Detection method for APTs (Advanced Persistent Threat) based on instruction monitoring
A threat detection and command technology, applied in the field of APT advanced threat detection based on command monitoring, can solve the problems of inability to adapt to the security situation, lack of unknown attack detection capabilities and traffic in-depth analysis capabilities, achieve high reliability and scalability, and improve security. performance, reliability and efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
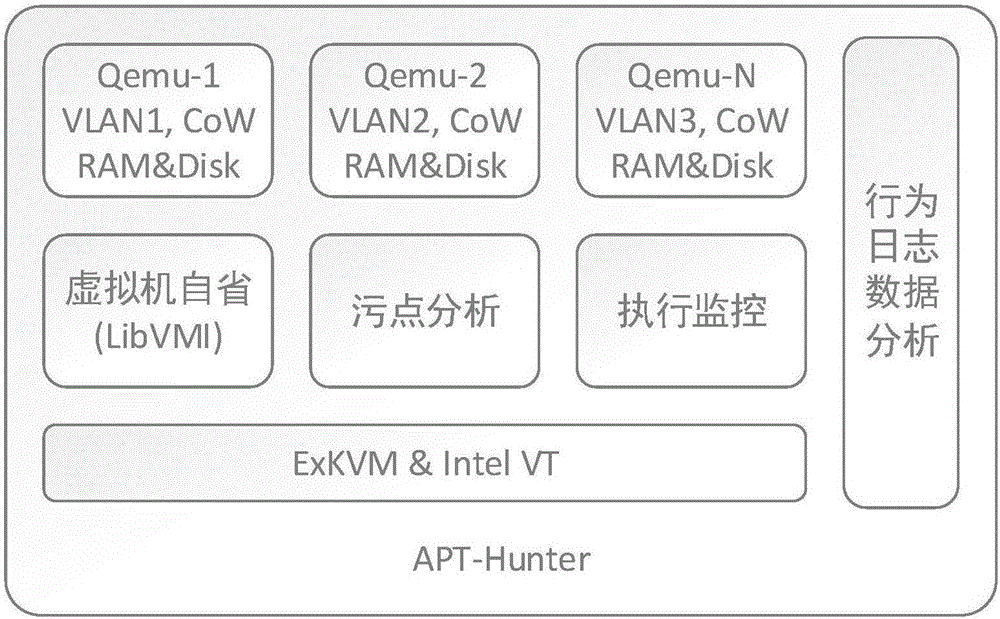
[0024] A new APT advanced threat detection method based on instruction-level monitoring proposed by the present invention uses KVM virtualization and Intel hardware virtualization technology (Intel-VT) to perform function (API) level and instruction on malicious code in APT attacks. In-depth analysis of high-level behavior monitoring; and use taint analysis and other vulnerability detection methods to effectively detect unknown and known vulnerability exploitation behaviors from the root cause. The invention has the characteristics of high scalability, strong concealment, high data fidelity and the like.
[0025] One, overall structure of the present invention
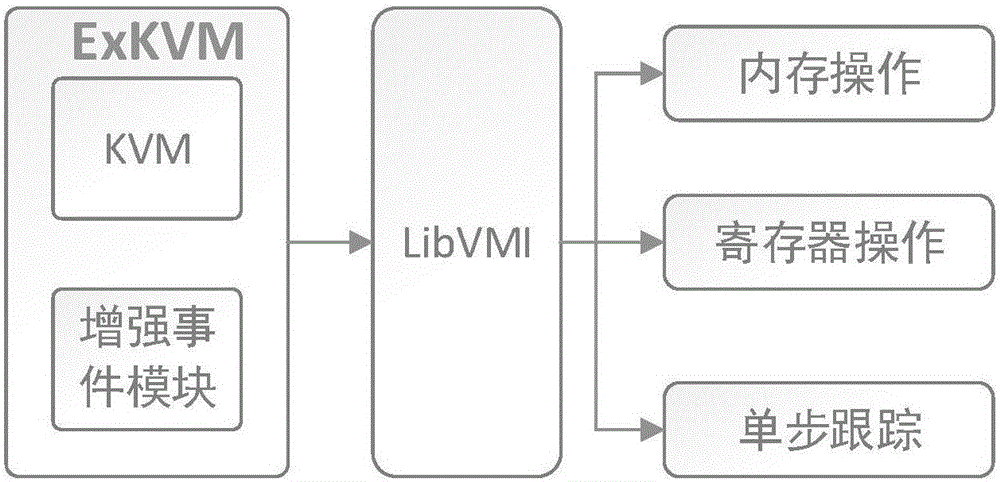
[0026] Such as figure 1 As shown, the main modules include: custom ExKVM (extended KVM), multiple virtual machines, virtual machine introspection (LibVMI), taint analysis, operation monitoring and behavior log data analysis modules. The design goal of the present invention is to be able to deeply and efficiently anal...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com