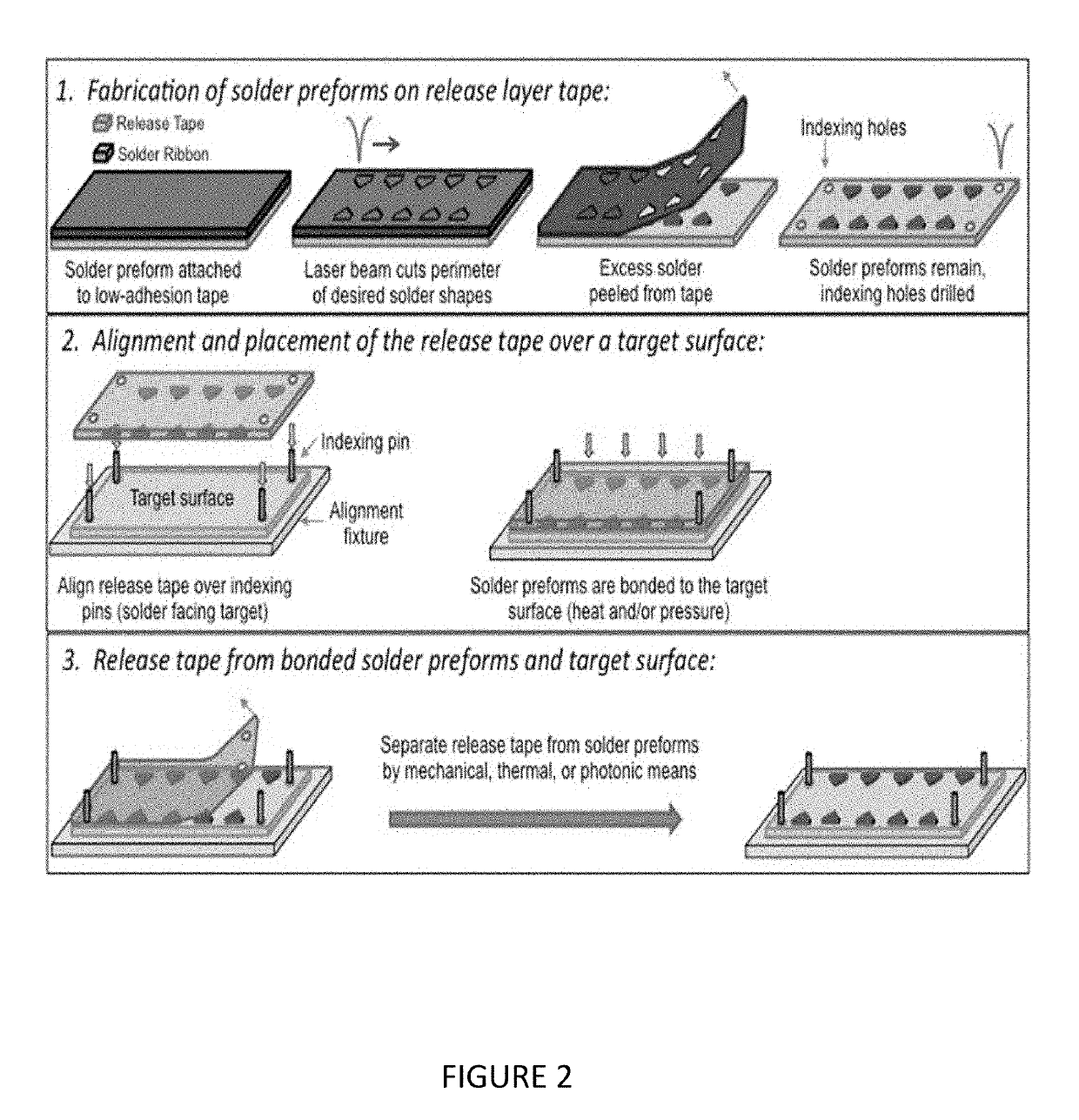
Precise Alignment and Decal Bonding of a Pattern of Solder Preforms to a Surface
InactiveUS20190184480A1Efficient and scalableEasy to integrateDecalcomaniaSemiconductor/solid-state device detailsTarget surfaceAdhesive belt
A method of making precise alignment and decal bonding of a pattern of solder preforms to a surface comprising cutting and placing a length of a solder ribbon onto a semiconductor release tape forming a solder ribbon and semiconductor release tape combination, placing the solder ribbon and semiconductor release tape combination on a vacuum chuck on X-Y stage pair in a laser micromachining system, adjusting the working distance, laser-cutting an outline, peeling off the solder ribbon, allowing the desired solder shape to remain, creating indexing holes, providing a target surface on an alignment fixture with indexing pins, aligning the indexing holes, placing the semiconductor release tape with the desired solder shape on the target surface, pressing the desired solder shape onto the target surface, removing the release tape, and making a pattern of the desired solder shape with precise alignment and decal bonding on the target surface.
Owner:UNITED STATES OF AMERICA
Privacy-preserving stream analytics
ActiveUS10390220B2Privacy protectionEfficient and scalableMultiple keys/algorithms usageData stream serial/continuous modificationInternet privacyThe Internet
Privacy-preserving stream analytics (personal data collection method, apparatus, and / or system) from an electronic (e.g., mobile) device providing communications, such as to a network (e.g., Internet). Data queries from a data analyst are received but not directly answered with a truthful query response. Truthful responses are privatized and anonymized based on a randomized response mechanism which releases privatized data and not the original answer. Anonymously transmitting randomized responses from the data owner to data aggregator using shares, each share of which is individually transmitted to an independent aggregator, which is configured for independently and asynchronously process each share, and sharing results with one another to arrive at a query response over an aggregate number of data owners.
Owner:RGT UNIV OF CALIFORNIA
Metallic and semiconducting carbon nanotube sorting
ActiveUS9017537B2Way fastReduce needElectrolysis componentsElectrostatic separatorsLiquid jetCarbon nanotube
Owner:EASTMAN KODAK CO
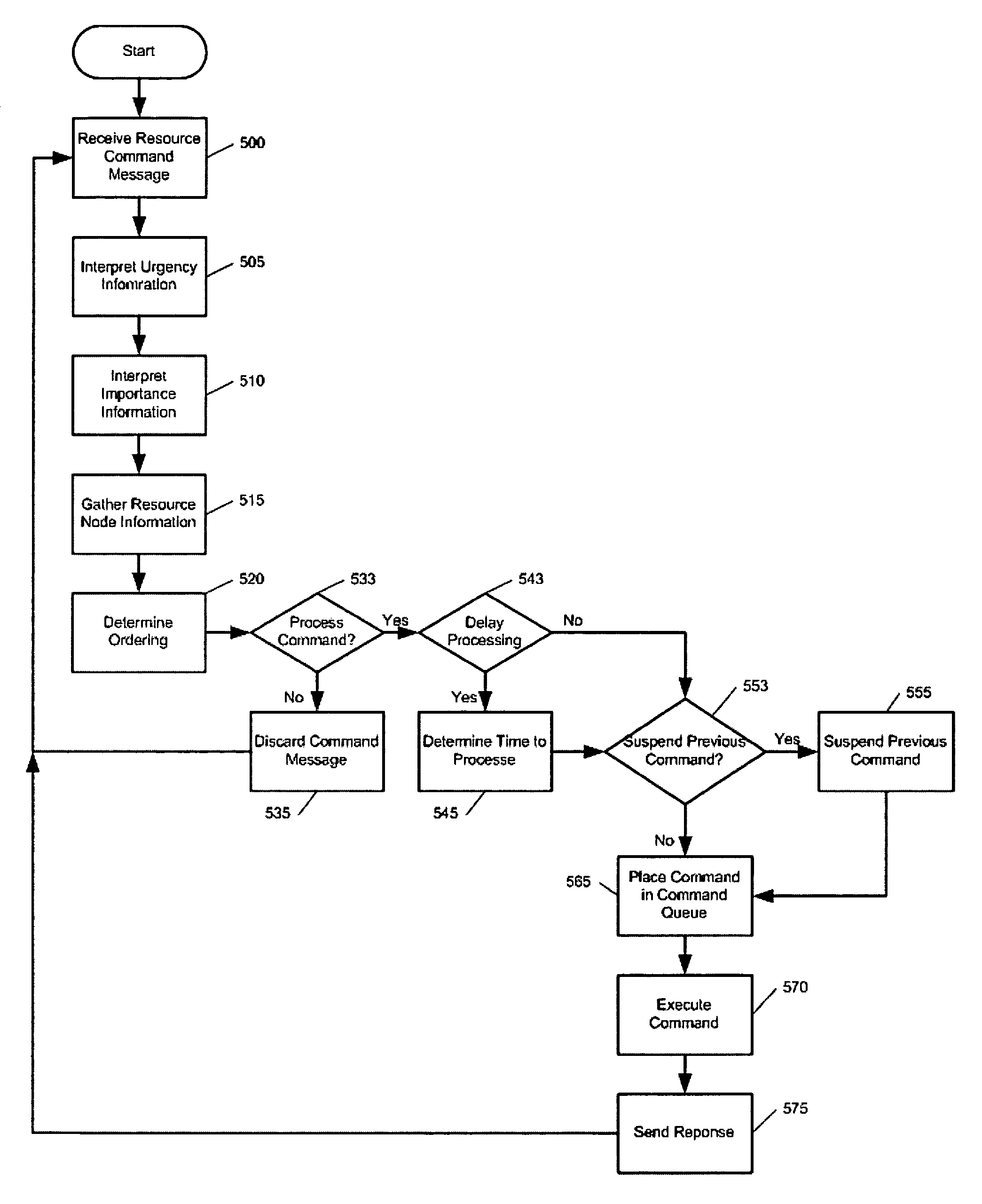
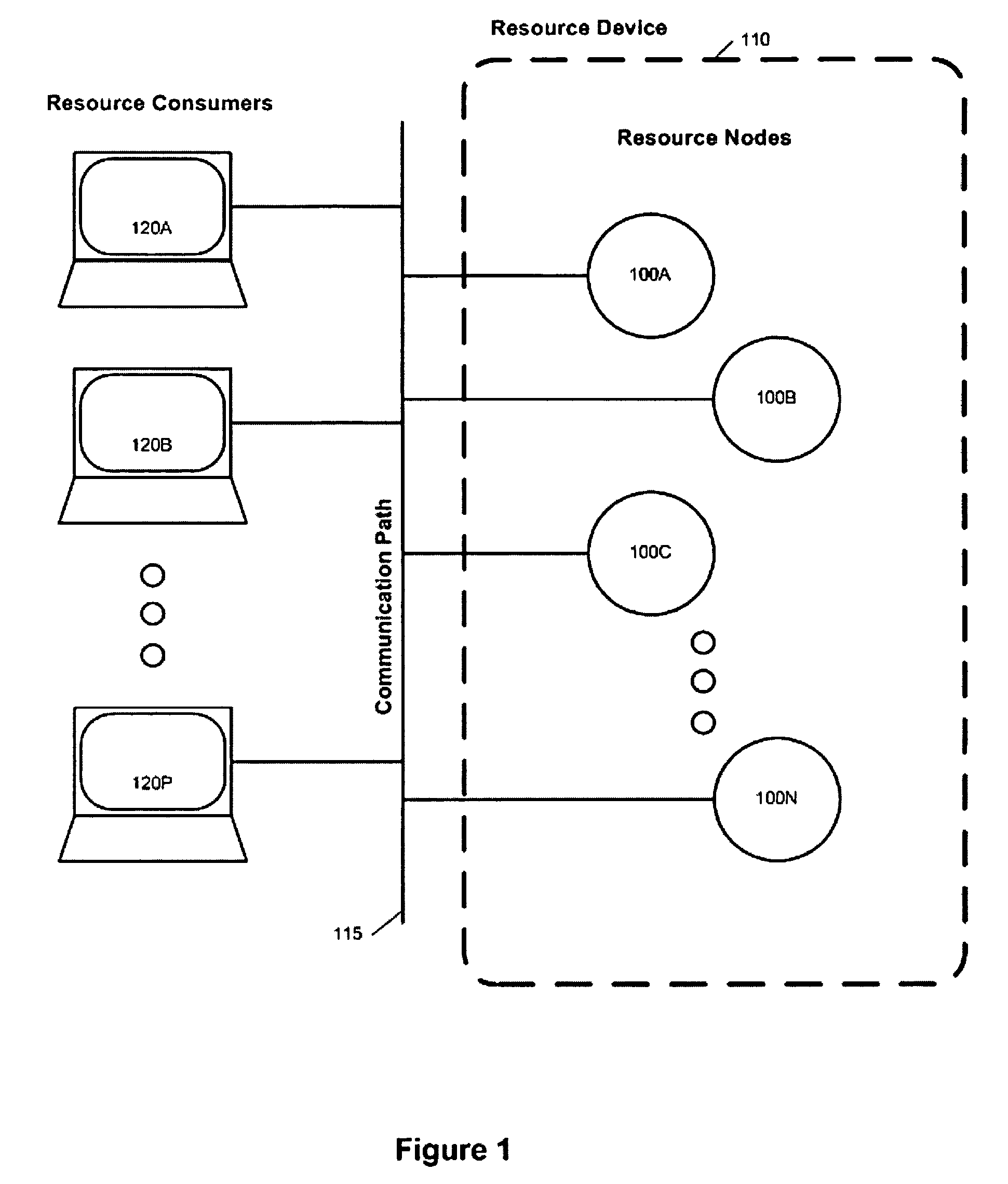
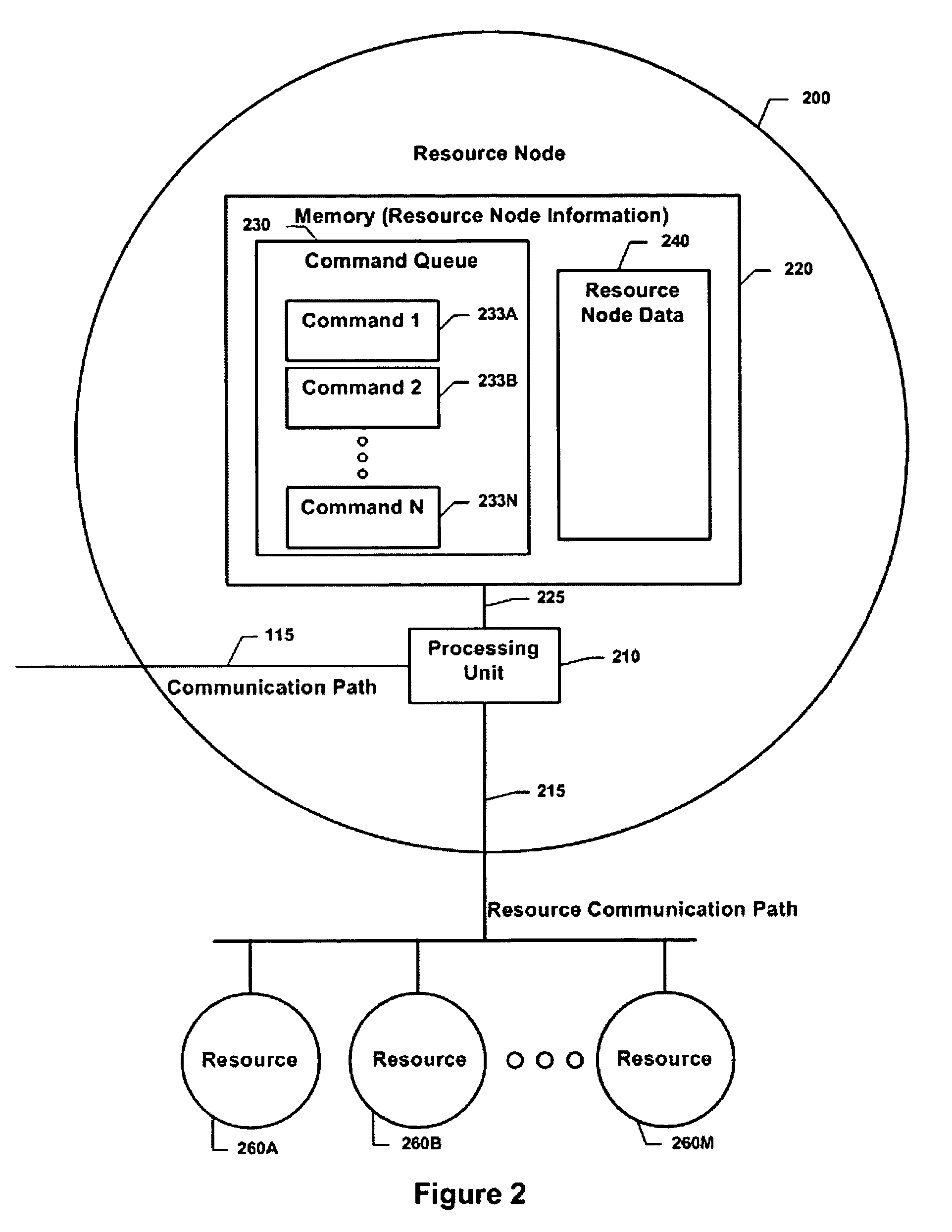
Resource command messages and methods
ActiveUS9270532B2Efficient and scalableImprove performanceSignal allocationMultiple digital computer combinationsComputer networkParallel processing
Resource command messages comprise commands and command urgency or importance information that is interpreted by a resource device and is coupled with information relating to the resource device to determine when to process the command within the resource command message. Resource devices comprising a plurality of resource nodes provide increased performance, responsiveness, and load balancing by multiple resource nodes processing the same resource command message in parallel.
Owner:RATEZE REMOTE MGMT LLC
Metallic and semiconducting carbon nanotube sorting
Owner:EASTMAN KODAK CO
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com