Processing method for ensuring information safety in communication system
An information security and communication system technology, applied in the field of information security assurance, can solve the problems of delayed PDG and terminal communication, data loss, dropped data packets, etc., to achieve the effect of strengthening flexible processing capabilities, enhancing functions, and saving air interface resources
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0097] The present invention will be described in further detail below through specific embodiments and accompanying drawings.
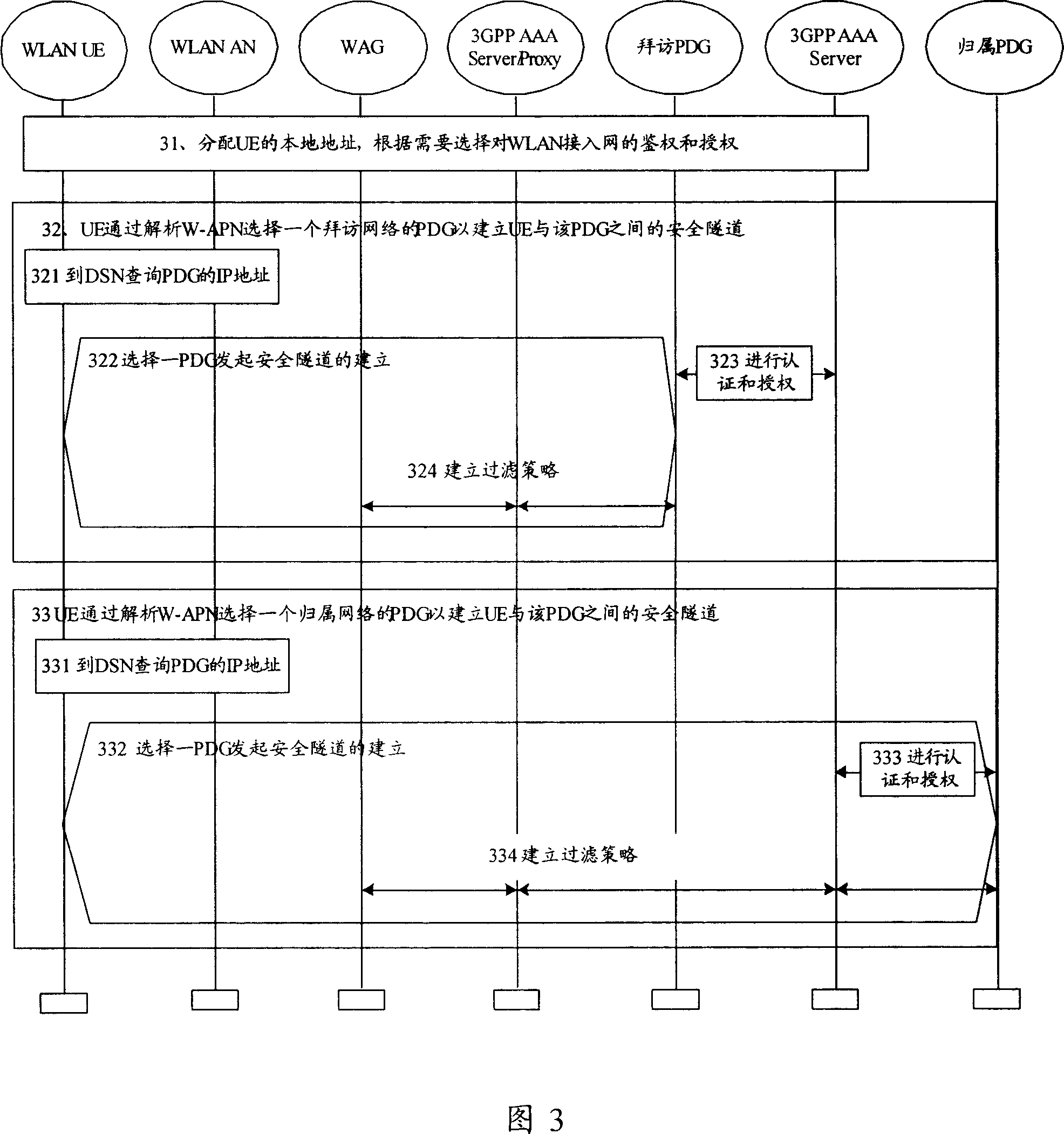
[0098] Fig. 6 is a flowchart of the method of the present invention. Referring to Fig. 6, the present invention is an information security processing method in a communication system, which is applicable to a communication system in which information is transmitted between a core network gateway and a terminal through a secure tunnel to ensure information security, including:
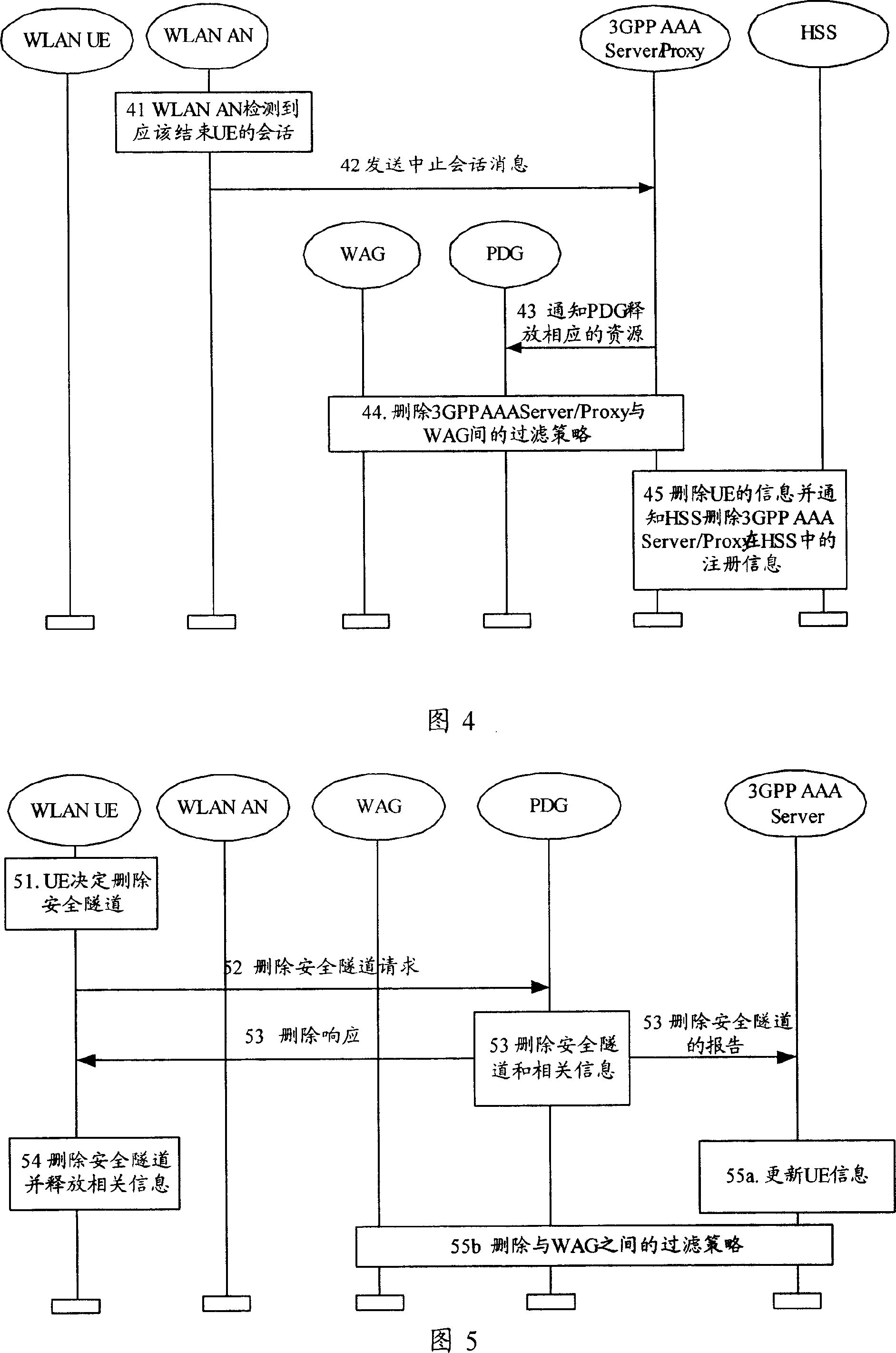
[0099] Step 61. When the terminal enters the inactive state, trigger deletion of the data channel between the terminal and the access network.
[0100] Step 62: When sending information to the terminal, the core network gateway notifies the access network to establish a data channel with the terminal, and sends the information to the terminal through the secure tunnel between the core network gateway and the terminal.
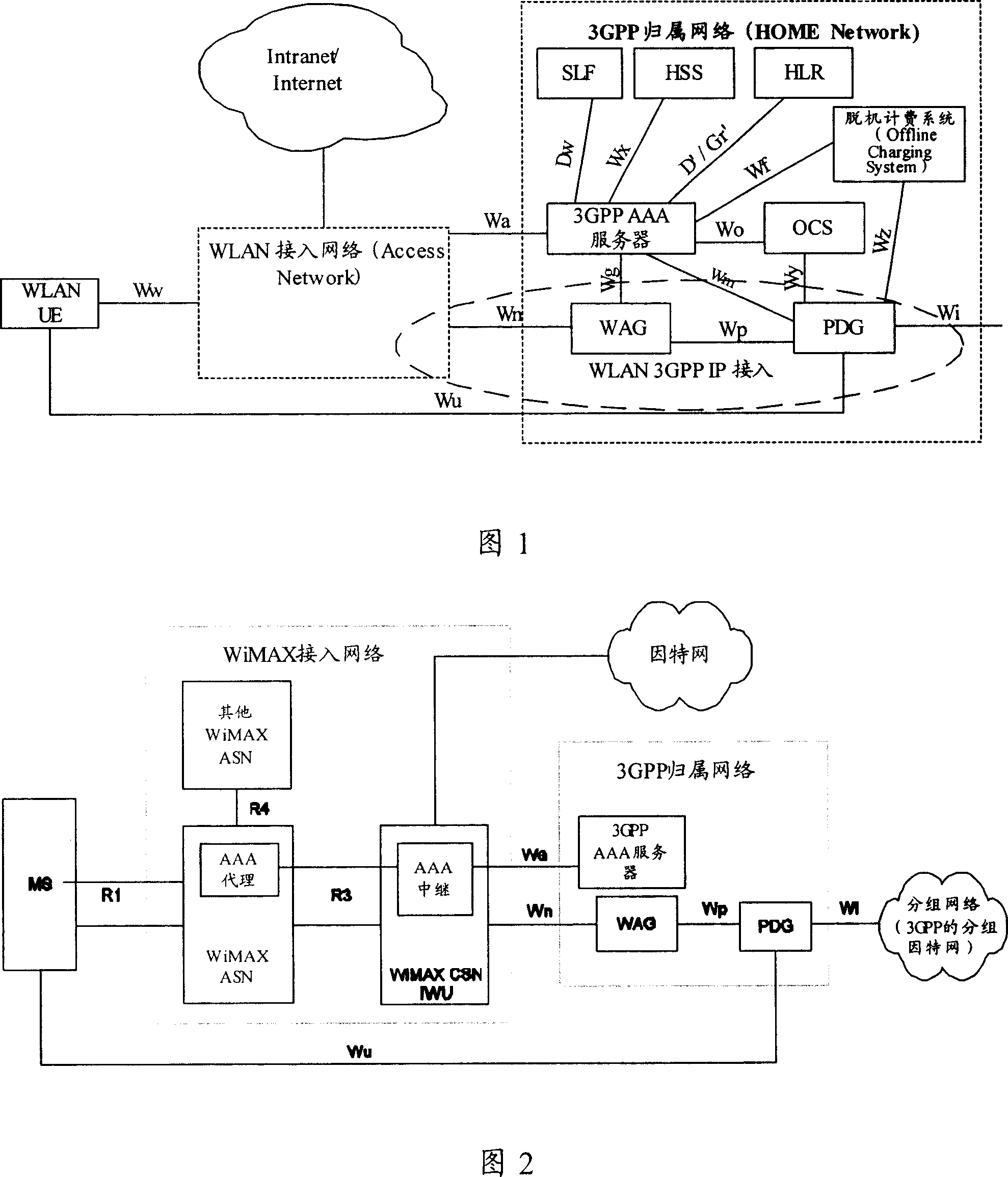
[0101] The access network described in the present inven...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com