Method for producing long code mask for cluster service
A technology for long code masking and trunking services, which is applied in multiplexing code allocation, image coding, broadcast service distribution, etc. The code is not the same, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
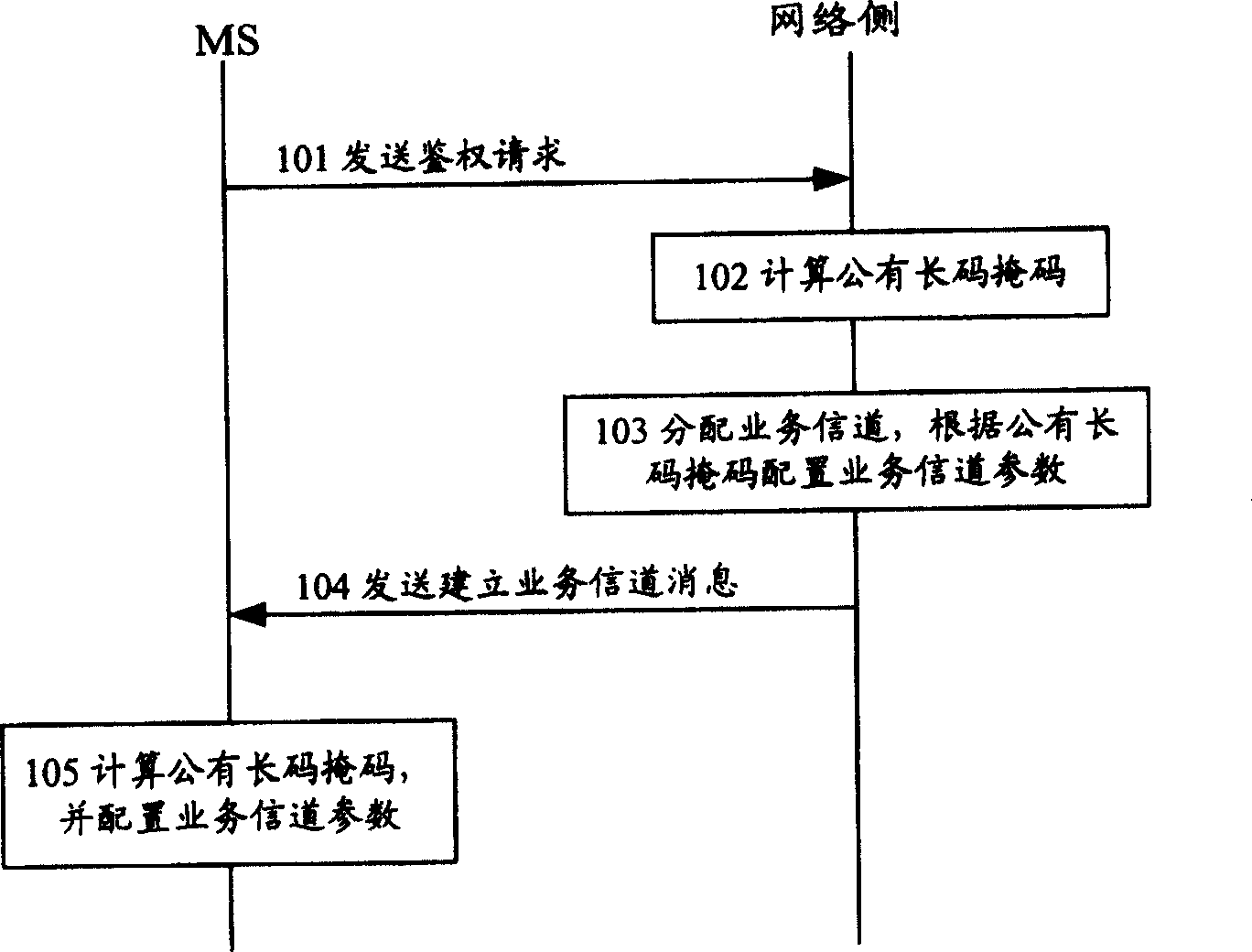
[0065] In order to make the object, technical solution and advantages of the present invention clearer, the present invention will be further described in detail below in conjunction with the embodiments and accompanying drawings.
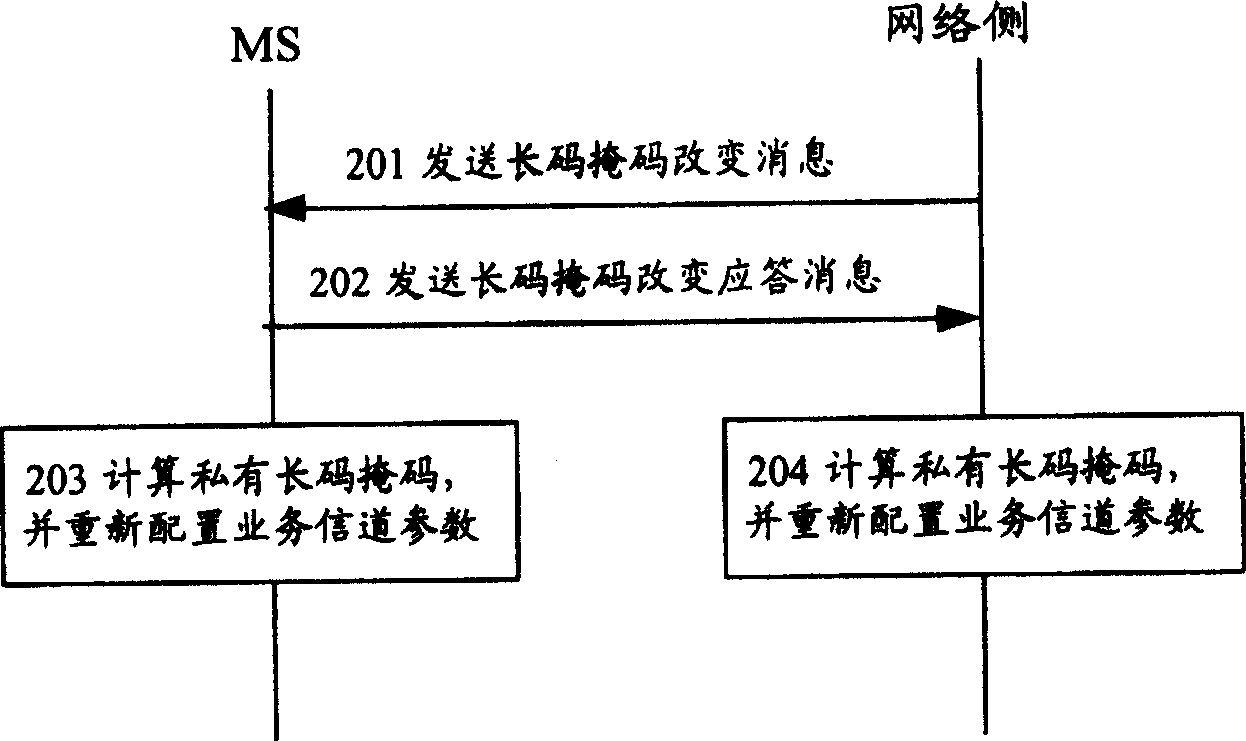
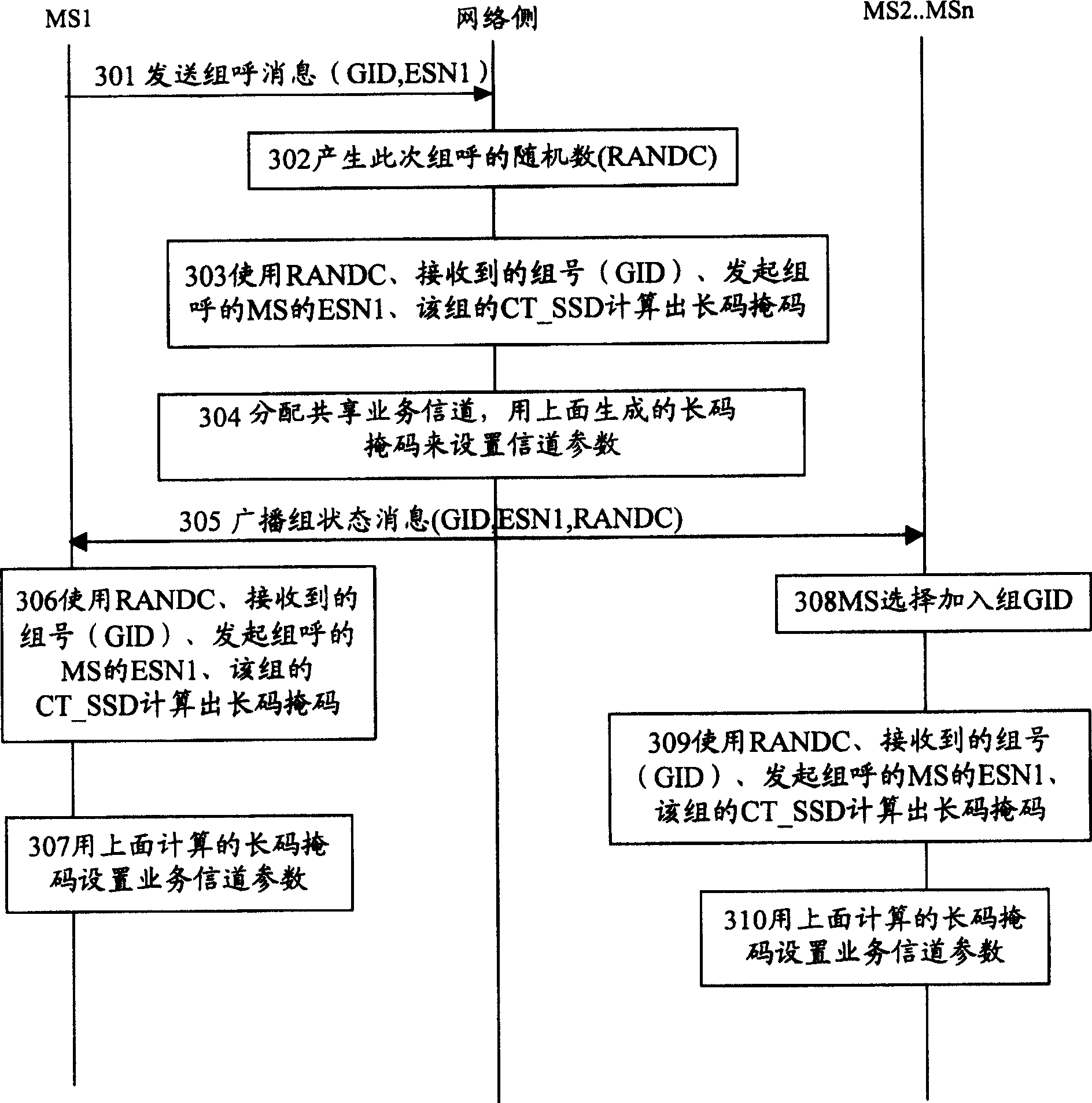
[0066] The core idea of the method for generating the long code mask for trunking services of the present invention is to replace the parameters in the private long code mask algorithm with new parameters on the basis of the CDMA2000 private long code mask algorithm, and use the private The long code mask algorithm is used to calculate and generate a long code mask that satisfies the confidentiality and sharing of cluster services.
[0067] Refer to Table 1 for parameter replacement:
[0068] parameter Input when calculating the private long code Input when calculating the cluster long code RAND_CHALLENGE RANDC is given by the network side RANDC is given by the network side ESN MS ESN ESN of the MS that initiated t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com