Security management method for mobile phone
A management method and security management technology, which is applied in the field of mobile phone security management, can solve the problems of easy misoperation, easy cracking of passwords, poor feasibility, etc., and achieve the effect of convenient use, flexible processing methods, and difficult cracking
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
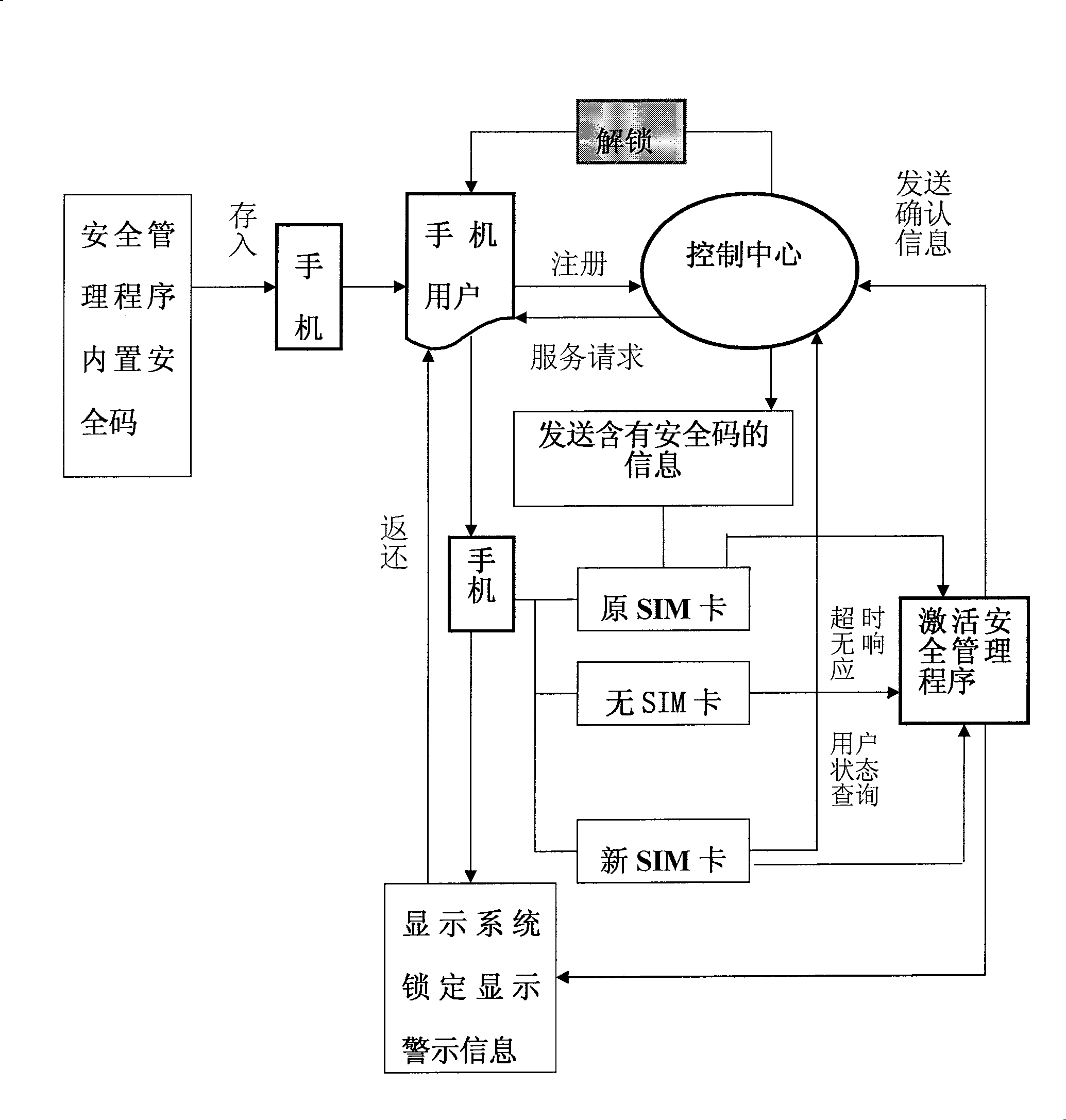
[0037] Referring to the accompanying drawings, the method includes
[0038] 1. First, save the security management program in the mobile phone, which is a program containing a "security code".
[0039] 2. The initial user information is input to the mobile phone through the control center, the control center stores the information, and the control center can call the information after receiving the service request. User information may include the user's name, mobile phone number, address, ID number or password, and question prompts in case the password is forgotten. After the initial user information input is completed, the user can modify the information content. The sending method of initial user information can be short message, telephone or Internet etc.
[0040] 3. Activate the security management program of the mobile phone
[0041] (1). When the user sends a service request to the control center, the control center will send a message containing the "security code" ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com