Secure pairing for wired or wireless communications devices
A kind of equipment and wireless technology, which is applied in the direction of wireless communication, security device, data exchange through path configuration, etc., to achieve the effect of improving the security level
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
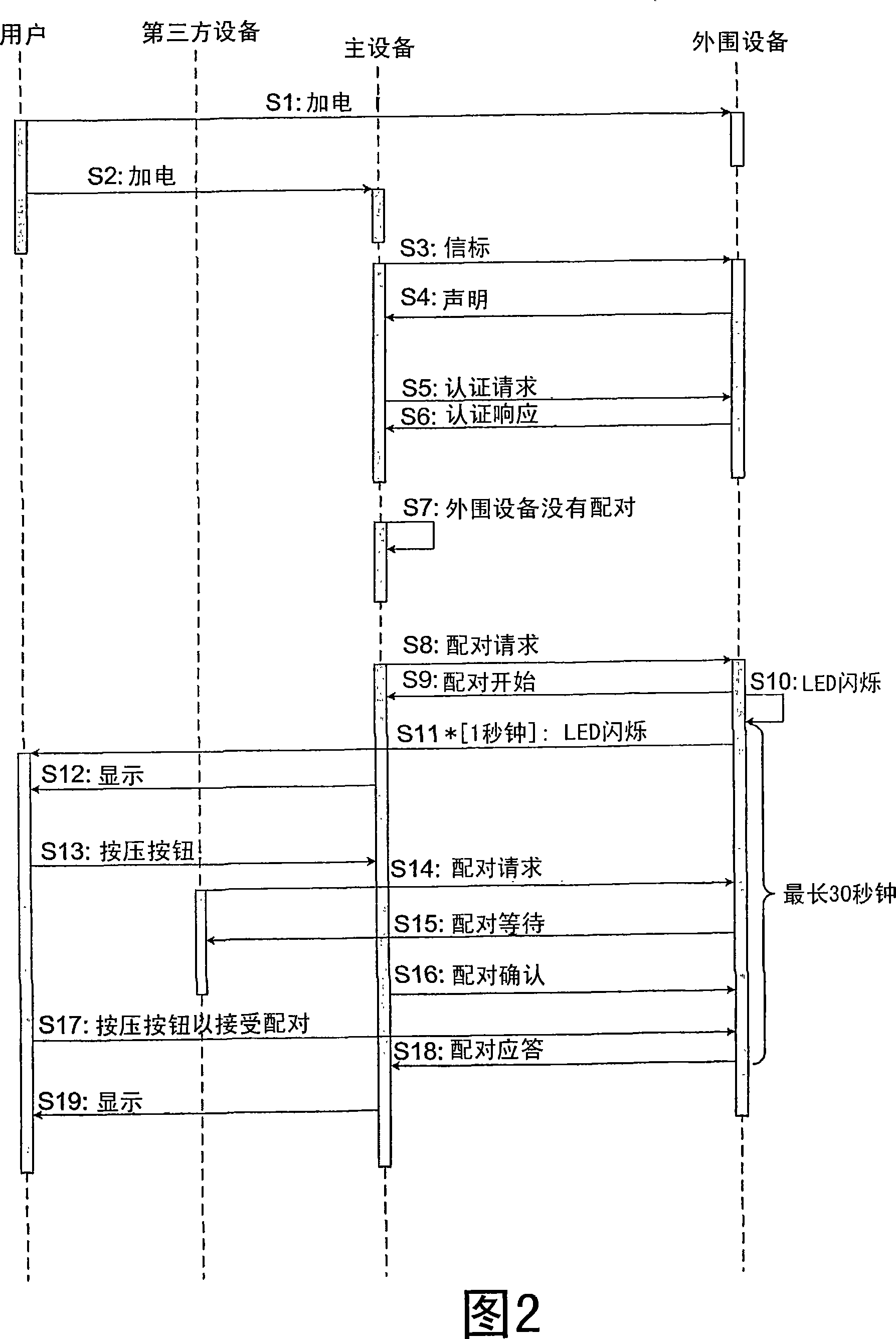
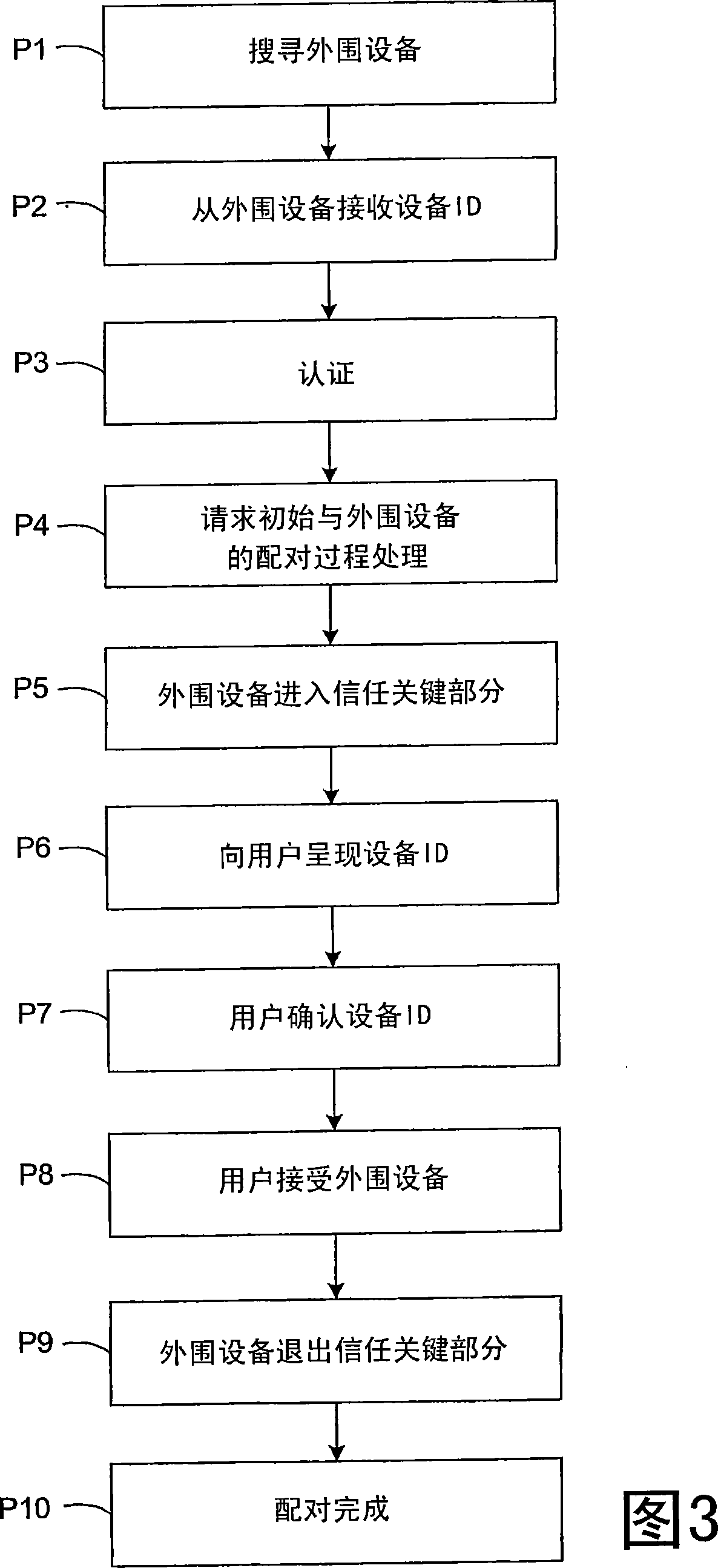
[0020] Although the invention is described herein as being implemented in a wireless network, it should be understood that the invention is also applicable to wired networks in which a host device is directly or indirectly connected to a peripheral device through a cable or other physical connector.
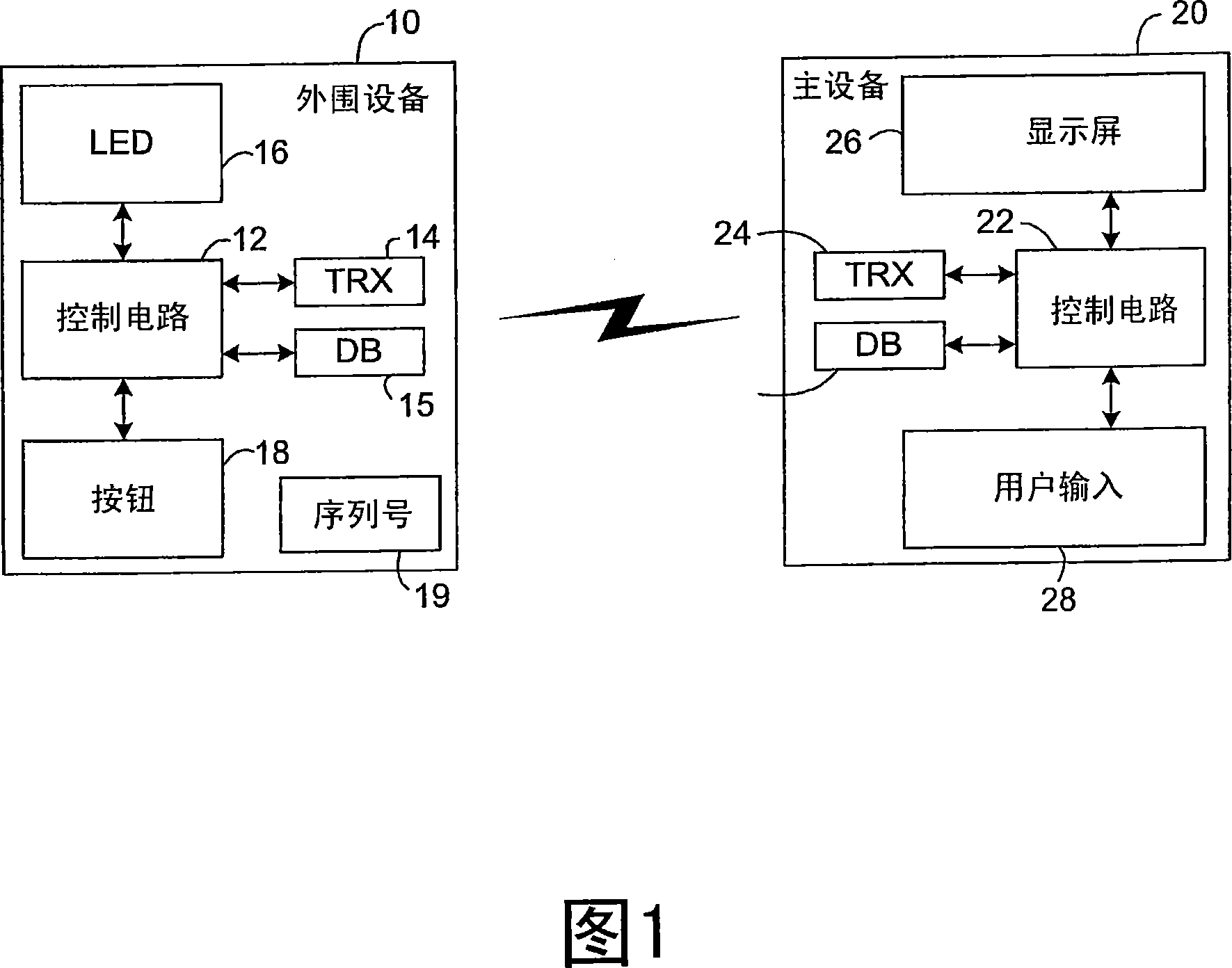
[0021] Two electronic devices 10 and 20 shown in the block diagram of FIG. 1 form an ad hoc wireless network through wireless connection.
[0022] In the illustrated embodiment of the invention, the first electronic device 10 acts as a peripheral device and the second electronic device 20 acts as a master device. For example, the first electronic device 10 may be a portable memory device, a mobile phone hands-free set or a wireless network access point (such as a Wi-Fi access point), while the second electronic device 20 may be a camera, a mobile phone or a personal computer, The formed ad hoc wireless network enables data transmission from the first device 10 to the second devic...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com